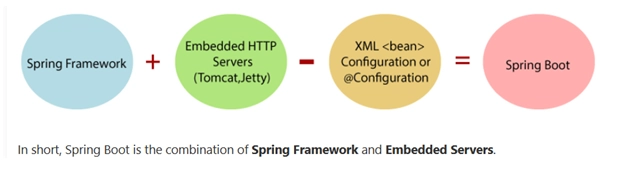
KernelSnitch – A New Side-Channel Attack Targeting Data Structures
Researchers have disclosed KernelSnitch, a novel side-channel attack exploiting timing variances in Linux kernel data structures, achieving covert data transmission rates up to 580 kbit/s and enabling website fingerprinting with 89% accuracy. The attack targets four critical container types: fixed/dynamic hash tables, radix trees, and red-black trees, bypassing hardware-based defenses through software-induced timing leaks. KernelSnitch […] The post KernelSnitch – A New Side-Channel Attack Targeting Data Structures appeared first on Cyber Security News.

Researchers have disclosed KernelSnitch, a novel side-channel attack exploiting timing variances in Linux kernel data structures, achieving covert data transmission rates up to 580 kbit/s and enabling website fingerprinting with 89% accuracy.
The attack targets four critical container types: fixed/dynamic hash tables, radix trees, and red-black trees, bypassing hardware-based defenses through software-induced timing leaks.
KernelSnitch exploits the fundamental property that kernel data structures require variable access times depending on their occupancy level – the number of elements stored. Key vulnerable structures include:
- futex_hash_table: Manages Fast User-space Mutex (FUTEX) queues
- posix_timers_hashtable: Stores POSIX timer objects
- ipc_ids.key_ht: Dynamically resizable hash table for IPC objects
- hrtimer_bases.clock_base.active: Red-black tree for high-resolution timers
The attack measures syscall execution times to infer structural changes. For example, sys_futex_wait appends elements to hash buckets, while sys_futex_wake probes occupancy through timed iterations.
To overcome nanosecond-scale timing differences, researchers developed two amplification methods:
Structure-Agnostic: Flushes CPU caches via LLC-sized eviction sets, forcing memory reloads. This converts cache hits to misses, amplifying timing deltas by 347%.
Hardware-Agnostic: Artificially inflates target structures. In futex attacks, appending 64+ queues to a single bucket via repeated sys_futex_wait calls creates measurable 8.2µs timing gaps.
Attack Vectors
Covert Channel Construction
Synchronized processes achieved:
- 580 kbit/s transmission using futex_hash_table
- 528 kbit/s via ipc_ids.key_ht dynamic hash table
- 35 kbit/s through red-black tree operations
Error rates remained below 2.8% using adaptive thresholding.
Kernel Heap Pointer Leak
By exploiting jhash2 collisions in futex hashing, attackers derived mm_struct addresses in ≤65 seconds. This enabled cross-cache reuse attacks, placing msg_msg objects at known locations for privilege escalation.
Website Fingerprinting
Monitoring futex_hash_table occupancy during Firefox browsing sessions generated 300-dimensional timing vectors. A convolutional neural network (CNN) classifier achieved:
- 89.5% F1-score on Ahrefs Top 100 sites
- 93.2% precision distinguishing media-heavy pages
Mitigation Challenges
A team from Graz University of Technology, outlines fundamental defense difficulties:
- Constant-Time Enforcement impractical for unbounded structures
- Namespace Isolation introduces performance overheads
- Timing Source Removal breaks legitimate applications
Proposed solutions include watermark-based execution padding and structure partitioning, but none eliminate leakage completely.
Linux kernel maintainers acknowledged the findings, noting existing KASLR vulnerabilities while emphasizing the novelty of heap pointer leaks.
The researchers open-sourced attack prototypes and urged reevaluation of kernel data structure security models.
This work highlights the persistent risk of software-induced side channels, proving that even “leakage-free” hardware cannot prevent OS-level information exposure.
As containerization and real-time systems proliferate, KernelSnitch underscores the need for structural security audits in foundational OS components.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response and Threat Hunting – Register Here
The post KernelSnitch – A New Side-Channel Attack Targeting Data Structures appeared first on Cyber Security News.









































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.jpg?#)
































_ArtemisDiana_Alamy.jpg?#)


 (1).webp?#)







































































-xl.jpg)










![Yes, the Gemini icon is now bigger and brighter on Android [U]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/02/Gemini-on-Galaxy-S25.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)









![Apple Rushes Five Planes of iPhones to US Ahead of New Tariffs [Report]](https://www.iclarified.com/images/news/96967/96967/96967-640.jpg)
![Apple Vision Pro 2 Allegedly in Production Ahead of 2025 Launch [Rumor]](https://www.iclarified.com/images/news/96965/96965/96965-640.jpg)