Understanding `sudo`: The Essential Tool for Linux Administration
Introduction If you’ve been using Linux for any amount of time, you’ve likely encountered the sudo command. This simple yet powerful tool allows users to execute commands with elevated privileges, making it an essential component of system administration. One of the most well-known references to sudo comes from an XKCD comic: Source: XKCD While humorous, this comic highlights the power of sudo—a command that grants a user superuser privileges, much like the “Run as Administrator” function in Windows. The Evolution of sudo The concept of sudo dates back to the early 1980s when Robert Coggeshall and Cliff Spenser developed its initial implementation. Between 1986 and 1993, the University of Colorado Boulder made substantial modifications to the tool. Since 1994, Todd C. Miller, an OpenBSD developer, has maintained sudo, ensuring its continued security and usability. Before sudo was widely used, Linux users had to switch to the root account using su (or su - to load the root environment) to perform administrative tasks. This practice posed significant security risks, such as leaving systems vulnerable to unauthorized access if a user remained logged in as root. With sudo, users can execute privileged commands without permanently logging in as the root user, reducing security risks and enhancing system stability. How sudo Works sudo provides users with temporary administrative privileges based on predefined permissions. When a user executes a command with sudo, they are prompted to enter their password. If authenticated, the command runs with elevated privileges. For example: sudo apt-get update Once authenticated, a user can run additional sudo commands for a short period (default is five minutes) without needing to re-enter their password. Managing User Permissions By default, not all Linux distributions grant sudo access to new users. Instead, administrators must manually assign users to the appropriate group. Adding a User to the sudo Group For Debian and Ubuntu-based distributions, users need to be added to the sudo group: sudo usermod -aG sudo username On Fedora, CentOS, and RHEL-based distributions, users should be added to the wheel group: sudo usermod -aG wheel username After running this command, the user must log out and log back in for the changes to take effect. Understanding the sudoers File The sudoers file (/etc/sudoers) controls sudo permissions and must be edited with caution. Modifications should always be made using the visudo command, which prevents syntax errors that could lock users out of administrative access. To open the sudoers file: sudo visudo Breaking Down a sudoers Entry A typical entry in the sudoers file looks like this: root ALL=(ALL) ALL Each ALL represents: The rule applies to all hosts. The user can execute commands as any other user. The user can execute commands as any group. The rule applies to all commands. Creating Custom User Permissions Instead of granting full root privileges, administrators can assign specific commands to designated users or groups. For instance, to allow specific users (olivia, camille, anton, and clara) to only run apt-get update and apt-get upgrade, create a command alias: Cmnd_Alias APT_CMDS = /usr/bin/apt-get update, /usr/bin/apt-get upgrade User_Alias LIMITED_USERS = olivia, camille, anton, clara LIMITED_USERS ALL=(ALL) NOPASSWD: APT_CMDS This configuration ensures that these users can execute only the defined commands without entering a password. Best Practices for Using sudo To maintain a secure and well-managed system, follow these best practices: Avoid Logging in as Root: Always use sudo instead of su to minimize security risks. Grant Minimal Permissions: Only assign necessary permissions to prevent unauthorized access. Monitor sudo Usage: Use logs (/var/log/auth.log on Debian/Ubuntu, /var/log/secure on RHEL/Fedora) to track sudo activity. Use sudo Timeouts Wisely: The default five-minute timeout can be adjusted in the sudoers file for added security. Conclusion The sudo command is a critical tool for Linux administration, offering a balance between security and usability. By properly configuring sudo, administrators can enhance system security while providing users with the necessary privileges to perform their tasks efficiently. For more in-depth information, refer to the official sudo documentation or the man pages: man sudo

