TryHackMe: Snort Challenge - The Basics
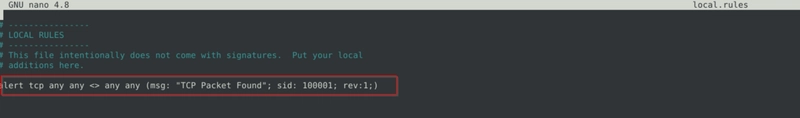
1. Writing IDS Rules (HTTP) Flag 1 Navigate to the task folder and use the given pcap file. Write a rule to detect all TCP packets from or to port 80. What is the number of detected packets you got? Note: You must answer this question correctly before answering the rest of the questions. Navigate to task folder and edit the local.rules file. Run sudo snort -c local.rules -A full -l . -r mx-3.pcap to examine the pcap file based on our recent rule addition. By this point a file named alert should be created in the same directory. As we run cat to read it, we see endless lines of similar messages. Each message indicate 1 entry of packets that fit our rule. Counting 1 by 1 will take ages, so we can run grep -o "TCP Packet Found" alert | wc -l to count the number of entries. Flag 2 Investigate the log file. What is the destination address of packet 63? We run sudo snort -r snort.log.1741528257 -n 63 to ensure that we get only the first 63 packets' information only. We can just scroll up to examine the last packet's destination IP. Flag 3 Investigate the log file. What is the ACK number of packet 64? Running a similar command as before, this time with -n as 64. sudo snort -r snort.log.1741528257 -n 64 And we examine the ACK number instead. Flag 4 Investigate the log file. What is the SEQ number of packet 62? Same thing, and now with -n as 62 and we examine its SEQ number. Flag 5 Investigate the log file. What is the TTL of packet 65? Same thing, now with -n as 65 and we examine its TTL. Flag 6 Investigate the log file. What is the source IP of packet 65? Picking up exactly where we were on flag 6, examine the source IP instead. Flag 7 Investigate the log file. What is the source port of packet 65? Picking up exactly where we were on flag 7, examine the source port instead. 2. Writing IDS Rules (FTP) Flag 1 Write a single rule to detect "all TCP port 21" traffic in the given pcap. What is the number of detected packets? We edit local.rules file and add a new rule as follows. We then run the newly added rule against our pcap file. We then examine the number of alerts, which is our flag. Flag 2 Investigate the log file. What is the FTP service name? strings snort.log.1741529561 | grep 2 We run strings to extract printable text from the file, and we grep 2 as a successful FTP connection has the code 2xx. Flag 3 Clear the previous log and alarm files. Deactivate/comment on the old rules. Write a rule to detect failed FTP login attempts in the given pcap. What is the number of detected packets? Here is a list of FTP failed status codes and their description. FTP Status Code Meaning 530 Authentication failed (incorrect username/password). 331 Username OK, but password is required. 332 Need account login (for certain restricted servers). 421 Service not available (server may be shutting down or limiting connections). 430 Invalid username or password (non-standard, used by some servers). We can create a rule that looks for 530 and filter them appropriately. alert tcp any any any 21 (msg: "Failed FTP Login Activity Detected"; content: "530"; sid: 100001; rev:1;) As we run the newly added rule against our pcap file, we get our flag. Flag 4 Clear the previous log and alarm files. Deactivate/comment on the old rule. Write a rule to detect successful FTP logins in the given pcap. What is the number of detected packets? As mentioned before, a successful attempt is having status code of 2xx, with further research we know that a successful login attempt is 230. New rule: alert tcp any any any 21 (msg: "Failed FTP Login Activity Detected"; content: "230"; sid: 100001; rev:1;) And there is the flag. Flag 5 Clear the previous log and alarm files. Deactivate/comment on the old rule. Write a rule to detect FTP login attempts with a valid username but no password entered yet. What is the number of detected packets? Based on our table at flag 3, we know that teh status code that fits that description is 331. So we add a new rule that fits that. alert tcp any any any 21 (msg: "Failed FTP Login Activity Detected"; content: "331"; sid: 100001; rev:1;) And there is the flag. Flag 6 Clear the previous log and alarm files. Deactivate/comment on the old rule. Write a rule to detect FTP login attempts with the "Administrator" username but no password entered yet. What is the number of detected packets? We write a rule that filters out the string Administrator, as follows. alert tcp any any any 21 (msg: "Failed FTP Login Activity Detected"; content: "331"; content: "Administrator"; sid: 100001; rev:1;) 3. Writing IDS Rules (PNG) Flag 1 Navigate to the task folder. Use the given pcap file. Write
1. Writing IDS Rules (HTTP)
Flag 1
Navigate to the task folder and use the given pcap file.
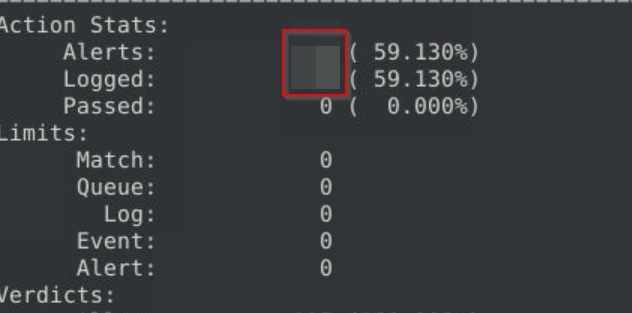
Write a rule to detect all TCP packets from or to port 80.
What is the number of detected packets you got?
Note: You must answer this question correctly before answering the rest of the questions.
Navigate to task folder and edit the local.rules file.
Run sudo snort -c local.rules -A full -l . -r mx-3.pcap to examine the pcap file based on our recent rule addition.
By this point a file named alert should be created in the same directory.
