JWT - Based Auth: A Deep Dive
Understanding JWT-Based Security In modern web applications, JSON Web Tokens (JWTs) have become the cornerstone of authentication and authorization. They provide a stateless, secure way to handle user sessions and permissions across distributed systems. This means that the server does not need to store session information, which can improve scalability and performance. What is a JWT? A JWT is a compact, URL-safe means of representing claims between two parties. Think of it as a digital passport that contains three parts: Header - Algorithm & token type Payload - Claims and data Signature - Verification code Interactive JWT Explorer Try editing the header and payload below to see how JWTs work in real-time: JWT Internals: Breaking Down the Parts 1. Header The header typically consists of two parts: Token type (JWT) Signing algorithm (e.g., HMAC SHA256 or RSA) The header is a JSON object that is Base64Url encoded to form the first part of the JWT. { "alg": "HS256", "typ": "JWT" } 2. Payload The payload contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims. Registered claims: Predefined claims that are not mandatory but recommended, such as iss (issuer), exp (expiration time), sub (subject), and aud (audience). Public claims: Custom claims created to share information, which should be defined in the IANA JSON Web Token Registry or be collision-resistant. Private claims: Custom claims agreed upon by parties using the JWT. { "sub": "1234567890", // Subject (user ID) "name": "John Doe", // Custom claim "role": "admin", // Role for authorization "iat": 1516239022, // Issued at timestamp "exp": 1516242622 // Expiration timestamp } 3. Signature The signature is created by: Taking the encoded header Taking the encoded payload Adding a secret Applying the algorithm specified in the header The signature ensures that the token hasn't been altered. It is crucial for verifying the authenticity of the token. HMACSHA256( base64UrlEncode(header) + "." + base64UrlEncode(payload), secret ) JWT: Encoding vs. Encryption JWTs use encoding, not encryption. This means the data in a JWT is visible to anyone with access to the token, as it is encoded using Base64Url. However, the integrity of the data is protected by a signature, ensuring the token hasn't been tampered with. Encoding: Converts data into a different format using a public scheme (Base64Url for JWTs), making it URL-safe but not secure from viewing. Encryption: Converts data into an unreadable format without a secret key, which JWTs do not use for payloads. The main purpose of a JWT is to verify the identity of the issuer and ensure the token's integrity through a digital signature. Understanding this distinction helps developers decide what data to include in a JWT and how to handle it securely. JWT in Authentication Flow User Login The client sends a login request with credentials. The server verifies the credentials and, if valid, generates a JWT. The JWT is sent back to the client and stored, typically in a secure, HttpOnly cookie. Subsequent Requests The client includes the JWT in the Authorization header of subsequent requests. The server verifies the JWT and checks permissions before granting access to protected resources. JWT for Authorization JWTs excel at authorization because they can carry role and permission information. This allows for fine-grained access control based on the user's role and permissions. { "sub": "1234567890", "role": "admin", "permissions": ["read", "write", "delete"], "department": "engineering" } Security Best Practices Token Expiration Use short-lived access tokens to minimize the risk of token theft. Implement refresh token rotation to maintain user sessions securely. Always include the exp claim to define the token's expiration time. Payload Security Never store sensitive data in the payload, as it can be decoded by anyone with access to the token. Minimize payload size to reduce the risk of exposure and improve performance. Use standard claims when possible to ensure compatibility and security. Signature Protection Use strong secrets and consider using asymmetric algorithms like RS256 for added security. Rotate secrets periodically to mitigate the risk of key compromise. Common JWT Pitfalls Client-side Storage Store JWTs in HttpOnly cookies to protect against XSS attacks. Avoid storing JWTs in localStorage, as it is accessible via JavaScript. Implement CSRF protection to prevent unauthorized requests. Token Invalidation JWTs cannot be directly revoked, so use a token blacklist to manage invalid tokens. Keep expiration t
