User Management in Red Hat Linux: Proven Strategies and Practical Use Cases
Managing users is one of the most important parts of working with any Red Hat Linux system. Whether you're handling a handful of users or supporting an entire organization, good user management helps keep things secure, organized, and running smoothly. In this article, we’ll cover everything from the basics to more advanced techniques, using real-world examples to show how these best practices play out in everyday situations. Table of Contents Introduction The Basics of User Management in Red Hat Linux Core Commands for User Management Group Management Privilege Management and Sudo Setup Real-World Scenarios and Use Cases Best Practices and Tips Conclusion References Introduction In any enterprise or even small business setting, managing users effectively is critical for ensuring security and operational efficiency. In Red Hat Linux, user management is not just about creating or deleting accounts; it extends to configuring permissions, managing groups, and controlling access through tools like sudo. This article demystifies user management on Red Hat Linux, providing you with actionable insights and examples that you can apply in real-life scenarios. This isn't confined to just Redhat Linux; it applies to other distributions as well, such as Fedora, CentOS, Kali, Ubuntu, and more. The Basics of User Management in Red Hat Linux Understanding System Files User-related data is stored in several key files: /etc/passwd: Contains user account information such as username, UID, home directory, and default shell. /etc/shadow: Stores encrypted password information and password aging details. /etc/group: Lists group accounts, associated users, and group IDs (GID). Understanding the role of these files is essential, as they serve as the foundation for all user management operations on your system. Essential Commands for Managing Users The Linux command line offers a set of commands designed for user management: Creating a User: To create a new user, use the useradd command. Example: useradd Martins passwd Martins This will create the user "Martins" and secure password. Modifying a User: To modify a user’s settings, the usermod command comes in handy. Example: sudo usermod -aG developers Martins This adds the user "Martins" to the "developers" group. Important note: When you use the -G option without the -a option in the usermod command to add a user to a group, it has a significant effect: it replaces the user's supplementary groups with the specified ones rather than just adding the user to the new group(s) while keeping their existing groups. Use "id Martins" to view the primary and secondary group user belong Deleting a User: To remove a user, use the userdel command. Example: userdel -r Martins The -r flag will also delete the user’s home directory and mail spool. Each of these commands is straightforward but offers detailed control over user settings and permissions. Group Management Groups are essential for organizing users and managing permissions collectively. Red Hat Linux allows administrators to create, modify, and delete groups. Creating a Group: groupadd developers Adding a User to a Group: usermod -aG Developers Mary Removing a User from a Group: You can modify /etc/group manually or use tools like gpasswd. Example: gpasswd -d Mary Developers Managing groups efficiently can simplify the process of setting permissions across directories and applications, particularly when dealing with projects that require team collaboration. Privilege Management and Sudo Setup Granting administrative privileges only when necessary is a critical security best practice. The sudo command allows designated users to execute commands with root-level privileges, without sharing the root password. Configuring Sudo Access: Modify the /etc/sudoers file using the visudo command to ensure syntax integrity. Example: sudo visudo Add an entry like: Martins ALL=(ALL) ALL This line grants the user Martins permission to execute any command from any terminal. Properly setting up sudo not only fine-tunes security but also helps in audit logging and accountability. Real-World Scenarios and Use Cases Scenario 1: Managing a Development Team Imagine a mid-sized software company where multiple developers require access to specific directories and tools. The system administrator can: Create individual user accounts for each developer. Create a common developers group. Add users to the group to grant access to shared repositories and folders. Use sudo carefully to allow required system updates without compromising security. Scenario 2: University Lab Environment In a university computer lab, different students may share the same machines. The admin can: Set up temporary user accounts for lab sessions. Implement group restrictions so that each course has its own set of permissions. Periodically clean up accounts and reset passwords using scripted automation. These scenarios underline how thoug
Managing users is one of the most important parts of working with any Red Hat Linux system. Whether you're handling a handful of users or supporting an entire organization, good user management helps keep things secure, organized, and running smoothly. In this article, we’ll cover everything from the basics to more advanced techniques, using real-world examples to show how these best practices play out in everyday situations.
Table of Contents
- Introduction
- The Basics of User Management in Red Hat Linux
- Core Commands for User Management
- Group Management
- Privilege Management and Sudo Setup
- Real-World Scenarios and Use Cases
- Best Practices and Tips
- Conclusion
- References
Introduction
In any enterprise or even small business setting, managing users effectively is critical for ensuring security and operational efficiency. In Red Hat Linux, user management is not just about creating or deleting accounts; it extends to configuring permissions, managing groups, and controlling access through tools like sudo. This article demystifies user management on Red Hat Linux, providing you with actionable insights and examples that you can apply in real-life scenarios. This isn't confined to just Redhat Linux; it applies to other distributions as well, such as Fedora, CentOS, Kali, Ubuntu, and more.
The Basics of User Management in Red Hat Linux
Understanding System Files
User-related data is stored in several key files:
/etc/passwd: Contains user account information such as username, UID, home directory, and default shell.
/etc/shadow: Stores encrypted password information and password aging details.
/etc/group: Lists group accounts, associated users, and group IDs (GID).
Understanding the role of these files is essential, as they serve as the foundation for all user management operations on your system.
Essential Commands for Managing Users
The Linux command line offers a set of commands designed for user management:
Creating a User:
To create a new user, use the useradd command.
Example:
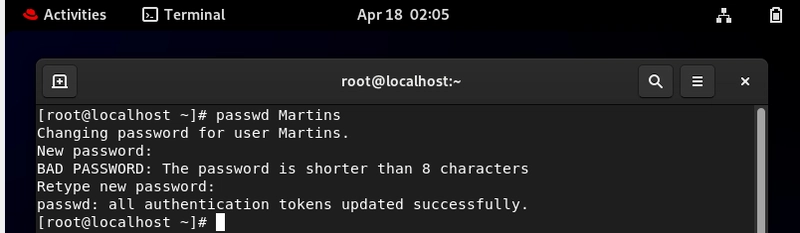
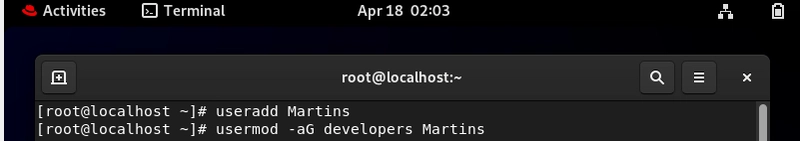
useradd Martins