As we run cat to read it, we see endless lines of similar messages. Each message indicate 1 entry of packets that fit our rule.
Counting 1 by 1 will take ages, so we can run grep -o "TCP Packet Found" alert | wc -l to count the number of entries.
Flag 2
Investigate the log file.
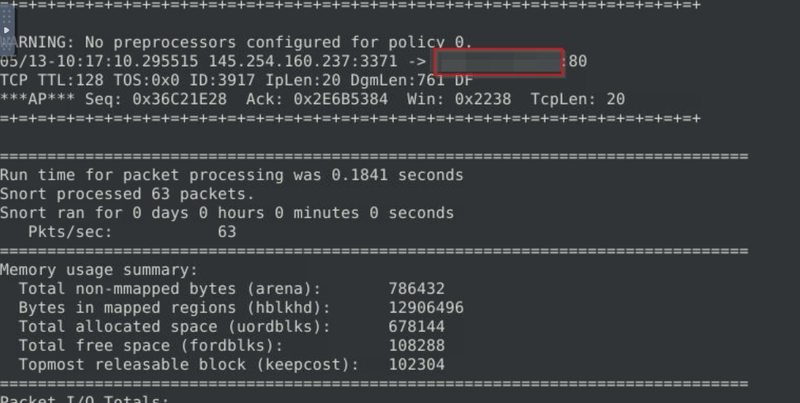
What is the destination address of packet 63?
We run sudo snort -r snort.log.1741528257 -n 63 to ensure that we get only the first 63 packets' information only.
We can just scroll up to examine the last packet's destination IP.
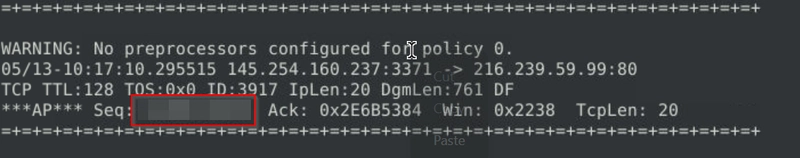
Flag 3
Investigate the log file.
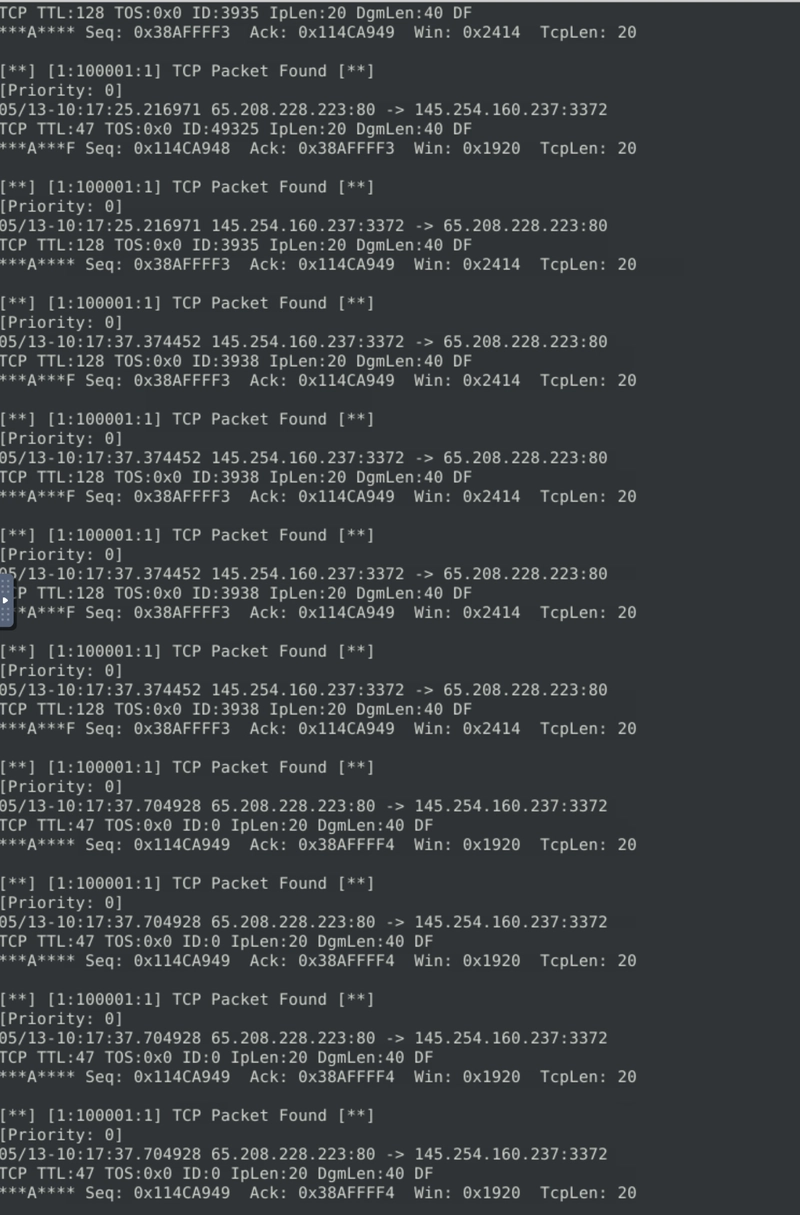
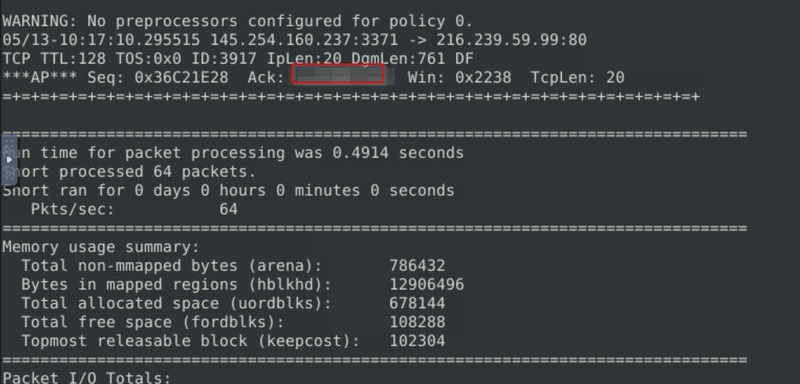
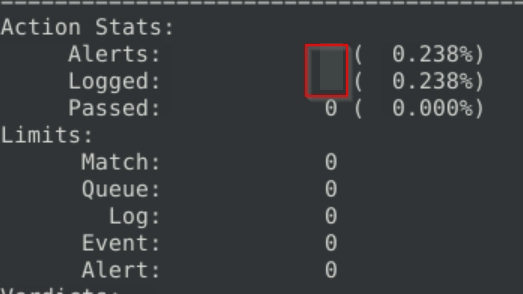
What is the ACK number of packet 64?
