Command the Crowd with Linux Group Management
It's Friday afternoon. Someone needs urgent access to production. Your boss is waiting. And you are manually updating permissions for the 17th time this week. There's a better way... Linux group management isn't just some dusty sysadmin skill, it's the difference between chaos and control in today's cloud first world. Companies scaling from 10 to 100 employees crash and burn without it. DevOps teams implementing zero-trust security depend on it. And yes, it might just save your weekend. Let's cut through the noise and master the commands that keep modern tech organizations running smoothly. What We're Tackling Today Introduction Creating Groups X-Ray Vision: Seeing Group Properties Group ID Management Without The Headaches The Two Commands That Handle 90% of User Management Mass User Management (Without Mass Confusion) Delegating Power Without Losing Control The Hidden File Most Admins Never Check Breaking Up With Groups (Cleanly) Summary Introduction Every Linux admin has a moment of realization: Managing permissions user-by-user is like trying to bail out a flooding server room with a coffee cup. Groups aren't just convenient, they're transformative. They turn the impossible task of managing hundreds of individual permissions into something you can handle before your morning standup. When your CI/CD pipeline breaks at 2 AM, you'll thank yourself for setting up proper deployment groups with specific access boundaries. "Show me an organization without proper group management, and I'll show you a company, one bad command away from problems." - Every senior Linux admin ever. Creating Groups # groupadd Simple? Yes. Powerful? Absolutely. But the real skill isn't running the command, it's knowing how to structure your groups. Instead of creating a random collection, think taxonomy: Function-based groups: developers, analysts, support. Project-based groups: alpha-project, beta-launch. Permission-level groups: prod-read, staging-write. In IT Reality: When you create sensible group structures, troubleshooting becomes intuitive. "Why can't Sarah access the logs?" Because she's in frontend-devs not logging-readers. Business Impact: Clear group structures mean clearer communication between IT and other departments. No more "I don't know why accounting can't access the reports folder." X-Ray Vision: Seeing Group Properties # grep /etc/group These commands reveal the wizard behind the curtain, showing you group membership, IDs, and structure. In IT Reality: During incident response, these commands help you quickly identify who has access to affected systems, streamlining your triage process. Business Impact: When compliance asks for an access report, you can deliver in minutes rather than days. Group ID Management Without The Headaches # groupmod -g Group IDs aren't just numbers, they're organizational DNA. Consistent ID management prevents permission conflicts and makes system mergers possible. In IT Reality: Automating deployments across multiple systems requires consistent GIDs, or your scripts will break in mysterious ways. Business Impact: When your company acquires another business, aligned group IDs make integrating their systems drastically simpler. The Two Commands That Handle 90% of User Management # gpasswd -a Damilola developers # Add Damilola to developers # gpasswd -d Damilola developers # Remove Damilola from developers These two commands will become your most typed Linux operations during onboarding and offboarding. In IT Reality: During a production incident, you can temporarily add a specialist to the right group, then remove them when resolved maintaining security while enabling fast response. Business Impact: Employee role changes happen in seconds, not days, dramatically reducing productivity gaps during transitions. Mass User Management (Without Mass Confusion) # gpasswd -M The power move of group administration. Reset an entire group's membership in one command. Warning!!!: This replaces ALL existing members. Miss one name, and you've just fired them (from the group, at least!). In IT Reality: Perfect for team reorganizations or quickly setting up identical access patterns across similar projects. Business Impact: When departments restructure, you can implement new access patterns immediately rather than becoming an access change bottleneck. Delegating Power Without Losing Control # gpasswd -A The truly enlightened admin doesn't do all the work, they delegate. This command makes Bob an administrator of the developers group. IT Reality: Team leads can manage their own group membership, freeing you from ticket hell while maintaining oversight. Business Impact: Department managers gain autonomy over their team's access without requiring constant IT intervention. The Hidden
It's Friday afternoon. Someone needs urgent access to production. Your boss is waiting. And you are manually updating permissions for the 17th time this week.
There's a better way...
Linux group management isn't just some dusty sysadmin skill, it's the difference between chaos and control in today's cloud first world. Companies scaling from 10 to 100 employees crash and burn without it. DevOps teams implementing zero-trust security depend on it. And yes, it might just save your weekend.
Let's cut through the noise and master the commands that keep modern tech organizations running smoothly.
What We're Tackling Today
- Introduction
- Creating Groups
- X-Ray Vision: Seeing Group Properties
- Group ID Management Without The Headaches
- The Two Commands That Handle 90% of User Management
- Mass User Management (Without Mass Confusion)
- Delegating Power Without Losing Control
- The Hidden File Most Admins Never Check
- Breaking Up With Groups (Cleanly)
- Summary
Introduction
Every Linux admin has a moment of realization: Managing permissions user-by-user is like trying to bail out a flooding server room with a coffee cup.
