A Look At Chainlink VRF and Oasis Network's RNG Implementation - Onchain Randomness
When I was reading an article on Oasis Network RNG, immediately Chainlink VRF came to mind and I started to find relationships between the two and how to make best use of the tools out there. The last time I wrote a lottery contract I used Chainlink VRF but after dissecting Oasis Network RNG implementations I was amazed. As a developer building dApps that demand fairness, unpredictability, and cryptographic security, selecting the right random number generation (RNG) method is critical. Whether you're powering a lottery, generating unique NFTs, or assigning randomized game mechanics, randomness becomes a cornerstone for security and trust. This article provides a deep technical comparison between Chainlink’s Verifiable Random Function (VRF) and Oasis Network’s RNG implementation via Sapphire’s randomBytes precompile. Designed for researchers, smart contract developers, and protocol architects, this guide helps you make an informed decision when integrating RNG into your decentralized application. Why Randomness Is Critical in Blockchain Randomness enables decentralization to go beyond consensus, it introduces unpredictability in systems that would otherwise be fully deterministic. In blockchain, random number generation underpins: Fair games: Ensuring unpredictability in outcomes (e.g., dice rolls, loot boxes) NFT uniqueness: Assigning random traits to NFT drops Secure identity/authentication: Creating non-repeating key pairs or seeds Random governance selection: For leader election or jury mechanisms Without secure randomness, these systems are prone to manipulation, predictability, or even exploitation, undermining user trust and protocol integrity. Challenges of Onchain Randomness Blockchains are deterministic by design, every node must produce the same output for a given input. This ensures consensus but makes integrating randomness difficult. Some core challenges include: Predictability: Simple methods (e.g., block.timestamp or blockhash) are predictable and manipulable by miners or validators. Lack of entropy sources: Blockchains cannot access hardware sensors or external randomness without oracles or trusted execution environments (TEEs). Verifiability: Users and other smart contracts must trust that the randomness was generated fairly and without tampering. Secure, verifiable, and decentralized randomness requires advanced cryptographic systems like VRFs, commit-reveal, or TEE-backed entropy pools each with unique trade-offs. How Chainlink VRF Solves It Chainlink VRF is one of the most popular solutions for secure onchain randomness. It provides cryptographic proof that the randomness was not tampered with, even by the oracle node itself. Architecture Overview: A smart contract makes a randomness request to the Chainlink VRF Coordinator. The oracle node generates a random number and a proof using its secret key and the request’s seed. The VRF Coordinator verifies the proof on-chain before delivering the random output to the requesting contract. Key Features: Verifiability: Every random output comes with proof. Decentralization (partially): Though the oracle is offchain, its response is verified by smart contracts. Ease of use: Widely adopted with libraries available across major blockchains like Ethereum, Polygon, Arbitrum, etc. Common Use Cases: Chain-based gaming: Loot boxes, lotteries NFTs: Trait randomization Airdrops: Random selection of eligible addresses Chainlink VRF is trusted but introduces some latency and cost, as it depends on off-chain computation and interaction with the VRF Coordinator contract. How Oasis Does It Differently The Oasis Network, especially through its Sapphire confidential EVM runtime, brings a fundamentally different approach. Rather than using external oracles, Oasis leverages confidential computing (TEE) and private ephemeral entropy. Architecture Overview: Ephemeral Key Generation: Every epoch, Oasis generates short-lived keys inside the Key Manager runtime, a secure enclave. Per-block RNG: These keys produce block-level private entropy, which is never persisted and inaccessible to external actors. Verifiable Root RNG: Oasis processes this entropy through VRF algorithms using TupleHash, KMAC256, and cSHAKE to derive a unique root RNG per block. Per-transaction domain separation: With Merlin transcripts, Sapphire isolates each transaction’s RNG, ensuring fully private, unbiased, and non-replayable outputs. Developer Interface: The RNG is accessed through a simple Solidity call: bytes memory randomPad = Sapphire.randomBytes(32, ""); This function delivers high-entropy randomness without needing an external oracle or additional infrastructure. Privacy-first Design: All entropy is generated inside a Trusted Execution Environment (TEE). Only remotely attested runtimes can request and use this randomness. Ephemeral keys and
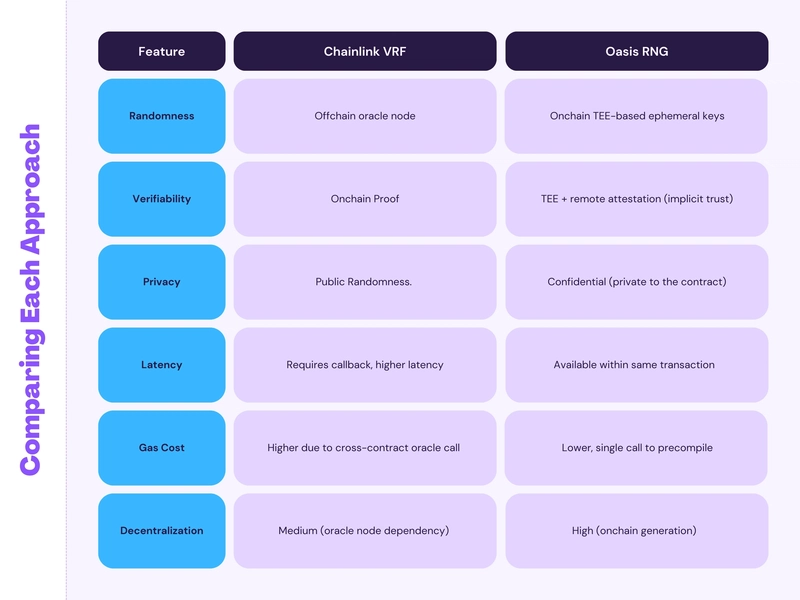
When I was reading an article on Oasis Network RNG, immediately Chainlink VRF came to mind and I started to find relationships between the two and how to make best use of the tools out there. The last time I wrote a lottery contract I used Chainlink VRF but after dissecting Oasis Network RNG implementations I was amazed. As a developer building dApps that demand fairness, unpredictability, and cryptographic security, selecting the right random number generation (RNG) method is critical. Whether you're powering a lottery, generating unique NFTs, or assigning randomized game mechanics, randomness becomes a cornerstone for security and trust.
This article provides a deep technical comparison between Chainlink’s Verifiable Random Function (VRF) and Oasis Network’s RNG implementation via Sapphire’s randomBytes precompile. Designed for researchers, smart contract developers, and protocol architects, this guide helps you make an informed decision when integrating RNG into your decentralized application.
