Python in Game Hacking: What Still Works?
Break the mold—learn how Python can help you explore game mechanics, even in a world where anti-cheat systems are getting tougher every day. If you’ve ever wondered whether memory editing, aimbots, and cheat engines still have a place in modern gaming, you’re in the right spot. While many of these techniques have been met with stricter countermeasures, the learning process behind them is invaluable. This article is your practical guide to understanding what still works, why it works, and how you can get hands-on experience—ethically and safely. 1. A New Era for Game Hackers The world of game hacking has changed dramatically. Gone are the days when a few lines of Python code could easily manipulate game memory or automate tasks without detection. Modern games integrate AI-powered anti-cheat systems that analyze player behavior in real time, making traditional hacking methods increasingly difficult to execute. But here’s the silver lining: understanding these techniques is still a tremendous learning opportunity. info: "Even if you're not planning to use these techniques for unfair play, experimenting in a controlled environment sharpens your skills in programming, reverse engineering, and cybersecurity." — A seasoned developer Python remains one of the most accessible languages for exploring these concepts. It provides a gentle introduction to memory editing, process handling, and even machine learning—all without the steep learning curve of lower-level languages. How Hackers and Spies Use the Same Psychological Tricks Against You Listen, there’s a reason why spies are the most dangerous individuals in the world. They don’t just sneak around—they control information, manipulate minds, and execute missions with surgical precision. This course isn’t some Hollywood fantasy. It’s a deep dive into the real-world techniques used by intelligence operatives, elite agencies, and covert specialists.Whether you want to understand the psychology of manipulation, master counter-surveillance, or learn how intelligence agencies truly operate, this is the most comprehensive espionage training you’ll find outside classified circles.What You’ll Master in This Course:MODULE 1: Introduction to Espionage & Spycraft How espionage has shaped wars, politics, and economies. The evolution of tradecraft from ancient times to modern intelligence. The role of intelligence agencies in national security. How covert operations truly work in today’s world. MODULE 2: The Fundamentals of Covert Operations Operational Security (OPSEC) secrets that keep you undetected. Surveillance and counter-surveillance techniques. The mechanics of stealth and infiltration. Secure communication methods that spies rely on. MODULE 3: Intelligence Gathering Methods Human intelligence (HUMINT) and how to extract secrets from people. Signals intelligence (SIGINT) and intercepting communication. Open-source intelligence (OSINT) and how to dig up hidden data. Cyber intelligence—spying in the digital world. MODULE 4: Psychological Manipulation & Persuasion The principles of psychological manipulation used in espionage. Persuasion tactics that can make anyone believe anything. How social engineering is used to extract secrets. Influence operations that shape global politics. MODULE 5: Advanced Surveillance & Countermeasures Electronic surveillance techniques and how to use them. Physical surveillance and how spies track targets. Counter-surveillance strategies to shake a tail. How modern technology is changing surveillance tactics. MODULE 6: Infiltration & Exfiltration Operations Urban and rural infiltration techniques. Escape and evasion tactics used behind enemy lines. Exfiltration methods when extraction is life or death. Mastering disguises and identity manipulation. MODULE 7: Advanced Counterintelligence Tactics How counterintelligence stops spies before they act. Identifying and neutralizing surveillance teams. Insider threats—how intelligence agencies handle moles. Cyber counterintelligence and protecting classified information. MODULE 8: Technological Tools in Modern Espionage Cyber espionage techniques used by top intelligence agencies. AI-driven intelligence gathering—how spies use machine learning. Surveillance technologies that track targets worldwide. Encryption and secure storage of sensitive data. MODULE 9: Legal, Ethical & Geopolitical Considerations International law and espionage—what’s legal, what’s not. The ethics of intelligence gathering. Balancing national security with civil liberties. Case studies of political espionage in action. MODULE 10: Real-Life Espionage Case Studies & Debriefing The greatest spy missions in history—analyzed. Cold War spy stories that shaped the world. Modern-day espionage operations and their impact. Psychological effects of espionage on operatives. MODULE 11: Th

