Tutorials: Using AWS SSM Session Manager Port Forwarding to Connect to Private VPC Resources
Tutorials: Using AWS SSM Session Manager Port Forwarding to Connect to Private VPC Resources A common issue people run into when using AWS is how to connect to private resources such as RDS databases and EC2 instances from their local machine without exposing their resources to the public internet. In this tutorial, I will show you how to use AWS SSM Port Forwarding to connect to a private RDS database without the need for a public database, a public facing bastion instance, or a VPN. What is AWS SSM Session Manager? AWS Systems Manager Session Manager is a fully managed tool that's part of the AWS Systems Manager (aka SSM) service which is used to manage EC2 instances, on-premises servers, and any other virtual machines (VMs). The Session Manager feature allows you to connect to your instances using an interactive browser-based shell accessible from the EC2 console, or from the AWS CLI The main benefits of using Session Manager are: You don't need to open any inbound ports or manage bastion hosts or SSH keys, which leads to a reduced attack surface Your instances and databases don't need to have public IP addresses attached (which also saves money) All sessions are end to end encrypted by default, and can be encrypted using a custom CMK if needed for compliance Access to your instances is centrally managed using IAM permissions, so you can control which users or groups can use Session Manager and which access which managed instances they can access All Session Manager calls are logged to CloudTrail, and session specific connection logs can be stored in S3 for additional auditing and compliance And most recently, port forwarding and tunneling to remote hosts is now supported, which is what we'll be covering in this tutorial What is AWS SSM Session Manager Port Forwarding to Remote Hosts? Why should I care? On May 27, 2022, AWS announced support for port forwarding to remote hosts using Session Manager. This feature was a game changer, it enables you to create a secure tunnel between your local machine and a remote host (e.g. an RDS database or EC2 instance) without needing to make your instance or database publicly accessible, or set up a VPN into your AWS VPC network. Session Manager is only one feature of AWS Systems Manager. AWS SSM includes a suite of tools that help you manage your AWS resources and benefit your operations, including automated instance patching via Patch Manager, automation workflows via Automation Documents and Run Commands, a centralized view of all your managed instances and other nodes, securely store parameters and secrets via SSM Parameter Store, and of course, connecting to your managed nodes via Session Manager without opening any inbound ports. Scenario: Connecting to a Private RDS Database From Your Local Machine In this tutorial, you are an AWS administrator or engineer who needs to connect to a private RDS database from your local machine to run some queries. You don't want to make your RDS database publicly accessible since that's against security best practices. You also aren't able to set up a VPN connection to your AWS VPC network or launch a public facing bastion instance due to your company's security policies. So what can you do? Enter AWS SSM Session Manager Prerequisites Before you begin, you should have the following: An AWS account that you have administrator permissions in to create the resources required for this tutorial AWS CLI that is set up and configured on the local system with the correct set of permissions. Refer to the Installing or updating to the latest version of the AWS CLI guide The AWS Session Manager plugin for the AWS CLI installed A database client installed locally, such as MySQLWorkbench, DBBeaver, or PGAdmin. Step 1: Create the AWS Infrastructure Note: if you've already configured an AWS VPC, SSM managed EC2 instance, and RDS database, you can skip this step. You will need to create an AWS VPC with 2 public and 2 private subnets, configured with a NAT gateway and appropriate route tables, a Amazon Linux 2023 EC2 instance that is managed by SSM in a private subnet, and an RDS database in the same private subnets as the instance. I've created a Cloudformation template that has everything you need to create the infrastructure for this tutorial. You can download the template from here: ssm-port-forwarding-tutorial.yaml Once you've saved the .yml template file, follow the instructions in this document to create the Cloudformation Stack in the AWS account you will be using for this tutorial. Create Cloudformation Stack via the AWS Console The Cloudformation template will create the following resources in your AWS account: VPC and Networking Resources VPC with CIDR block 10.200.0.0/24 2 Public Subnets (10.200.0.0/26 and 10.200.0.64/26) 2 Private Subnets (10.200.0.128/26 and 10.200.0.192/26) Internet Gateway for public subnet internet access NAT

