Apache Pinot Vulnerability Let Attackers Bypass Authentication
A critical security vulnerability (CVE-2024-56325) in Apache Pinot, the open-source distributed OLAP datastore used by LinkedIn, Uber, and Microsoft for real-time analytics, allows unauthenticated attackers to bypass authentication controls and gain full system access. Rated 9.8 on the CVSS v3 scale – the maximum severity score – this flaw exposes organizations to data exfiltration, privilege […] The post Apache Pinot Vulnerability Let Attackers Bypass Authentication appeared first on Cyber Security News.
 (1).webp?#)
A critical security vulnerability (CVE-2024-56325) in Apache Pinot, the open-source distributed OLAP datastore used by LinkedIn, Uber, and Microsoft for real-time analytics, allows unauthenticated attackers to bypass authentication controls and gain full system access.
Rated 9.8 on the CVSS v3 scale – the maximum severity score – this flaw exposes organizations to data exfiltration, privilege escalation, and infrastructure compromise.
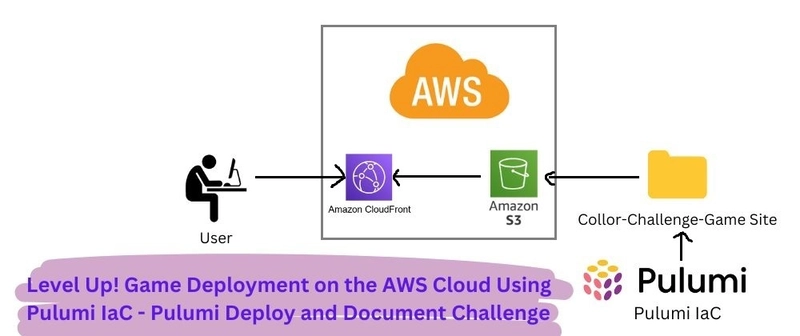
Apache Pinot Vulnerability
The vulnerability stems from improper neutralization of special characters in the AuthenticationFilter class (org.apache.pinot.core.auth.AuthenticationFilter), which handles URI validation for API endpoints.
Attackers can craft HTTP requests containing specially encoded sequences like %2e%2e/ or null-byte injections to bypass path normalization checks. For example:
This payload exploits insufficient sanitization in the shouldAllowUnauthenticatedAccess() method, tricking the filter into misclassifying restricted endpoints like /config or /tables as public routes.
The flaw violates CWE-707 (“Improper Neutralization of Control Elements”) and affects:
- Apache Pinot Broker: 0.12.0 through 1.2.0
- Apache Pinot Controller: 0.7.0 through 1.2.0
Successful exploitation grants attackers the same privileges as authenticated users, enabling access to internal APIs, Zookeeper configurations (via /appConfigs endpoint), and Groovy script execution interfaces.
Security analysts confirm this creates a direct pathway for remote code execution (RCE) through malicious query injections.
Operational Impact and Attack Surface
Apache Pinot’s architecture – designed for low-latency queries across petabyte-scale datasets – makes compromised instances high-value targets. Attackers could:
- Exfiltrate sensitive PII/PHI data from real-time analytics pipelines
- Manipulate financial reporting metrics through fraudulent record injection
- Disrupt IoT sensor analytics in manufacturing environments
- Pivot to integrated systems like Kafka or Hadoop clusters
Trend Micro’s Zero Day Initiative (ZDI), which tracked the flaw as ZDI-CAN-24001, confirms exploit code requires only basic HTTP manipulation skills.
Mitigation and Patch Deployment
Apache resolved the vulnerability in Pinot 1.3.0 through improved URI normalization using Java’s URI.normalize() method combined with regex-based path validation. Administrators must:
Post-upgrade, organizations should:
- Implement role-based access control (RBAC) via pinot.controller.access.protocols=http+rbac
- Disable Groovy scripting with pinot.server.instance.enable.groovy=false
- Deploy WAF rules blocking URIs containing .., %252e%252e, or %00 sequences
This incident highlights escalating risks in high-performance data infrastructure, where authentication logic often lags behind query optimization efforts.
It mirrors recent vulnerabilities in Elasticsearch (CVE-2024-35253) and MongoDB Atlas (CVE-2024-48721), underscoring the need for runtime CVE monitoring in distributed systems.
Security teams using Apache Pinot for real-time analytics should conduct forensic audits of access logs for patterns like HTTP 200 responses to /.. requests from unauthenticated IPs.
With 78% of data breaches originating from authentication bypass flaws according to IBM’s 2025 Threat Intelligence Index, this vulnerability serves as a critical reminder to prioritize input validation in distributed architectures.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
The post Apache Pinot Vulnerability Let Attackers Bypass Authentication appeared first on Cyber Security News.











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)























.webp?#)










_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)




































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)
































































































































.webp?#)

.webp?#)