Introduction
If you’ve been using Linux for any amount of time, you’ve likely encountered the sudo command. This simple yet powerful tool allows users to execute commands with elevated privileges, making it an essential component of system administration.
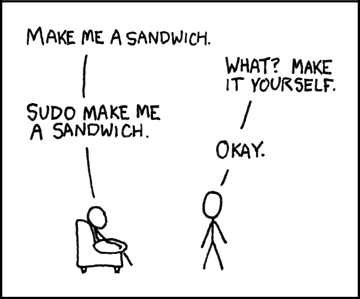
One of the most well-known references to sudo comes from an XKCD comic:
Source: XKCD
While humorous, this comic highlights the power of sudo—a command that grants a user superuser privileges, much like the “Run as Administrator” function in Windows.
The Evolution of sudo
The concept of sudo dates back to the early 1980s when Robert Coggeshall and Cliff Spenser developed its initial implementation. Between 1986 and 1993, the University of Colorado Boulder made substantial modifications to the tool. Since 1994, Todd C. Miller, an OpenBSD developer, has maintained sudo, ensuring its continued security and usability.
Before sudo was widely used, Linux users had to switch to the root account using su (or su - to load the root environment) to perform administrative tasks. This practice posed significant security risks, such as leaving systems vulnerable to unauthorized access if a user remained logged in as root.
With sudo, users can execute privileged commands without permanently logging in as the root user, reducing security risks and enhancing system stability.
How sudo Works
sudo provides users with temporary administrative privileges based on predefined permissions. When a user executes a command with sudo, they are prompted to enter their password. If authenticated, the command runs with elevated privileges.
For example:
sudo apt-get update
Once authenticated, a user can run additional sudo commands for a short period (default is five minutes) without needing to re-enter their password.
Managing User Permissions
By default, not all Linux distributions grant sudo access to new users. Instead, administrators must manually assign users to the appropriate group.
Adding a User to the sudo Group
For Debian and Ubuntu-based distributions, users need to be added to the sudo group:
sudo usermod -aG sudo username
On Fedora, CentOS, and RHEL-based distributions, users should be added to the wheel group:
sudo usermod -aG wheel username
After running this command, the user must log out and log back in for the changes to take effect.
Understanding the sudoers File
The sudoers file (/etc/sudoers) controls sudo permissions and must be edited with caution. Modifications should always be made using the visudo command, which prevents syntax errors that could lock users out of administrative access.
To open the sudoers file:
sudo visudo
Breaking Down a sudoers Entry
A typical entry in the sudoers file looks like this:
root ALL=(ALL) ALL
Each ALL represents:
- The rule applies to all hosts.
- The user can execute commands as any other user.
- The user can execute commands as any group.
- The rule applies to all commands.
Creating Custom User Permissions
Instead of granting full root privileges, administrators can assign specific commands to designated users or groups.
For instance, to allow specific users (olivia, camille, anton, and clara) to only run apt-get update and apt-get upgrade, create a command alias:
Cmnd_Alias APT_CMDS = /usr/bin/apt-get update, /usr/bin/apt-get upgrade
User_Alias LIMITED_USERS = olivia, camille, anton, clara
LIMITED_USERS ALL=(ALL) NOPASSWD: APT_CMDS
This configuration ensures that these users can execute only the defined commands without entering a password.
Best Practices for Using sudo
To maintain a secure and well-managed system, follow these best practices:
-
Avoid Logging in as Root: Always use
sudoinstead ofsuto minimize security risks. - Grant Minimal Permissions: Only assign necessary permissions to prevent unauthorized access.
-
Monitor
sudoUsage: Use logs (/var/log/auth.logon Debian/Ubuntu,/var/log/secureon RHEL/Fedora) to tracksudoactivity. -
Use
sudoTimeouts Wisely: The default five-minute timeout can be adjusted in thesudoersfile for added security.
Conclusion
The sudo command is a critical tool for Linux administration, offering a balance between security and usability. By properly configuring sudo, administrators can enhance system security while providing users with the necessary privileges to perform their tasks efficiently.
For more in-depth information, refer to the official sudo documentation or the man pages:
man sudo











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)




























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)

































_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)





































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)