Tutorials: Using AWS SSM Session Manager Port Forwarding to Connect to Private VPC Resources
A common issue people run into when using AWS is how to connect to private resources such as RDS databases and EC2 instances from their local machine without exposing their resources to the public internet. In this tutorial, I will show you how to use AWS SSM Port Forwarding to connect to a private RDS database without the need for a public database, a public facing bastion instance, or a VPN.
What is AWS SSM Session Manager?
AWS Systems Manager Session Manager is a fully managed tool that's part of the AWS Systems Manager (aka SSM) service which is used to manage EC2 instances, on-premises servers, and any other virtual machines (VMs). The Session Manager feature allows you to connect to your instances using an interactive browser-based shell accessible from the EC2 console, or from the AWS CLI
The main benefits of using Session Manager are:
- You don't need to open any inbound ports or manage bastion hosts or SSH keys, which leads to a reduced attack surface
- Your instances and databases don't need to have public IP addresses attached (which also saves money)
- All sessions are end to end encrypted by default, and can be encrypted using a custom CMK if needed for compliance
- Access to your instances is centrally managed using IAM permissions, so you can control which users or groups can use Session Manager and which access which managed instances they can access
- All Session Manager calls are logged to CloudTrail, and session specific connection logs can be stored in S3 for additional auditing and compliance
- And most recently, port forwarding and tunneling to remote hosts is now supported, which is what we'll be covering in this tutorial
What is AWS SSM Session Manager Port Forwarding to Remote Hosts? Why should I care?
On May 27, 2022, AWS announced support for port forwarding to remote hosts using Session Manager. This feature was a game changer, it enables you to create a secure tunnel between your local machine and a remote host (e.g. an RDS database or EC2 instance) without needing to make your instance or database publicly accessible, or set up a VPN into your AWS VPC network.
Session Manager is only one feature of AWS Systems Manager. AWS SSM includes a suite of tools that help you manage your AWS resources and benefit your operations, including automated instance patching via Patch Manager, automation workflows via Automation Documents and Run Commands, a centralized view of all your managed instances and other nodes, securely store parameters and secrets via SSM Parameter Store, and of course, connecting to your managed nodes via Session Manager without opening any inbound ports.
Scenario: Connecting to a Private RDS Database From Your Local Machine
In this tutorial, you are an AWS administrator or engineer who needs to connect to a private RDS database from your local machine to run some queries. You don't want to make your RDS database publicly accessible since that's against security best practices. You also aren't able to set up a VPN connection to your AWS VPC network or launch a public facing bastion instance due to your company's security policies. So what can you do? Enter AWS SSM Session Manager
Prerequisites
Before you begin, you should have the following:
- An AWS account that you have administrator permissions in to create the resources required for this tutorial
- AWS CLI that is set up and configured on the local system with the correct set of permissions. Refer to the Installing or updating to the latest version of the AWS CLI guide
- The AWS Session Manager plugin for the AWS CLI installed
- A database client installed locally, such as MySQLWorkbench, DBBeaver, or PGAdmin.
Step 1: Create the AWS Infrastructure
Note: if you've already configured an AWS VPC, SSM managed EC2 instance, and RDS database, you can skip this step.
You will need to create an AWS VPC with 2 public and 2 private subnets, configured with a NAT gateway and appropriate route tables, a Amazon Linux 2023 EC2 instance that is managed by SSM in a private subnet, and an RDS database in the same private subnets as the instance.
I've created a Cloudformation template that has everything you need to create the infrastructure for this tutorial. You can download the template from here: ssm-port-forwarding-tutorial.yaml
Once you've saved the .yml template file, follow the instructions in this document to create the Cloudformation Stack in the AWS account you will be using for this tutorial. Create Cloudformation Stack via the AWS Console
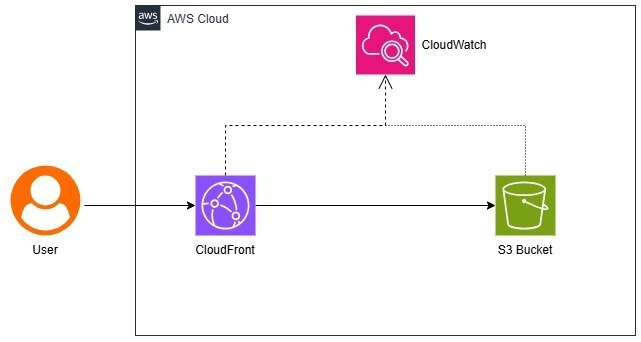
The Cloudformation template will create the following resources in your AWS account:
-
VPC and Networking Resources
- VPC with CIDR block 10.200.0.0/24
- 2 Public Subnets (10.200.0.0/26 and 10.200.0.64/26)
- 2 Private Subnets (10.200.0.128/26 and 10.200.0.192/26)
- Internet Gateway for public subnet internet access
- NAT Gateway for private subnet internet access
- Route Tables for both public and private subnets
-
EC2 Instance Bastion with SSM Agent preinstalled
- t4g.nano EC2 instance running Amazon Linux 2023 (ARM64) in private subnet
- SSM Agent pre-installed and configured via instance profile
- IAM Role and Instance Profile for SSM access
- Security Group for the bastion host with no inbound rules and all outbound network access allowed to 0.0.0.0/0
-
Database
- An Aurora Postgres RDS database cluster in the same private subnets
- Database Subnet Group for the Aurora cluster
- Secrets Manager secret containing database username and password
- Security Group for the RDS database allowing inbound access from bastion host on port 5432 (the PostgreSQL default port)

Figure 1: AWS SSM Port Forwarding Tutorial Architecture












































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)

























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)





































































































.png?#)





.jpg?#)






























_Christophe_Coat_Alamy.jpg?#)





































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)