Snyk and Sonar : committed credentials security test
Disclaimer : this guide deliberately contains an Easter egg - easy to spot security issue. Introduction I've been looking closely to understand the market of the code quality and security providers and got to know the leaders : Snyk Sonar They are both great and are different to certain extent even in terms of pricing model, it's up to you which security provider you prefer for your needs, it's quite certain you need an Enterprise version to protect the business and you definitely need more overall security oriented providers as well, see the Swiss cheese model. When having been watching some sort of performance around the security subject I have realized that one trivial use-case is quite new for me : committed credentials to the repository, I've witnessed this happening and every time it has been either a design imperfection or a necessity, at the same time the recovery from such an issue is not trivial, that is what I will cover in this guide. Setup I will get help from two AI assistants today - let me introduce ChatGPT and Mistral, I hope they will harmonically enhance my both cerebral hemispheres and we get fast to the point and we will have some fun. They have suggested me to use WSL with Kali Linux for this purpose. Create the demo project: mkdir demo-project cd demo-project git config --global init.defaultBranch main git config --global user.email "you@example.com" git config --global user.name "Your Name" git init touch index.js git add -A git commit -m 'init' and now I will add a sample of credentials for AWS, Azure and GCP to index.js cat > index.js git commit -m 'console-log' Snyk Sonar OK we have another issue, I didn't expect that, this was my Easter egg, funny. However we have no initial credentials related issue. Is the problem solved ? NO You can get to the previous state in git and retrieve the credentials : git checkout HEAD~3 && cat index.js Flash forward : I will be using git reflog Let's do the interactive rebase and remove the commit from history : git reflog git checkout HEAD@{1} git rebase -i HEAD~4 Still I can get the credentials : git reflog git checkout HEAD@{7} && cat index.js Recovery How to really fix the issue ? Disclaimer : the technical solution provided below has limited applicability and rather brutal Let's just proceed with a clean minimalistic setup : mkdir demo-project cd demo-project git init touch index.js git add -A git commit -m 'init' cat
Disclaimer : this guide deliberately contains an Easter egg - easy to spot security issue.
Introduction
I've been looking closely to understand the market of the code quality and security providers and got to know the leaders :
They are both great and are different to certain extent even in terms of pricing model, it's up to you which security provider you prefer for your needs, it's quite certain you need an Enterprise version to protect the business and you definitely need more overall security oriented providers as well, see the Swiss cheese model.
When having been watching some sort of performance around the security subject I have realized that one trivial use-case is quite new for me : committed credentials to the repository, I've witnessed this happening and every time it has been either a design imperfection or a necessity, at the same time the recovery from such an issue is not trivial, that is what I will cover in this guide.
Setup
I will get help from two AI assistants today - let me introduce ChatGPT and Mistral, I hope they will harmonically enhance my both cerebral hemispheres and we get fast to the point and we will have some fun. They have suggested me to use WSL with Kali Linux for this purpose.
Create the demo project:
mkdir demo-project
cd demo-project
git config --global init.defaultBranch main
git config --global user.email "you@example.com"
git config --global user.name "Your Name"
git init
touch index.js
git add -A
git commit -m 'init'
and now I will add a sample of credentials for AWS, Azure and GCP to index.js
cat < index.js
// index.js
// Basic Password
const password = 'SecurePass123!';
// AWS Credentials
const awsCredentials = {
accessKeyId: 'AKIAIOSFODNN7EXAMPLE',
secretAccessKey: 'wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY'
};
// Azure Credentials
const azureCredentials = {
subscriptionId: 'dummy_subscription_id',
clientId: 'dummy_client_id',
secret: 'dummy_secret',
tenant: 'dummy_tenant_id'
};
// GCP Credentials
const gcpCredentials = {
type: 'service_account',
project_id: 'dummy-project-id',
private_key_id: 'dummy_private_key_id',
private_key: '-----BEGIN PRIVATE KEY-----\nDUMMY_PRIVATE_KEY\n-----END PRIVATE KEY-----\n',
client_email: 'dummy-service-account@dummy-project-id.iam.gserviceaccount.com',
client_id: 'dummy_client_id',
auth_uri: 'https://accounts.google.com/o/oauth2/auth',
token_uri: 'https://oauth2.googleapis.com/token',
auth_provider_x509_cert_url: 'https://www.googleapis.com/oauth2/v1/certs',
client_x509_cert_url: 'https://www.googleapis.com/robot/v1/metadata/x509/dummy-service-account%40dummy-project-id.iam.gserviceaccount.com'
};
// Export the credentials and password
module.exports = {
password,
awsCredentials,
azureCredentials,
gcpCredentials
};
EOF
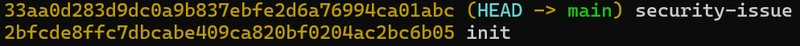
git add -A
git commit -m 'security-issue'
Now we are set.
