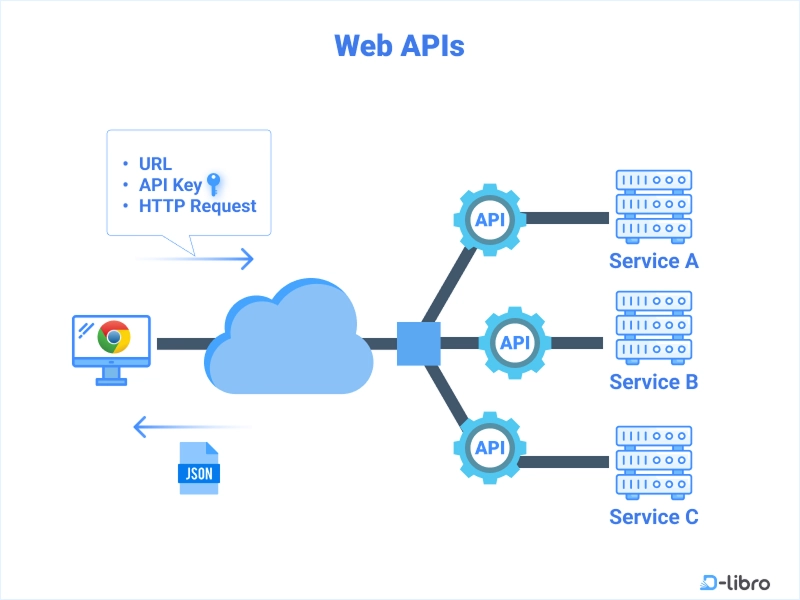
Mastering Amazon VPC: Gateways, Endpoints, and Monitoring Tools
Introduction to Amazon VPC Amazon Virtual Private Cloud (VPC) is a foundational AWS service that enables users to create an isolated section of the AWS Cloud where they can launch resources in a logically defined network. This article covers key VPC components, including NAT gateways, VPC endpoints, and monitoring tools, to help you optimize your cloud networking setup. 1. NAT Gateways: Connecting Private Subnets to the Internet NAT (Network Address Translation) gateways allow instances in private subnets to connect to the internet (or other AWS services) while remaining secure from inbound traffic. AWS offers two types of NAT solutions: A. Managed NAT Gateway Fully managed by AWS (no maintenance required). Highly available (automatically scales). Supports up to 10 Gbps bandwidth. Billed per hour and per GB of data processed. Use Case: Best for production workloads requiring high availability. B. NAT Instance (EC2-Based) Runs on an EC2 instance (user-managed). Not inherently highly available (requires manual failover). Limited by EC2 instance type (network bandwidth varies). Cheaper for low-traffic workloads (but requires maintenance). Use Case: Suitable for cost-sensitive, non-critical workloads where manual management is acceptable. 2. VPC Endpoints: Secure Private Connectivity to AWS Services VPC endpoints allow private communication between your VPC and AWS services without traversing the public internet, improving security and reducing latency. A. Interface VPC Endpoints (AWS PrivateLink) Powered by AWS PrivateLink, providing private connectivity. Works with many AWS services (e.g., EC2 API, SNS, SQS). Uses Elastic Network Interfaces (ENIs) in your subnet. Costs apply (per-hour and per-GB data processing). Throughput depends on ENI capacity. Use Case: Secure access to AWS services like EC2 API, KMS, or CloudWatch Logs. B. Gateway VPC Endpoints Directly connects to Amazon S3 & DynamoDB. No additional cost (free to use). No throughput limitations. No ENIs required (routes via VPC route tables). Use Case: High-throughput access to S3 or DynamoDB without NAT or internet gateways. C. Gateway Load Balancer Endpoints Used with Gateway Load Balancers for traffic inspection. Routes traffic to third-party security appliances (firewalls, intrusion detection systems). Supports inline security deployments. Use Case: Deep packet inspection for compliance or security monitoring. 3. VPC Flow Logs & Network Monitoring Tools Monitoring and troubleshooting network traffic is critical for security and performance. AWS provides several tools: A. VPC Flow Logs Captures IP traffic flow data (accepted/rejected traffic). Logs include: Source/destination IP & ports Packet counts & bytes transferred Timestamps & action (ACCEPT/REJECT) Three log destinations: CloudWatch Logs (for analysis & alarms). S3 (for long-term storage). Kinesis Data Firehose (for real-time processing). Use Case: Security audits, troubleshooting connectivity issues. B. Reachability Analyzer Tests connectivity between two VPC resources. Identifies if a path exists (and why if blocked). Helps debug security group & NACL issues. Use Case: Validating network paths before deployment. C. Network Access Analyzer Detects unintended network access. Identifies overly permissive security policies. Helps enforce least-privilege security. Use Case: Compliance audits & security hardening. D. Traffic Mirroring Copies network traffic from an ENI to monitoring tools. Used for intrusion detection, forensics, and troubleshooting. Supports third-party security appliances. Use Case: Security monitoring & threat detection. Conclusion: Best Practices for Amazon VPC Use NAT Gateways for Production Workloads (avoid NAT instances unless necessary). Prefer VPC Endpoints Over Public Internet Access (enhances security & reduces latency). Enable VPC Flow Logs for Security & Troubleshooting. Regularly Audit Network Access with Reachability Analyzer & Network Access Analyzer. Inspect Traffic with Gateway Load Balancer & Traffic Mirroring for compliance. By leveraging these VPC features, you can build secure, scalable, and observable cloud networks on AWS.

