Avoid the Mistakes That Led to the NTT Breach: Secure Linux User Onboarding and Access Control
18,000 organizations paid the price for poor access control. Don’t let yours be the next headline. The NTT Communications breach showed us what happens when user permissions and privileges are mismanaged. Attackers exploited weak access control and exposed sensitive data from over 18,000 organizations. Here’s how it should have been done: secure onboarding, least privilege, and strict access control using real-world Linux best practices. Table of Contents Scenario: You’re the SysAdmin 1. Create a New Group 2. Create User Accounts 3. Secure Home Directories 4. Assign Sudo Access to Team Lead 5. Implement Security Policies a. Password Complexity b. Password Expiry c. Protect Sensitive Files 6. Shared Directory for Collaboration 7. Basic Monitoring Best Practices Recap Conclusion: Secure by Design Let's Connect on LinkedIn Scenario: You’re the SysAdmin You’ve been assigned to set up a secure system for a newly hired technical team. Your goals: Create users and groups Apply controlled access Enforce security policies Protect sensitive data 1. Create a New Group 2. Create User Accounts Create three users (mr.a, mr.b, mrs.c), add them to the tech_team, and set their passwords: sudo passwd mr.a sudo passwd mrs.c Force password change on first login: 3. Secure Home Directories Ensure each user’s home is private: 4. Assign Sudo Access to Team Lead Give sudo rights to the team lead only: Leave mr.a and mrs.c as regular users. 5. Implement Security Policies a. Password Complexity Edit the PAM config: Set the following: minlen = 10 dcredit = -1 ucredit = -1 ocredit = -1 lcredit = -1 abc123 → Rejected Password1! → Accepted b. Password Expiry c. Protect Sensitive Files Restrict file access: sudo chmod 600 /var/log/auth.log Encrypt sensitive files: gpg -c secret_file.txt 6. Shared Directory for Collaboration sudo mkdir /project_data sudo chown :tech_team /project_data sudo chmod 770 /project_data This lets team members collaborate while keeping outsiders out. 7. Basic Monitoring User login logs: last Track sudo usage: grep 'sudo' /var/log/auth.log Monitor unauthorized privilege escalations early. Best Practices Recap Principle of Least Privilege (PoLP): Only give users access to what they need. Access Audits: Periodically review group and user access. Password Policies: Complexity, expiry, and rotation. Monitoring & Alerts: Use logs and tools to spot anomalies early. Conclusion: Secure by Design Ignoring access control is costly. Secure user onboarding, granular permissions, and proactive monitoring are non-negotiables in today’s landscape. By applying these Linux-based practices, you reduce your organization’s attack surface and stay out of the headlines. Let’s connect on LinkedIn (https://www.linkedin.com/in/chiamaka-chielo?utm_source=share&utm_campaign=share_via&utm_content=profile&utm_medium=android_app)

18,000 organizations paid the price for poor access control.
Don’t let yours be the next headline.
The NTT Communications breach showed us what happens when user permissions and privileges are mismanaged. Attackers exploited weak access control and exposed sensitive data from over 18,000 organizations.
Here’s how it should have been done: secure onboarding, least privilege, and strict access control using real-world Linux best practices.
Table of Contents
- Scenario: You’re the SysAdmin
- 1. Create a New Group
- 2. Create User Accounts
- 3. Secure Home Directories
- 4. Assign Sudo Access to Team Lead
-
5. Implement Security Policies
- a. Password Complexity
- b. Password Expiry
- c. Protect Sensitive Files
- 6. Shared Directory for Collaboration
- 7. Basic Monitoring
- Best Practices Recap
- Conclusion: Secure by Design
- Let's Connect on LinkedIn
Scenario: You’re the SysAdmin
You’ve been assigned to set up a secure system for a newly hired technical team. Your goals:
- Create users and groups
- Apply controlled access
- Enforce security policies
- Protect sensitive data
1. Create a New Group
2. Create User Accounts
Create three users (mr.a, mr.b, mrs.c), add them to the tech_team, and set their passwords:
sudo passwd mr.a
sudo passwd mrs.c
Force password change on first login:
3. Secure Home Directories
Ensure each user’s home is private:
4. Assign Sudo Access to Team Lead
Give sudo rights to the team lead only:
Leave mr.a and mrs.c as regular users.
5. Implement Security Policies
a. Password Complexity
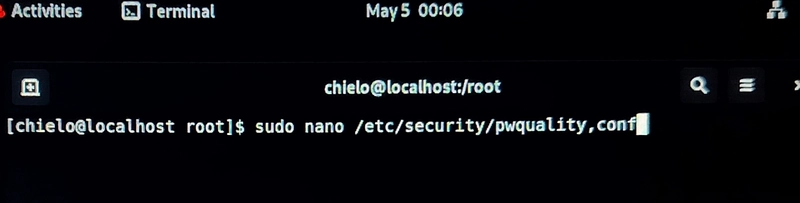
Edit the PAM config:
Set the following:
minlen = 10
dcredit = -1
ucredit = -1
ocredit = -1
lcredit = -1
-
abc123→ Rejected -
Password1!→ Accepted
b. Password Expiry
c. Protect Sensitive Files
Restrict file access:
sudo chmod 600 /var/log/auth.log
Encrypt sensitive files:
gpg -c secret_file.txt
6. Shared Directory for Collaboration
sudo mkdir /project_data
sudo chown :tech_team /project_data
sudo chmod 770 /project_data
This lets team members collaborate while keeping outsiders out.
7. Basic Monitoring
User login logs:
last
Track sudo usage:
grep 'sudo' /var/log/auth.log
Monitor unauthorized privilege escalations early.
Best Practices Recap
- Principle of Least Privilege (PoLP): Only give users access to what they need.
- Access Audits: Periodically review group and user access.
- Password Policies: Complexity, expiry, and rotation.
- Monitoring & Alerts: Use logs and tools to spot anomalies early.
Conclusion: Secure by Design
Ignoring access control is costly.
Secure user onboarding, granular permissions, and proactive monitoring are non-negotiables in today’s landscape.
By applying these Linux-based practices, you reduce your organization’s attack surface and stay out of the headlines.








































































































































































![[The AI Show Episode 145]: OpenAI Releases o3 and o4-mini, AI Is Causing “Quiet Layoffs,” Executive Order on Youth AI Education & GPT-4o’s Controversial Update](https://www.marketingaiinstitute.com/hubfs/ep%20145%20cover.png)

















































































































































































































































































































































































![Apple Shares Official Teaser for 'Highest 2 Lowest' Starring Denzel Washington [Video]](https://www.iclarified.com/images/news/97221/97221/97221-640.jpg)

![Under-Display Face ID Coming to iPhone 18 Pro and Pro Max [Rumor]](https://www.iclarified.com/images/news/97215/97215/97215-640.jpg)