Special Permissions in Linux (SUID, SGID & Sticky Bit)
In Linux environments, standard file permissions can fall short, especially when multiple users need to share files or run important commands. That’s where special permissions like SUID, SGID, and the Sticky Bit come in. They offer advanced control over file execution and directory behavior, making them essential for secure, collaborative systems. Table of Contents What Are Special Permissions? 1. SUID (Set User ID) 2. SGID (Set Group ID) 3. Sticky Bit Special Permissions: Numeric Mode Conclusion Let's Connect on LinkedIn What Are Special Permissions? There are three types of special permissions in Linux: SUID (Set User ID) SGID (Set Group ID) Sticky Bit These are mainly applied to executable files and directories to control execution rights, inheritance, and deletion permissions in shared environments. 1. SUID (Set User ID) When applied to an executable file, SUID allows any user to execute the file with the permissions of the file owner. Use Case: The passwd command is owned by root, but regular users must use it to change their passwords. ls -l /usr/bin/passwd You’ll see: -rwsr-xr-x 1 root root 54256 Apr 23 09:32 /usr/bin/passwd The s in the user/owner execute position represents the SUID bit. To set SUID: chmod u+s file_name To remove: chmod u-s file_name 2. SGID (Set Group ID) SGID has two behaviors: On files: Runs the file with the group owner's permissions. On directories: Ensures all new files/subdirectories inherit the group of the parent directory—not the user’s default group. Use Case: In a shared group directory like /project, you want every file created to belong to the same group. chmod g+s /project ls -ld /project Output: drwxr-sr-x 2 devs devs 4096 Apr 23 09:32 /project The s in the group execute position means SGID is active. 3. Sticky Bit Used only on directories, the Sticky Bit prevents users from deleting files they don't own—even if they have write access to the directory. Use Case: On shared directories like /tmp, you don’t want users accidentally or maliciously deleting others’ files. chmod o+t /tmp ls -ld /tmp Output: drwxrwxrwt 10 root root 4096 Apr 23 09:32 /tmp The t at the end? That’s the Sticky Bit. Special Permissions: Numeric Mode You can set SUID, SGID, and Sticky Bit using numeric values: SUID = 4 SGID = 2 Sticky Bit = 1 Example: chmod 6755 script.sh 6 (4 + 2) = SUID + SGID 755 = Regular permissions Special permissions in Linux provide fine-grained control for shared environments and collaborative workflows. They're vital tools for sysadmins and DevOps engineers. But—use with caution. Setting SUID or SGID on sensitive files can expose your system to security risks if misconfigured. Keep your permissions smart, not sloppy. Let’s connect on LinkedIn (https://www.linkedin.com/in/chiamaka-chielo?utm_source=share&utm_campaign=share_via&utm_content=profile&utm_medium=android_app) As I automate my journey into RHCE and Ansible, I’d love to connect with fellow learners and professionals. Feel free to reach out and join me as I share tips, resources, and insights throughout this 30-day challenge. cloudwhistler #30daysLinuxchallenge Linux #ACL #FilePermissions #CloudWhistler #30DaysLinux