Groups aren't just convenient, they're transformative. They turn the impossible task of managing hundreds of individual permissions into something you can handle before your morning standup.
When your CI/CD pipeline breaks at 2 AM, you'll thank yourself for setting up proper deployment groups with specific access boundaries.
"Show me an organization without proper group management, and I'll show you a company, one bad command away from problems." - Every senior Linux admin ever.
Creating Groups
# groupadd
Simple? Yes. Powerful? Absolutely.
But the real skill isn't running the command, it's knowing how to structure your groups. Instead of creating a random collection, think taxonomy:
-
Function-based groups:
developers,analysts,support. -
Project-based groups:
alpha-project,beta-launch. -
Permission-level groups:
prod-read,staging-write.
In IT Reality: When you create sensible group structures, troubleshooting becomes intuitive. "Why can't Sarah access the logs?" Because she's in frontend-devs not logging-readers.
Business Impact: Clear group structures mean clearer communication between IT and other departments. No more "I don't know why accounting can't access the reports folder."
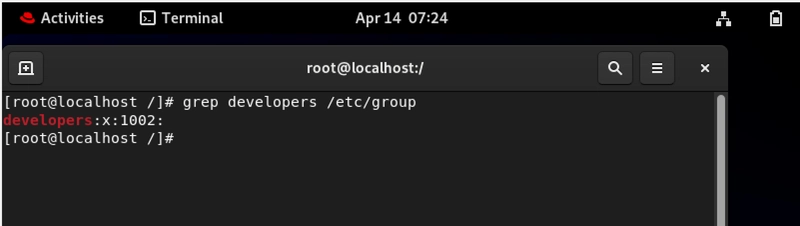
X-Ray Vision: Seeing Group Properties
# grep /etc/group
These commands reveal the wizard behind the curtain, showing you group membership, IDs, and structure.
In IT Reality: During incident response, these commands help you quickly identify who has access to affected systems, streamlining your triage process.
Business Impact: When compliance asks for an access report, you can deliver in minutes rather than days.
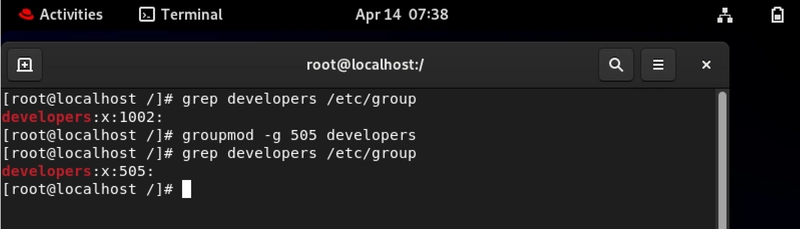
Group ID Management Without The Headaches
# groupmod -g
Group IDs aren't just numbers, they're organizational DNA. Consistent ID management prevents permission conflicts and makes system mergers possible.
In IT Reality: Automating deployments across multiple systems requires consistent GIDs, or your scripts will break in mysterious ways.
Business Impact: When your company acquires another business, aligned group IDs make integrating their systems drastically simpler.
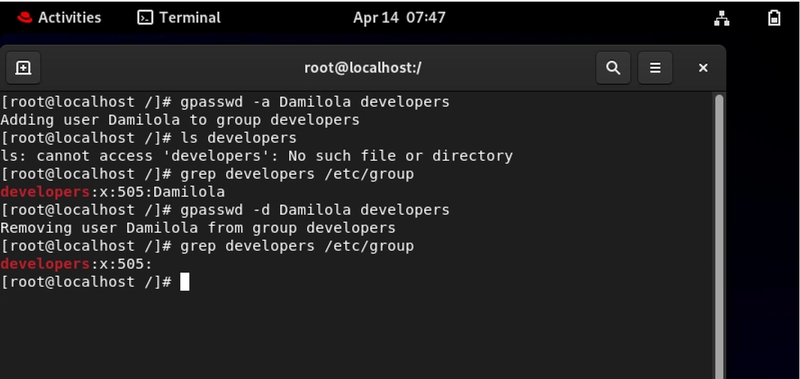
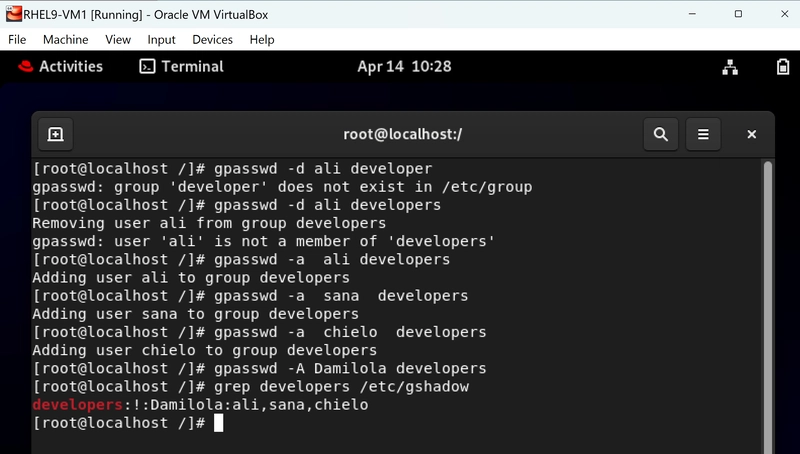
The Two Commands That Handle 90% of User Management
# gpasswd -a Damilola developers # Add Damilola to developers
# gpasswd -d Damilola developers # Remove Damilola from developers
These two commands will become your most typed Linux operations during onboarding and offboarding.
