Bypassing Port Forwarding Restrictions on T-Mobile Home Internet Using Pinggy
If you're using T-Mobile's Home Internet, you might have encountered difficulties when trying to set up port forwarding—a common requirement for hosting servers, using remote desktop, or managing smart devices. The root of the issue lies in Carrier-Grade NAT (CG-NAT), a technology T-Mobile uses to manage IP addresses. What Is Port Forwarding and Why Do You Need It? Port forwarding is a method that allows external devices (e.g., from the internet) to access services hosted within your local private network. It’s commonly used for: Hosting web servers Running game servers Remote SSH access File transfers (FTP/SFTP) Receiving webhooks or API requests from external systems Accessing surveillance systems or NAS storage remotely Typically, port forwarding is configured at the router level by mapping an external port to a specific internal IP and port. Why T-Mobile Home Internet Blocks Port Forwarding T-Mobile uses Carrier-Grade Network Address Translation (CG-NAT), which means multiple users share a single public IP address. As a result: You don’t receive a dedicated public IP Inbound traffic from the internet is blocked before it reaches your router You cannot configure router-level port forwarding even if your device supports it. This setup is beneficial for conserving IPv4 addresses but creates challenges for anyone needing direct external access to devices on their home network. A Workaround: Using Reverse Tunneling with Pinggy To bypass CG-NAT, you can use reverse tunneling—a technique where a device inside your network initiates an outbound connection to a server (outside your network), which then relays external traffic back into your network. Pinggy is one such tool that creates tunnels from your local machine to the public internet, allowing you to expose local services (like HTTP servers or SSH) even behind CG-NAT. Below are step-by-step instructions on how to use Pinggy effectively. Step-by-Step Guide: Using Pinggy for Port Forwarding on T-Mobile Option 1: Create an HTTP Tunnel (for web servers, APIs, etc.) Use Case: You’re running a local HTTP server (e.g., on port 8000) and want it accessible from the internet. Command: ssh -p 443 -R0:localhost:8000 qr@a.pinggy.io What This Does: Establishes a secure reverse SSH tunnel from your system to Pinggy’s server Exposes port 8000 of your local machine to the internet Returns a public HTTP/HTTPS URL like: https://abcxyz123.pinggy.link You (or others) can access your local site by visiting this URL in a browser. Optional: Add Custom Settings You can adjust the command for added reliability: ssh -p 443 -L4300:localhost:4300 -o StrictHostKeyChecking=no -o ServerAliveInterval=30 -R0:localhost:8080 a.pinggy.io This setup enables: A local web debugger at http://localhost:4300 Automatic connection keep-alive Better reliability on unstable networks Option 2: Create a TCP Tunnel (for SSH, FTP, RDP, etc.) Use Case: You want to remotely SSH into your home machine (the default SSH port is 22). Command: ssh -p 443 -R0:localhost:22 tcp@a.pinggy.io What This Does: Exposes your local TCP port 22 to the internet Returns a public address like: tcp://abcxyz123.a.pinggy.link:42123 Now, you can SSH into your home machine from another device using: ssh -p 42123 user@abcxyz123.a.pinggy.link Replace user with your local machine’s username. Optional: Reliable TCP Tunnel ssh -p 443 -o StrictHostKeyChecking=no -o ServerAliveInterval=30 -R0:localhost:22 tcp@a.pinggy.io Security Best Practices Using public tunnels introduces some risks, so it's recommended to: Use strong passwords or SSH key authentication Limit tunnel access (e.g., with IP whitelisting) Consider password-protecting your tunnel URLs Avoid exposing sensitive services without encryption (use HTTPS or SFTP) Persistent URLs (Optional) By default, Pinggy gives you a random URL every time you open a tunnel. If you require persistent or branded URLs: Visit https://dashboard.pinggy.io Sign in and retrieve your access token Start a tunnel using the token to maintain consistent endpoints You can also link a custom domain to your tunnel for easy access Note: Persistent tunnels may require a paid plan, depending on the provider. Conclusion T-Mobile’s CG-NAT setup limits your ability to use traditional port forwarding. This can be frustrating if you want to run servers, access your home devices remotely, or use real-time communication services. Fortunately, tunneling tools like Pinggy provide an effective, secure workaround. With just a terminal and a few commands, you can make your local applications publicly accessible—without needing a public IP or router access.
If you're using T-Mobile's Home Internet, you might have encountered difficulties when trying to set up port forwarding—a common requirement for hosting servers, using remote desktop, or managing smart devices. The root of the issue lies in Carrier-Grade NAT (CG-NAT), a technology T-Mobile uses to manage IP addresses.
What Is Port Forwarding and Why Do You Need It?