Running a similar command as before, this time with -n as 64.
sudo snort -r snort.log.1741528257 -n 64
![]()
And we examine the ACK number instead.
Flag 4
Investigate the log file.
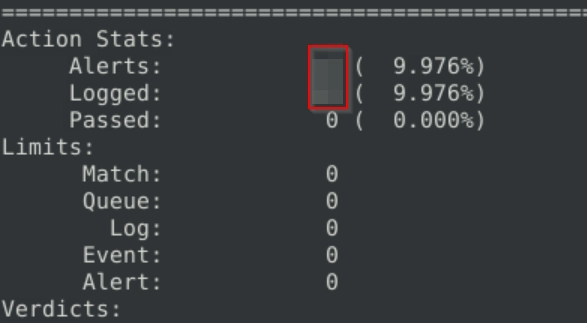
What is the SEQ number of packet 62?
Same thing, and now with -n as 62 and we examine its SEQ number.
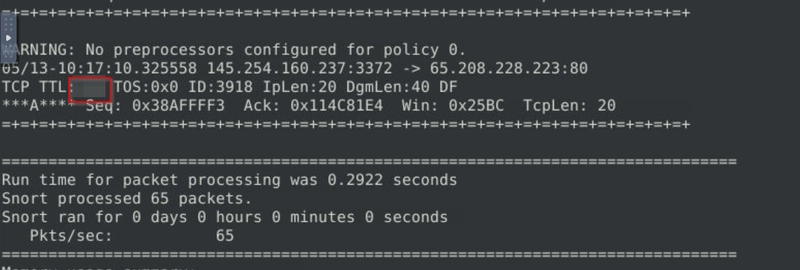
Flag 5
Investigate the log file.
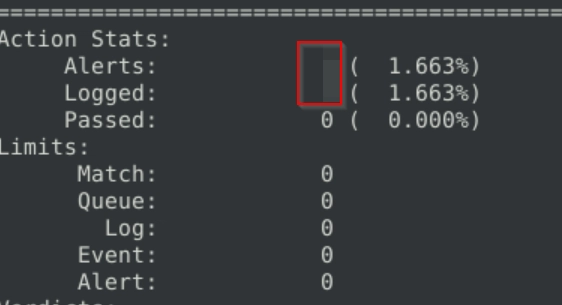
What is the TTL of packet 65?
Same thing, now with -n as 65 and we examine its TTL.
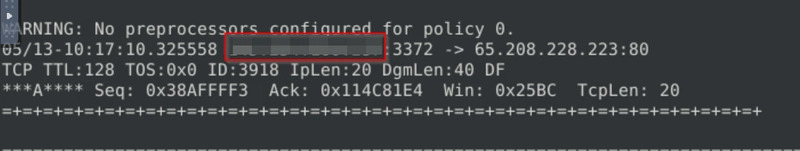
Flag 6
Investigate the log file.
What is the source IP of packet 65?
Picking up exactly where we were on flag 6, examine the source IP instead.
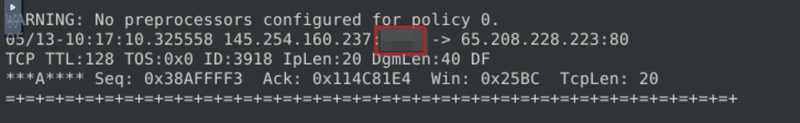
Flag 7
Investigate the log file.
What is the source port of packet 65?
Picking up exactly where we were on flag 7, examine the source port instead.
2. Writing IDS Rules (FTP)
Flag 1
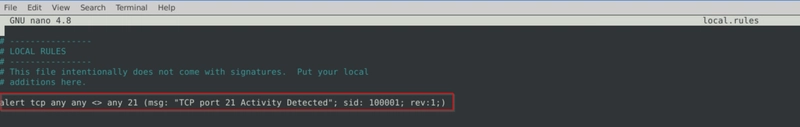
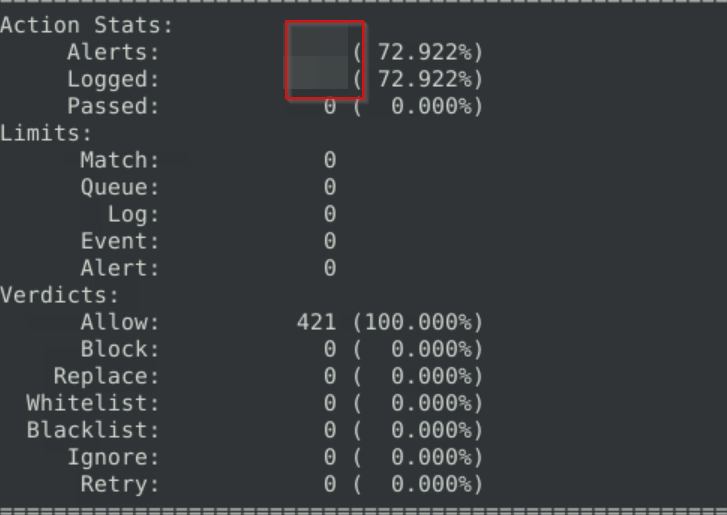
Write a single rule to detect "all TCP port 21" traffic in the given pcap.
