EnvShare - A secured, Role-based Access way to share .env file
This is a submission for the Permit.io Authorization Challenge: API-First Authorization Reimagined What I Built I built an API-first, environment variable hosting service that demonstrates secure, role-based access to environment variables using Permit.io. The project solves the common problem of managing and sharing .env files in teams—preventing accidental leaks, insecure sharing, and misconfiguration—by centralizing environment variables behind a secure API. Access to each environment (dev, staging, prod) is strictly controlled by Permit.io roles and permissions, ensuring only authorized users can fetch the secrets they need. Demo Screenshots: Video: https://youtu.be/rKPC_3-ui7A Sample API Usage: # Fetch dev environment variables as a Developer curl -H "X-API-Key: dev1" http://localhost:3000/getEnv/dev # Fetch staging environment variables as a Manager curl -H "X-API-Key: manager1" http://localhost:3000/getEnv/staging # Fetch prod environment variables as a Director curl -H "X-API-Key: director1" http://localhost:3000/getEnv/prod See more in demo-commands.md. Project Repo GitHub Repo: permit-challenge Includes a thorough README.md with setup, usage, and Permit.io integration instructions. My Journey I started by defining the problem: .env file sprawl and the risks of manual sharing. My goal was to create a backend service that would serve environment variables securely, using Permit.io for fine-grained, role-based access control. The project was built in Agile sprints: Sprint 1: Project setup, Express server, and config structure. Sprint 2: Permit.io integration and robust error handling. Sprint 3: Demo scripts, documentation, and polish. Challenges: Mapping API keys to Permit.io users and roles required careful dashboard configuration. Ensuring error messages and status codes were consistent for a clean API experience. Debugging Permit.io PDP connectivity and resource naming conventions. What I learned: Permit.io makes it easy to add RBAC to any API, but planning your resource and role model up front is key. API-first authorization can be both secure and developer-friendly with the right tools and patterns. API-First Authorization Permit.io powers all access control in this project: Each environment (env:dev, env:staging, env:prod) is a Permit.io resource. Roles (Developer, Manager, Director) are mapped to users in the Permit.io dashboard and granted read permissions on the corresponding resources. The Express API checks authorization on every request using permit.check(user_key, 'read', resource), where user_key is the API key provided in the request header. All access decisions, including denials, are handled by Permit.io—making the API stateless and secure by design. Permit.io Setup Steps: Define resources for each environment in the dashboard. Create roles and assign read permissions. Add users with their API keys and assign roles. The API enforces these rules with a single call to Permit.io on each request. Team Submissions: Longmaba, Hoangmrb
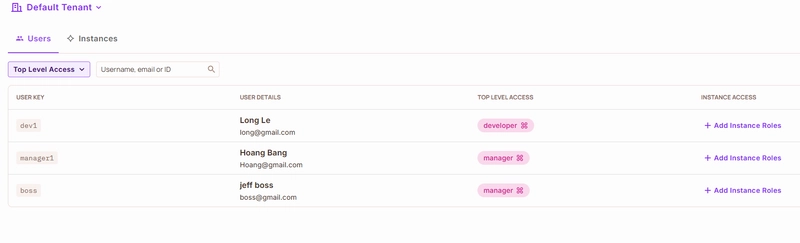
This is a submission for the Permit.io Authorization Challenge: API-First Authorization Reimagined
What I Built