Understanding JWT-Based Security
In modern web applications, JSON Web Tokens (JWTs) have become the cornerstone of authentication and authorization. They provide a stateless, secure way to handle user sessions and permissions across distributed systems. This means that the server does not need to store session information, which can improve scalability and performance.
What is a JWT?
A JWT is a compact, URL-safe means of representing claims between two parties. Think of it as a digital passport that contains three parts:
- Header - Algorithm & token type
- Payload - Claims and data
- Signature - Verification code
Interactive JWT Explorer
Try editing the header and payload below to see how JWTs work in real-time:
JWT Internals: Breaking Down the Parts
1. Header
The header typically consists of two parts:
- Token type (JWT)
- Signing algorithm (e.g., HMAC SHA256 or RSA)
The header is a JSON object that is Base64Url encoded to form the first part of the JWT.
{
"alg": "HS256",
"typ": "JWT"
}
2. Payload
The payload contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims.
-
Registered claims: Predefined claims that are not mandatory but recommended, such as
iss(issuer),exp(expiration time),sub(subject), andaud(audience). - Public claims: Custom claims created to share information, which should be defined in the IANA JSON Web Token Registry or be collision-resistant.
- Private claims: Custom claims agreed upon by parties using the JWT.
{
"sub": "1234567890", // Subject (user ID)
"name": "John Doe", // Custom claim
"role": "admin", // Role for authorization
"iat": 1516239022, // Issued at timestamp
"exp": 1516242622 // Expiration timestamp
}
3. Signature
The signature is created by:
- Taking the encoded header
- Taking the encoded payload
- Adding a secret
- Applying the algorithm specified in the header
The signature ensures that the token hasn't been altered. It is crucial for verifying the authenticity of the token.
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret
)
JWT: Encoding vs. Encryption
JWTs use encoding, not encryption. This means the data in a JWT is visible to anyone with access to the token, as it is encoded using Base64Url. However, the integrity of the data is protected by a signature, ensuring the token hasn't been tampered with.
- Encoding: Converts data into a different format using a public scheme (Base64Url for JWTs), making it URL-safe but not secure from viewing.
- Encryption: Converts data into an unreadable format without a secret key, which JWTs do not use for payloads.
The main purpose of a JWT is to verify the identity of the issuer and ensure the token's integrity through a digital signature. Understanding this distinction helps developers decide what data to include in a JWT and how to handle it securely.
JWT in Authentication Flow
-
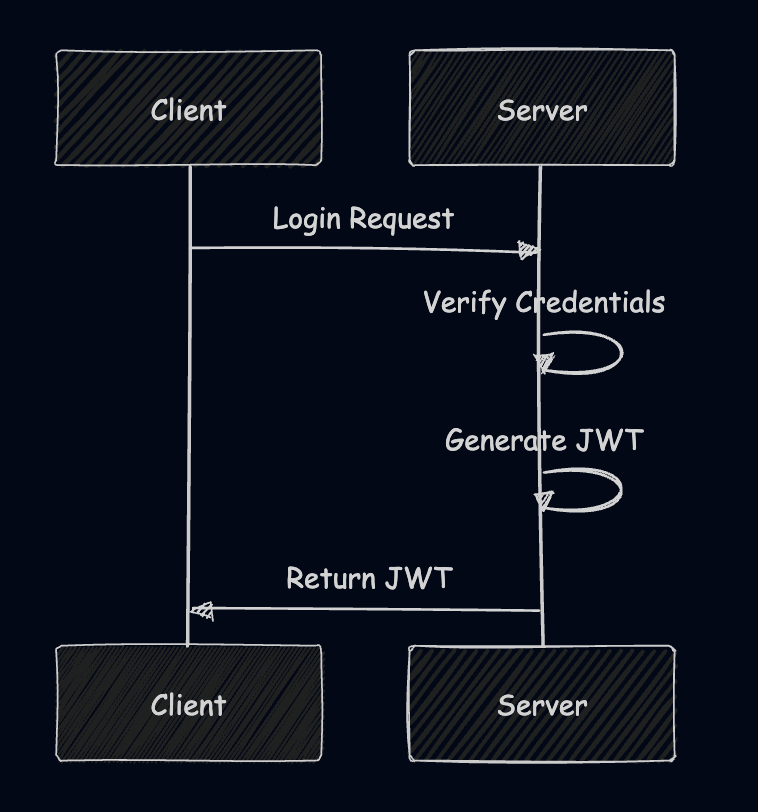
User Login
- The client sends a login request with credentials.
- The server verifies the credentials and, if valid, generates a JWT.
- The JWT is sent back to the client and stored, typically in a secure, HttpOnly cookie.
-
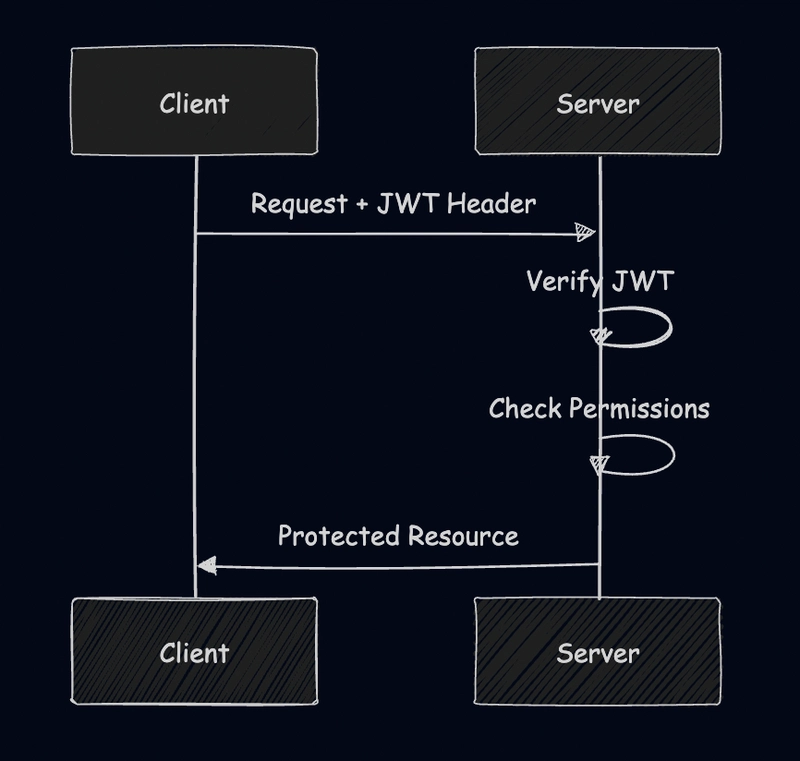
Subsequent Requests
- The client includes the JWT in the Authorization header of subsequent requests.
- The server verifies the JWT and checks permissions before granting access to protected resources.
JWT for Authorization
JWTs excel at authorization because they can carry role and permission information. This allows for fine-grained access control based on the user's role and permissions.
{
"sub": "1234567890",
"role": "admin",