Break the mold—learn how Python can help you explore game mechanics, even in a world where anti-cheat systems are getting tougher every day.
If you’ve ever wondered whether memory editing, aimbots, and cheat engines still have a place in modern gaming, you’re in the right spot. While many of these techniques have been met with stricter countermeasures, the learning process behind them is invaluable. This article is your practical guide to understanding what still works, why it works, and how you can get hands-on experience—ethically and safely.
1. A New Era for Game Hackers
The world of game hacking has changed dramatically. Gone are the days when a few lines of Python code could easily manipulate game memory or automate tasks without detection. Modern games integrate AI-powered anti-cheat systems that analyze player behavior in real time, making traditional hacking methods increasingly difficult to execute. But here’s the silver lining: understanding these techniques is still a tremendous learning opportunity.
info:
"Even if you're not planning to use these techniques for unfair play, experimenting in a controlled environment sharpens your skills in programming, reverse engineering, and cybersecurity."— A seasoned developer
Python remains one of the most accessible languages for exploring these concepts. It provides a gentle introduction to memory editing, process handling, and even machine learning—all without the steep learning curve of lower-level languages.
2. Python-Based Cheat Engines vs. Modern Anti-Cheat Systems
Understanding the Basics
Python has long been the go-to language for hobbyist hackers. In the early days, developers could write simple scripts to attach to running game processes, read memory addresses, and alter game variables on the fly. Here’s a simplified example using the pymem library to read a memory address:
import pymem
# Attach to a process by its executable name
pm = pymem.Pymem('game.exe')
# Assume 0x00FFAA00 is the memory address for player health
health_address = 0x00FFAA00
# Read the current health value
current_health = pm.read_int(health_address)
print(f"Current Health: {current_health}")
# Write a new health value
pm.write_int(health_address, 999)
print("Health set to 999!")
This basic script demonstrates the early days of cheat engines. However, modern games now employ dynamic memory allocation, randomized addresses, and kernel-level protections that make such simple scans far less effective.
The Evolution of Anti-Cheat
Modern anti-cheat systems use:
- Real-time memory monitoring: They continuously check for unauthorized changes.
- Randomized memory layouts: By shuffling memory addresses, they prevent static scripts from easily locating important values.
- Behavioral analysis: AI algorithms assess if a player’s actions are humanly possible.
According to recent studies, over 75% of popular multiplayer games now implement multi-layered anti-cheat systems, rendering many basic Python hacks ineffective in live environments. However, these systems are mostly designed to protect competitive play rather than educational exploration.
info:
"Understanding these security measures can transform a hacker’s mindset into that of a security researcher—a skill that’s highly valuable in today’s tech landscape."— Industry Expert
Actionable Insights:
- Begin with Older or Indie Games: Test your scripts on games that haven’t implemented advanced anti-cheat measures.
- Embrace the Learning Curve: Use your experiments as an opportunity to learn about memory management, process hooking, and security practices.
- Stay Ethical: Always work in a controlled, legal environment—preferably on your own projects or open-source games designed for experimentation.
3. AI-Powered Anti-Cheat: Shutting Down Script Kiddies
How AI is Changing the Game
The introduction of AI into anti-cheat systems means that these programs now detect anomalies with greater precision. For example, advanced algorithms analyze mouse movement patterns to distinguish between human behavior and automated aimbot actions.
Here’s a simplified concept of what an AI-based detection mechanism might monitor:
- Precision: Does the aim lock onto targets with mechanical accuracy?
- Timing: Is there an unnatural delay between movement and reaction?
- Pattern Recognition: Do repeated actions follow a fixed, non-human pattern?
Recent statistics show that AI-based anti-cheat solutions have reduced successful cheats by nearly 60% in some competitive games. This drastic improvement means that traditional Python scripts are more likely to be caught if used inappropriately.
info:
"Modern anti-cheat systems are now as much about behavior analysis as they are about memory scanning. They learn and adapt, which forces hackers to become equally innovative if they wish to bypass them."— Cybersecurity Analyst
Actionable Insights:
- Learn AI Basics: Understanding the fundamentals of AI and machine learning can give you insight into both building smarter cheats and creating stronger defense systems.
- Simulate AI in Controlled Environments: Create your own simulation projects to mimic how AI might analyze behavior. Libraries like TensorFlow or PyTorch are excellent starting points.
- Stay Informed: Regularly check trusted sources to understand the latest trends in anti-cheat technology.
4. The Rise of Machine Learning in Gaming Exploits
Adaptive Techniques for a Dynamic Battlefield
Machine learning is not just for anti-cheat—it’s also being exploited to develop more sophisticated, adaptive hacks. Unlike static scripts, machine learning models can adjust their behavior in real time, making them far more difficult to detect.
For instance, consider a machine learning approach to an aimbot. Instead of using fixed coordinates, the model learns from the game environment and adjusts its target selection to mimic human behavior more convincingly.
Here’s a very basic example using TensorFlow:
import tensorflow as tf
import numpy as np
# Simulated game data: features might include target distance, movement speed, etc.
data = np.array([[0.2, 0.4], [0.6, 0.8], [0.1, 0.3], [0.9, 0.5]])
