Google Launches Sec-Gemini v1 AI Model to Enhance Cybersecurity
Originally published at ssojet Google’s Sec-Gemini model is an advanced AI tool designed for cybersecurity, enhancing SecOps workflows for root cause analysis, threat analysis, and understanding vulnerability impacts. Google Cybersecurity x AI Research Lead Elie Bursztein announced the release of Sec-Gemini v1, which combines the capabilities of Google Gemini’s Large Language Model (LLM) with real-time cybersecurity data. The model addresses the significant challenge that defenders face in securing systems against cyber threats. Attackers only need to exploit one vulnerability, whereas defenders must secure against all potential threats. AI-powered tools like Sec-Gemini aim to shift this balance back in favor of defenders, providing security analysts with faster insights into risks and threats associated with specific vulnerabilities. Sec-Gemini v1 integrates various data sources including Google Threat Intelligence (GTI), the Open-Source Vulnerabilities database (OSV), and Mandiant Threat intelligence data. It excels in key benchmarks such as the Cyber Threat Intelligence Multiple Choice Questions (CTI-MCQ) and Cybersecurity Threat Intelligence-Root Cause Mapping (CTI-RCM). Image courtesy of Google Performance and Capabilities Sec-Gemini v1 has outperformed other AI models in cybersecurity on critical benchmarks, scoring at least 11% higher on CTI-MCQ and 10.5% on CTI-RCM. This model is designed to assist security practitioners by providing comprehensive answers to cybersecurity questions. For example, it accurately identifies threat actors such as Salt Typhoon and contextualizes vulnerabilities based on threat intelligence data. Image courtesy of Google The model's advantages stem from its integration with Google’s various data streams, including Mandiant and OSV, enabling it to provide timely and relevant cybersecurity insights. This capability allows security analysts to react more effectively to threats and vulnerabilities. Image courtesy of Google Access and Collaboration Opportunities Currently, access to Sec-Gemini v1 is limited to a select group of organizations for experimental purposes. Google aims to gather feedback on how security professionals can best utilize the model in their workflows, with early access provided to non-governmental and academic organizations. Google is keen to understand real-world applications of Sec-Gemini, emphasizing that feedback from users will help refine the model. As organizations explore AI's potential in cybersecurity, collaboration between researchers and Google is essential to identify effective use cases. Interested parties can request early access through the provided form, aiming to promote wider use of the technology while ensuring it meets the needs of security teams. Image courtesy of Google Implications for Cybersecurity Practices The introduction of models like Sec-Gemini reflects a growing trend towards integrating AI in cybersecurity practices. The need for tools that can efficiently process vast amounts of data is critical for security teams, as they face increasing threats. With capabilities to provide faster analysis and insights, Sec-Gemini could significantly enhance the operational efficiency of security professionals. As organizations adopt AI solutions, it is crucial to leverage these tools as complements to human expertise rather than replacements. Google’s initiative to open Sec-Gemini to the cybersecurity community demonstrates a commitment to collaborative innovation. For organizations looking to enhance their cybersecurity framework, SSOJet offers a competitive edge. With SSOJet's API-first platform, enterprises can implement secure Single Sign-On (SSO), Multi-Factor Authentication (MFA), and user management. SSOJet's solutions include directory sync, SAML, OIDC, and magic link authentication, enabling organizations to safeguard against breaches effectively. Explore SSOJet's offerings or contact us for more information on advanced authentication solutions tailored to your organization's needs.

