How to Secure Your .NET Applications
Security is one of the most critical aspects of modern application development. In an era where data breaches and cyber threats are increasingly common, securing your .NET applications is not optional – it’s essential. This guide covers practical strategies and tools you can apply right now to make your applications safer and more resilient. 1. Implement Strong Authentication and Authorisation Security begins with ensuring only the right people access your application. .NET offers robust options for managing identity and access control. Use ASP.NET Core Identity for user and role management. Integrate external providers like Microsoft, Google, GitHub via OAuth 2.0 or OpenID Connect. Prefer policy-based authorisation over simple role checks for more granular control. services.AddAuthentication("Cookies") .AddCookie("Cookies", options => { options.LoginPath = "/Account/Login"; }); [Authorize(Policy = "AdminOnly")] public IActionResult AdminDashboard() => View(); 2. Protect Sensitive Data Your app likely handles personal or confidential data. It's crucial to protect it both during transmission and while stored. Use HTTPS to encrypt data in transit (see section 4). Store passwords using ASP.NET Identity’s built-in hashing. Use the Data Protection API for encrypting custom data like tokens. var protector = _dataProtectionProvider.CreateProtector("MyApp.Purpose"); var protectedData = protector.Protect("my-secret-data"); var unprotected = protector.Unprotect(protectedData); 3. Prevent Common Attacks Many attacks can be mitigated by using .NET’s security features correctly. SQL Injection: Use Entity Framework Core with LINQ or parameterised queries. Cross-Site Scripting (XSS): Razor views automatically encode content. Avoid @Html.Raw() unless necessary. Cross-Site Request Forgery (CSRF): Enabled by default with [ValidateAntiForgeryToken]. Content Security Policy (CSP): Implement CSP headers to mitigate advanced XSS attacks. var user = await _context.Users .Where(u => u.Email == email) .FirstOrDefaultAsync(); 4. Enforce HTTPS and Secure Headers Ensuring encrypted communication and proper HTTP headers is vital for protecting user data. app.UseHttpsRedirection(); app.UseHsts(); // Adds HTTP Strict Transport Security Production Example (appsettings.json + Startup) "Kestrel": { "Endpoints": { "Https": { "Url": "https://*:5001", "Certificate": { "Path": "certs/yourcert.pfx", "Password": "yourpassword" } } } } Add secure headers using middleware like NWebsec. 5. Manage Secrets Securely Avoid hardcoding secrets like connection strings or API keys in your codebase. Use .NET Secret Manager for local development. Use Environment Variables in staging or production. Use Azure Key Vault for secure, scalable secret management. var secret = configuration["MySecret"]; Example with Azure Key Vault builder.Configuration.AddAzureKeyVault( new Uri("https://.vault.azure.net/"), new DefaultAzureCredential()); 6. Keep Dependencies Up to Date Outdated packages are a common entry point for attackers. Stay current using automated tools: dotnet list package --vulnerable GitHub Dependabot OWASP Dependency-Check 7. Add Logging and Monitoring Proactive logging helps you detect and respond to suspicious activity. Log failed logins, access denials, and other events. Use Serilog, NLog, or built-in logging with Microsoft.Extensions.Logging. Log.Logger = new LoggerConfiguration() .WriteTo.Console() .CreateLogger(); Cloud-based monitoring options Azure Application Insights Sentry, Datadog, Seq ✅ Security Checklist Before deploying your .NET app, review the following: [ ] HTTPS is enforced [ ] Secrets are not in source control [ ] Authentication & Authorisation are in place [ ] CSRF and XSS protections are active [ ] SQL access is parameterised or via EF Core [ ] Secure headers (CSP, HSTS, etc.) are configured [ ] Dependencies are up to date [ ] Monitoring/logging is active Tools & Resources ASP.NET Core Security Docs OWASP Top 10 Microsoft Threat Modelling Tool Final Thoughts Security is a journey, not a destination. By following these best practices, you’ll significantly reduce risk and build trust with your users. As threats evolve, so should your defences. Keep your knowledge up to date, review your code regularly, and never stop improving.

