Silent Intruders
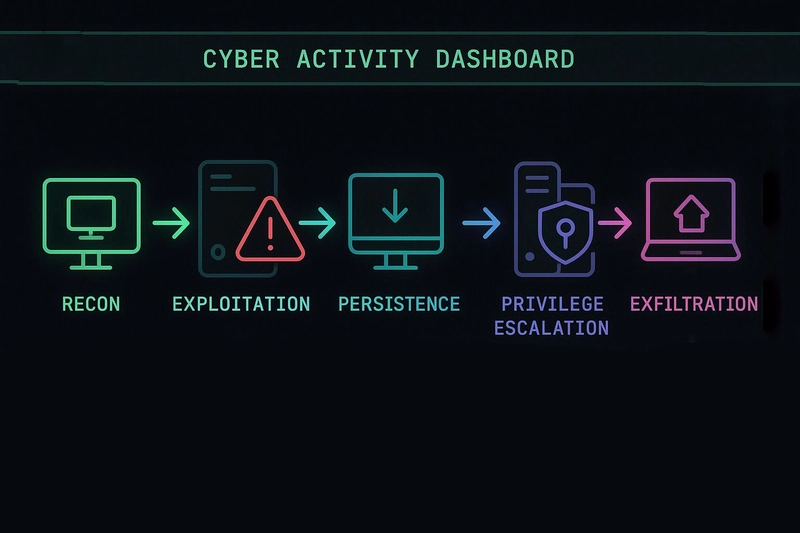
Introduction In 2021, a seemingly minor misconfiguration in Windows’ Print Spooler service unleashed a global cybersecurity crisis—aptly named PrintNightmare. This wasn't just a technical glitch; it was a textbook case of Remote Code Execution (RCE) a class of vulnerabilities that lets attackers run arbitrary code on your system without ever touching it. As our reliance on Windows-powered infrastructures continues, so does our exposure to such invisible threats. RCE vulnerabilities allow attackers to hijack systems, exfiltrate data, install malware, or escalate privileges—all remotely. Given their scope and severity, RCE flaws are the nightmare fuel of cybersecurity professionals and enterprise administrators alike. This article dives deep into how RCE works in the Windows ecosystem, explores infamous real-world cases, explains how attackers exploit these flaws, and—most importantly—how you can defend your systems. What is Remote Code Execution (RCE)? Remote Code Execution (RCE) refers to the ability of an attacker to remotely execute malicious code on a victim's machine. RCE is often achieved by exploiting a vulnerability in software that improperly processes user input or insecurely handles memory, files, or data structures. In Windows, this could mean executing a payload through a misconfigured network service, a buffer overflow in a driver, or even via a malicious email opened in Outlook. The Hacker’s Playbook: Exploitation Techniques These code snippets are simulated examples that demonstrate how RCE vulnerabilities arise due to poor coding practices or misconfiguration. 1. Buffer Overflow in C (NTFS Driver Analogy) char buffer[64]; strcpy(buffer, user_input); // No bounds checking How It Works: buffer[64] allocates 64 bytes of memory. strcpy(buffer, user_input) blindly copies data from user_input into buffer. If user_input is longer than 64 bytes, it overflows into adjacent memory. ⚠️ Why It’s Dangerous: Attackers can overwrite the return address on the stack with the address of their own shellcode. When the function returns, the program counter jumps to the malicious code. On Windows, this has been seen in drivers (like NTFS or TCP/IP stack) where attackers achieve SYSTEM-level code execution.
Introduction
In 2021, a seemingly minor misconfiguration in Windows’ Print Spooler service unleashed a global cybersecurity crisis—aptly named PrintNightmare. This wasn't just a technical glitch; it was a textbook case of Remote Code Execution (RCE) a class of vulnerabilities that lets attackers run arbitrary code on your system without ever touching it.
As our reliance on Windows-powered infrastructures continues, so does our exposure to such invisible threats. RCE vulnerabilities allow attackers to hijack systems, exfiltrate data, install malware, or escalate privileges—all remotely. Given their scope and severity, RCE flaws are the nightmare fuel of cybersecurity professionals and enterprise administrators alike.
This article dives deep into how RCE works in the Windows ecosystem, explores infamous real-world cases, explains how attackers exploit these flaws, and—most importantly—how you can defend your systems.
What is Remote Code Execution (RCE)?
Remote Code Execution (RCE) refers to the ability of an attacker to remotely execute malicious code on a victim's machine. RCE is often achieved by exploiting a vulnerability in software that improperly processes user input or insecurely handles memory, files, or data structures.
In Windows, this could mean executing a payload through a misconfigured network service, a buffer overflow in a driver, or even via a malicious email opened in Outlook.
The Hacker’s Playbook: Exploitation Techniques
These code snippets are simulated examples that demonstrate how RCE vulnerabilities arise due to poor coding practices or misconfiguration.
1. Buffer Overflow in C (NTFS Driver Analogy)
char buffer[64];
strcpy(buffer, user_input); // No bounds checking
How It Works:
buffer[64]allocates 64 bytes of memory.strcpy(buffer, user_input)blindly copies data fromuser_inputintobuffer.If
user_inputis longer than 64 bytes, it overflows into adjacent memory.
⚠️ Why It’s Dangerous:
Attackers can overwrite the return address on the stack with the address of their own shellcode.
When the function returns, the program counter jumps to the malicious code.
On Windows, this has been seen in drivers (like NTFS or TCP/IP stack) where attackers achieve SYSTEM-level code execution.




























![[Webinar] AI Is Already Inside Your SaaS Stack — Learn How to Prevent the Next Silent Breach](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiOWn65wd33dg2uO99NrtKbpYLfcepwOLidQDMls0HXKlA91k6HURluRA4WXgJRAZldEe1VReMQZyyYt1PgnoAn5JPpILsWlXIzmrBSs_TBoyPwO7hZrWouBg2-O3mdeoeSGY-l9_bsZB7vbpKjTSvG93zNytjxgTaMPqo9iq9Z5pGa05CJOs9uXpwHFT4/s1600/ai-cyber.jpg?#)













































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)




































































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)








































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




























































































![What’s new in Android’s April 2025 Google System Updates [U: 4/18]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/01/google-play-services-3.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)










![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)