Understanding Two-Factor Authentication: What Every Software Engineer Should Know
We've all used 2FA. But as a software engineer, do you know how it works under the hood? Like we all know, two-factor authentication is a security method that requires two forms of identity before giving someone access to an account. The first factor is what you know. That’s your password. The second factor is either what you have or what you are. What you have can be your phone or a security key. What you are can be your fingerprint or your face. Here’s the flow: You enter your email or username and password, if the details are correct, the second layer kicks in. That could be an OTP sent to your phone, a code from an authenticator app, or a biometric check. Once you complete the second step, access is granted. If not, you’re blocked. As a dev, this is how you can implement 2FA: Start by storing a shared secret between your app and the user’s authenticator app. You can use libraries. When the user logs in successfully, generate a time-based one-time password using the shared secret and the current time. Send a prompt to the user to enter the 2FA code. Once they enter the code, verify it by comparing it with the one your server generates in real-time using the same secret and time. If it matches, proceed. If not, reject access. Avoid using SMS-based 2FA. It’s weak and vulnerable to SIM swap attacks. Go with TOTP or physical keys. Knowing how 2FA works helps you build more secure products. And if you're shipping anything that handles sensitive data, you shouldn't treat 2FA like an optional feature.
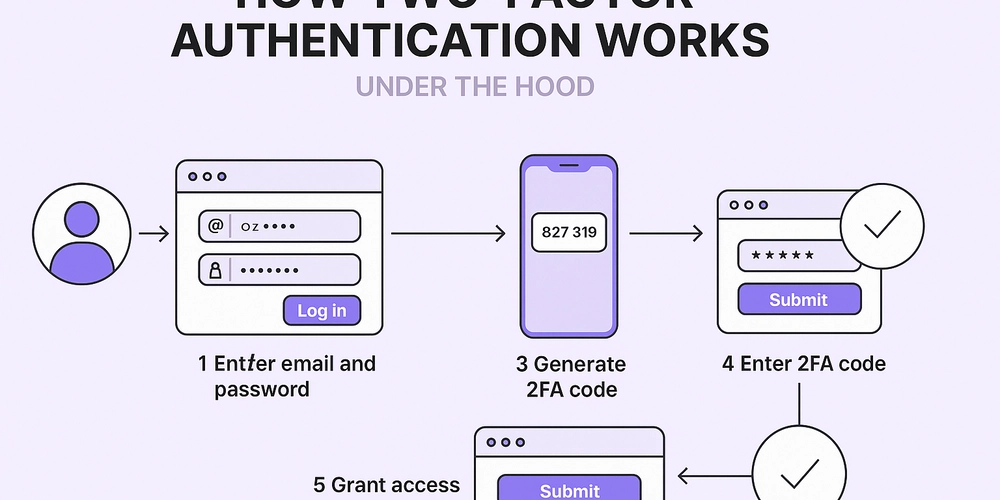
We've all used 2FA. But as a software engineer, do you know how it works under the hood?
Like we all know, two-factor authentication is a security method that requires two forms of identity before giving someone access to an account.
The first factor is what you know. That’s your password.
The second factor is either what you have or what you are. What you have can be your phone or a security key. What you are can be your fingerprint or your face.
Here’s the flow:
You enter your email or username and password, if the details are correct, the second layer kicks in. That could be an OTP sent to your phone, a code from an authenticator app, or a biometric check.
Once you complete the second step, access is granted. If not, you’re blocked.
As a dev, this is how you can implement 2FA:
Start by storing a shared secret between your app and the user’s authenticator app. You can use libraries.
When the user logs in successfully, generate a time-based one-time password using the shared secret and the current time.
Send a prompt to the user to enter the 2FA code.
Once they enter the code, verify it by comparing it with the one your server generates in real-time using the same secret and time.
If it matches, proceed. If not, reject access.
Avoid using SMS-based 2FA. It’s weak and vulnerable to SIM swap attacks. Go with TOTP or physical keys.
Knowing how 2FA works helps you build more secure products.
And if you're shipping anything that handles sensitive data, you shouldn't treat 2FA like an optional feature.
































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




















































































































_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





 CISO’s Core Focus.webp?#)




































































































![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)