What is the number of detected packets?
We edit local.rules file and add a new rule as follows.
We then run the newly added rule against our pcap file.
We then examine the number of alerts, which is our flag.
Flag 2
Investigate the log file.
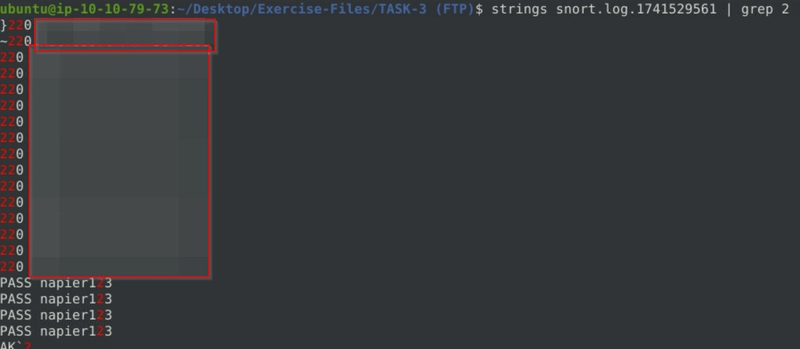
What is the FTP service name?
strings snort.log.1741529561 | grep 2
We run strings to extract printable text from the file, and we grep 2 as a successful FTP connection has the code 2xx.
Flag 3
Clear the previous log and alarm files.
Deactivate/comment on the old rules.
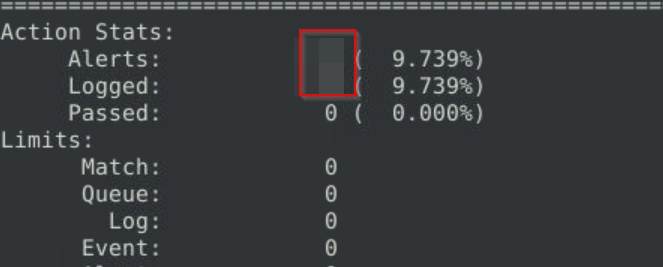
Write a rule to detect failed FTP login attempts in the given pcap.
What is the number of detected packets?
Here is a list of FTP failed status codes and their description.
| FTP Status Code | Meaning |
|---|---|
| 530 | Authentication failed (incorrect username/password). |
| 331 | Username OK, but password is required. |
| 332 | Need account login (for certain restricted servers). |
| 421 | Service not available (server may be shutting down or limiting connections). |
| 430 | Invalid username or password (non-standard, used by some servers). |
We can create a rule that looks for 530 and filter them appropriately.
alert tcp any any <> any 21 (msg: "Failed FTP Login Activity Detected"; content: "530"; sid: 100001; rev:1;)
As we run the newly added rule against our pcap file, we get our flag.
Flag 4
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect successful FTP logins in the given pcap.
What is the number of detected packets?
As mentioned before, a successful attempt is having status code of 2xx, with further research we know that a successful login attempt is 230.
New rule:
alert tcp any any <> any 21 (msg: "Failed FTP Login Activity Detected"; content: "230"; sid: 100001; rev:1;)
And there is the flag.
Flag 5
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect FTP login attempts with a valid username but no password entered yet.
What is the number of detected packets?
Based on our table at flag 3, we know that teh status code that fits that description is 331.
So we add a new rule that fits that.
alert tcp any any <> any 21 (msg: "Failed FTP Login Activity Detected"; content: "331"; sid: 100001; rev:1;)
And there is the flag.
Flag 6
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect FTP login attempts with the "Administrator" username but no password entered yet.
What is the number of detected packets?
We write a rule that filters out the string Administrator, as follows.
alert tcp any any <> any 21 (msg: "Failed FTP Login Activity Detected"; content: "331"; content: "Administrator"; sid: 100001; rev:1;)
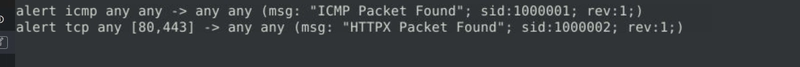
3. Writing IDS Rules (PNG)
Flag 1
Navigate to the task folder.
Use the given pcap file.
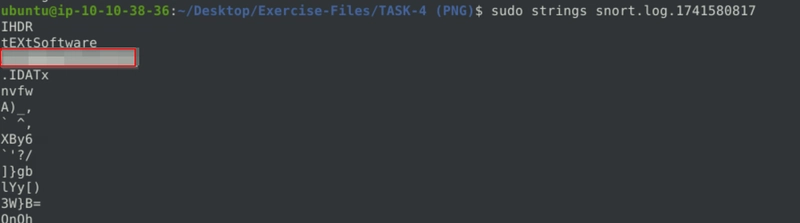
Write a rule to detect the PNG file in the given pcap.
Investigate the logs and identify the software name embedded in the packet.
After doing some research, we can get to know that PNG files start with the following 8-byte signature:
89 50 4E 47 0D 0A 1A 0A
With this in mind, we can create a snort rule that takes that as one of its parameters as follows.
alert tcp any any <> any any (msg: "PNG File Detected"; content: "|89 50 4E 47 0D 0A 1A 0A|"; sid: 100001; rev:1;)
Then we run the rule against the pcap file.
sudo snort -c local.rules -A full -l . -r
After that we run strings on the log file.
