A Guide to the MITRE ATT&CK Framework: Understanding Tactics & Techniques
If you’ve just dipped your toes into cybersecurity, you’ve probably heard conversations about MITRE ATT&CK. But what is it really? Is it a tool? A framework? What is MITRE ATT&CK? MITRE ATT&CK stands for: Adversarial Tactics, Techniques, and Common Knowledge It’s like a massive cheat sheet—but instead of helping you win a game, it helps security teams understand how real-world hackers operate, step by step. Created by MITRE (a non-profit that works with the U.S. government), the ATT&CK framework is a publicly available knowledge base of tactics and techniques that bad actors use when attacking systems. Imagine you're designing a fortress. To protect it well, you need to know: How attackers typically sneak in (Initial Access) What they do once inside (Execution, Persistence, etc.) How they steal stuff (Exfiltration) That’s what MITRE ATT&CK lays out—for computers instead of castles. MITRE ATT&CK Matrix When you look at the MITRE ATT&CK Matrix, it looks like a giant table with columns and rows. Each column represents a Tactic (aka hacker’s goal), and each row contains Techniques (aka the methods used to achieve that goal). Some common Tactics include: Tactic What it means Initial Access How they get in Execution How they run malicious code Persistence How they stay even after a reboot Credential Access How they steal usernames/passwords Exfiltration How they take data out And under each tactic, there are Techniques like: Phishing emails PowerShell commands Keylogging File transfer tools Why Is ATT&CK So Important? Let’s say you're a cybersecurity analyst defending a company. The ATT&CK framework helps you: Understand how real attackers work Model threats and simulate possible attacks Find gaps in your defenses Prioritize what you need to fix first Test your detection tools Instead of blindly installing a bunch of firewalls, you can use ATT&CK to build a smart, targeted defense based on how real-world hackers operate. Wrapping up You don’t need to be a hacker or security guru to start using MITRE ATT&CK. Even beginners can: Explore the matrix and learn about tactics and techniques Watch videos that explain common attack flows Practice spotting attacks using real-world case studies If you're learning cybersecurity, ATT&CK is a fantastic map of the enemy territory. The more familiar you are with it, the stronger your security mindset becomes. If you're a software developer who enjoys exploring different technologies and techniques like this one, check out LiveAPI. It’s a super-convenient tool that lets you generate interactive API docs instantly. So, if you’re working with a codebase that lacks documentation, just use LiveAPI to generate it and save time! You can instantly try it out here!
If you’ve just dipped your toes into cybersecurity, you’ve probably heard conversations about MITRE ATT&CK. But what is it really? Is it a tool? A framework?
What is MITRE ATT&CK?
MITRE ATT&CK stands for:
Adversarial Tactics, Techniques, and Common Knowledge
It’s like a massive cheat sheet—but instead of helping you win a game, it helps security teams understand how real-world hackers operate, step by step.
Created by MITRE (a non-profit that works with the U.S. government), the ATT&CK framework is a publicly available knowledge base of tactics and techniques that bad actors use when attacking systems.
Imagine you're designing a fortress. To protect it well, you need to know:
- How attackers typically sneak in (Initial Access)
- What they do once inside (Execution, Persistence, etc.)
- How they steal stuff (Exfiltration)
That’s what MITRE ATT&CK lays out—for computers instead of castles.
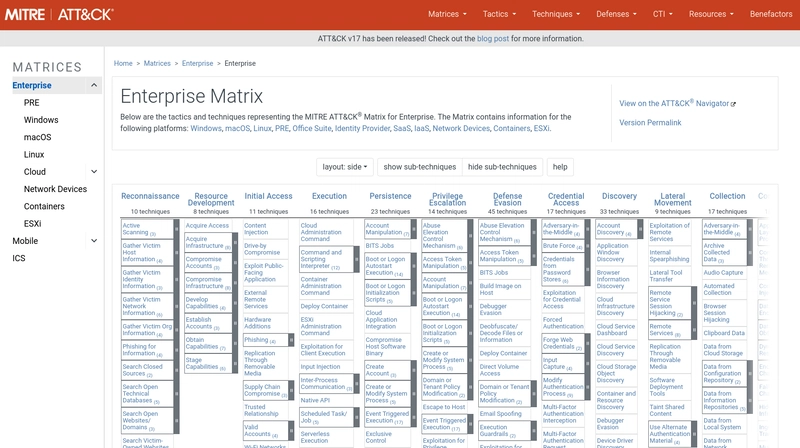
MITRE ATT&CK Matrix
When you look at the MITRE ATT&CK Matrix, it looks like a giant table with columns and rows. Each column represents a Tactic (aka hacker’s goal), and each row contains Techniques (aka the methods used to achieve that goal).
Some common Tactics include:
| Tactic | What it means |
|---|---|
| Initial Access | How they get in |
| Execution | How they run malicious code |
| Persistence | How they stay even after a reboot |
| Credential Access | How they steal usernames/passwords |
| Exfiltration | How they take data out |
And under each tactic, there are Techniques like:
- Phishing emails
- PowerShell commands
- Keylogging
- File transfer tools
Why Is ATT&CK So Important?
Let’s say you're a cybersecurity analyst defending a company. The ATT&CK framework helps you:
Understand how real attackers work
Model threats and simulate possible attacks
Find gaps in your defenses
Prioritize what you need to fix first
Test your detection tools
Instead of blindly installing a bunch of firewalls, you can use ATT&CK to build a smart, targeted defense based on how real-world hackers operate.
Wrapping up
You don’t need to be a hacker or security guru to start using MITRE ATT&CK. Even beginners can:
- Explore the matrix and learn about tactics and techniques
- Watch videos that explain common attack flows
- Practice spotting attacks using real-world case studies
If you're learning cybersecurity, ATT&CK is a fantastic map of the enemy territory. The more familiar you are with it, the stronger your security mindset becomes.
If you're a software developer who enjoys exploring different technologies and techniques like this one, check out LiveAPI. It’s a super-convenient tool that lets you generate interactive API docs instantly.
So, if you’re working with a codebase that lacks documentation, just use LiveAPI to generate it and save time!
You can instantly try it out here!



































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




















































































































































































.jpg?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)























































.jpg?#)













































































































































![Apple to Shift Robotics Unit From AI Division to Hardware Engineering [Report]](https://www.iclarified.com/images/news/97128/97128/97128-640.jpg)

![Apple Shares New Ad for iPhone 16: 'Trust Issues' [Video]](https://www.iclarified.com/images/news/97125/97125/97125-640.jpg)