Snyk
I need node to be installed, hence I will just follow the instructions and get nvm first.
Then I've got some help from AI :
npm install -g snyk
snyk --version
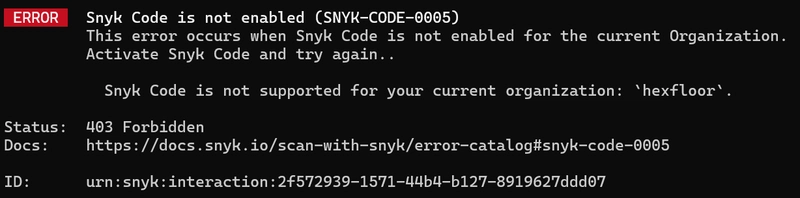
snyk code test
at this point I need to create a test account :
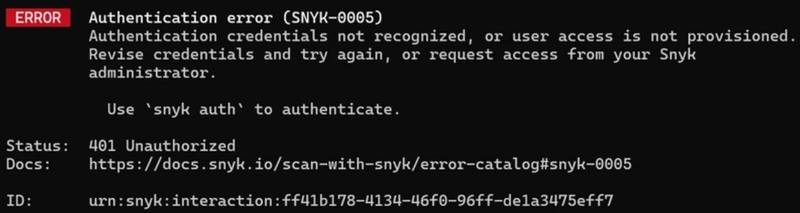
snyk auth
snyk code test
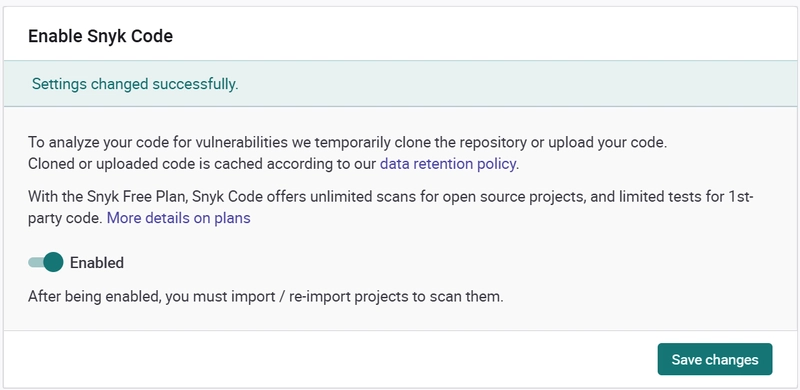
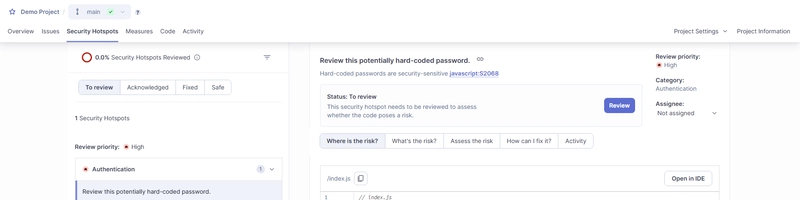
Let's enable snyk code :
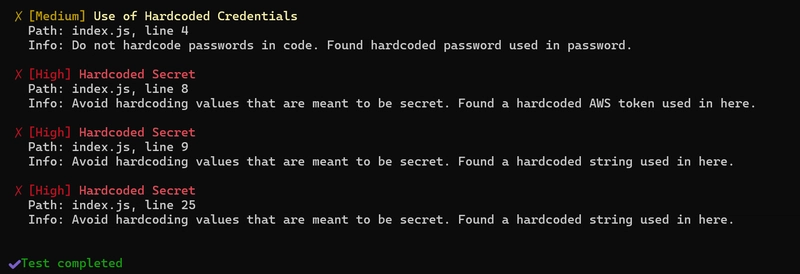
And see what we have :
OK, good start.