Flag 2
Clear the previous log and alarm files.
Deactivate/comment on the old rule.
Write a rule to detect the GIF file in the given pcap.
Investigate the logs and identify the image format embedded in the packet.
After doing some research, we got to know that GIF files has 2 common headers, 47 49 46 38 37 61 for older format and 47 49 46 38 39 61 for newer ones.
With this in mind, the snort rules can be created as follows.
alert tcp any any <> any any (msg: "GIF File Detected"; content: "|47 49 46 38 37 61|"; sid: 100001; rev:1;)
alert tcp any any <> any any (msg: "GIF File Detected"; content: "|47 49 46 38 39 61|"; sid: 100001; rev:1;)
Then we run the rule against the pcap file.
sudo snort -c local.rules -A full -l . -r
After that we run strings on the log file.
We see that all 4 packets logged have the same GIF format.
4. Writing IDS Rules (Torrent Metafile)
Flag 1
Navigate to the task folder.
Use the given pcap file.
Write a rule to detect the torrent metafile in the given pcap.
What is the number of detected packets?
After some research we know that .torrent files do not have a specific signature as PNG does. We instead investigate based on its file type instead.
We create snort rules based on those.
alert tcp any any <> any any (msg: "Torrent File Detected"; content: ".torrent"; sid: 100001; rev:1;)
Then we run the rule against the pcap file.
sudo snort -c local.rules -A full -l . -r
Scroll up a bit and we see the flag.
Flag 2
Investigate the log/alarm files.
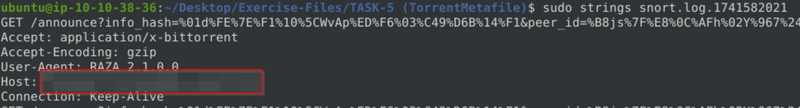
What is the name of the torrent application?
After that we run strings on the log file.
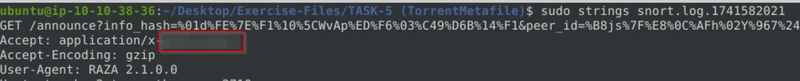
Flag 3
Investigate the log/alarm files.
What is the MIME (Multipurpose Internet Mail Extensions) type of the torrent metafile?
We can get the flag exactly where we got the last flag.
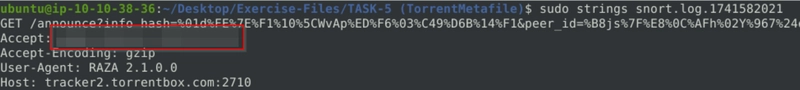
Flag 4
Investigate the log/alarm files.
What is the hostname of the torrent metafile?
We can get the flag exactly where we got the last flag.
5. Troubleshooting Rules Syntax Errors
Flag 1
In this section, you need to fix the syntax errors in the given rule files.
You can test each ruleset with the following command structure;
sudo snort -c local-X.rules -r mx-1.pcap -A console
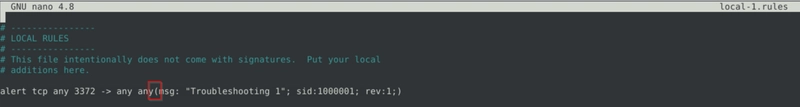
Fix the syntax error in local-1.rules file and make it work smoothly.
What is the number of the detected packets?
The problem with local-1.rules is the missing spacing between any and (.
After fixing that, we just run sudo snort -c local-1.rules -r mx-1.pcap -A console and there is the flag.
Flag 2
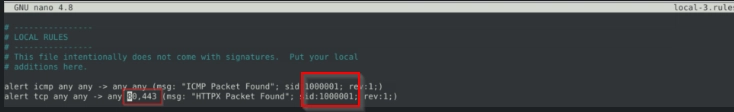
Fix the syntax error in local-3.rules file and make it work smoothly.
What is the number of the detected packets?
Missing source port.
We can correct it like so.
And we get the flagafter running sudo snort -c local-2.rules -r mx-1.pcap -A console
Flag 3
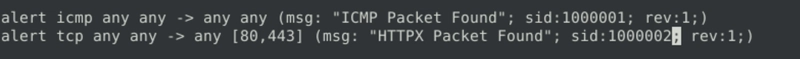
Fix the syntax error in local-3.rules file and make it work smoothly.
What is the number of the detected packets?
We need square brackets to include multiple destination ports and have different sid for different rules.
Like so.
And the flag is retrieved after running sudo snort -c local-3.rules -r mx-1.pcap -A console
Flag 4
Fix the syntax error in local-4.rules file and make it work smoothly.
What is the number of the detected packets?
So right off the bat we see 3 errors:
- missing square brackets at the source ports
- incorrect syntax as there is missing semicolon at the end of the
msgparameter of the second rule - not having unique
sid
Correct them like so.
And the flag is retreived after running sudo snort -c local-4.rules -r mx-1.pcap -A console.
Flag 5
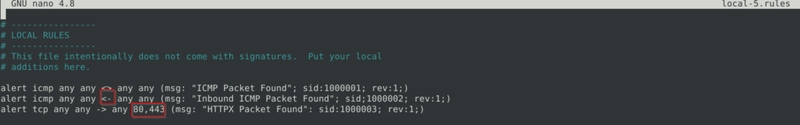
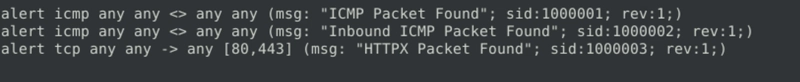
Fix the syntax error in local-5.rules file and make it work smoothly.