labels = np.array([1, 0, 1, 0]) # 1: Target acquired, 0: No target
# Define a simple model
model = tf.keras.models.Sequential([
tf.keras.layers.Dense(4, activation='relu', input_shape=(2,)),
tf.keras.layers.Dense(1, activation='sigmoid')
])
# Compile the model
model.compile(optimizer='adam', loss='binary_crossentropy', metrics=['accuracy'])
# Train the model
model.fit(data, labels, epochs=50, verbose=0)
# Predict on new data
new_data = np.array([[0.3, 0.6]])
prediction = model.predict(new_data)
print(f"Prediction: {prediction[0][0]:.2f}")
This script illustrates the early stages of integrating machine learning into gaming exploits. While real-world implementations are more complex, the idea is the same: adapt and learn from the environment.
info:
"The shift towards machine learning in game hacking is a double-edged sword—providing sophisticated tools for both attackers and defenders."— Machine Learning Researcher
Actionable Insights:
- Experiment with Models: Use sandbox environments to train and test simple models that simulate game decision-making processes.
- Deepen Your Knowledge: Resources like online courses in AI and machine learning can help you understand the intricate details behind these adaptive systems.
- Join Communities: Engage with online forums and groups that discuss ethical hacking and machine learning applications in gaming.
5. Practical Python Tricks and Code Examples
Even as anti-cheat systems become more advanced, some practical Python tricks remain useful for educational purposes. Let’s break down some examples.
Memory Scanning and Editing Example
We already saw a basic example with pymem. Here’s a more detailed version that includes error handling and a simple loop for continuous monitoring:
import pymem
import time
def attach_to_game(process_name):
try:
pm = pymem.Pymem(process_name)
print(f"Attached to {process_name} successfully!")
return pm
except Exception as e:
print(f"Error attaching to process: {e}")
return None
def monitor_and_edit(pm, address, target_value):
try:
while True:
current_value = pm.read_int(address)
print(f"Current Value: {current_value}")
if current_value != target_value:
pm.write_int(address, target_value)
print(f"Value updated to {target_value}!")
time.sleep(1) # Check every second
except Exception as e:
print(f"Error during monitoring: {e}")
if __name__ == "__main__":
game_process = "game.exe"
health_address = 0x00FFAA00 # Replace with actual address
desired_health = 999
pm = attach_to_game(game_process)
if pm:
monitor_and_edit(pm, health_address, desired_health)
Automating Tasks: A Basic Aimbot Simulation
For educational purposes, here’s a simple script to simulate mouse movement. Note: This code uses the pyautogui library and is only for simulation.
import pyautogui
import time
def simulate_aim(target_x, target_y):
# Move the mouse to the target coordinates
pyautogui.moveTo(target_x, target_y, duration=0.25)
print(f"Aimed at ({target_x}, {target_y})")
if __name__ == "__main__":
# Example target positions; in real scenarios, these would be calculated dynamically
targets = [(300, 400), (500, 350), (450, 450)]
for x, y in targets:
simulate_aim(x, y)
time.sleep(0.5) # Pause between movements
Building Defensive Tools: Anti-Cheat Modules
Learning how cheats work can be inverted to build better defenses. Consider a module that checks for unusual memory changes:
def monitor_memory(pm, address, expected_value, tolerance=5):
"""
Monitor a specific memory address and alert if the value deviates from the expected range.
"""
current_value = pm.read_int(address)
if abs(current_value - expected_value) > tolerance:
print(f"Alert! Memory value {current_value} deviates from expected {expected_value}.")
else:
print("Memory value within acceptable range.")
# Example usage:
# monitor_memory(pm, health_address, 100)
info:
"Practical coding exercises like these not only deepen your technical skills but also build a mindset of thinking both offensively and defensively in the realm of cybersecurity."— Developer Insight
6. Overcoming Challenges: Legal, Ethical, and Technical
Legal and Ethical Considerations
The most critical point to remember is that using these techniques outside controlled environments is both unethical and illegal. Here are some key guidelines:
- Only Experiment on Your Own Systems: Never use these methods in multiplayer games or on systems where you do not have explicit permission.
- Use for Educational Purposes: Channel your skills into cybersecurity research or contribute to the development of robust anti-cheat systems.
- Stay Updated on Laws: Cyber laws evolve, so keep yourself informed to avoid unintentional breaches.
Technical Hurdles
Modern anti-cheat mechanisms incorporate multiple layers of defense:
- Dynamic Memory Addressing: Randomized memory spaces make static scanning challenging.
- Kernel-Level Protections: These prevent external processes from modifying critical game data.
- Behavioral Algorithms: AI detects non-human patterns in actions like aiming and movement.
Understanding these challenges is part of the learning process. Every roadblock is an opportunity to deepen your understanding of computer systems, operating system internals, and network security.
info:
"The more you experiment and encounter real-world challenges, the better you become at designing resilient systems—be it for hacking or for defense."— Cybersecurity Mentor
7. Essential Resources and Statistics
For anyone serious about diving into this field, here are some curated resources:
-
Python Developer Resources:
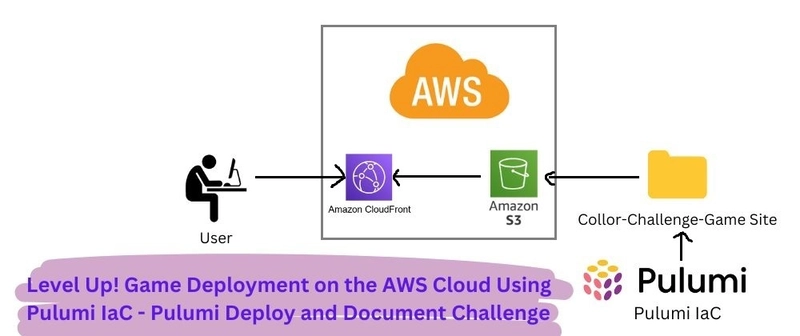
Explore a comprehensive collection of tools, articles, and trending discussions at Python Developer Resources - Made by 0x3d.site.











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)























.webp?#)










_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)




































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)
































































































































 snappytuts.gumroad.com
snappytuts.gumroad.com