Sonar
Let's install docker
and the follow the documentation
$ docker run -d --name sonarqube -e SONAR_ES_BOOTSTRAP_CHECKS_DISABLE=true -p 9000:9000 sonarqube:latest
and install Sonar CLI (ad-hoc solution)
sudo apt install unzip wget -y
wget https://binaries.sonarsource.com/Distribution/sonar-scanner-cli/sonar-scanner-cli-5.0.1.3006-linux.zip
unzip sonar-scanner-cli-*.zip
sudo mkdir /opt/sonar-scanner
sudo mv sonar-scanner-* /opt/sonar-scanner
echo 'export PATH=$PATH:/opt/sonar-scanner/sonar-scanner-5.0.1.3006-linux/bin' >> ~/.bashrc
source ~/.bashrc
Now open sonar :
- http://localhost:9000
- login + change password
- My Account -> Security -> Generate Tokens
- generate
sonar-scanner-token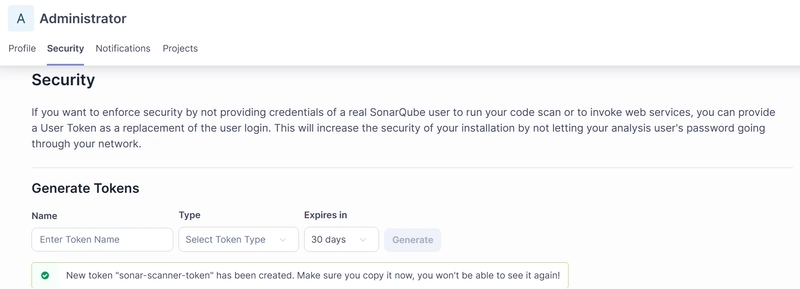
create Sonar configuration file with the generated token :
cat < sonar-project.properties
sonar.projectKey=demo-project
sonar.projectName=Demo Project
sonar.projectVersion=1.0
sonar.sources=.
sonar.host.url=http://localhost:9000
sonar.login=
EOF
now run the scanner :
sonar-scanner
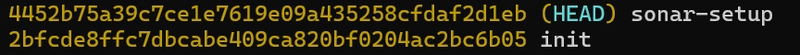
I will commit the setup:
git add -A
git commit -m 'sonar-setup'
Issue
Alright we have done a mistake, let's try to perform a recovery, I will just revert the commit leading to the security issue, add another line to the index.js
echo "console.log('demo');" >> index.js
git commit -m 'console-log'
Snyk
Sonar
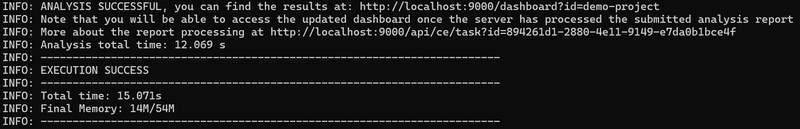
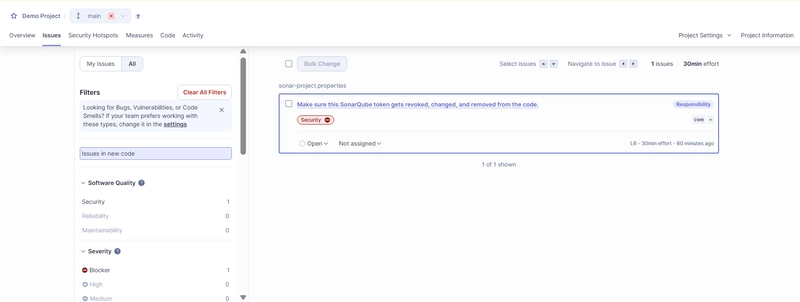
OK we have another issue, I didn't expect that, this was my Easter egg, funny. However we have no initial credentials related issue.
Is the problem solved ?
