AWS Network Security Showdown: Network ACLs vs. Security Groups Demystified
** Relatable problem, setting the stage)** Picture this: you've just deployed your shiny new application on an EC2 instance in AWS. It works! But then, that nagging feeling creeps in... is it secure? You dive into the AWS console and encounter two security layers that sound suspiciously similar: Network Access Control Lists (NACLs) and Security Groups (SGs). Panic sets in. What's the difference? Do I need both? Which one does what? It feels like showing up to a party with two different bouncers checking your ID for seemingly the same reason. Relax! You're not alone. This confusion is common, but understanding the distinct roles of NACLs and SGs is fundamental to building secure and robust infrastructure on AWS. Let's unravel this together. (Why It Matters: Relevance and importance) In the cloud, security isn't just a feature; it's the foundation. A misconfigured firewall rule can be the difference between a smooth launch and a headline-making data breach. Network ACLs and Security Groups are your primary tools for controlling network traffic flow to and from your resources within your Virtual Private Cloud (VPC). Mastering them means: Stronger Security Posture: Implementing defense-in-depth by layering controls. Compliance Adherence: Meeting requirements for data isolation and access control. Troubleshooting Efficiency: Knowing where to look when connectivity issues arise. Optimized Performance: Preventing unwanted traffic from even reaching your instances. Getting this right isn't just best practice; it's essential for survival in the modern tech landscape. (The Concept in Simple Terms: Analogy time!) Imagine your AWS VPC is a large office building complex. Network ACLs (NACLs) are like the **Main Security Checkpoint at the Building Entrance.** They control access to the entire building complex (your VPC Subnet). They check everyone going in AND coming out (Stateless). They need explicit permission lists for both directions. The guards have a numbered list of rules (lowest number first) and stop checking once they find a match (allow or deny). If no rule matches, there's a default "deny all" catch-all (for custom NACLs; default NACLs start by allowing all). They operate at the subnet boundary. Security Groups (SGs) are like the **Key Card Access on Individual Office Doors.** They control access to a specific office or resource (your EC2 instance, RDS database, etc.). They primarily check who's trying to enter the office (Stateful). If you're allowed in, they assume you're allowed back out for that same conversation. You don't need a separate "exit pass" for return traffic. The door only has "allow" rules. If you're not on the allow list, you're implicitly denied entry. All allow rules are checked. They operate at the instance level (specifically, the Elastic Network Interface or ENI). Key takeaway: NACLs are the broader, stateless guards for the whole neighborhood (subnet), while SGs are the smarter, stateful guards for individual houses (instances). (Deeper Dive: Technical breakdown) Let's solidify that with more technical details: Network ACLs (NACLs): Your Subnet's Firewall Level: Operate at the Subnet level. Each subnet in your VPC must be associated with one NACL. A single NACL can span multiple subnets. State: Stateless. This is crucial. If you allow inbound traffic on port 80 (HTTP), you must also explicitly allow outbound traffic for the corresponding ephemeral ports (typically 1024-65535) for the response to get back out. Rules: Support both Allow and Deny rules. Rule Processing: Rules are evaluated in order by Rule Number, starting from the lowest. The first matching rule is applied, regardless of any subsequent rules. Default NACL: Allows ALL inbound and ALL outbound traffic. Custom NACL: Denies ALL inbound and ALL outbound traffic by default until you add rules. Use Cases: Blocking specific malicious IP addresses at the subnet level. Enforcing broad network segmentation rules between subnets (e.g., denying all traffic from a specific subnet). Acting as a coarse-grained, stateless firewall. Security Groups (SGs): Your Instance's Firewall Level: Operate at the Instance/ENI level. An instance can have multiple SGs attached, and an SG can be attached to multiple instances. State: Stateful. This is convenient. If you allow inbound traffic on port 22 (SSH) from a specific IP, the return traffic from the instance back to that IP is automatically allowed, regardless of outbound SG rules. Rules: Support Allow rules only. There's an implicit deny for any traffic not explicitly allowed. Rule Processing: All rules are evaluated before a decision is made to allow traffic. Default SG: Allows ALL outbound traffic. Allows inbound traffic only from other instances associated with the same default SG. Denies all other inbound traffic. Custom SG: Allows ALL outbound traffic by default. Denies ALL inbound traffic

** Relatable problem, setting the stage)**
Picture this: you've just deployed your shiny new application on an EC2 instance in AWS. It works! But then, that nagging feeling creeps in... is it secure? You dive into the AWS console and encounter two security layers that sound suspiciously similar: Network Access Control Lists (NACLs) and Security Groups (SGs).