Introduction to Amazon VPC
Amazon Virtual Private Cloud (VPC) is a foundational AWS service that enables users to create an isolated section of the AWS Cloud where they can launch resources in a logically defined network. This article covers key VPC components, including NAT gateways, VPC endpoints, and monitoring tools, to help you optimize your cloud networking setup.
1. NAT Gateways: Connecting Private Subnets to the Internet
NAT (Network Address Translation) gateways allow instances in private subnets to connect to the internet (or other AWS services) while remaining secure from inbound traffic. AWS offers two types of NAT solutions:
A. Managed NAT Gateway
- Fully managed by AWS (no maintenance required).
- Highly available (automatically scales).
- Supports up to 10 Gbps bandwidth.
- Billed per hour and per GB of data processed.
Use Case: Best for production workloads requiring high availability.
B. NAT Instance (EC2-Based)
- Runs on an EC2 instance (user-managed).
- Not inherently highly available (requires manual failover).
- Limited by EC2 instance type (network bandwidth varies).
- Cheaper for low-traffic workloads (but requires maintenance).
Use Case: Suitable for cost-sensitive, non-critical workloads where manual management is acceptable.
2. VPC Endpoints: Secure Private Connectivity to AWS Services
VPC endpoints allow private communication between your VPC and AWS services without traversing the public internet, improving security and reducing latency.
A. Interface VPC Endpoints (AWS PrivateLink)
- Powered by AWS PrivateLink, providing private connectivity.
- Works with many AWS services (e.g., EC2 API, SNS, SQS).
- Uses Elastic Network Interfaces (ENIs) in your subnet.
- Costs apply (per-hour and per-GB data processing).
- Throughput depends on ENI capacity.
Use Case: Secure access to AWS services like EC2 API, KMS, or CloudWatch Logs.
B. Gateway VPC Endpoints
- Directly connects to Amazon S3 & DynamoDB.
- No additional cost (free to use).
- No throughput limitations.
- No ENIs required (routes via VPC route tables).
Use Case: High-throughput access to S3 or DynamoDB without NAT or internet gateways.
C. Gateway Load Balancer Endpoints
- Used with Gateway Load Balancers for traffic inspection.
- Routes traffic to third-party security appliances (firewalls, intrusion detection systems).
- Supports inline security deployments.
Use Case: Deep packet inspection for compliance or security monitoring.
3. VPC Flow Logs & Network Monitoring Tools
Monitoring and troubleshooting network traffic is critical for security and performance. AWS provides several tools:
A. VPC Flow Logs
- Captures IP traffic flow data (accepted/rejected traffic).
- Logs include:
- Source/destination IP & ports
- Packet counts & bytes transferred
- Timestamps & action (ACCEPT/REJECT)
-
Three log destinations:
- CloudWatch Logs (for analysis & alarms).
- S3 (for long-term storage).
- Kinesis Data Firehose (for real-time processing).
Use Case: Security audits, troubleshooting connectivity issues.
B. Reachability Analyzer
- Tests connectivity between two VPC resources.
- Identifies if a path exists (and why if blocked).
- Helps debug security group & NACL issues.
Use Case: Validating network paths before deployment.
C. Network Access Analyzer
- Detects unintended network access.
- Identifies overly permissive security policies.
- Helps enforce least-privilege security.
Use Case: Compliance audits & security hardening.
D. Traffic Mirroring
- Copies network traffic from an ENI to monitoring tools.
- Used for intrusion detection, forensics, and troubleshooting.
- Supports third-party security appliances.
Use Case: Security monitoring & threat detection.
Conclusion: Best Practices for Amazon VPC
- Use NAT Gateways for Production Workloads (avoid NAT instances unless necessary).
- Prefer VPC Endpoints Over Public Internet Access (enhances security & reduces latency).
- Enable VPC Flow Logs for Security & Troubleshooting.
- Regularly Audit Network Access with Reachability Analyzer & Network Access Analyzer.
- Inspect Traffic with Gateway Load Balancer & Traffic Mirroring for compliance.
By leveraging these VPC features, you can build secure, scalable, and observable cloud networks on AWS.













































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
























































































































































![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)


























































































-All-will-be-revealed-00-35-05.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-All-will-be-revealed-00-17-36.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)
-Jack-Black---Steve's-Lava-Chicken-(Official-Music-Video)-A-Minecraft-Movie-Soundtrack-WaterTower-00-00-32_lMoQ1fI.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)

















































































































![What iPhone 17 model are you most excited to see? [Poll]](https://9to5mac.com/wp-content/uploads/sites/6/2025/04/iphone-17-pro-sky-blue.jpg?quality=82&strip=all&w=290&h=145&crop=1)
















![Hands-On With 'iPhone 17 Air' Dummy Reveals 'Scary Thin' Design [Video]](https://www.iclarified.com/images/news/97100/97100/97100-640.jpg)
![Mike Rockwell is Overhauling Siri's Leadership Team [Report]](https://www.iclarified.com/images/news/97096/97096/97096-640.jpg)
![Instagram Releases 'Edits' Video Creation App [Download]](https://www.iclarified.com/images/news/97097/97097/97097-640.jpg)
![Inside Netflix's Rebuild of the Amsterdam Apple Store for 'iHostage' [Video]](https://www.iclarified.com/images/news/97095/97095/97095-640.jpg)