This will create the user "Martins" and secure password.
Modifying a User:
To modify a user’s settings, the usermod command comes in handy.
Example:
sudo usermod -aG developers Martins
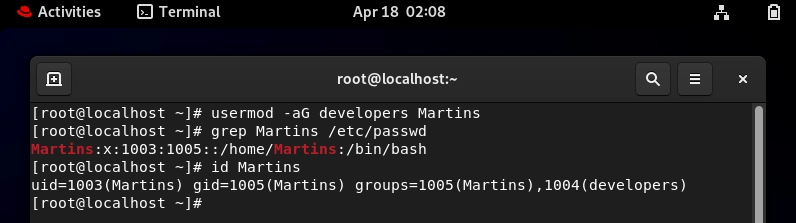
This adds the user "Martins" to the "developers" group.
Important note:
- When you use the -G option without the -a option in the usermod command to add a user to a group, it has a significant effect: it replaces the user's supplementary groups with the specified ones rather than just adding the user to the new group(s) while keeping their existing groups.
- Use "id Martins" to view the primary and secondary group user belong
Deleting a User:
To remove a user, use the userdel command.
Example:
userdel -r Martins
The -r flag will also delete the user’s home directory and mail spool.
Each of these commands is straightforward but offers detailed control over user settings and permissions.
Group Management
Groups are essential for organizing users and managing permissions collectively. Red Hat Linux allows administrators to create, modify, and delete groups.
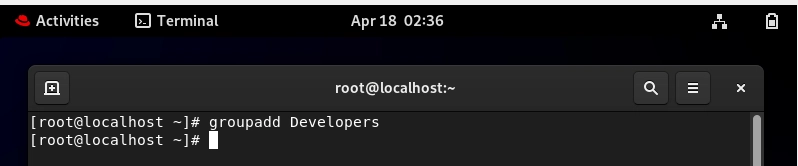
Creating a Group:
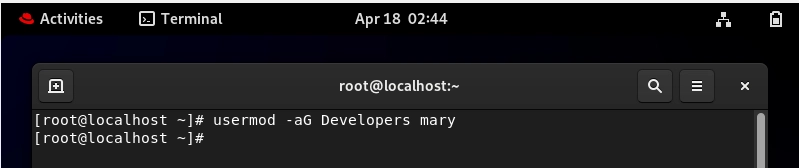
Adding a User to a Group:
usermod -aG Developers Mary
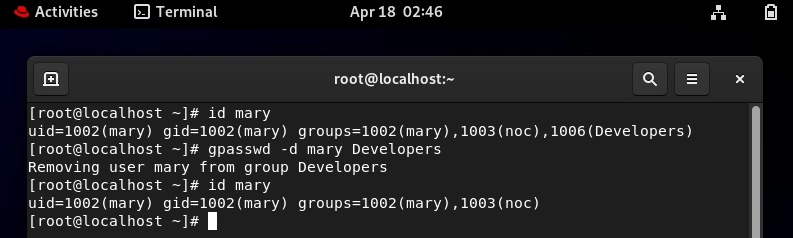
Removing a User from a Group:
You can modify /etc/group manually or use tools like gpasswd.
Example:
gpasswd -d Mary Developers
Managing groups efficiently can simplify the process of setting permissions across directories and applications, particularly when dealing with projects that require team collaboration.
Privilege Management and Sudo Setup
Granting administrative privileges only when necessary is a critical security best practice. The sudo command allows designated users to execute commands with root-level privileges, without sharing the root password.
Configuring Sudo Access:
Modify the /etc/sudoers file using the visudo command to ensure syntax integrity.
Example:
sudo visudo
Add an entry like:
Martins ALL=(ALL) ALL
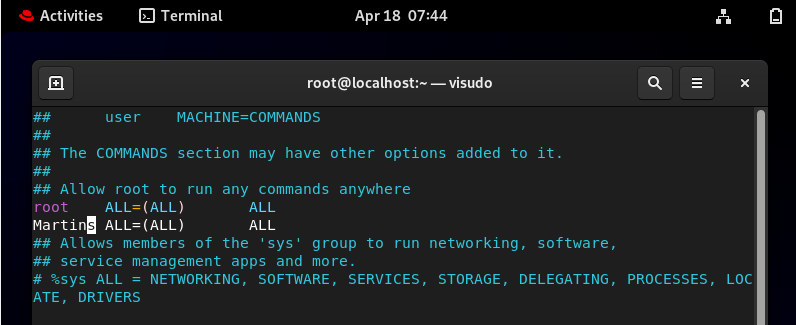
This line grants the user Martins permission to execute any command from any terminal.
Properly setting up sudo not only fine-tunes security but also helps in audit logging and accountability.
Real-World Scenarios and Use Cases
Scenario 1: Managing a Development Team
Imagine a mid-sized software company where multiple developers require access to specific directories and tools. The system administrator can:
- Create individual user accounts for each developer.
- Create a common developers group.
