5 Tricks to Secure your Docker Images
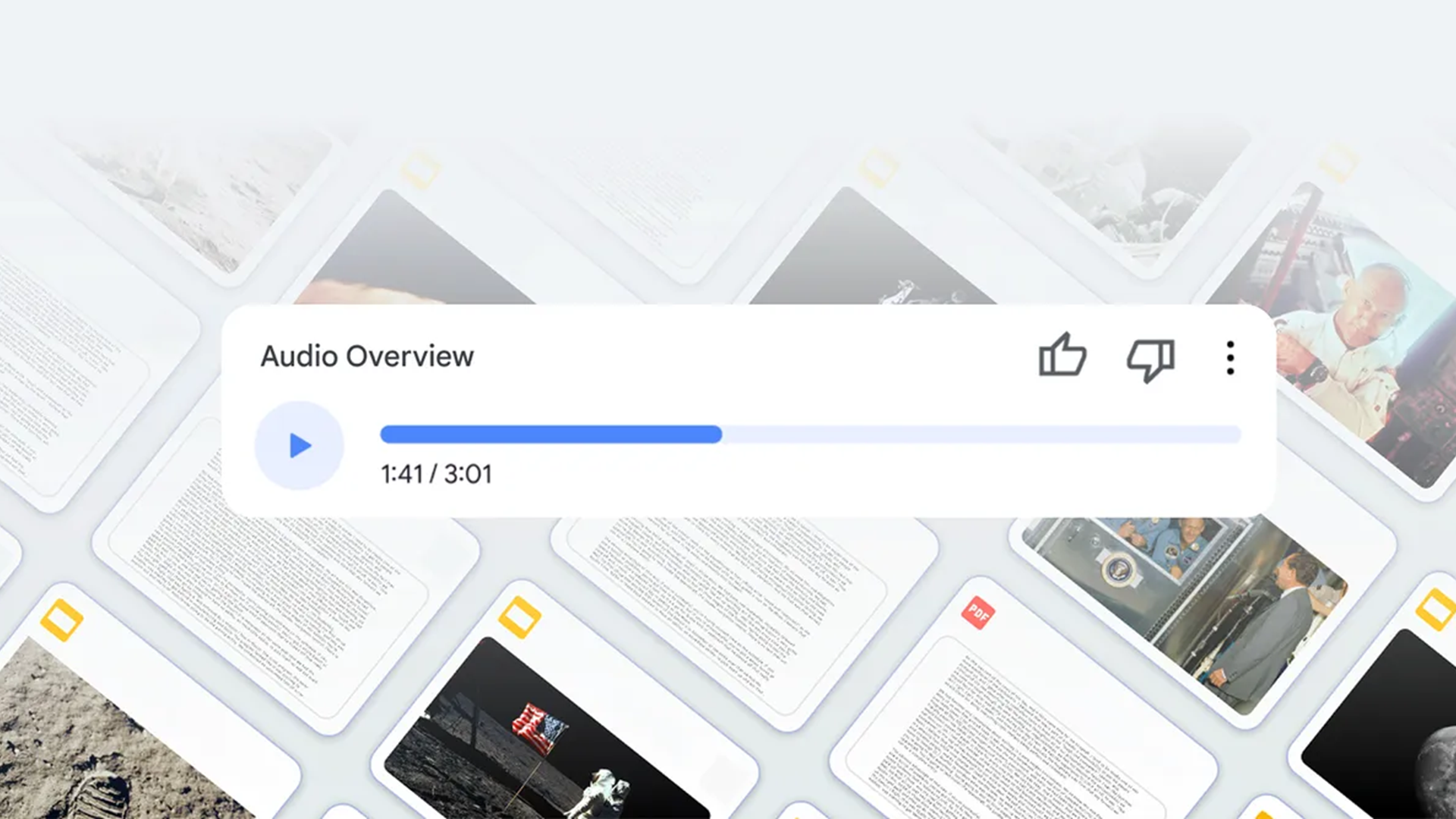
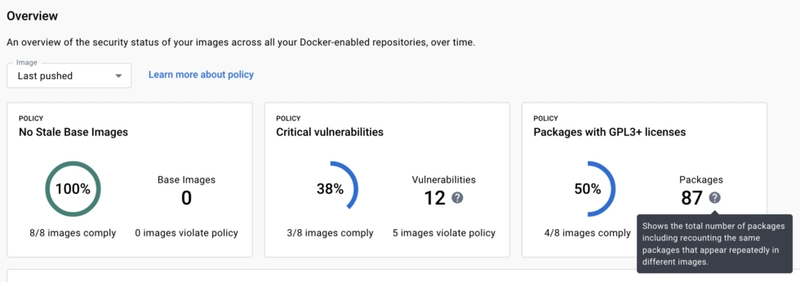
Docker images are central to modern application deployment, but poor security can expose them to unecessary risks. At sliplane.io, we deploy and handle thousands of Docker images every month and have identified a few common security pitfalls. Here are five easy ways to improve your Docker Image security! 1. Scan for Vulnerabilities with Docker Scout Regularly scanning your Docker images for vulnerabilities is a key security step. Docker Scout, integrated with Docker Desktop and CLI, identifies potential issues in your images before they become problems. To scan an image, run: docker scout quickview my-image Make it a habit to scan frequentl y— especially before deploying to production — and keep your base images up to date. This proactive approach helps catch issues early. There are also other alternatives to Docker Scout, but I think the ease of integration just makes this a no-brainer. 2. Use Minimal Images Minimal images improve security by reducing unnecessary components and thus reducing the attack surface. Lightweight bases like Alpine Linux limit potential vulnerabilities and, as a bonus, speed up builds due to their smaller size (win win!). Here’s a simple Node.js Dockerfile example: FROM node:18.12.1-slim WORKDIR /app COPY package*.json ./ RUN npm install --only=production COPY . . CMD ["node", "index.js"] Choose a slim base image, install only what’s required, and use multi-stage builds to exclude unneeded files. This keeps your images secure and efficient :) 3. Avoid Hardcoded Credentials Hardcoding credentials in a Dockerfile is a major security risk—if the image is compromised or accidentally shared, those secrets are exposed. Instead, use environment variables or secret management tools like Infisical or AWS Secrets Manager. Pass credentials at runtime with: docker run -e DATABASE_URL=your_database_url my-image This method is more secure and flexible. At sliplane.io, we see hardcoded credentials as the most frequent security mistake — don’t skip this one! 4. Run as Non-Root By default, Docker containers run as root, which can amplify damage if breached. Switching to a non-root user limits the impact of a compromise and is simple to implement. Add this to your Dockerfile: RUN useradd -m myuser USER myuser CMD ["myapp"] It’s a straightforward change with minimal downsides and a clear security benefit. 5. Use Rootless Mode Rootless mode runs the Docker engine as a non-root user, reducing its privileges on the host system. It requires extra setup—such as configuring user namespaces and installing tools like newuidmap—but offers a significant security boost. Check the official docs for setup details. Be aware that there are quite a few tradeoffs that might not make sense for you! Conclusion At sliplane.io, we focus on making your Docker deployments super easy and see a lot of preventable mistakes every day. These five tips will get you started on the never ending journey of security :) Have additional security tips? Share them in the comments! Cheers, Jonas, Co-founder @ Sliplane.io

