Understanding AWS Shared Responsibility and Security Principles
Understanding AWS Shared Responsibility and Security Principles Amazon Web Services (AWS) is one of the most widely used cloud platforms, offering a robust infrastructure for businesses to build, deploy, and scale applications. However, with great power comes great responsibility, especially when it comes to security. AWS operates on a shared responsibility model, which divides security responsibilities between AWS and its customers. This article will explore the AWS shared responsibility model, the security pillar of the AWS Well-Architected Framework, design principles for security, and the role of AWS Identity and Access Management (IAM) in securing cloud resources. AWS Shared Responsibility Model The AWS shared responsibility model is a foundational concept in cloud security. It clearly defines the division of security responsibilities between AWS and its customers: AWS is responsible for the security of the cloud: This includes the physical security of data centers, the infrastructure (hardware, software, networking, and facilities) that runs AWS services, and the global infrastructure that supports AWS regions and availability zones. Customers are responsible for security in the cloud: This includes securing their data, applications, operating systems, network configurations, and access management. Customers must also ensure compliance with industry standards and regulations. This model ensures that AWS manages the underlying infrastructure, while customers have control over their data and how they configure their cloud environment. Security as a Pillar of the AWS Well-Architected Framework The AWS Well-Architected Framework is a set of best practices designed to help customers build secure, high-performing, resilient, and efficient infrastructure. Security is one of the six pillars of this framework, alongside operational excellence, reliability, performance efficiency, cost optimization, and sustainability. Design Principles for the Security Pillar To build a secure cloud environment, AWS recommends the following design principles: Implement a Strong Identity Foundation: Use AWS Identity and Access Management (IAM) to control access to resources. Ensure that users and applications have the minimum permissions necessary to perform their tasks (principle of least privilege). Protect Data in Transit and at Rest: Encrypt data both when it is being transferred (in transit) and when it is stored (at rest). This ensures privacy and prevents unauthorized access. Apply Security at All Layers: Security should be implemented at every layer of your architecture, including the network, application, and data layers. Keep People Away from Data: Limit human access to sensitive data. Use automation and tools to reduce the risk of human error or malicious activity. Maintain Traceability: Enable logging and monitoring to track access and changes to your resources. This helps in detecting and responding to security incidents. Prepare for Security Events: Have a well-defined incident response plan in place. Regularly test and update the plan to ensure readiness. Automate Security Best Practices: Use automation to enforce security policies, such as automatically applying patches or rotating credentials. AWS IAM: Authentication and Authorization AWS Identity and Access Management (IAM) is a core service that helps customers manage access to their AWS resources. IAM controls both authentication and authorization: Authentication: Determines who is requesting access to AWS resources. This involves verifying the identity of the requester, which could be a person or an application, using credentials such as usernames, passwords, or access keys. Authorization: Determines what the authenticated user or application is allowed to do. This involves defining permissions through policies, which specify whether a request should be allowed or denied. IAM Terminology IAM Resources: Objects stored in IAM, such as users, groups, roles, policies, and identity providers. IAM Entities: Resources used for authentication, such as users and roles. IAM Identities: Resources that can be authorized to perform actions, such as users, groups, or roles. Principal: A person or application that can sign in and make requests to AWS. IAM Credentials for Authentication Different actions require different credentials: Action Credentials Needed Sign in to AWS Management Console Username and password Run commands from AWS CLI AWS Access Key Make programmatic calls to AWS AWS Access Key An access key consists of an access key ID and a secret key, which are used to authenticate programmatic requests. IAM Policies and Permissions IAM policies are JSON documents that define permissions. There are two types of policies: Identity-Based Policies: Attached to IAM users, groups, or roles. These policies specify what actions the id
Understanding AWS Shared Responsibility and Security Principles
Amazon Web Services (AWS) is one of the most widely used cloud platforms, offering a robust infrastructure for businesses to build, deploy, and scale applications. However, with great power comes great responsibility, especially when it comes to security. AWS operates on a shared responsibility model, which divides security responsibilities between AWS and its customers. This article will explore the AWS shared responsibility model, the security pillar of the AWS Well-Architected Framework, design principles for security, and the role of AWS Identity and Access Management (IAM) in securing cloud resources.
AWS Shared Responsibility Model
The AWS shared responsibility model is a foundational concept in cloud security. It clearly defines the division of security responsibilities between AWS and its customers:
AWS is responsible for the security of the cloud: This includes the physical security of data centers, the infrastructure (hardware, software, networking, and facilities) that runs AWS services, and the global infrastructure that supports AWS regions and availability zones.
Customers are responsible for security in the cloud: This includes securing their data, applications, operating systems, network configurations, and access management. Customers must also ensure compliance with industry standards and regulations.
This model ensures that AWS manages the underlying infrastructure, while customers have control over their data and how they configure their cloud environment.
Security as a Pillar of the AWS Well-Architected Framework
