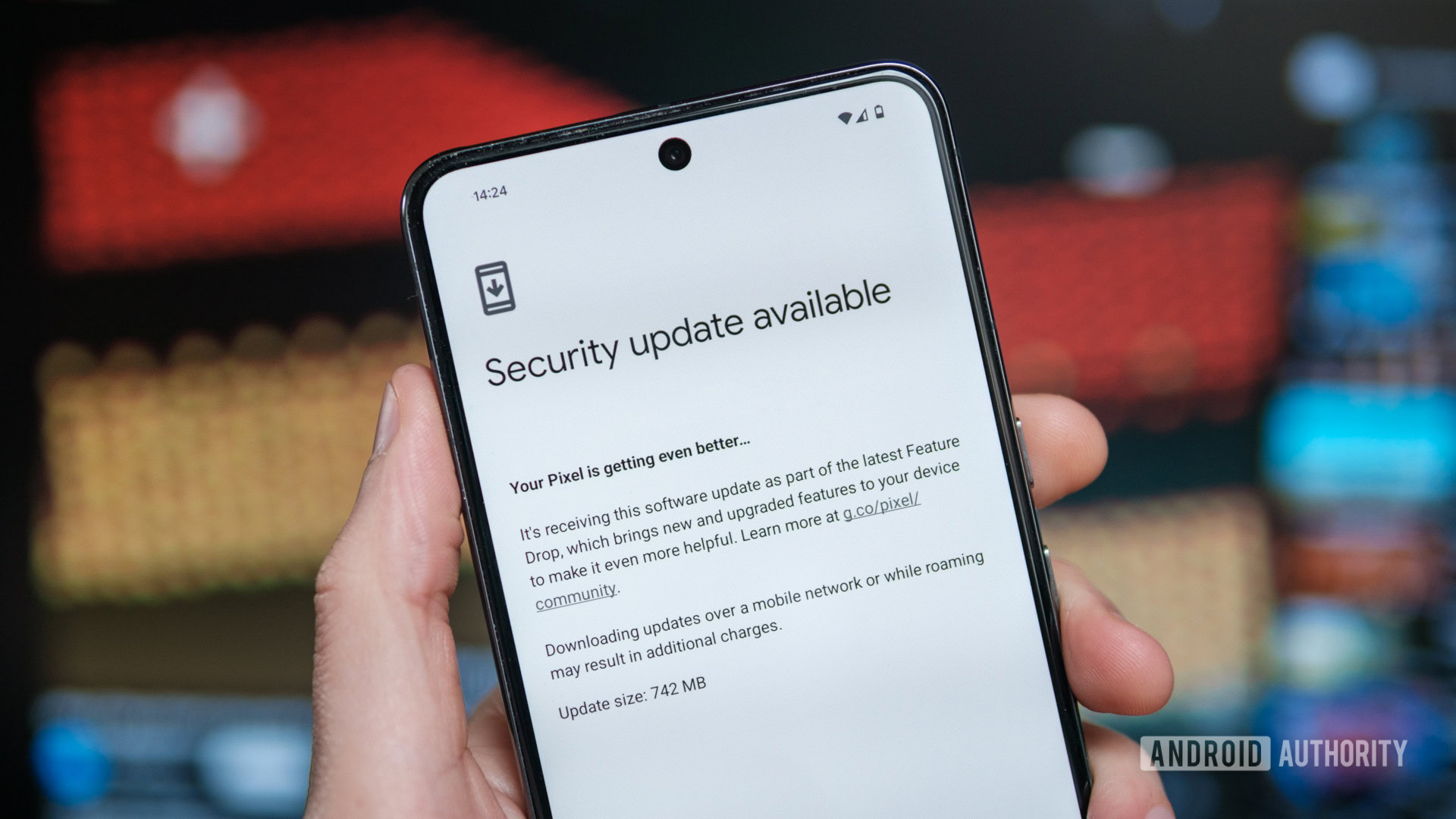
Beware of $5 SMS Phishing Attack Targeting Toll Road Users
A widespread and ongoing SMS phishing (smishing) campaign targeting toll road users across the United States has been identified, posing a significant threat to motorists’ financial security. Since mid-October 2024, cybercriminals have been impersonating legitimate toll road payment services such as E-ZPass to steal credit card information from unsuspecting victims. The attackers have concentrated their […] The post Beware of $5 SMS Phishing Attack Targeting Toll Road Users appeared first on Cyber Security News.

