How to verify GitHub commits with SSH
First Things First: Why Should You Sign Your Commits? By default, Git accepts whatever name and email you set when authoring a commit. When you push that commit to GitHub, GitHub associates it with a profile matching those details. However, the problem is that—anyone can configure Git with someone else's name and email, making it appear as if they authored the commit. When a commit is unsigned, there is no guarantee that: The author is truly the person whose name appears on the commit. The code has not been altered or tampered with after it was written. Signing commits using GPG or SSH provides cryptographic proof of authorship and integrity, making sure that the commit is from the claimed author and has not been modified. Requirements to verify commit signature in GitHub: Generate an SSH key Add the SSH public key to GitHub Configure git to sign the commits automatically Generate a SSH Key You can generate a new SSH key on your local machine. After you generate the key, you can add the public key to your account on GitHub.com to enable authentication/signing for Git operations over SSH. Run the following command in your terminal: ssh-keygen -t ed25519 -C "your_email@example.com" Tip: To prevent exposing your personal email by any means, I recommend using the GitHub's generated email which will end with @users.noreply.github.com Next, Add the key to SSH agent by running eval "$(ssh-agent -s)" Add the SSH public key to GitHub You can add an SSH key in GitHub and use it for authentication, or commit signing, or both. If you want to use the same SSH key for both authentication and signing, you need to upload it twice. Let's add the SSH key for signing. Copy the public key $ pbcopy < ~/.ssh/id_ed25519.pub # Copies the contents of the id_ed25519.pub file to your clipboard Go to https://github.com/settings/keys and add the SSH key for signing as shown in the following image Configure git to sign commits and tags SSH signature verification is available in Git 2.34 or later. To configure Git to use SSH to sign commits and tags: git config --global gpg.format ssh To configure your Git client to sign all commits by default in any local repository on your computer, run git config --global commit.gpgsign true And, add the path to public key file to git config git config --global user.signingkey ~/.ssh/id_ed25519.pub In addition, we should also add the public keys to allowedSigners file. Its a file to tell git the public keys you are willing to trust for signing commits. echo "your_email@example.com $(cat ~/.ssh/id_ed25519.pub)" > ~/.config/git/allowed-signers git config gpg.ssh.allowedSignersFile '~/.config/git/allowed-signers' Note: You can store the allowed signers file anywhere, as long as the path is correctly configured. You're all set Now, when you commit changes, GitHub should display a "Verified" badge next to your commits, proving they are securely signed.
First Things First: Why Should You Sign Your Commits?
By default, Git accepts whatever name and email you set when authoring a commit. When you push that commit to GitHub, GitHub associates it with a profile matching those details. However, the problem is that—anyone can configure Git with someone else's name and email, making it appear as if they authored the commit.
When a commit is unsigned, there is no guarantee that:
- The author is truly the person whose name appears on the commit.
- The code has not been altered or tampered with after it was written.
Signing commits using GPG or SSH provides cryptographic proof of authorship and integrity, making sure that the commit is from the claimed author and has not been modified.
Requirements to verify commit signature in GitHub:
- Generate an SSH key
- Add the SSH public key to GitHub
- Configure git to sign the commits automatically
Generate a SSH Key
You can generate a new SSH key on your local machine. After you generate the key, you can add the public key to your account on GitHub.com to enable authentication/signing for Git operations over SSH.
Run the following command in your terminal:
ssh-keygen -t ed25519 -C "your_email@example.com"
Tip: To prevent exposing your personal email by any means, I recommend using the GitHub's generated email which will end with @users.noreply.github.com
Next, Add the key to SSH agent by running
eval "$(ssh-agent -s)"
Add the SSH public key to GitHub
You can add an SSH key in GitHub and use it for authentication, or commit signing, or both. If you want to use the same SSH key for both authentication and signing, you need to upload it twice.
Let's add the SSH key for signing.
- Copy the public key
$ pbcopy < ~/.ssh/id_ed25519.pub
# Copies the contents of the id_ed25519.pub file to your clipboard
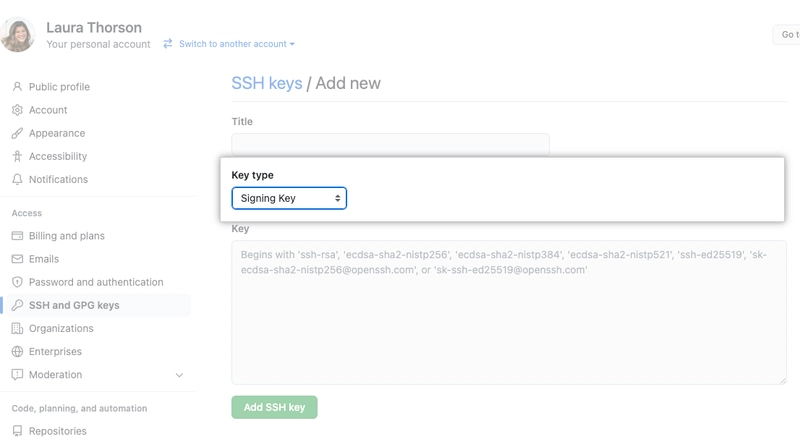
- Go to https://github.com/settings/keys and add the SSH key for signing as shown in the following image
Configure git to sign commits and tags
SSH signature verification is available in Git 2.34 or later. To configure Git to use SSH to sign commits and tags:
git config --global gpg.format ssh
To configure your Git client to sign all commits by default in any local repository on your computer, run
git config --global commit.gpgsign true
And, add the path to public key file to git config
git config --global user.signingkey ~/.ssh/id_ed25519.pub
In addition, we should also add the public keys to allowedSigners file. Its a file to tell git the public keys you are willing to trust for signing commits.
echo "your_email@example.com $(cat ~/.ssh/id_ed25519.pub)" > ~/.config/git/allowed-signers
git config gpg.ssh.allowedSignersFile '~/.config/git/allowed-signers'
Note: You can store the allowed signers file anywhere, as long as the path is correctly configured.
You're all set
Now, when you commit changes, GitHub should display a "Verified" badge next to your commits, proving they are securely signed.











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)























.webp?#)










_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)




































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)



































































































