Panic sets in. What's the difference? Do I need both? Which one does what? It feels like showing up to a party with two different bouncers checking your ID for seemingly the same reason. Relax! You're not alone. This confusion is common, but understanding the distinct roles of NACLs and SGs is fundamental to building secure and robust infrastructure on AWS. Let's unravel this together.
(Why It Matters: Relevance and importance)
In the cloud, security isn't just a feature; it's the foundation. A misconfigured firewall rule can be the difference between a smooth launch and a headline-making data breach. Network ACLs and Security Groups are your primary tools for controlling network traffic flow to and from your resources within your Virtual Private Cloud (VPC). Mastering them means:
- Stronger Security Posture: Implementing defense-in-depth by layering controls.
- Compliance Adherence: Meeting requirements for data isolation and access control.
- Troubleshooting Efficiency: Knowing where to look when connectivity issues arise.
- Optimized Performance: Preventing unwanted traffic from even reaching your instances.
Getting this right isn't just best practice; it's essential for survival in the modern tech landscape.
(The Concept in Simple Terms: Analogy time!)
Imagine your AWS VPC is a large office building complex.
-
Network ACLs (NACLs) are like the **Main Security Checkpoint at the Building Entrance.**
- They control access to the entire building complex (your VPC Subnet).
- They check everyone going in AND coming out (Stateless). They need explicit permission lists for both directions.
- The guards have a numbered list of rules (lowest number first) and stop checking once they find a match (allow or deny). If no rule matches, there's a default "deny all" catch-all (for custom NACLs; default NACLs start by allowing all).
- They operate at the subnet boundary.
-
Security Groups (SGs) are like the **Key Card Access on Individual Office Doors.**
- They control access to a specific office or resource (your EC2 instance, RDS database, etc.).
- They primarily check who's trying to enter the office (Stateful). If you're allowed in, they assume you're allowed back out for that same conversation. You don't need a separate "exit pass" for return traffic.
- The door only has "allow" rules. If you're not on the allow list, you're implicitly denied entry. All allow rules are checked.
- They operate at the instance level (specifically, the Elastic Network Interface or ENI).
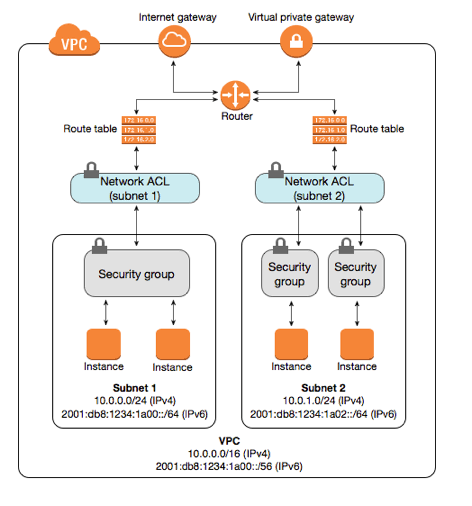
Key takeaway: NACLs are the broader, stateless guards for the whole neighborhood (subnet), while SGs are the smarter, stateful guards for individual houses (instances).
(Deeper Dive: Technical breakdown)
Let's solidify that with more technical details:
Network ACLs (NACLs): Your Subnet's Firewall
- Level: Operate at the Subnet level. Each subnet in your VPC must be associated with one NACL. A single NACL can span multiple subnets.
- State: Stateless. This is crucial. If you allow inbound traffic on port 80 (HTTP), you must also explicitly allow outbound traffic for the corresponding ephemeral ports (typically 1024-65535) for the response to get back out.
- Rules: Support both Allow and Deny rules.
- Rule Processing: Rules are evaluated in order by Rule Number, starting from the lowest. The first matching rule is applied, regardless of any subsequent rules.
- Default NACL: Allows ALL inbound and ALL outbound traffic.
- Custom NACL: Denies ALL inbound and ALL outbound traffic by default until you add rules.
- Use Cases:
- Blocking specific malicious IP addresses at the subnet level.
- Enforcing broad network segmentation rules between subnets (e.g., denying all traffic from a specific subnet).
- Acting as a coarse-grained, stateless firewall.
Security Groups (SGs): Your Instance's Firewall
- Level: Operate at the Instance/ENI level. An instance can have multiple SGs attached, and an SG can be attached to multiple instances.
- State: Stateful. This is convenient. If you allow inbound traffic on port 22 (SSH) from a specific IP, the return traffic from the instance back to that IP is automatically allowed, regardless of outbound SG rules.
- Rules: Support Allow rules only. There's an implicit deny for any traffic not explicitly allowed.