I built an API-first, environment variable hosting service that demonstrates secure, role-based access to environment variables using Permit.io. The project solves the common problem of managing and sharing .env files in teams—preventing accidental leaks, insecure sharing, and misconfiguration—by centralizing environment variables behind a secure API. Access to each environment (dev, staging, prod) is strictly controlled by Permit.io roles and permissions, ensuring only authorized users can fetch the secrets they need.
Demo
Screenshots:
Video: https://youtu.be/rKPC_3-ui7A
Sample API Usage:
# Fetch dev environment variables as a Developer
curl -H "X-API-Key: dev1" http://localhost:3000/getEnv/dev
# Fetch staging environment variables as a Manager
curl -H "X-API-Key: manager1" http://localhost:3000/getEnv/staging
# Fetch prod environment variables as a Director
curl -H "X-API-Key: director1" http://localhost:3000/getEnv/prod
See more in demo-commands.md.
Project Repo
- Includes a thorough README.md with setup, usage, and Permit.io integration instructions.
My Journey
I started by defining the problem: .env file sprawl and the risks of manual sharing. My goal was to create a backend service that would serve environment variables securely, using Permit.io for fine-grained, role-based access control.
The project was built in Agile sprints:
- Sprint 1: Project setup, Express server, and config structure.
- Sprint 2: Permit.io integration and robust error handling.
- Sprint 3: Demo scripts, documentation, and polish.
Challenges:
- Mapping API keys to Permit.io users and roles required careful dashboard configuration.
- Ensuring error messages and status codes were consistent for a clean API experience.
- Debugging Permit.io PDP connectivity and resource naming conventions.
What I learned:
- Permit.io makes it easy to add RBAC to any API, but planning your resource and role model up front is key.
- API-first authorization can be both secure and developer-friendly with the right tools and patterns.
API-First Authorization
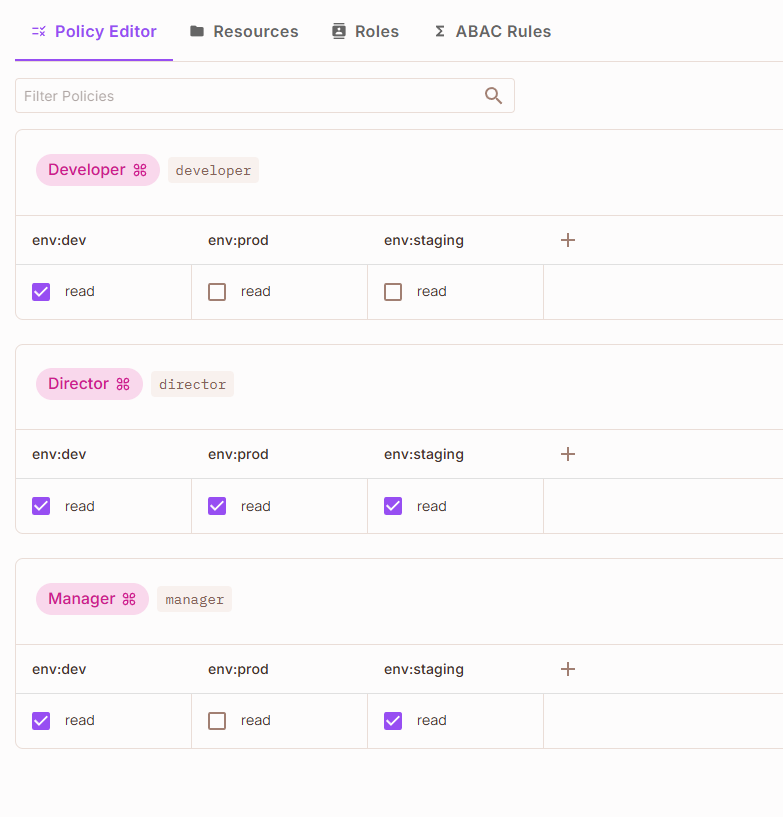
Permit.io powers all access control in this project:
- Each environment (
env:dev,env:staging,env:prod) is a Permit.io resource. - Roles (
Developer,Manager,Director) are mapped to users in the Permit.io dashboard and grantedreadpermissions on the corresponding resources. - The Express API checks authorization on every request using
permit.check(user_key, 'read', resource), whereuser_keyis the API key provided in the request header. - All access decisions, including denials, are handled by Permit.io—making the API stateless and secure by design.
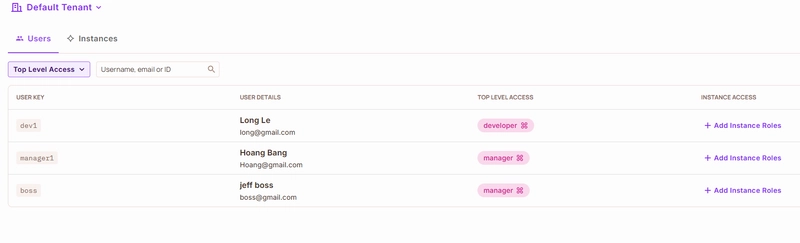
Permit.io Setup Steps:
- Define resources for each environment in the dashboard.
- Create roles and assign
readpermissions. - Add users with their API keys and assign roles.
- The API enforces these rules with a single call to Permit.io on each request.
Team Submissions: Longmaba, Hoangmrb
































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)






























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




















































































































_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




 CISO’s Core Focus.webp?#)







































































































![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)