Originally published at ssojet
Google’s Sec-Gemini model is an advanced AI tool designed for cybersecurity, enhancing SecOps workflows for root cause analysis, threat analysis, and understanding vulnerability impacts. Google Cybersecurity x AI Research Lead Elie Bursztein announced the release of Sec-Gemini v1, which combines the capabilities of Google Gemini’s Large Language Model (LLM) with real-time cybersecurity data.
The model addresses the significant challenge that defenders face in securing systems against cyber threats. Attackers only need to exploit one vulnerability, whereas defenders must secure against all potential threats. AI-powered tools like Sec-Gemini aim to shift this balance back in favor of defenders, providing security analysts with faster insights into risks and threats associated with specific vulnerabilities.
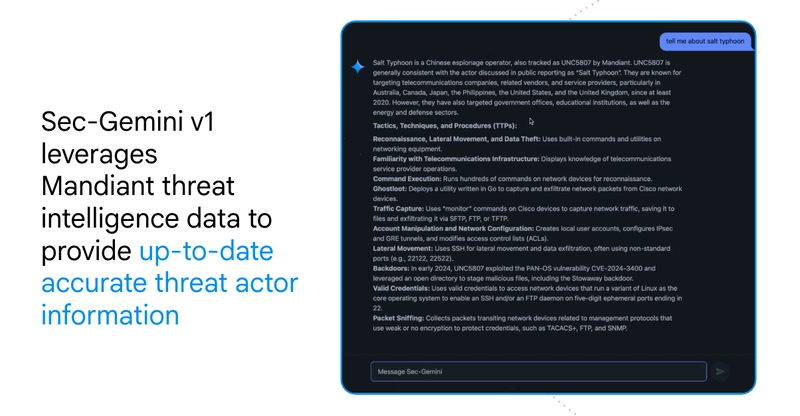
Sec-Gemini v1 integrates various data sources including Google Threat Intelligence (GTI), the Open-Source Vulnerabilities database (OSV), and Mandiant Threat intelligence data. It excels in key benchmarks such as the Cyber Threat Intelligence Multiple Choice Questions (CTI-MCQ) and Cybersecurity Threat Intelligence-Root Cause Mapping (CTI-RCM).
Image courtesy of Google
Performance and Capabilities
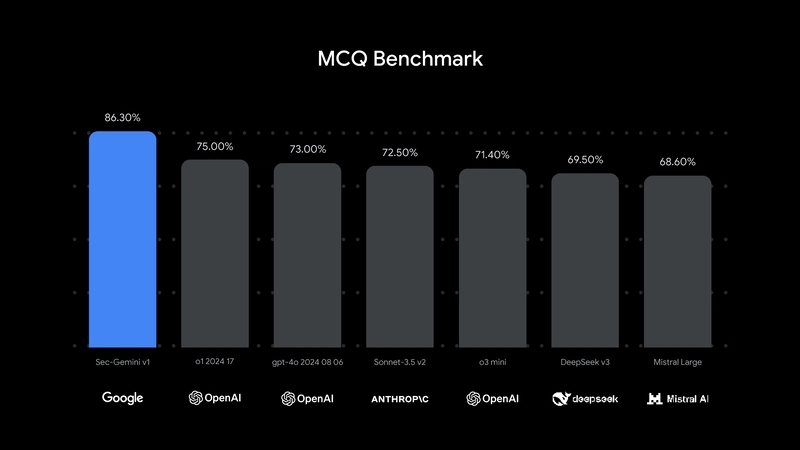
Sec-Gemini v1 has outperformed other AI models in cybersecurity on critical benchmarks, scoring at least 11% higher on CTI-MCQ and 10.5% on CTI-RCM. This model is designed to assist security practitioners by providing comprehensive answers to cybersecurity questions. For example, it accurately identifies threat actors such as Salt Typhoon and contextualizes vulnerabilities based on threat intelligence data.
Image courtesy of Google
The model's advantages stem from its integration with Google’s various data streams, including Mandiant and OSV, enabling it to provide timely and relevant cybersecurity insights. This capability allows security analysts to react more effectively to threats and vulnerabilities.
Image courtesy of Google
Access and Collaboration Opportunities
Currently, access to Sec-Gemini v1 is limited to a select group of organizations for experimental purposes. Google aims to gather feedback on how security professionals can best utilize the model in their workflows, with early access provided to non-governmental and academic organizations.
Google is keen to understand real-world applications of Sec-Gemini, emphasizing that feedback from users will help refine the model. As organizations explore AI's potential in cybersecurity, collaboration between researchers and Google is essential to identify effective use cases.
Interested parties can request early access through the provided form, aiming to promote wider use of the technology while ensuring it meets the needs of security teams.
Image courtesy of Google
Implications for Cybersecurity Practices
The introduction of models like Sec-Gemini reflects a growing trend towards integrating AI in cybersecurity practices. The need for tools that can efficiently process vast amounts of data is critical for security teams, as they face increasing threats. With capabilities to provide faster analysis and insights, Sec-Gemini could significantly enhance the operational efficiency of security professionals.
As organizations adopt AI solutions, it is crucial to leverage these tools as complements to human expertise rather than replacements. Google’s initiative to open Sec-Gemini to the cybersecurity community demonstrates a commitment to collaborative innovation.
For organizations looking to enhance their cybersecurity framework, SSOJet offers a competitive edge. With SSOJet's API-first platform, enterprises can implement secure Single Sign-On (SSO), Multi-Factor Authentication (MFA), and user management. SSOJet's solutions include directory sync, SAML, OIDC, and magic link authentication, enabling organizations to safeguard against breaches effectively.
Explore SSOJet's offerings or contact us for more information on advanced authentication solutions tailored to your organization's needs.








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




































































































































































































![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)
































.png?#)










-Baldur’s-Gate-3-The-Final-Patch---An-Animated-Short-00-03-43.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)











![Nanoleaf Announces New Pegboard Desk Dock With Dual-Sided Lighting [Video]](https://www.iclarified.com/images/news/97030/97030/97030-640.jpg)





















































































































![Apple's Foldable iPhone May Cost Between $2100 and $2300 [Rumor]](https://www.iclarified.com/images/news/97028/97028/97028-640.jpg)
![Apple Releases Public Betas of iOS 18.5, iPadOS 18.5, macOS Sequoia 15.5 [Download]](https://www.iclarified.com/images/news/97024/97024/97024-640.jpg)