Port forwarding is a method that allows external devices (e.g., from the internet) to access services hosted within your local private network. It’s commonly used for:
- Hosting web servers
- Running game servers
- Remote SSH access
- File transfers (FTP/SFTP)
- Receiving webhooks or API requests from external systems
- Accessing surveillance systems or NAS storage remotely
Typically, port forwarding is configured at the router level by mapping an external port to a specific internal IP and port.
Why T-Mobile Home Internet Blocks Port Forwarding
T-Mobile uses Carrier-Grade Network Address Translation (CG-NAT), which means multiple users share a single public IP address. As a result:
- You don’t receive a dedicated public IP
- Inbound traffic from the internet is blocked before it reaches your router
- You cannot configure router-level port forwarding even if your device supports it.
This setup is beneficial for conserving IPv4 addresses but creates challenges for anyone needing direct external access to devices on their home network.
A Workaround: Using Reverse Tunneling with Pinggy
To bypass CG-NAT, you can use reverse tunneling—a technique where a device inside your network initiates an outbound connection to a server (outside your network), which then relays external traffic back into your network.
Pinggy is one such tool that creates tunnels from your local machine to the public internet, allowing you to expose local services (like HTTP servers or SSH) even behind CG-NAT.
Below are step-by-step instructions on how to use Pinggy effectively.
Step-by-Step Guide: Using Pinggy for Port Forwarding on T-Mobile
Option 1: Create an HTTP Tunnel (for web servers, APIs, etc.)
Use Case:
You’re running a local HTTP server (e.g., on port 8000) and want it accessible from the internet.
Command:
ssh -p 443 -R0:localhost:8000 qr@a.pinggy.io
What This Does:
- Establishes a secure reverse SSH tunnel from your system to Pinggy’s server
- Exposes port
8000of your local machine to the internet - Returns a public HTTP/HTTPS URL like:
https://abcxyz123.pinggy.link
You (or others) can access your local site by visiting this URL in a browser.
Optional: Add Custom Settings
You can adjust the command for added reliability:
ssh -p 443 -L4300:localhost:4300 -o StrictHostKeyChecking=no -o ServerAliveInterval=30 -R0:localhost:8080 a.pinggy.io
This setup enables:
- A local web debugger at
http://localhost:4300 - Automatic connection keep-alive
- Better reliability on unstable networks
Option 2: Create a TCP Tunnel (for SSH, FTP, RDP, etc.)
Use Case:
You want to remotely SSH into your home machine (the default SSH port is 22).
Command:
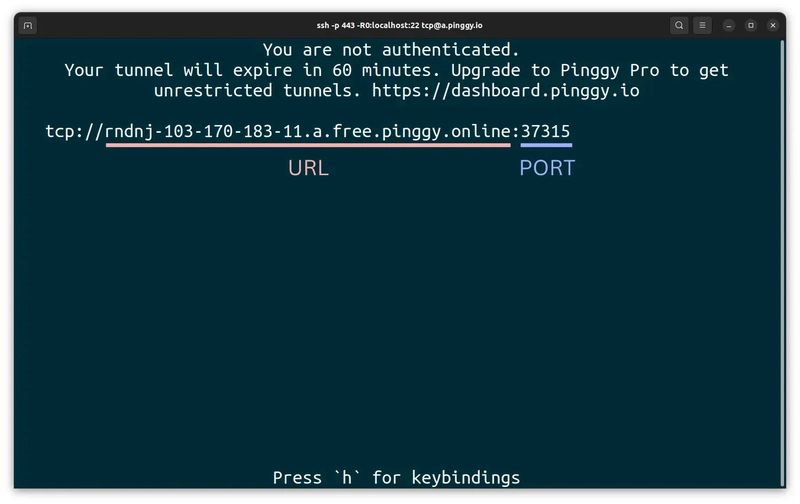
ssh -p 443 -R0:localhost:22 tcp@a.pinggy.io
What This Does:
- Exposes your local TCP port
22to the internet - Returns a public address like:
tcp://abcxyz123.a.pinggy.link:42123
Now, you can SSH into your home machine from another device using:
ssh -p 42123 user@abcxyz123.a.pinggy.link
Replace
userwith your local machine’s username.
Optional: Reliable TCP Tunnel
ssh -p 443 -o StrictHostKeyChecking=no -o ServerAliveInterval=30 -R0:localhost:22 tcp@a.pinggy.io
Security Best Practices
Using public tunnels introduces some risks, so it's recommended to:
- Use strong passwords or SSH key authentication
- Limit tunnel access (e.g., with IP whitelisting)
- Consider password-protecting your tunnel URLs
- Avoid exposing sensitive services without encryption (use HTTPS or SFTP)
Persistent URLs (Optional)
By default, Pinggy gives you a random URL every time you open a tunnel. If you require persistent or branded URLs:
- Visit https://dashboard.pinggy.io
- Sign in and retrieve your access token
- Start a tunnel using the token to maintain consistent endpoints
- You can also link a custom domain to your tunnel for easy access
Note: Persistent tunnels may require a paid plan, depending on the provider.
Conclusion
T-Mobile’s CG-NAT setup limits your ability to use traditional port forwarding. This can be frustrating if you want to run servers, access your home devices remotely, or use real-time communication services.
Fortunately, tunneling tools like Pinggy provide an effective, secure workaround. With just a terminal and a few commands, you can make your local applications publicly accessible—without needing a public IP or router access.




























![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiOWn65wd33dg2uO99NrtKbpYLfcepwOLidQDMls0HXKlA91k6HURluRA4WXgJRAZldEe1VReMQZyyYt1PgnoAn5JPpILsWlXIzmrBSs_TBoyPwO7hZrWouBg2-O3mdeoeSGY-l9_bsZB7vbpKjTSvG93zNytjxgTaMPqo9iq9Z5pGa05CJOs9uXpwHFT4/s1600/ai-cyber.jpg?#)














































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)







































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




























































































![What’s new in Android’s April 2025 Google System Updates [U: 4/18]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)









![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)