Bug Bounty Hidden Treasures
What's Bug Bounty Bug bounty is a monetary reward given to ethical hackers for successfully discovering and reporting a vulnerability or bug in an application, API, or computer system. Bug bounty programs allow companies to leverage the hacker community to improve their systems’ security posture over time continuously. Hidden Treasures Bug bounty hunters thrive on uncovering vulnerabilities that others overlook, and some of the most rewarding finds come from hidden routes within an application. These routes, often undocumented or left exposed due to misconfigurations, can lead to critical areas such as admin panels, debug endpoints, or forgotten API endpoints. Attackers who discover these paths can manipulate backend systems, access sensitive data, or even take control of critical functionalities. By carefully mapping an application’s structure and testing unconventional input, hunters can reveal these concealed attack surfaces. Another lucrative area for discovery lies in deployed but unknown features—those pushed into production without proper security vetting. Developers sometimes leave experimental or beta functionalities accessible via specific parameters or headers, unaware that they can be exploited. These features may bypass authentication, introduce unintended behaviors, or expose sensitive internal tools. A skilled hunter knows how to probe for such hidden mechanisms by analyzing application requests, reviewing JavaScript files, and testing feature flags to unlock functionalities that shouldn’t be publicly accessible. Decommissioned features lingering in production are another goldmine. Organizations may retire certain functionalities but fail to fully remove their backend components, leaving old endpoints or outdated authentication mechanisms still operational. These forgotten elements often lack modern security protections, making them prime targets for exploitation. By identifying and testing legacy endpoints or accessing outdated documentation, hunters can uncover these remnants and turn them into high-value reports before malicious actors do. How I Found One of Those Treasures I've been doing bug bounties since 2018, and over the years have learned a thing or two on how to approach a target that may seem difficult or unhackable. I had a target.com that I found online that offers great bounties for their cloud assets. After the enumeration of all subdomains, I picked one that looked interesting to hack on. I utilized ffuf to enumerate directories since it's faster and also has great flags that can help you get the results you want. I discovered quite a number of directories that looked like normal stuff and un interesting. I then discovered one called "/system/ which seemed more interesting and fun to probe further. I fuzzed it, and then I discovered an endpoint "/system/auth" that allowed users to authenticate to the application via a login form, as shown below. This was not the normal endpoint for authentication to that application, but a way system administrators used to get to the application. The fun bit of it was that they used default credentials to access the console as shown above. This may seem like a trivial hack, but its impact was massive to the organization since the console was a central place where multiple client workloads were, as shown below The above finding paid a 4-figure bounty. Sounds easy but gets paid a lot based on impact Key Takeaways Based on the example given above, hidden elements present high-value opportunities for bug bounty hunters who know where to look. Some of the things to look for are: Hidden Routes in Applications Undocumented admin panels, debug endpoints, and API paths can expose critical functionality. Mapping an application’s structure helps reveal concealed attack surfaces. Exploiting misconfigurations in routing can lead to data leaks or privilege escalation. Deployed but Unknown Features Experimental or beta features may be accessible via hidden parameters or headers. Poorly tested functionalities can bypass authentication or introduce unintended behaviors. Reviewing JavaScript files and application requests can expose hidden features. Decommissioned Features in Production Retired functionalities may still have active backend components, creating security gaps. Legacy endpoints often lack modern security protections, making them easy targets. Accessing outdated documentation or API references can uncover forgotten vulnerabilities. Conclusion Finding hidden treasures in bug bounty hunting requires patience, curiosity, and a keen eye for overlooked vulnerabilities. Whether it's discovering undocumented routes, probing deployed but forgotten features, or exploiting remnants of decommissioned functionalities, these hidden gems often lead to significant security findings. Skilled hunters who think outside the box, analyze applications t
What's Bug Bounty
Bug bounty is a monetary reward given to ethical hackers for successfully discovering and reporting a vulnerability or bug in an application, API, or computer system. Bug bounty programs allow companies to leverage the hacker community to improve their systems’ security posture over time continuously.
Hidden Treasures
Bug bounty hunters thrive on uncovering vulnerabilities that others overlook, and some of the most rewarding finds come from hidden routes within an application. These routes, often undocumented or left exposed due to misconfigurations, can lead to critical areas such as admin panels, debug endpoints, or forgotten API endpoints. Attackers who discover these paths can manipulate backend systems, access sensitive data, or even take control of critical functionalities. By carefully mapping an application’s structure and testing unconventional input, hunters can reveal these concealed attack surfaces.
Another lucrative area for discovery lies in deployed but unknown features—those pushed into production without proper security vetting. Developers sometimes leave experimental or beta functionalities accessible via specific parameters or headers, unaware that they can be exploited. These features may bypass authentication, introduce unintended behaviors, or expose sensitive internal tools. A skilled hunter knows how to probe for such hidden mechanisms by analyzing application requests, reviewing JavaScript files, and testing feature flags to unlock functionalities that shouldn’t be publicly accessible.
Decommissioned features lingering in production are another goldmine. Organizations may retire certain functionalities but fail to fully remove their backend components, leaving old endpoints or outdated authentication mechanisms still operational. These forgotten elements often lack modern security protections, making them prime targets for exploitation. By identifying and testing legacy endpoints or accessing outdated documentation, hunters can uncover these remnants and turn them into high-value reports before malicious actors do.