What is the number of the detected packets?
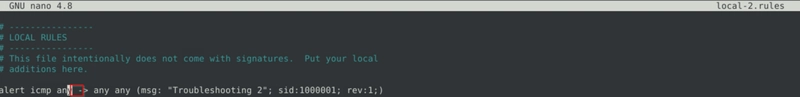
We see 2 errors here:
- there is no
<-operator in snort - missing square brackets
- incorrect syntax as there is missing semicolon at the end of the
msgparameter of the second rule
Corrected version.
And the flag is retreived after running sudo snort -c local-5.rules -r mx-1.pcap -A console.
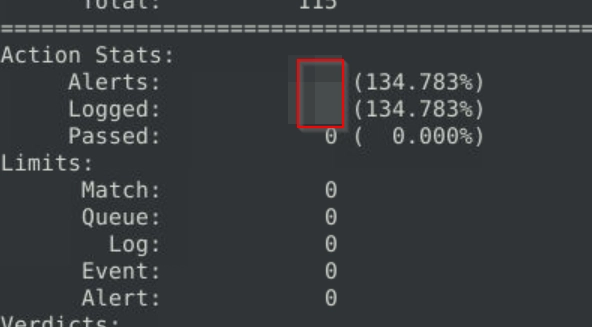
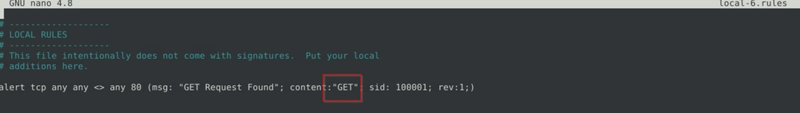
Flag 6
Fix the logical error in local-6.rules file and make it work smoothly to create alerts.
What is the number of the detected packets?
Corrected rule.
Alternatively, we can change the content parameter to 67 65 74 as the hex values of GET
And the flag is retreived after running sudo snort -c local-6.rules -r mx-1.pcap -A console.
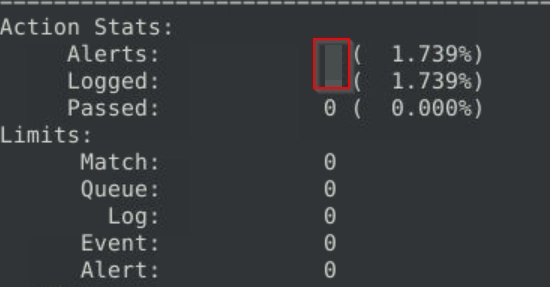
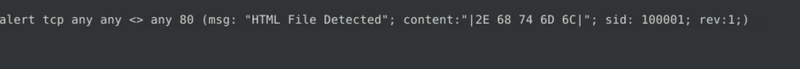
Flag 7
Fix the logical error in local-7.rules file and make it work smoothly to create alerts.
What is the number of the detected packets?
The missing parameter is msg, which is the flag.
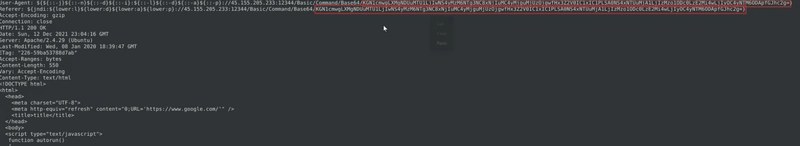
As we run the hex values in CyberChef, we see that the rule intend to detect HTML files.
The corrected rule should be:
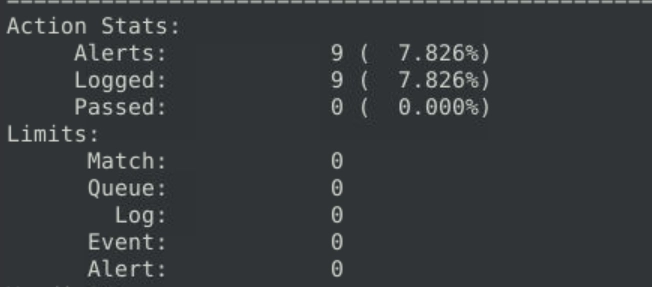
Which gives us a total of 9 alerts after running the rule against the pcap file.
6. Using External Rules (MS17-010)
Flag 1
Navigate to the task folder.
Use the given pcap file.
Use the given rule file (local.rules) to investigate the ms1710 exploitation.
What is the number of detected packets?
Upon reading both .rules files, we got to figure out that local.rules is the one with the rules to detect the MS17-010 exploit.
So we execute sudo snort -c local.rules -r ms-17-010.pcap -A console.
And we got the flag like so.
Flag 2
Clear the previous log and alarm files.
Use local-1.rules empty file to write a new rule to detect payloads containing the "\IPC$" keyword.
What is the number of detected packets?
Rule created.
alert tcp any any <> any any (msg: "Keyword IPC$ Detected"; content: "IPC$"; sid: 1000001; rev: 1;)
Flag is retrieved after adding the rule into local-1.rules and running sudo snort -c local-1.rules -r ms-17-010.pcap -A full -l ..
Flag 3
Investigate the log/alarm files.
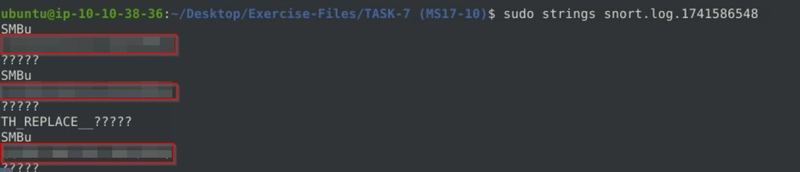
What is the requested path?
