Verifiable Digital Credential Ecosystem: All You Need to Know
In an increasingly digitally shifting world, there is more need than ever before for secure, reliable, and user-owned identity solutions. That is where verifiable digital credentials come in—a revolutionary technology that is transforming how people and organizations demonstrate qualifications, identities, and attributes online. This article examines what verifiable credentials are, how they work, their advantages, and why they are at the heart of digital identity's future. What Are Verifiable Digital Credentials? Verifiable credentials (VCs) are digitally secured documents that are cryptographic equivalents of traditional credentials such as ID cards, diplomas, certificates, or licenses. In contrast to physical or even traditional digital credentials, VCs are tamper-evident, instantaneously verifiable, as well as privacy-preserving. Through them, individuals can share evidence of identification, competency, or affiliation with any receiver, anywhere, anytime, without requiring direct authentication from the original issuer. How Verifiable Credentials Work The verifiable credential ecosystem includes three central actors: Issuer:The issuing authority (e.g., university, employer, governmental body) that issues and digitally signs the credential. Holder:The person or organization receiving, storing, and controlling the credential, usually in an electronic wallet. Verifier: The person or entity that must confirm the validity of the credential. Once issued, a credential is cryptographically signed by the issuing organization. The owner can then produce this credential to a verifier, who verifies the digital signature, typically by means of DIDs and public keys residing in a blockchain or other distributed ledger, to prove its authority and integrity. Read More:What are Verifiable Credentials and Why You Must Know About Them Today Key benefits of Verifiable Credentials include: 1. Real-time, Worldwide Validation VCs are verified in just seconds, independent of geographical location, negating the lag associated with legacy verification processes. 2. Tamper-Proof & Secure Due to cryptography, VCs are extremely resistant to tampering or unauthorized amendment. They can be verified independently by anyone without communication with the issuer. 3. User Control & Privacy Holders are in complete control of their credentials and can select which information to disclose. It is possible, for instance, to validate age without divulging a complete birth date. 4. No Centralised Data Storage Personal information does not reside on the blockchain; cryptographic proofs or pointers are. This reduces privacy threats and increases user confidence. 5. Interoperability and Portability VCs are also stored in digital wallets and can be used across various platforms and services, which makes them highly portable and versatile. Use Cases for Verifiable Credentials Digital Identity Verification:Secure, reusable online IDs to access online services, government portals, or banks. Education: Secure, digitally signed diplomas, certificates, and transcripts that can be verified instantaneously by employers or other educational institutions. Professional Licenses: Documentation of credentials or memberships for doctors, engineers, or lawyers. Know Your Customer (KYC):Simplified banking, fintech, and cryptocurrency platform onboarding, minimizing fraud and compliance expenses. Verified evidence of activity in online or offline groups and activities. Role of Blockchain and Decentralized Identifiers One of the major innovations in verifiable credentials is decentralized identifiers (DIDs) and blockchain technology. DIDs are essentially globally unique, cryptographically verifiable identifiers independent of central registries. They facilitate secure, privacy-preserving interactions since verifiers can verify credential signatures with openly published public keys on a blockchain, without revealing personal information or depending upon a solitary authority. Blockchain's tamper-evident ledger guarantees transparency of credential issuance and revocation events. The credentials themselves are typically stored off-chain, in the wallet of their owner, in order to optimize privacy and reduce blockchain storage needs. Verifiable Credentials vs. NFTs Although both NFTs (non-fungible tokens) and VCs are digitally secured with cryptography, they are used for different purposes. NFTs are always kept on the blockchain and are generally used for collectibles and digital ownership. Self-contained, cryptographically signed documents that don't necessarily have to live on a blockchain, VCs are meant to be used for privacy and verifiable claims. Occasionally, an NFT will have embedded in it a verifiable credential in its data, but VCs are specifically intended to be used for secure, privacy-preserving identification and qualification verification. Challenges in Infrastruct
In an increasingly digitally shifting world, there is more need than ever before for secure, reliable, and user-owned identity solutions. That is where verifiable digital credentials come in—a revolutionary technology that is transforming how people and organizations demonstrate qualifications, identities, and attributes online. This article examines what verifiable credentials are, how they work, their advantages, and why they are at the heart of digital identity's future.
What Are Verifiable Digital Credentials?
Verifiable credentials (VCs) are digitally secured documents that are cryptographic equivalents of traditional credentials such as ID cards, diplomas, certificates, or licenses. In contrast to physical or even traditional digital credentials, VCs are tamper-evident, instantaneously verifiable, as well as privacy-preserving. Through them, individuals can share evidence of identification, competency, or affiliation with any receiver, anywhere, anytime, without requiring direct authentication from the original issuer.
How Verifiable Credentials Work
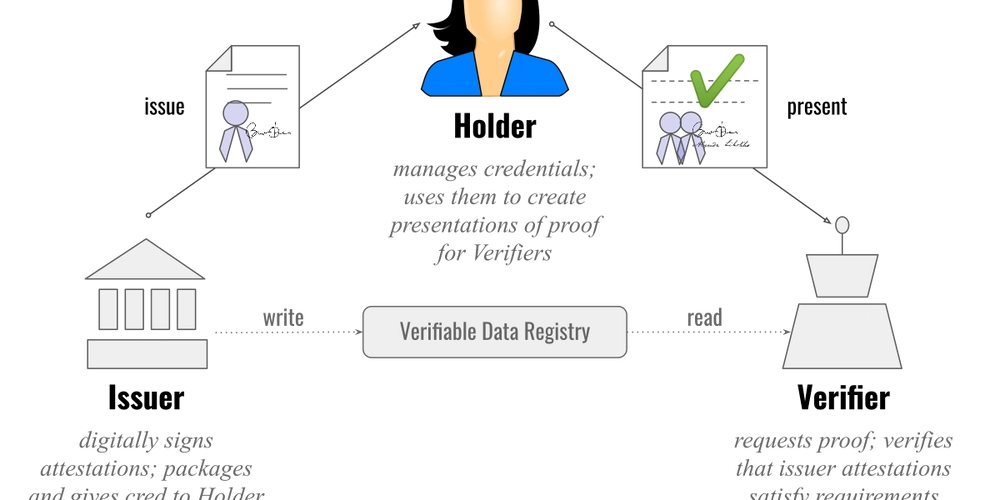