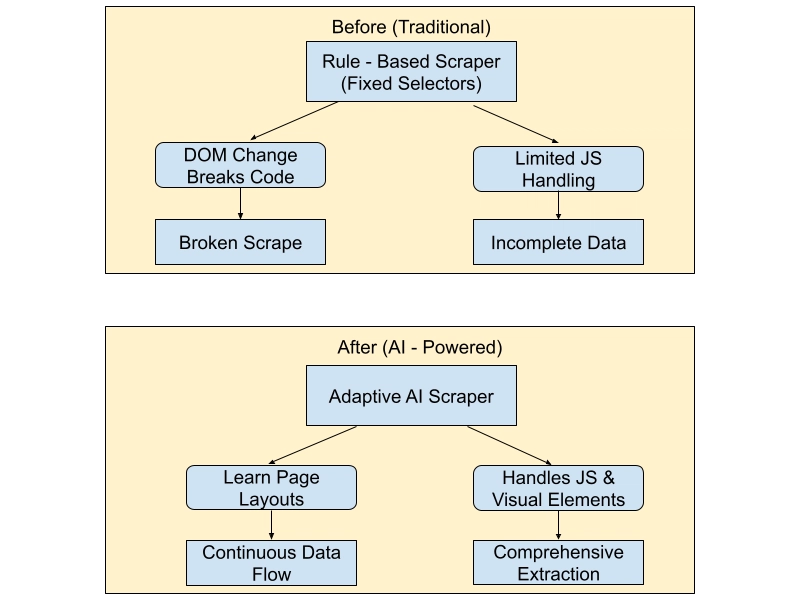
Security is one of the most critical aspects of modern application development. In an era where data breaches and cyber threats are increasingly common, securing your .NET applications is not optional – it’s essential. This guide covers practical strategies and tools you can apply right now to make your applications safer and more resilient.
1. Implement Strong Authentication and Authorisation
Security begins with ensuring only the right people access your application. .NET offers robust options for managing identity and access control.
- Use ASP.NET Core Identity for user and role management.
- Integrate external providers like Microsoft, Google, GitHub via OAuth 2.0 or OpenID Connect.
- Prefer policy-based authorisation over simple role checks for more granular control.
services.AddAuthentication("Cookies")
.AddCookie("Cookies", options => {
options.LoginPath = "/Account/Login";
});
[Authorize(Policy = "AdminOnly")]
public IActionResult AdminDashboard() => View();
2. Protect Sensitive Data
Your app likely handles personal or confidential data. It's crucial to protect it both during transmission and while stored.
- Use HTTPS to encrypt data in transit (see section 4).
- Store passwords using ASP.NET Identity’s built-in hashing.
- Use the Data Protection API for encrypting custom data like tokens.
var protector = _dataProtectionProvider.CreateProtector("MyApp.Purpose");
var protectedData = protector.Protect("my-secret-data");
var unprotected = protector.Unprotect(protectedData);
3. Prevent Common Attacks
Many attacks can be mitigated by using .NET’s security features correctly.
- SQL Injection: Use Entity Framework Core with LINQ or parameterised queries.
-
Cross-Site Scripting (XSS): Razor views automatically encode content. Avoid
@Html.Raw()unless necessary. -
Cross-Site Request Forgery (CSRF): Enabled by default with
[ValidateAntiForgeryToken]. - Content Security Policy (CSP): Implement CSP headers to mitigate advanced XSS attacks.
var user = await _context.Users
.Where(u => u.Email == email)
.FirstOrDefaultAsync();
4. Enforce HTTPS and Secure Headers
Ensuring encrypted communication and proper HTTP headers is vital for protecting user data.
app.UseHttpsRedirection();
app.UseHsts(); // Adds HTTP Strict Transport Security
Production Example (appsettings.json + Startup)
"Kestrel": {
"Endpoints": {
"Https": {
"Url": "https://*:5001",
"Certificate": {
"Path": "certs/yourcert.pfx",
"Password": "yourpassword"
}
}
}
}
Add secure headers using middleware like NWebsec.
5. Manage Secrets Securely
Avoid hardcoding secrets like connection strings or API keys in your codebase.
- Use .NET Secret Manager for local development.
- Use Environment Variables in staging or production.
- Use Azure Key Vault for secure, scalable secret management.
var secret = configuration["MySecret"];
Example with Azure Key Vault
builder.Configuration.AddAzureKeyVault(
new Uri("https://.vault.azure.net/" ),
new DefaultAzureCredential());
6. Keep Dependencies Up to Date
Outdated packages are a common entry point for attackers. Stay current using automated tools:
dotnet list package --vulnerable- GitHub Dependabot
- OWASP Dependency-Check
7. Add Logging and Monitoring
Proactive logging helps you detect and respond to suspicious activity.
- Log failed logins, access denials, and other events.
- Use Serilog, NLog, or built-in logging with
Microsoft.Extensions.Logging.
Log.Logger = new LoggerConfiguration()
.WriteTo.Console()
.CreateLogger();
Cloud-based monitoring options
- Azure Application Insights
- Sentry, Datadog, Seq
✅ Security Checklist
Before deploying your .NET app, review the following:
- [ ] HTTPS is enforced
- [ ] Secrets are not in source control
- [ ] Authentication & Authorisation are in place
- [ ] CSRF and XSS protections are active
- [ ] SQL access is parameterised or via EF Core
- [ ] Secure headers (CSP, HSTS, etc.) are configured
- [ ] Dependencies are up to date
- [ ] Monitoring/logging is active
Tools & Resources
Final Thoughts
Security is a journey, not a destination. By following these best practices, you’ll significantly reduce risk and build trust with your users. As threats evolve, so should your defences. Keep your knowledge up to date, review your code regularly, and never stop improving.







































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)















































































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)











![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)



























![Mobile Legends: Bang Bang [MLBB] Free Redeem Codes April 2025](https://www.talkandroid.com/wp-content/uploads/2024/07/Screenshot_20240704-093036_Mobile-Legends-Bang-Bang.jpg)