We get to retreive the flag after running strings on the log file created.
Flag 4
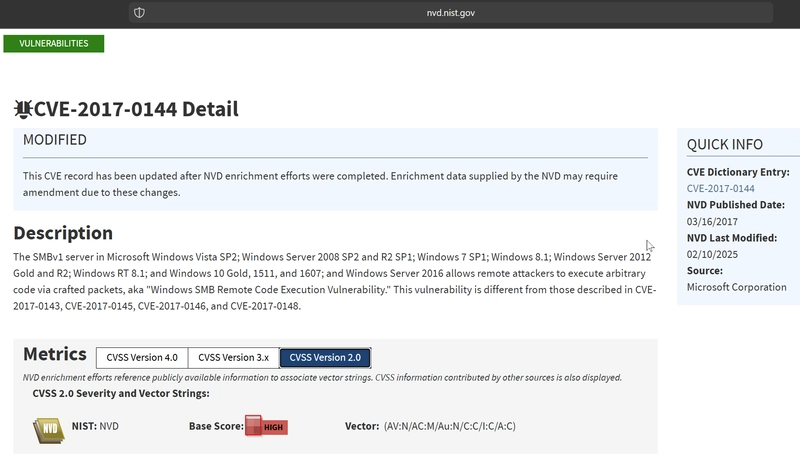
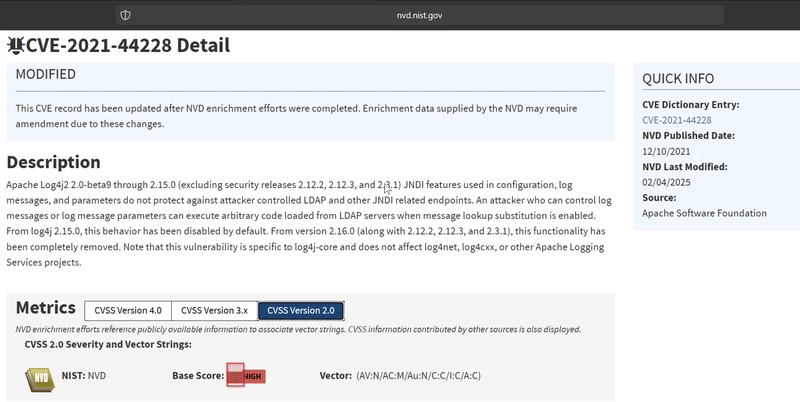
What is the CVSS v2 score of the MS17-010 vulnerability?
We get the score by visiting the NIST site and navigate to CVSS v2.
Using External Rules: Log4j
Flag 1
Navigate to the task folder.
Use the given pcap file.
Use the given rule file (local.rules) to investigate the log4j exploitation.
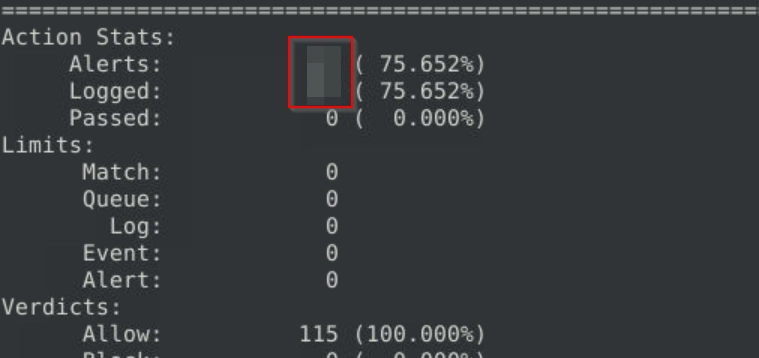
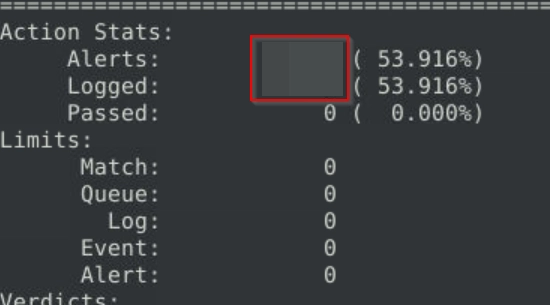
What is the number of detected packets?
Upon reading both .rules files, we get to determine that local.rules is the file with the rules to detect the malicious traffic.
We can run sudo snort -c local.rules -r log4j.pcap -A full -l .
Flag 2
Investigate the log/alarm files.
How many rules were triggered?.
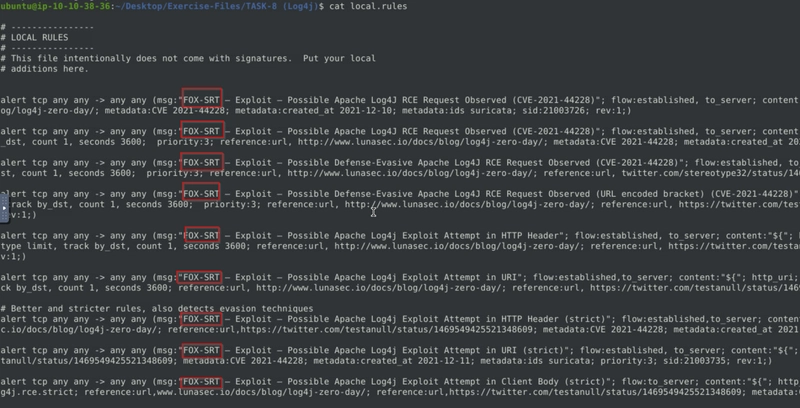
As we can see, all rules were configured so that msg will display FOX-SRT whenever an alert is generated.
