Auto-Scaling Web Application with CI/CD Pipeline on AWS
Objective: Deploy a highly available, scalable, and secure web application on Amazon EC2 using Terraform, Ansible, and AWS DevOps tools. Step 1: Setting Up My AWS Environment First, I made sure I had the necessary tools installed on my system: sudo apt update && sudo apt install -y terraform ansible awscli Then, I configured AWS CLI with my credentials: aws configure Step 2: Writing Terraform Code to Provision AWS Infrastructure I created a project directory and initialized Terraform: mkdir ec2-project && cd ec2-project mkdir terraform && cd terraform terraform init Then, I wrote my Terraform configuration files: main.tf - Setting Up AWS VPC and Subnets provider "aws" { region = "us-east-1" } resource "aws_vpc" "main_vpc" { cidr_block = "10.0.0.0/16" tags = { Name = "MainVPC" } } resource "aws_subnet" "public_subnet" { vpc_id = aws_vpc.main_vpc.id cidr_block = "10.0.1.0/24" map_public_ip_on_launch = true availability_zone = "us-east-1a" tags = { Name = "PublicSubnet" } } resource "aws_internet_gateway" "gw" { vpc_id = aws_vpc.main_vpc.id tags = { Name = "MainIGW" } } resource "aws_route_table" "public_rt" { vpc_id = aws_vpc.main_vpc.id route { cidr_block = "0.0.0.0/0" gateway_id = aws_internet_gateway.gw.id } } resource "aws_route_table_association" "public_association" { subnet_id = aws_subnet.public_subnet.id route_table_id = aws_route_table.public_rt.id } security_groups.tf - Setting Up Security resource "aws_security_group" "web_sg" { vpc_id = aws_vpc.main_vpc.id ingress { from_port = 80 to_port = 80 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } ingress { from_port = 22 to_port = 22 protocol = "tcp" cidr_blocks = ["0.0.0.0/0"] } egress { from_port = 0 to_port = 0 protocol = "-1" cidr_blocks = ["0.0.0.0/0"] } tags = { Name = "WebSecurityGroup" } } ec2.tf - Launching My EC2 Instance resource "aws_instance" "web_server" { ami = "ami-0c55b159cbfafe1f0" instance_type = "t2.micro" subnet_id = aws_subnet.public_subnet.id security_groups = [aws_security_group.web_sg.name] key_name = "ec2-key" user_data = file("install_apache.sh") tags = { Name = "WebServer" } } install_apache.sh - Automating Apache Installation #!/bin/bash sudo yum update -y sudo yum install -y httpd sudo systemctl start httpd sudo systemctl enable httpd echo "Welcome to My AWS EC2 Web App" | sudo tee /var/www/html/index.html Deploying with Terraform Once everything was set up, I ran: terraform apply -auto-approve This successfully launched my EC2 instance with Apache installed. Step 3: Configuring My EC2 Instance with Ansible After Terraform deployed my infrastructure, I configured the EC2 instance using Ansible. First, I created an Ansible inventory file with my EC2 public IP: [web_servers] ansible_user=ec2-user ansible_ssh_private_key_file=~/.ssh/id_rsa Then, I wrote an Ansible playbook (deploy.yml): - name: Configure Web Server hosts: web_servers become: yes tasks: - name: Install Apache yum: name: httpd state: present - name: Start Apache service: name: httpd state: started enabled: yes - name: Deploy Web Page copy: content: "Deployed via Ansible!" dest: /var/www/html/index.html I executed the playbook: ansible-playbook -i inventory.ini deploy.yml Apache was installed, and my webpage was deployed. Step 4: Setting Up a CI/CD Pipeline with AWS CodePipeline To automate deployments, I set up AWS CodePipeline with the following stages: Source Stage (AWS CodeCommit) I created a Git repository in AWS CodeCommit and pushed my project code. Build Stage (AWS CodeBuild) I created a buildspec.yml file: version: 0.2 phases: install: commands: - yum install -y httpd build: commands: - echo "Building the application..." post_build: commands: - echo "Build completed!" Deploy Stage (AWS CodeDeploy) I used AWS CodeDeploy to deploy new versions of my app. Step 5: Monitoring and Security I ensured high availability and security by: ✅ Enabling AWS CloudWatch for monitoring. ✅ Setting Up AWS CloudTrail to log API calls. ✅ Using IAM Policies to restrict access. Final Deliverables 1) Terraform Code to automate infrastructure deployment. 2) Ansible Playbook to configure and deploy the app. 3) CI/CD Pipeline for automated deployments. 4) GitHub Repository with Documentation. 4) Demo Video of the entire process.
Objective:
Deploy a highly available, scalable, and secure web application on Amazon EC2 using Terraform, Ansible, and AWS DevOps tools.