A widespread and ongoing SMS phishing (smishing) campaign targeting toll road users across the United States has been identified, posing a significant threat to motorists’ financial security.
Since mid-October 2024, cybercriminals have been impersonating legitimate toll road payment services such as E-ZPass to steal credit card information from unsuspecting victims.
The attackers have concentrated their efforts on at least eight states, including Washington, Florida, Pennsylvania, Virginia, Texas, Ohio, Illinois, and Kansas.
The smishing messages inform recipients of an outstanding toll balance, typically under $5, and warn of potential late fees of approximately $35 if payment is not made promptly.
The messages include a hyperlink to a spoofed domain that mimics official toll collection services.
To create a sense of urgency, the text threatens “penalties or legal action” if the recipient fails to pay by a specified date, prompting immediate action from concerned motorists.
“Please settle your toll immediately after reading this message to avoid penalties for delaying the payment.
Thank you for your cooperation,” reads one sample message analyzed in the investigation. The attackers employ typosquatted domains with names containing state abbreviations to enhance the appearance of legitimacy.
Cisco Talos analysts identified the campaign through extensive monitoring of phishing infrastructure and message patterns.
Their research indicates with moderate confidence that multiple financially motivated threat actors are utilizing a common smishing kit developed by an individual known as “Wang Duo Yu” to execute these attacks.
.webp)
Upon clicking the link in the SMS message, victims are directed through a sophisticated phishing flow designed to harvest personal and financial information.
First, users encounter a fake CAPTCHA challenge, after which they are redirected to a counterfeit webpage displaying the legitimate toll service’s logo. This page requests the victim’s name and ZIP code, ostensibly to view their bill.
Phishing Flow Analysis
The technical sophistication of the attack lies in its multi-stage approach. After entering initial information, victims are presented with a fraudulent bill displaying their name and an outstanding balance of approximately $4, along with warnings about a $35 late payment fee.
.webp)
When victims click the “Proceed Now” button, they are redirected to another fake webpage that solicits comprehensive personal information including name, address, phone number, and credit card details.
The phishing infrastructure utilizes domains created between October 2024 and March 2025, resolving to several IP addresses (45.152.115.161, 82.147.88.22, and more recently 43.156.47.209).
.webp)
Domain names are carefully crafted to impersonate legitimate toll services, such as “e-zpass.com-etcjr.xin” and “txtag.vipsf.top,” enhancing the credibility of the scam.
The ongoing registration of new domains as recently as March 2025 indicates that this campaign remains active, highlighting the need for continued vigilance among toll road users nationwide.
Equip your team with real-time threat analysis With ANY.RUN’s interactive cloud sandbox -> Try 14-day Free Trial
The post Beware of $5 SMS Phishing Attack Targeting Toll Road Users appeared first on Cyber Security News.








































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




































































































































































































![Blue Archive tier list [April 2025]](https://media.pocketgamer.com/artwork/na-33404-1636469504/blue-archive-screenshot-2.jpg?#)
































.png?#)









-Baldur’s-Gate-3-The-Final-Patch---An-Animated-Short-00-03-43.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)































































































































![Apple to Split Enterprise and Western Europe Roles as VP Exits [Report]](https://www.iclarified.com/images/news/97032/97032/97032-640.jpg)
![Nanoleaf Announces New Pegboard Desk Dock With Dual-Sided Lighting [Video]](https://www.iclarified.com/images/news/97030/97030/97030-640.jpg)

![Apple's Foldable iPhone May Cost Between $2100 and $2300 [Rumor]](https://www.iclarified.com/images/news/97028/97028/97028-640.jpg)






































































































