With this in mind, we can execute the command below:
cat alert | grep FOX* | sort | uniq | wc -l
We read the alert file, filtering all the output by the common msg pattern of FOX-SRT. We also pipe the output through | sort | uniq to extract only unique outputs, and wc -l to count the total lines of output.
And the flag is retrieved.
Flag 3
Investigate the log/alarm files.
What are the first six digits of the triggered rule sids?
We can just read the local.rules file and notice any rule's sid.
The first 6 digits will be our flag.
Flag 4
Clear the previous log and alarm files.
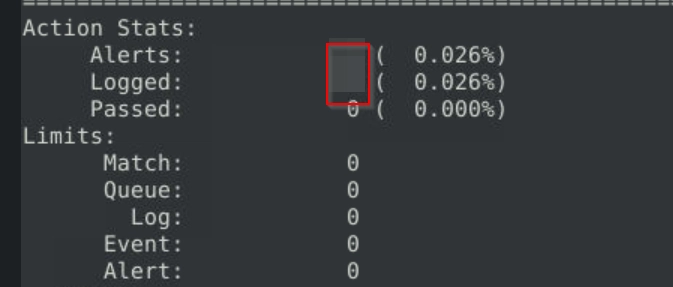
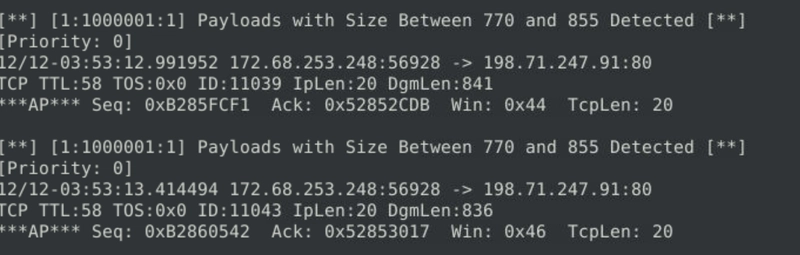
Use local-1.rules empty file to write a new rule to detect packet payloads between 770 and 855 bytes.
What is the number of detected packets?
New rule added to local-1.rules.
alert tcp any any <> any any (msg: "Payloads with Size Between 700 and 855 Detected"; dsize: 770<>855; sid: 1000001; rev: 1;)
We get the flag after executing sudo snort -c local-1.rules -r log4j.pcap -A full -l ..
Flag 5
Investigate the log/alarm files.
What is the name of the used encoding algorithm?
As we run sudo strings , we see something interesting.
We see that some strings were encoded in Base64, as recognised by the = sign at the end and the unusually long string of what seemed like gibberish. We can also confirm that its Base64 as it is mentioned in the previous /.
Coincidentally, the flag is base64.
Flag 6
Investigate the log/alarm files.
What is the IP ID of the corresponding packet?
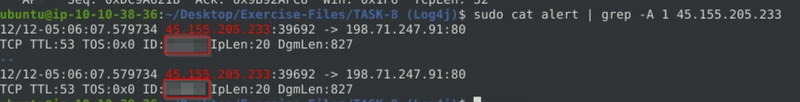
We can see the IP of the packet that sent the encoded string.
Upon running sudo cat alert, we can see the output follows a format of the IP, then ID at the next line.
So we can run sudo cat alert | grep -A 1 45.155.205.233. The -A 1 prints an additional line after the IP match.
And there is the flag.
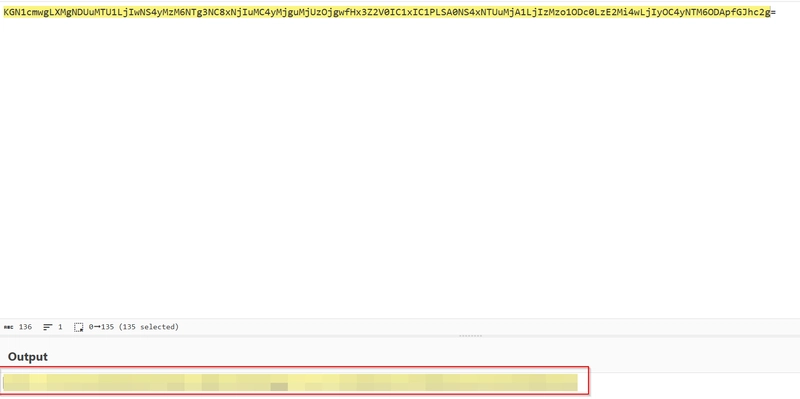
Flag 7
Investigate the log/alarm files.
Decode the encoded command.
What is the attacker's command?
We just run sudo strings and retrieve the encoded string as follows.
We then copy that and Bae64 decode it in CyberChef.
Flag 8
What is the CVSS v2 score of the Log4j vulnerability?
We then hop onto NIST site and search for log4j and get the score under CVSS v2.



































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)










































































































































_Muhammad_R._Fakhrurrozi_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
_NicoElNino_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





























































































![What Google Messages features are rolling out [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2023/12/google-messages-name-cover.png?resize=1200%2C628&quality=82&strip=all&ssl=1)












![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)