NO
You can get to the previous state in git and retrieve the credentials :
git checkout HEAD~3 && cat index.js
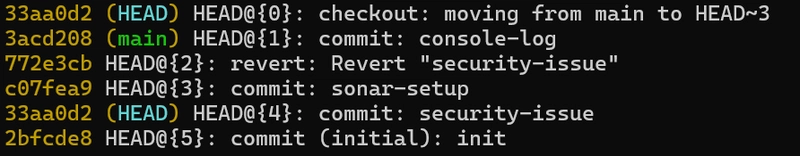
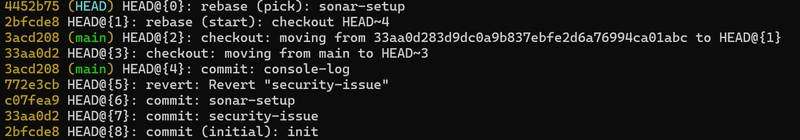
Flash forward : I will be using git reflog
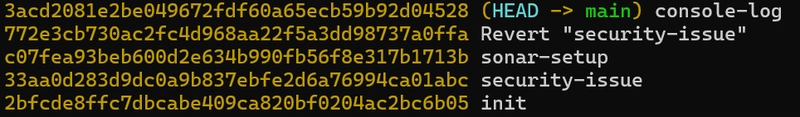
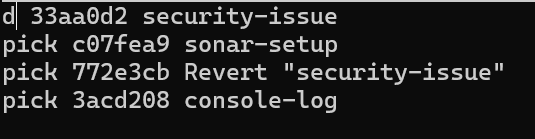
Let's do the interactive rebase and remove the commit from history :
git reflog
git checkout HEAD@{1}
git rebase -i HEAD~4
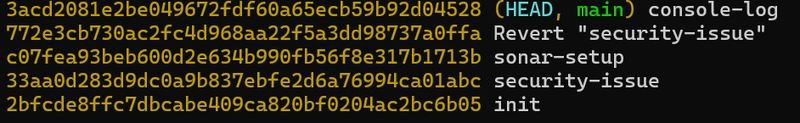
Still I can get the credentials :
git reflog
git checkout HEAD@{7} && cat index.js
Recovery
How to really fix the issue ?
Disclaimer : the technical solution provided below has limited applicability and rather brutal
Let's just proceed with a clean minimalistic setup :
mkdir demo-project
cd demo-project
git init
touch index.js
git add -A
git commit -m 'init'
cat < index.js
// index.js
const password = 'SecurePass123!';
EOF
git add -A
git commit -m 'security-issue'
And let's fix :
- remove
index.jsfrom all git history - expire
git reflog - prune dangling blobs
- force push (!)
- verify
sudo apt install git-filter-repo
which git-filter-repo
git filter-repo --path index.js --invert-paths --force
git reflog expire --expire=now --all
git gc --prune=now --aggressive
Destructive
git push --force --all
git push --force --tags
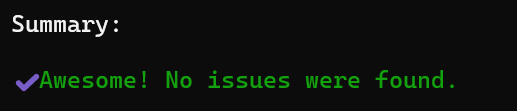
Verify :
git log --all -- index.js
git grep 'SecurePass123!' $(git rev-list --all)
rm -rf .git/filter-repo
rm -rf .git/lost-found
Post-mortem :
- reclone the repository
- rotate keys
- purge system cache (a topic in itself)
Summary
Long story short : once you have leaked the keys it's a bit of a challenge to recover as yes, you will rotate the keys and the immediate issue will be fixed, whereas another issue is to prevent it from happening again.
There have been real cases of leaking the keys through the reflog by the leaders :
- GitHub OAuth Token Leak by Slack – 2015
- Uber AWS Key Leak – 2016
- Facebook Access Token Leak – 2017
Hence yes, you need some sort of code analysis software in Enterprise edition for your business, as it seems that for Sonar the password leaks are part of the Community edition and leaked api keys detection is a part of the Enterprise edition only, for Snyk the Enterprise edition is also more powerful and contains essential features.
And even then you will have to stay vigilant and to go deeper.
I would suggest to switch to cloud native for the dev purposes, as the whole recovery is pretty complicated due to the caching on different levels.
Happy Easter !









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)



























































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)




























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





























































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)