How I Found One of Those Treasures
I've been doing bug bounties since 2018, and over the years have learned a thing or two on how to approach a target that may seem difficult or unhackable. I had a target.com that I found online that offers great bounties for their cloud assets. After the enumeration of all subdomains, I picked one that looked interesting to hack on.
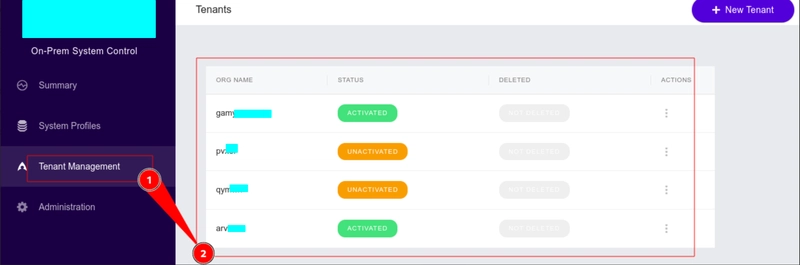
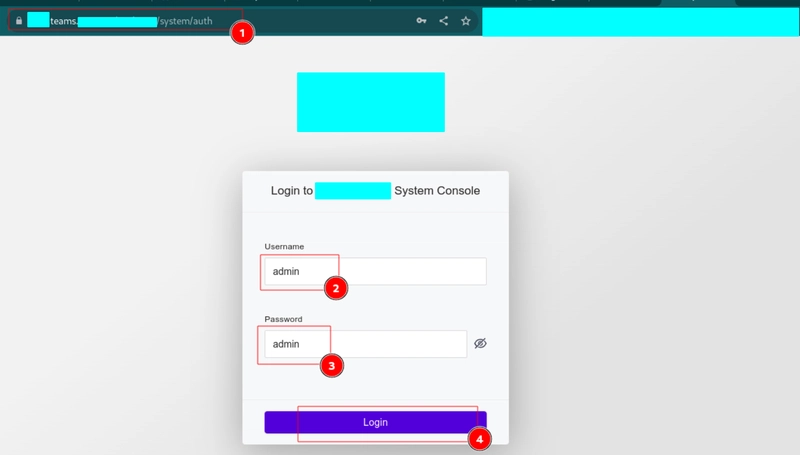
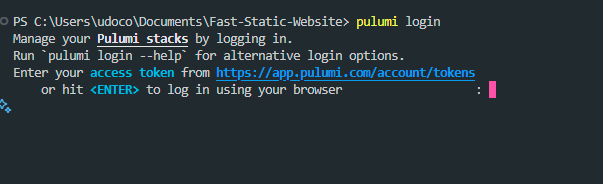
I utilized ffuf to enumerate directories since it's faster and also has great flags that can help you get the results you want. I discovered quite a number of directories that looked like normal stuff and un interesting. I then discovered one called "/system/ which seemed more interesting and fun to probe further. I fuzzed it, and then I discovered an endpoint "/system/auth" that allowed users to authenticate to the application via a login form, as shown below.
This was not the normal endpoint for authentication to that application, but a way system administrators used to get to the application. The fun bit of it was that they used default credentials to access the console as shown above. This may seem like a trivial hack, but its impact was massive to the organization since the console was a central place where multiple client workloads were, as shown below
The above finding paid a 4-figure bounty. Sounds easy but gets paid a lot based on impact
Key Takeaways
Based on the example given above, hidden elements present high-value opportunities for bug bounty hunters who know where to look. Some of the things to look for are:
Hidden Routes in Applications
Undocumented admin panels, debug endpoints, and API paths can expose critical functionality.
Mapping an application’s structure helps reveal concealed attack surfaces.
Exploiting misconfigurations in routing can lead to data leaks or privilege escalation.
Deployed but Unknown Features
Experimental or beta features may be accessible via hidden parameters or headers.
Poorly tested functionalities can bypass authentication or introduce unintended behaviors.
Reviewing JavaScript files and application requests can expose hidden features.
Decommissioned Features in Production
Retired functionalities may still have active backend components, creating security gaps.
Legacy endpoints often lack modern security protections, making them easy targets.
Accessing outdated documentation or API references can uncover forgotten vulnerabilities.
Conclusion
Finding hidden treasures in bug bounty hunting requires patience, curiosity, and a keen eye for overlooked vulnerabilities. Whether it's discovering undocumented routes, probing deployed but forgotten features, or exploiting remnants of decommissioned functionalities, these hidden gems often lead to significant security findings. Skilled hunters who think outside the box, analyze applications thoroughly, and test unconventional attack surfaces can uncover critical weaknesses before malicious actors do. In the ever-evolving world of cybersecurity, the real rewards lie in what others fail to see. Keep digging—you never know what hidden bounty awaits!










































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)




































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)