Step 1: Setting Up My AWS Environment
First, I made sure I had the necessary tools installed on my system:
sudo apt update && sudo apt install -y terraform ansible awscli
Then, I configured AWS CLI with my credentials:
aws configure
Step 2: Writing Terraform Code to Provision AWS Infrastructure
I created a project directory and initialized Terraform:
mkdir ec2-project && cd ec2-project
mkdir terraform && cd terraform
terraform init
Then, I wrote my Terraform configuration files:
- main.tf - Setting Up AWS VPC and Subnets
provider "aws" {
region = "us-east-1"
}
resource "aws_vpc" "main_vpc" {
cidr_block = "10.0.0.0/16"
tags = { Name = "MainVPC" }
}
resource "aws_subnet" "public_subnet" {
vpc_id = aws_vpc.main_vpc.id
cidr_block = "10.0.1.0/24"
map_public_ip_on_launch = true
availability_zone = "us-east-1a"
tags = { Name = "PublicSubnet" }
}
resource "aws_internet_gateway" "gw" {
vpc_id = aws_vpc.main_vpc.id
tags = { Name = "MainIGW" }
}
resource "aws_route_table" "public_rt" {
vpc_id = aws_vpc.main_vpc.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.gw.id
}
}
resource "aws_route_table_association" "public_association" {
subnet_id = aws_subnet.public_subnet.id
route_table_id = aws_route_table.public_rt.id
}
- security_groups.tf - Setting Up Security
resource "aws_security_group" "web_sg" {
vpc_id = aws_vpc.main_vpc.id
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = { Name = "WebSecurityGroup" }
}
- ec2.tf - Launching My EC2 Instance
resource "aws_instance" "web_server" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = "t2.micro"
subnet_id = aws_subnet.public_subnet.id
security_groups = [aws_security_group.web_sg.name]
key_name = "ec2-key"
user_data = file("install_apache.sh")
tags = { Name = "WebServer" }
}
- install_apache.sh - Automating Apache Installation
#!/bin/bash
sudo yum update -y
sudo yum install -y httpd
sudo systemctl start httpd
sudo systemctl enable httpd
echo "Welcome to My AWS EC2 Web App
" | sudo tee /var/www/html/index.html
- Deploying with Terraform Once everything was set up, I ran:
terraform apply -auto-approve
This successfully launched my EC2 instance with Apache installed.
Step 3: Configuring My EC2 Instance with Ansible
After Terraform deployed my infrastructure, I configured the EC2 instance using Ansible.
First, I created an Ansible inventory file with my EC2 public IP:
[web_servers]
ansible_user=ec2-user ansible_ssh_private_key_file=~/.ssh/id_rsa
Then, I wrote an Ansible playbook (deploy.yml):
- name: Configure Web Server
hosts: web_servers
become: yes
tasks:
- name: Install Apache
yum:
name: httpd
state: present
- name: Start Apache
service:
name: httpd
state: started
enabled: yes
- name: Deploy Web Page
copy:
content: "Deployed via Ansible!
"
dest: /var/www/html/index.html
I executed the playbook:
ansible-playbook -i inventory.ini deploy.yml
Apache was installed, and my webpage was deployed.
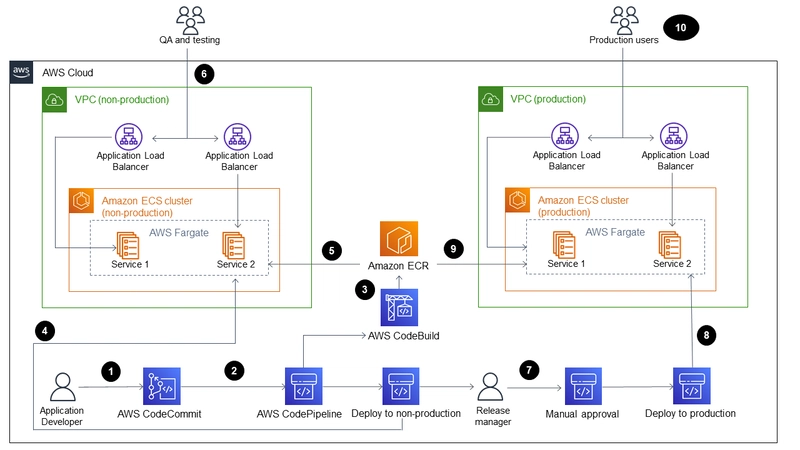
Step 4: Setting Up a CI/CD Pipeline with AWS CodePipeline
To automate deployments, I set up AWS CodePipeline with the following stages:
- Source Stage (AWS CodeCommit) I created a Git repository in AWS CodeCommit and pushed my project code.
- Build Stage (AWS CodeBuild) I created a buildspec.yml file:
version: 0.2
phases:
install:
commands:
- yum install -y httpd
build:
commands:
- echo "Building the application..."
post_build:
commands:
- echo "Build completed!"
- Deploy Stage (AWS CodeDeploy) I used AWS CodeDeploy to deploy new versions of my app.
Step 5: Monitoring and Security
I ensured high availability and security by:
✅ Enabling AWS CloudWatch for monitoring.
✅ Setting Up AWS CloudTrail to log API calls.
✅ Using IAM Policies to restrict access.
Final Deliverables
1) Terraform Code to automate infrastructure deployment.
2) Ansible Playbook to configure and deploy the app.
3) CI/CD Pipeline for automated deployments.
4) GitHub Repository with Documentation.
4) Demo Video of the entire process.












































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)

























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)





































































































.png?#)





.jpg?#)






























_Christophe_Coat_Alamy.jpg?#)





































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)