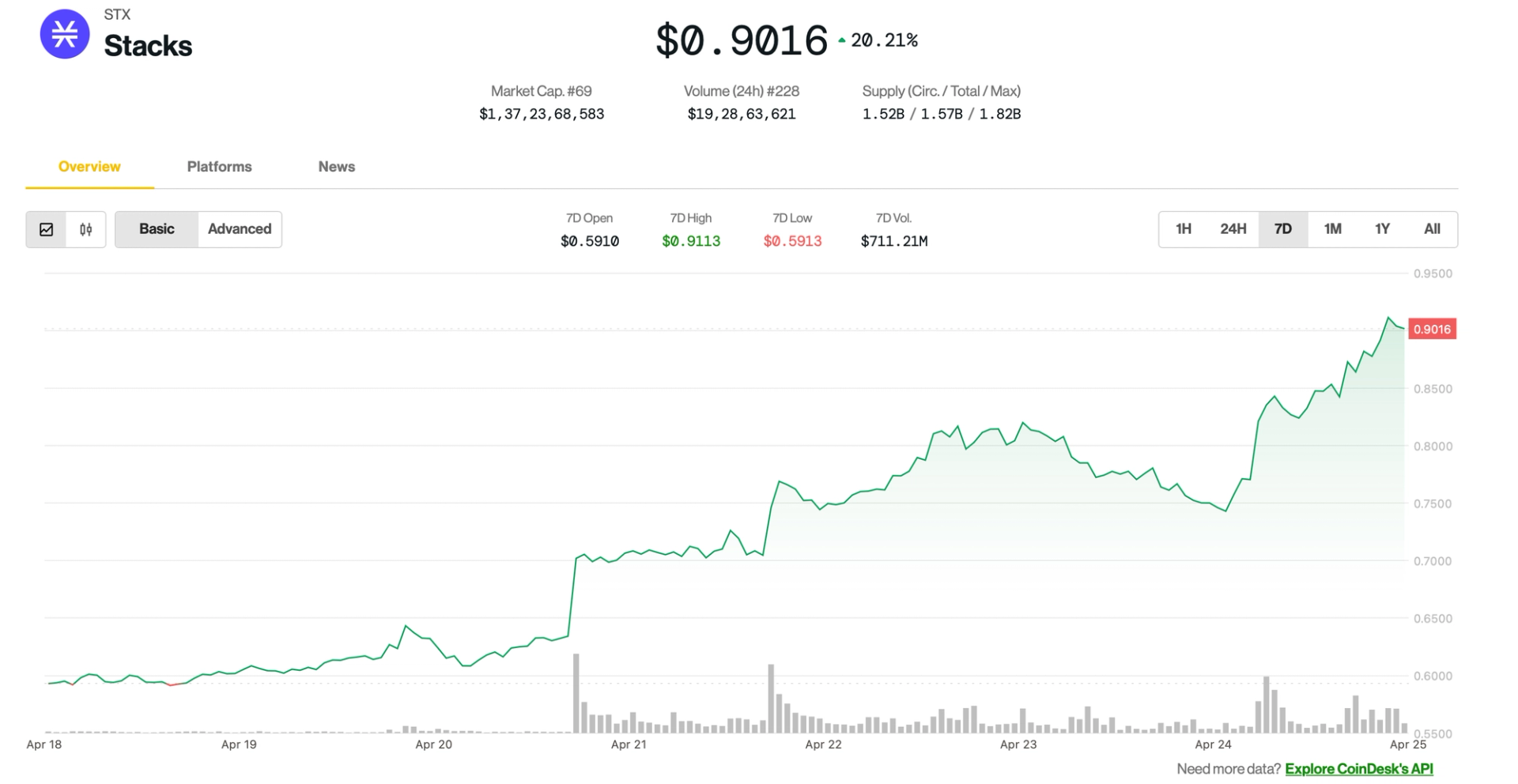
In Linux environments, standard file permissions can fall short, especially when multiple users need to share files or run important commands. That’s where special permissions like SUID, SGID, and the Sticky Bit come in.
They offer advanced control over file execution and directory behavior, making them essential for secure, collaborative systems.
Table of Contents
- What Are Special Permissions?
- 1. SUID (Set User ID)
- 2. SGID (Set Group ID)
- 3. Sticky Bit
- Special Permissions: Numeric Mode
- Conclusion
- Let's Connect on LinkedIn
What Are Special Permissions?
There are three types of special permissions in Linux:
SUID (Set User ID)
SGID (Set Group ID)
Sticky Bit
These are mainly applied to executable files and directories to control execution rights, inheritance, and deletion permissions in shared environments.
1. SUID (Set User ID)
When applied to an executable file, SUID allows any user to execute the file with the permissions of the file owner.
Use Case:
The passwd command is owned by root, but regular users must use it to change their passwords.
ls -l /usr/bin/passwd
You’ll see:
-rwsr-xr-x 1 root root 54256 Apr 23 09:32 /usr/bin/passwd
The s in the user/owner execute position represents the SUID bit.
To set SUID:
chmod u+s file_name
To remove:
chmod u-s file_name
2. SGID (Set Group ID)
SGID has two behaviors:
On files: Runs the file with the group owner's permissions.
On directories: Ensures all new files/subdirectories inherit the group of the parent directory—not the user’s default group.
Use Case:
In a shared group directory like /project, you want every file created to belong to the same group.
chmod g+s /project
ls -ld /project
Output:
drwxr-sr-x 2 devs devs 4096 Apr 23 09:32 /project
The s in the group execute position means SGID is active.
3. Sticky Bit
Used only on directories, the Sticky Bit prevents users from deleting files they don't own—even if they have write access to the directory.
Use Case:
On shared directories like /tmp, you don’t want users accidentally or maliciously deleting others’ files.
chmod o+t /tmp
ls -ld /tmp
Output:
drwxrwxrwt 10 root root 4096 Apr 23 09:32 /tmp
The t at the end? That’s the Sticky Bit.
Special Permissions: Numeric Mode
You can set SUID, SGID, and Sticky Bit using numeric values:
SUID = 4
SGID = 2
Sticky Bit = 1
Example:
chmod 6755 script.sh
6 (4 + 2) = SUID + SGID
755 = Regular permissions
Special permissions in Linux provide fine-grained control for shared environments and collaborative workflows. They're vital tools for sysadmins and DevOps engineers.
But—use with caution. Setting SUID or SGID on sensitive files can expose your system to security risks if misconfigured.
Keep your permissions smart, not sloppy.
Let’s connect on LinkedIn
As I automate my journey into RHCE and Ansible, I’d love to connect with fellow learners and professionals. Feel free to reach out and join me as I share tips, resources, and insights throughout this 30-day challenge.



































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




















































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)























































.jpg?#)













































































































































![Apple to Shift Robotics Unit From AI Division to Hardware Engineering [Report]](https://www.iclarified.com/images/news/97128/97128/97128-640.jpg)

![Apple Shares New Ad for iPhone 16: 'Trust Issues' [Video]](https://www.iclarified.com/images/news/97125/97125/97125-640.jpg)