Secrets Management in DevOps: Best Practices for Security
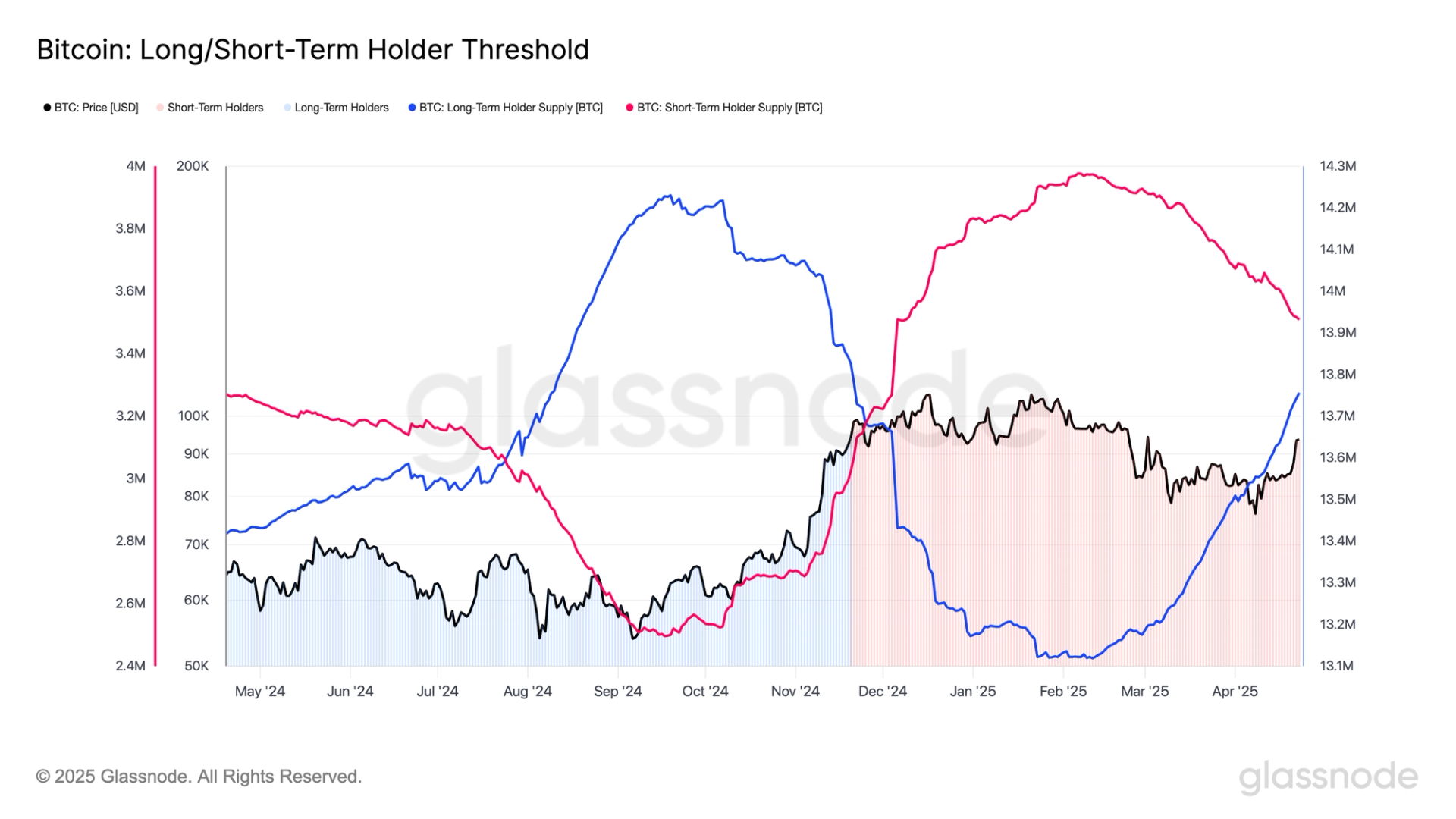
In a world of lightning-fast deployments, are you sure your secrets are safe? Secrets—like API keys, database passwords, SSH credentials—are the lifeblood of your infrastructure. But they're also a prime target for attackers. One leak can lead to massive breaches, downtime, or worse—customer trust loss. Let’s break down how you can secure your secrets like a pro and avoid becoming tomorrow’s headline. What Is Secrets Management in DevOps? Secrets management is the practice of securely handling sensitive data used in applications and infrastructure. These secrets include: API tokens SSH keys Database credentials OAuth tokens TLS certificates The goal is simple: keep these safe, automated, and audit-ready across environments. Why You Can’t Store Secrets in Code (Even If You Think It’s “Just a Dev Environment”) It might seem harmless to add a key in a .env file or even hard-code it for convenience. But here’s what can go wrong: Accidental commits to version control (yes, even private repos) Logs exposing environment variables Insider threats or misconfigured permissions CI/CD pipelines leaking secrets during builds Here’s a real-world example where Uber accidentally exposed credentials on GitHub—resulting in a $100,000 bug bounty payout. Lesson? If it’s not encrypted and audited, it’s not secure. Best Practices for Secrets Management Let’s get practical. Here are actionable tips to improve your secrets hygiene today: 1. Use a Secrets Management Tool Skip DIY solutions. Use battle-tested tools like: HashiCorp Vault AWS Secrets Manager Doppler Azure Key Vault These offer encryption, access controls, automatic rotation, and audit logs. 2. Never Store Secrets in Version Control Use .gitignore to avoid committing .env or config files: # Example .gitignore .env config/*.json *.pem And scan your repo regularly using tools like: GitGuardian Gitleaks 3. Leverage Environment Variables (But Securely) Inject secrets at runtime via environment variables, not hard-coded values: export DB_PASSWORD=$(aws secretsmanager get-secret-value --secret-id my-db | jq -r .SecretString) Use this in containerized deployments (like Docker/Kubernetes) too. 4. Automate Secret Rotation Manually rotating secrets = human error. Most modern tools offer automatic rotation—enable it. Rotate credentials regularly, especially after employee offboarding or vendor access. 5. Limit Access With the Principle of Least Privilege (PoLP) Don’t let everyone access everything. Use fine-grained access policies: Devs only see non-prod credentials CI/CD pipelines only get access to what's necessary No shared credentials (everyone gets their own) 6. Monitor and Audit Access Enable logs for secret access. Track who accessed what, when, and where. This is crucial for both compliance and incident response. Want to Learn More? Here are some