The AWS Well-Architected Framework is a set of best practices designed to help customers build secure, high-performing, resilient, and efficient infrastructure. Security is one of the six pillars of this framework, alongside operational excellence, reliability, performance efficiency, cost optimization, and sustainability.
Design Principles for the Security Pillar
To build a secure cloud environment, AWS recommends the following design principles:
Implement a Strong Identity Foundation: Use AWS Identity and Access Management (IAM) to control access to resources. Ensure that users and applications have the minimum permissions necessary to perform their tasks (principle of least privilege).
Protect Data in Transit and at Rest: Encrypt data both when it is being transferred (in transit) and when it is stored (at rest). This ensures privacy and prevents unauthorized access.
Apply Security at All Layers: Security should be implemented at every layer of your architecture, including the network, application, and data layers.
Keep People Away from Data: Limit human access to sensitive data. Use automation and tools to reduce the risk of human error or malicious activity.
Maintain Traceability: Enable logging and monitoring to track access and changes to your resources. This helps in detecting and responding to security incidents.
Prepare for Security Events: Have a well-defined incident response plan in place. Regularly test and update the plan to ensure readiness.
Automate Security Best Practices: Use automation to enforce security policies, such as automatically applying patches or rotating credentials.
AWS IAM: Authentication and Authorization
AWS Identity and Access Management (IAM) is a core service that helps customers manage access to their AWS resources. IAM controls both authentication and authorization:
Authentication: Determines who is requesting access to AWS resources. This involves verifying the identity of the requester, which could be a person or an application, using credentials such as usernames, passwords, or access keys.
Authorization: Determines what the authenticated user or application is allowed to do. This involves defining permissions through policies, which specify whether a request should be allowed or denied.
IAM Terminology
- IAM Resources: Objects stored in IAM, such as users, groups, roles, policies, and identity providers.
- IAM Entities: Resources used for authentication, such as users and roles.
- IAM Identities: Resources that can be authorized to perform actions, such as users, groups, or roles.
- Principal: A person or application that can sign in and make requests to AWS.
IAM Credentials for Authentication
Different actions require different credentials:
| Action | Credentials Needed |
|---|---|
| Sign in to AWS Management Console | Username and password |
| Run commands from AWS CLI | AWS Access Key |
| Make programmatic calls to AWS | AWS Access Key |
An access key consists of an access key ID and a secret key, which are used to authenticate programmatic requests.
IAM Policies and Permissions
IAM policies are JSON documents that define permissions. There are two types of policies:
- Identity-Based Policies: Attached to IAM users, groups, or roles. These policies specify what actions the identity can perform.
- Resource-Based Policies: Attached to AWS resources (e.g., S3 buckets). These policies specify who can access the resource and what actions they can perform.
The principle of least privilege is a best practice that involves granting only the minimum permissions necessary to perform a task. This reduces the risk of accidental or malicious actions.
IAM Policy Structure: Effect, Statement, and More
IAM policies are written in JSON format and consist of several key components:
-
Effect: Specifies whether the policy allows or denies access. The two possible values are:
-
"Allow": Grants permission for the specified actions. -
"Deny": Explicitly denies permission for the specified actions.
-
Action: Defines the specific AWS API actions that the policy applies to. For example,
"s3:GetObject"allows reading an object from an S3 bucket.Resource: Specifies the AWS resource(s) to which the policy applies. Resources are identified using Amazon Resource Names (ARNs). For example,
"arn:aws:s3:::example-bucket/*"refers to all objects in an S3 bucket namedexample-bucket.Condition (Optional): Adds additional constraints to the policy. Conditions are based on key-value pairs and can include factors like IP address, time of day, or whether the request is encrypted.
Example IAM Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::example-bucket/*",
"Condition": {
"IpAddress": {
"aws:SourceIp": "192.0.2.0/24"
}
}
}
]
}
In this example:
- The Effect is
"Allow", meaning the policy grants permission. - The Action is
"s3:GetObject", allowing the user to read objects from an S3 bucket. - The Resource is
"arn:aws:s3:::example-bucket/*", specifying that the policy applies to all objects in theexample-bucket. - The Condition restricts access to requests originating from the IP range
192.0.2.0/24.
Encryption for Data Protection
Encryption is a critical tool for protecting data in transit and at rest:
Data in Transit: Encrypting data in transit ensures privacy by securing the communication channel. This is typically done using cryptographic protocols like TLS (Transport Layer Security).
-
Data at Rest: Encrypting data at rest involves encrypting files before they are stored. There are two main approaches:
- Client-Side Encryption: Data is encrypted on the client side before being sent to the cloud. The data remains encrypted while stored in the cloud.
- Server-Side Encryption: Data is encrypted by the cloud service before being stored. For example, Amazon S3 provides server-side encryption, where data is encrypted at the object level as it is written to disk and decrypted when accessed.
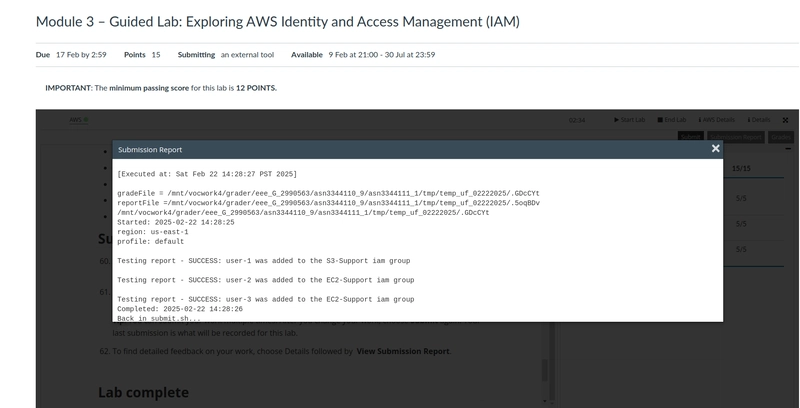
First Lab Test Result
Conclusion
Security is a shared responsibility in the AWS cloud. While AWS ensures the security of the cloud infrastructure, customers must take responsibility for securing their data and applications. By following the design principles of the AWS Well-Architected Framework, leveraging IAM for access control, and using encryption to protect data, customers can build a secure and resilient cloud environment. Understanding these concepts is essential for anyone working with AWS, whether you're a developer, architect, or security professional.










































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
















































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





































![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)