- Rule Processing: All rules are evaluated before a decision is made to allow traffic.
- Default SG: Allows ALL outbound traffic. Allows inbound traffic only from other instances associated with the same default SG. Denies all other inbound traffic.
- Custom SG: Allows ALL outbound traffic by default. Denies ALL inbound traffic by default until you add rules.
- Use Cases:
- Allowing specific ports/protocols (HTTP, SSH, RDP, DB ports) to instances.
- Restricting access based on source IP address or another Security Group (powerful!).
- Acting as a fine-grained, stateful firewall for individual resources.
Quick Comparison Table:
| Feature | Network ACL (NACL) | Security Group (SG) |
|---|---|---|
| Level | Subnet | Instance / ENI |
| State | Stateless | Stateful |
| Rule Type | Allow & Deny | Allow Only (Implicit Deny) |
| Rule Eval | Numbered Order (Lowest First) | All Rules Evaluated |
| Association | One NACL per Subnet | Multiple SGs per Instance/ENI possible |
| Default | Default NACL: Allow All In/Out | Default SG: Allow All Out, Deny All In * |
| Custom NACL: Deny All In/Out | Custom SG: Allow All Out, Deny All In |
*Default SG allows inbound only from itself.
(Practical Example or Use Case: Web Application)
Let's apply this to a common scenario: a standard two-tier web application with web servers in a public subnet and a database server in a private subnet.
-
VPC Setup:
- VPC:
10.0.0.0/16 - Public Subnet (Web Servers):
10.0.1.0/24 - Private Subnet (Database):
10.0.2.0/24
- VPC:
-
Network ACLs:
- Public Subnet NACL:
- Inbound:
- Rule 100: Allow TCP port 80 (HTTP) from
0.0.0.0/0 - Rule 110: Allow TCP port 443 (HTTPS) from
0.0.0.0/0 - Rule 120: Allow TCP port 22 (SSH) from Your Corporate IP Range (e.g.,
203.0.113.0/24) - Rule 200: Deny TCP port 22 from
0.0.0.0/0(Blocks SSH from anywhere else)
- Rule 100: Allow TCP port 80 (HTTP) from
- Outbound:
- Rule 100: Allow TCP ports 1024-65535 (Ephemeral) to
0.0.0.0/0(For replies to inbound HTTP/S/SSH) - Rule 110: Allow TCP port DB_PORT (e.g., 3306) to Private Subnet CIDR (
10.0.2.0/24)
- Rule 100: Allow TCP ports 1024-65535 (Ephemeral) to
- Inbound:
- Private Subnet NACL:
- Inbound:
- Rule 100: Allow TCP port DB_PORT (e.g., 3306) from Public Subnet CIDR (
10.0.1.0/24) - Rule 110: Allow TCP ports 1024-65535 from Public Subnet CIDR (
10.0.1.0/24) (For replies initiated from DB)
- Rule 100: Allow TCP port DB_PORT (e.g., 3306) from Public Subnet CIDR (
- Outbound:
- Rule 100: Allow TCP ports 1024-65535 to Public Subnet CIDR (
10.0.1.0/24) (Replies to web server requests) - Rule 110: Maybe allow traffic to specific AWS services (e.g., S3 endpoint) or patching servers if needed.
- Rule 100: Allow TCP ports 1024-65535 to Public Subnet CIDR (
- Inbound:
- Public Subnet NACL:
-
Security Groups:
- Web Server SG (
sg-web):- Inbound:
- Allow TCP port 80 from
0.0.0.0/0 - Allow TCP port 443 from
0.0.0.0/0 - Allow TCP port 22 from Bastion Host SG or Your Corporate IP
- Allow TCP port 80 from
- Outbound: (Default allows all, often sufficient, but can be restricted)
- Allow TCP port DB_PORT to Database SG (
sg-db)
- Allow TCP port DB_PORT to Database SG (
- Inbound:
- Database SG (
sg-db):- Inbound:
- Allow TCP port DB_PORT (e.g., 3306) only from the Web Server SG (
sg-web). This is key! Don't use IPs here; referencing the SG is more dynamic and secure.
- Allow TCP port DB_PORT (e.g., 3306) only from the Web Server SG (
- Outbound: (Default allows all, usually okay for DB response traffic)
- Inbound:
- Web Server SG (
Why both? The NACL provides a broad boundary (e.g., blocks SSH from the internet to the whole public subnet except your office IP), while the SG provides fine-grained control (e.g., only the web servers can talk to the database on the DB port). This is defense-in-depth.