In a world of lightning-fast deployments, are you sure your secrets are safe?
Secrets—like API keys, database passwords, SSH credentials—are the lifeblood of your infrastructure.
But they're also a prime target for attackers.
One leak can lead to massive breaches, downtime, or worse—customer trust loss.
Let’s break down how you can secure your secrets like a pro and avoid becoming tomorrow’s headline.
What Is Secrets Management in DevOps?
Secrets management is the practice of securely handling sensitive data used in applications and infrastructure. These secrets include:
API tokens
SSH keys
Database credentials
OAuth tokens
TLS certificates
The goal is simple: keep these safe, automated, and audit-ready across environments.
Why You Can’t Store Secrets in Code (Even If You Think It’s “Just a Dev Environment”)
It might seem harmless to add a key in a .env file or even hard-code it for convenience. But here’s what can go wrong:
Accidental commits to version control (yes, even private repos)
Logs exposing environment variables
Insider threats or misconfigured permissions
CI/CD pipelines leaking secrets during builds
Here’s a real-world example where Uber accidentally exposed credentials on GitHub—resulting in a $100,000 bug bounty payout.
Lesson? If it’s not encrypted and audited, it’s not secure.
Best Practices for Secrets Management
Let’s get practical. Here are actionable tips to improve your secrets hygiene today:
1. Use a Secrets Management Tool
Skip DIY solutions. Use battle-tested tools like:
These offer encryption, access controls, automatic rotation, and audit logs.
2. Never Store Secrets in Version Control
Use .gitignore to avoid committing .env or config files:
# Example .gitignore
.env
config/*.json
*.pem
And scan your repo regularly using tools like:
3. Leverage Environment Variables (But Securely)
Inject secrets at runtime via environment variables, not hard-coded values:
export DB_PASSWORD=$(aws secretsmanager get-secret-value --secret-id my-db | jq -r .SecretString)
Use this in containerized deployments (like Docker/Kubernetes) too.
4. Automate Secret Rotation
Manually rotating secrets = human error.
Most modern tools offer automatic rotation—enable it. Rotate credentials regularly, especially after employee offboarding or vendor access.
5. Limit Access With the Principle of Least Privilege (PoLP)
Don’t let everyone access everything.
Use fine-grained access policies:
Devs only see non-prod credentials
CI/CD pipelines only get access to what's necessary
No shared credentials (everyone gets their own)
6. Monitor and Audit Access
Enable logs for secret access. Track who accessed what, when, and where.
This is crucial for both compliance and incident response.
Want to Learn More?
Here are some





































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)































































































































![[DEALS] Sterling Stock Picker: Lifetime Subscription (85% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)












































































































































_Olekcii_Mach_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)











































































































![M4 MacBook Air Drops to New All-Time Low of $912 [Deal]](https://www.iclarified.com/images/news/97108/97108/97108-640.jpg)
![New iPhone 17 Dummy Models Surface in Black and White [Images]](https://www.iclarified.com/images/news/97106/97106/97106-640.jpg)