The verifiable credential ecosystem includes three central actors:
Issuer:The issuing authority (e.g., university, employer, governmental body) that issues and digitally signs the credential.
Holder:The person or organization receiving, storing, and controlling the credential, usually in an electronic wallet.
Verifier: The person or entity that must confirm the validity of the credential.
Once issued, a credential is cryptographically signed by the issuing organization. The owner can then produce this credential to a verifier, who verifies the digital signature, typically by means of DIDs and public keys residing in a blockchain or other distributed ledger, to prove its authority and integrity.
Read More:What are Verifiable Credentials and Why You Must Know About Them Today
Key benefits of Verifiable Credentials include:
1. Real-time, Worldwide Validation
VCs are verified in just seconds, independent of geographical location, negating the lag associated with legacy verification processes.
2. Tamper-Proof & Secure
Due to cryptography, VCs are extremely resistant to tampering or unauthorized amendment. They can be verified independently by anyone without communication with the issuer.
3. User Control & Privacy
Holders are in complete control of their credentials and can select which information to disclose. It is possible, for instance, to validate age without divulging a complete birth date.
4. No Centralised Data Storage
Personal information does not reside on the blockchain; cryptographic proofs or pointers are. This reduces privacy threats and increases user confidence.
5. Interoperability and Portability
VCs are also stored in digital wallets and can be used across various platforms and services, which makes them highly portable and versatile.
Use Cases for Verifiable Credentials
Digital Identity Verification:Secure, reusable online IDs to access online services, government portals, or banks.
Education: Secure, digitally signed diplomas, certificates, and transcripts that can be verified instantaneously by employers or other educational institutions.
Professional Licenses: Documentation of credentials or memberships for doctors, engineers, or lawyers.
Know Your Customer (KYC):Simplified banking, fintech, and cryptocurrency platform onboarding, minimizing fraud and compliance expenses.
Verified evidence of activity in online or offline groups and activities.
Role of Blockchain and Decentralized Identifiers
One of the major innovations in verifiable credentials is decentralized identifiers (DIDs) and blockchain technology. DIDs are essentially globally unique, cryptographically verifiable identifiers independent of central registries. They facilitate secure, privacy-preserving interactions since verifiers can verify credential signatures with openly published public keys on a blockchain, without revealing personal information or depending upon a solitary authority.
Blockchain's tamper-evident ledger guarantees transparency of credential issuance and revocation events. The credentials themselves are typically stored off-chain, in the wallet of their owner, in order to optimize privacy and reduce blockchain storage needs.
Verifiable Credentials vs. NFTs
Although both NFTs (non-fungible tokens) and VCs are digitally secured with cryptography, they are used for different purposes. NFTs are always kept on the blockchain and are generally used for collectibles and digital ownership. Self-contained, cryptographically signed documents that don't necessarily have to live on a blockchain, VCs are meant to be used for privacy and verifiable claims. Occasionally, an NFT will have embedded in it a verifiable credential in its data, but VCs are specifically intended to be used for secure, privacy-preserving identification and qualification verification.
Challenges in Infrastructure Development
In spite of their promise, their use is hindered by various challenges:
Interoperability: Making sure that credentials are accepted and recognized by various platforms and jurisdictions.
Standardisation: Organizations such as the W3C continue to work towards developing universal norms for VCs, but adoption across the globe is still underway.
User Experience: Making wallet handling and credential exchange easier for non-tech-savvy customers continues to be paramount.
Regulatory Compliance: Compliance with privacy laws and data protection regulations is imperative to achieve widespread acceptance.
Conclusion
Verifiable credentials have the potential to become the foundation of digital identity over the years. Providing secure, user-centric, and instantly verifiable identification, credentials, and other forms of credentials, they solve many of the problems associated with traditional credential schemes. With blockchain technology advancing along with decentralized identity technologies, along with progress being made in standards, the system of verifiable credentials will become instrumental in creating a more reliable, efficient, and privacy-respecting online world.





























![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiOWn65wd33dg2uO99NrtKbpYLfcepwOLidQDMls0HXKlA91k6HURluRA4WXgJRAZldEe1VReMQZyyYt1PgnoAn5JPpILsWlXIzmrBSs_TBoyPwO7hZrWouBg2-O3mdeoeSGY-l9_bsZB7vbpKjTSvG93zNytjxgTaMPqo9iq9Z5pGa05CJOs9uXpwHFT4/s1600/ai-cyber.jpg?#)










































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)



























































































































![[FREE EBOOKS] Machine Learning Hero, AI-Assisted Programming for Web and Machine Learning & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)








































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)







































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)






























































































![What’s new in Android’s April 2025 Google System Updates [U: 4/18]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)