(Common Mistakes or Misunderstandings)
- Forgetting NACLs are Stateless: The #1 issue. You allow inbound port 80 but forget to allow outbound ephemeral ports (1024-65535), and your web server responses get blocked by the NACL.
- Treating NACLs like SGs: Trying to apply very granular rules (like allowing instance A to talk to instance B) in the NACL. Use SGs for this level of detail. NACLs are for subnet-level rules.
- Overly Permissive Rules: Using
0.0.0.0/0(Any IP) liberally in both NACLs and SGs when more specific ranges or SG references could be used. Least privilege applies to networking too! - Rule Number Conflicts/Ordering: Adding a deny rule with a lower number than an allow rule in a NACL can block traffic unexpectedly. Plan your numbering.
- Relying Only on SGs: Thinking SGs are enough. NACLs add a crucial extra layer, especially for blocking unwanted traffic before it even reaches your instances.
- Default NACL vs. Custom NACL: Remembering that the default NACL allows everything, while a custom NACL you create denies everything initially. This can trip you up if you replace the default.
(Pro Tips & Hidden Features)
- VPC Flow Logs: Your best friend for troubleshooting network connectivity. Enable Flow Logs at the VPC, Subnet, or ENI level to see ACCEPT/REJECT records, which can pinpoint whether a NACL or SG dropped the traffic.
- Security Group Referencing: Instead of allowing traffic from an IP range in an SG, allow traffic from another SG. This is incredibly powerful for multi-tier applications, as instances automatically get access if they belong to the referenced SG, without you needing to update IP lists. (We used this in the DB SG example).
- Keep NACLs Simple: Use NACLs for broad strokes – block known bad IPs, allow/deny traffic between subnets. Use SGs for the fine-grained application/port-level control. Don't replicate complex SG logic in NACLs.
- Ephemeral Port Range: Remember the
1024-65535range for stateless NACL outbound rules. While technically OS-dependent, this range covers most Linux/Windows defaults. - Infrastructure as Code (IaC): Define your NACLs and SGs using Terraform, AWS CloudFormation, or CDK. This ensures consistency, version control, and easier management than click-ops in the console.
- AWS Firewall Manager: For organizations managing many accounts and VPCs, Firewall Manager can help centrally configure and audit NACLs and SGs across your AWS Organization.
(Minimal Code Snippet / CLI Command)
Want to quickly check the rules for a specific Security Group? Use the AWS CLI:
# Replace sg-xxxxxxxxxxxxxxxxx with your actual Security Group ID
aws ec2 describe-security-groups --group-ids sg-xxxxxxxxxxxxxxxxx --query "SecurityGroups[0].IpPermissions" --output table
# Example to check Network ACL rules (replace acl-xxxxxxxxxxxxxxxxx)
# aws ec2 describe-network-acls --network-acl-ids acl-xxxxxxxxxxxxxxxxx --query "NetworkAcls[0].Entries" --output table
This command fetches the inbound rules (IpPermissions) for the specified SG and formats them neatly. Use IpPermissionsEgress for outbound rules. A similar command exists for describe-network-acls.
(Final Thoughts + Call to Action)
Network ACLs and Security Groups aren't adversaries; they're partners in your AWS security strategy. Think of them as distinct layers working together: NACLs guard the subnet gates (stateless, broad), while SGs guard the instance doors (stateful, specific). Understanding their differences and using them in tandem provides robust, layered network security.
Don't just read about it – try it! Set up a test VPC, create public and private subnets, deploy a couple of EC2 instances, and experiment with different NACL and SG rules. Use VPC Flow Logs to see the impact. Break things, fix them, and learn. That's the best way to internalize these concepts.
What are your go-to strategies for managing NACLs and SGs? Any tricky scenarios you've overcome? Share your experiences and questions in the comments below – let's learn from each other!



































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)










































































































































_Muhammad_R._Fakhrurrozi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





























































































![What Google Messages features are rolling out [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)












![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)