Why Randomness Is Critical in Blockchain
Randomness enables decentralization to go beyond consensus, it introduces unpredictability in systems that would otherwise be fully deterministic. In blockchain, random number generation underpins:
- Fair games: Ensuring unpredictability in outcomes (e.g., dice rolls, loot boxes)
- NFT uniqueness: Assigning random traits to NFT drops
- Secure identity/authentication: Creating non-repeating key pairs or seeds
- Random governance selection: For leader election or jury mechanisms
Without secure randomness, these systems are prone to manipulation, predictability, or even exploitation, undermining user trust and protocol integrity.
Challenges of Onchain Randomness
Blockchains are deterministic by design, every node must produce the same output for a given input. This ensures consensus but makes integrating randomness difficult.
Some core challenges include:
- Predictability: Simple methods (e.g.,
block.timestamporblockhash) are predictable and manipulable by miners or validators. - Lack of entropy sources: Blockchains cannot access hardware sensors or external randomness without oracles or trusted execution environments (TEEs).
- Verifiability: Users and other smart contracts must trust that the randomness was generated fairly and without tampering.
Secure, verifiable, and decentralized randomness requires advanced cryptographic systems like VRFs, commit-reveal, or TEE-backed entropy pools each with unique trade-offs.
How Chainlink VRF Solves It
Chainlink VRF is one of the most popular solutions for secure onchain randomness. It provides cryptographic proof that the randomness was not tampered with, even by the oracle node itself.
Architecture Overview:
- A smart contract makes a randomness request to the Chainlink VRF Coordinator.
- The oracle node generates a random number and a proof using its secret key and the request’s seed.
- The VRF Coordinator verifies the proof on-chain before delivering the random output to the requesting contract.
Key Features:
- Verifiability: Every random output comes with proof.
- Decentralization (partially): Though the oracle is offchain, its response is verified by smart contracts.
- Ease of use: Widely adopted with libraries available across major blockchains like Ethereum, Polygon, Arbitrum, etc.
Common Use Cases:
- Chain-based gaming: Loot boxes, lotteries
- NFTs: Trait randomization
- Airdrops: Random selection of eligible addresses
Chainlink VRF is trusted but introduces some latency and cost, as it depends on off-chain computation and interaction with the VRF Coordinator contract.
How Oasis Does It Differently
The Oasis Network, especially through its Sapphire confidential EVM runtime, brings a fundamentally different approach. Rather than using external oracles, Oasis leverages confidential computing (TEE) and private ephemeral entropy.
Architecture Overview:
- Ephemeral Key Generation: Every epoch, Oasis generates short-lived keys inside the Key Manager runtime, a secure enclave.
- Per-block RNG: These keys produce block-level private entropy, which is never persisted and inaccessible to external actors.
- Verifiable Root RNG: Oasis processes this entropy through VRF algorithms using
TupleHash,KMAC256, andcSHAKEto derive a unique root RNG per block. - Per-transaction domain separation: With Merlin transcripts, Sapphire isolates each transaction’s RNG, ensuring fully private, unbiased, and non-replayable outputs.
Developer Interface:
The RNG is accessed through a simple Solidity call:
bytes memory randomPad = Sapphire.randomBytes(32, "");
This function delivers high-entropy randomness without needing an external oracle or additional infrastructure.
Privacy-first Design:
- All entropy is generated inside a Trusted Execution Environment (TEE).
- Only remotely attested runtimes can request and use this randomness.
- Ephemeral keys and domain separation ensure unpredictability and non-reusability.
Usages of Oasis RNG Implementation
Oasis’ RNG implementation unlocks several privacy-preserving use cases:
- Private gaming mechanics: Random rewards or states visible only to the player
- ZK + RNG applications: Secure generation of secrets or inputs for zero-knowledge circuits
- Secure key pair generation: For signing keys, session keys, or confidential tokens
- Randomized airdrops with hidden selection logic
- Decentralized lotteries that require tamperproof and private RNG
With a single precompile call, developers can focus on building their application logic without needing to manage randomness infrastructure or worry about third-party dependencies.
Conclusion
Choosing the right RNG mechanism depends on your application’s requirements—whether you prioritize verifiability, privacy, latency, or ease of use.
- Use Chainlink VRF if your app requires publicly verifiable randomness and you're operating on major chains like Ethereum or Polygon.
- Choose Oasis RNG (Sapphire) if your dApp demands confidentiality, low latency, and native integration within a privacy-preserving runtime.
As randomness becomes increasingly essential in blockchain-native applications, Oasis Network’s approach introduces a powerful, secure, and developer-friendly paradigm particularly for privacy-first and next-gen Web3 use cases.







































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)















































































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)



























![Mobile Legends: Bang Bang [MLBB] Free Redeem Codes April 2025](https://www.talkandroid.com/wp-content/uploads/2024/07/Screenshot_20240704-093036_Mobile-Legends-Bang-Bang.jpg)