In IT Reality: During a production incident, you can temporarily add a specialist to the right group, then remove them when resolved maintaining security while enabling fast response.
Business Impact: Employee role changes happen in seconds, not days, dramatically reducing productivity gaps during transitions.
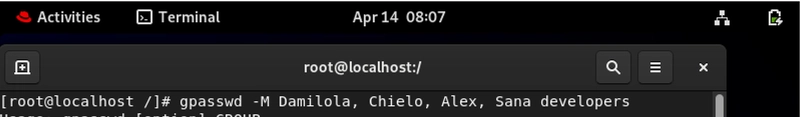
Mass User Management (Without Mass Confusion)
# gpasswd -M
The power move of group administration. Reset an entire group's membership in one command.
Warning!!!: This replaces ALL existing members. Miss one name, and you've just fired them (from the group, at least!).
In IT Reality: Perfect for team reorganizations or quickly setting up identical access patterns across similar projects.
Business Impact: When departments restructure, you can implement new access patterns immediately rather than becoming an access change bottleneck.
Delegating Power Without Losing Control
# gpasswd -A
The truly enlightened admin doesn't do all the work, they delegate. This command makes Bob an administrator of the developers group.
IT Reality: Team leads can manage their own group membership, freeing you from ticket hell while maintaining oversight.
Business Impact: Department managers gain autonomy over their team's access without requiring constant IT intervention.
The Hidden File Most Admins Never Check
# grep developers /etc/gshadow
This command reveals the usually ignored /etc/gshadow file home to group password and admin settings.
IT Reality: Auditing group administration rights can prevent privilege escalation vulnerabilities before they happen.
Business Impact: When regulatory compliance demands you prove separation of duties, this file contains the evidence you need.
Breaking Up With Groups (Cleanly)
# groupdel developers
Projects end. Teams dissolve. When groups are no longer needed, clean removal prevents permission sprawl.
IT Reality: Post project cleanup prevents orphaned permissions that complicate future deployments.
Business Impact: Proper group lifecycle management is key to passing security audits and maintaining least privilege principles.
Summary
Linux group management isn't just about running commands, it's about implementing a philosophy of access control.
The most successful organizations create:
- Consistent naming conventions everyone understands
- Hierarchical structures that mirror organizational reality
- Clear documentation of who goes where and why
- Regular audits to prevent permission drift
- Automation for repeatable, error-free management
When done right, Linux group management becomes invisible infrastructure, the kind that just works so well nobody notices until it's gone.
User-by-user management is a fast track to burnout and security holes. Proper group management isn't optional in modern environments, it's the foundation that makes everything else possible.
Your future self will thank you for mastering these commands today. Your security team will thank you tomorrow. And your business stakeholders will never know how much chaos you've saved them from.
That's the hallmark of true expertise: Making the complex look effortless.
If you enjoyed and learnt from this, drop a comment and connect with me on LinkedIn, cause I will like to connect with you too.
#30DaysLinuxChallenge #CloudWhistler #RedHat #CloudJourney #DevOps #Linux #OpenSource #CloudComputing #WomenInTech #RedHatEnterpriseLinux #ITInfrastructure #EnterpriseIT #Ansible #OpenShift #SysAdmin #Automation #CloudEngineer









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)



























































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)