Docker images are central to modern application deployment, but poor security can expose them to unecessary risks. At sliplane.io, we deploy and handle thousands of Docker images every month and have identified a few common security pitfalls. Here are five easy ways to improve your Docker Image security!
1. Scan for Vulnerabilities with Docker Scout
Regularly scanning your Docker images for vulnerabilities is a key security step. Docker Scout, integrated with Docker Desktop and CLI, identifies potential issues in your images before they become problems.
To scan an image, run:
docker scout quickview my-image
Make it a habit to scan frequentl y— especially before deploying to production — and keep your base images up to date. This proactive approach helps catch issues early. There are also other alternatives to Docker Scout, but I think the ease of integration just makes this a no-brainer.
2. Use Minimal Images
Minimal images improve security by reducing unnecessary components and thus reducing the attack surface. Lightweight bases like Alpine Linux limit potential vulnerabilities and, as a bonus, speed up builds due to their smaller size (win win!).
Here’s a simple Node.js Dockerfile example:
FROM node:18.12.1-slim
WORKDIR /app
COPY package*.json ./
RUN npm install --only=production
COPY . .
CMD ["node", "index.js"]
Choose a slim base image, install only what’s required, and use multi-stage builds to exclude unneeded files. This keeps your images secure and efficient :)
3. Avoid Hardcoded Credentials
Hardcoding credentials in a Dockerfile is a major security risk—if the image is compromised or accidentally shared, those secrets are exposed. Instead, use environment variables or secret management tools like Infisical or AWS Secrets Manager.
Pass credentials at runtime with:
docker run -e DATABASE_URL=your_database_url my-image
This method is more secure and flexible. At sliplane.io, we see hardcoded credentials as the most frequent security mistake — don’t skip this one!
4. Run as Non-Root
By default, Docker containers run as root, which can amplify damage if breached. Switching to a non-root user limits the impact of a compromise and is simple to implement.
Add this to your Dockerfile:
RUN useradd -m myuser
USER myuser
CMD ["myapp"]
It’s a straightforward change with minimal downsides and a clear security benefit.
5. Use Rootless Mode
Rootless mode runs the Docker engine as a non-root user, reducing its privileges on the host system. It requires extra setup—such as configuring user namespaces and installing tools like newuidmap—but offers a significant security boost.
Check the official docs for setup details. Be aware that there are quite a few tradeoffs that might not make sense for you!
Conclusion
At sliplane.io, we focus on making your Docker deployments super easy and see a lot of preventable mistakes every day. These five tips will get you started on the never ending journey of security :)
Have additional security tips? Share them in the comments!
Cheers,
Jonas, Co-founder @ Sliplane.io








































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)
































































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.jpg?#)
































_ArtemisDiana_Alamy.jpg?#)


 (1).webp?#)





































































-xl.jpg)










![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)