"permissions": ["read", "write", "delete"],
"department": "engineering"
}
Security Best Practices
-
Token Expiration
- Use short-lived access tokens to minimize the risk of token theft.
- Implement refresh token rotation to maintain user sessions securely.
- Always include the
expclaim to define the token's expiration time.
-
Payload Security
- Never store sensitive data in the payload, as it can be decoded by anyone with access to the token.
- Minimize payload size to reduce the risk of exposure and improve performance.
- Use standard claims when possible to ensure compatibility and security.
-
Signature Protection
- Use strong secrets and consider using asymmetric algorithms like RS256 for added security.
- Rotate secrets periodically to mitigate the risk of key compromise.
Common JWT Pitfalls
-
Client-side Storage
- Store JWTs in HttpOnly cookies to protect against XSS attacks.
- Avoid storing JWTs in localStorage, as it is accessible via JavaScript.
- Implement CSRF protection to prevent unauthorized requests.
-
Token Invalidation
- JWTs cannot be directly revoked, so use a token blacklist to manage invalid tokens.
- Keep expiration times short to limit the impact of a compromised token.
-
Algorithm Attacks
- Always validate the
algheader to prevent algorithm substitution attacks. - Do not accept the
nonealgorithm, and use explicit algorithm checking to ensure security.
- Always validate the
Self-contained JWT Example
Encoding Example
You can create and inspect JWT parts using basic bash commands. This example demonstrates how to manually create a JWT using a secret key.
# Create a header
HEADER='{"alg":"HS256","typ":"JWT"}'
# Base64URL encode the header
function base64UrlEncode() {
local input="$1"
echo -n "$input" | base64 | tr '+/' '-_' | tr -d '='
}
# Base64URL encode the header
HEADER_ENCODED=$(base64UrlEncode "$HEADER")
echo $HEADER_ENCODED
# Create a payload
PAYLOAD='{"sub":"1234567890","name":"John Doe","iat":1516239022}'
# Base64URL encode the payload
PAYLOAD_ENCODED=$(base64UrlEncode "$PAYLOAD")
echo $PAYLOAD_ENCODED
# Create signature (using OpenSSL with a secret key)
SECRET="your-256-bit-secret"
SIGNATURE=$(echo -n "${HEADER_ENCODED}.${PAYLOAD_ENCODED}" | \
openssl dgst -binary -sha256 -hmac $SECRET | \
base64 | tr '+/' '-_' | tr -d '=')
# Combine all parts to create the final JWT
JWT="${HEADER_ENCODED}.${PAYLOAD_ENCODED}.${SIGNATURE}"
echo $JWT
Further Reading
- JWT.io - A great resource for decoding, verifying, and generating JWTs.
- RFC 7519 - JWT Standard - The official specification for JSON Web Tokens.
- OWASP JWT Security Cheat Sheet - A comprehensive guide to JWT security best practices.
- Understanding Encryption vs. Hashing - A fun and easy-to-understand explanation of the difference between encryption and hashing.
Final Thoughts
JWTs provide a powerful mechanism for handling both authentication and authorization in modern web applications. While they come with their own set of challenges, understanding their internals and following security best practices allows you to implement robust, stateless authentication systems.
Remember: Always validate tokens server-side, protect your secrets, and never trust client-side data without verification.









































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)

























































































































![[FREE EBOOKS] The Kubernetes Bible, The Ultimate Linux Shell Scripting Guide & Four More Best Selling Titles](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)



![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)






































































































.png?#)




.jpg?#)
































_Christophe_Coat_Alamy.jpg?#)






































































































![Rapidus in Talks With Apple as It Accelerates Toward 2nm Chip Production [Report]](https://www.iclarified.com/images/news/96937/96937/96937-640.jpg)