- Add users to the group to grant access to shared repositories and folders.
- Use sudo carefully to allow required system updates without compromising security.
Scenario 2: University Lab Environment
In a university computer lab, different students may share the same machines. The admin can:
- Set up temporary user accounts for lab sessions.
- Implement group restrictions so that each course has its own set of permissions.
- Periodically clean up accounts and reset passwords using scripted automation.
- These scenarios underline how thoughtful user management can enhance both security and operational efficiency.
Best Practices and Tips
- Use Strong Password Policies: Leverage the /etc/login.defs and **/etc/pam.d/ **configuration files to enforce password strength and aging policies.
- Automate Routine Tasks: Script the creation, modification, and deletion of user accounts to reduce human error.
- Regularly Audit and Update: Periodically review /etc/passwd, /etc/group, and /etc/shadow to ensure that only authorized users have access.
- Backup System Files: Before applying major changes, back up key files like /etc/passwd and /etc/group.
- Educate Users: Inform users about the importance of secure password practices and the proper use of sudo.
Conclusion
Managing users in Red Hat Linux is an important skill for any system admin. With the right commands, proper group setup, and smart use of sudo for controlling permissions, you can keep everything secure and running smoothly. As systems get bigger and more complex, getting a handle on these tools helps things run more efficiently and securely.
By looking at the real-life examples above, you can apply these techniques to your own setup—whether it’s in a corporate office, a university lab, or a cloud server environment.
References
- Red Hat Enterprise Linux System Administrator's Guide
- The Linux Command Line by William Shotts
- Linux Administration: User Management
Connect with me on LinkedIn
To learn more about Linux, cloud and on-prem Infrastructure, DevOps and automation.
#Cloudwhister #Security #DevOps #Automation #Linux #Opensource











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)



























































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)

















































































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





























































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)