Failing the DevOps Audit? Here's What Every Secure Pipeline Needs in 2025
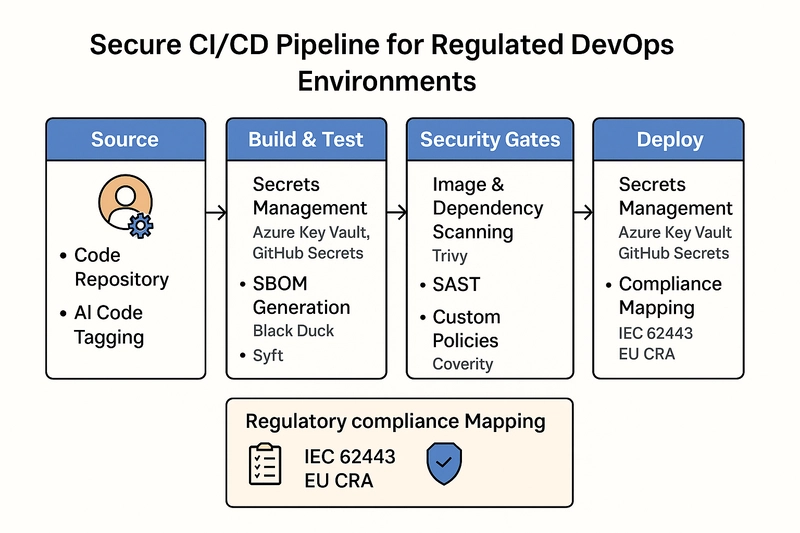
"Last month, I reviewed a FinTech's CI pipeline. Everything looked smooth… until the audit flagged 37 license violations on Open-Source Software (OSS), 2 hardcoded secrets, and no SBOM at all. Sound familiar?" It's 2025, and DevOps is everywhere - but so are audit failures. You're exposed if your team is shipping code fast but hasn't prepared for SBOM governance, CI/CD security, and AI-generated code traceability. As someone helping teams across MedTech, FinTech, and Industrial Software, here's what I've seen inside real pipelines - and why they're failing. The 5 Most Common Compliance Pitfalls in DevOps 1. No SBOM Strategy Most teams still don't generate a proper Software Bill of Materials (SBOM), or worse, they rely on automated SCA tools but never review the output. Fix: Adopt SBOM tools like BlackDuck, Syft, or CycloneDX, and automate export in your build. 2. Secrets in Repos or CI Variables I've reviewed pipelines with unencrypted secrets exposed in env variables or YAML files - a ticking time bomb. Fix: Use Azure Key Vault, GitHub Secrets, or HashiCorp Vault with strict access policies. 3. No Policy Gates or Security Gating CI/CD runs green even when critical vulnerabilities exist. Why? No security gate policies. Fix: Integrate gating with Coverity, BlackDuck, Trivy, or custom rules to break builds. 4. Lack of AI Code Tracking With the rise of AI code tools, teams can't distinguish AI-generated vs. developer-written code. This creates audit headaches under the EU CRA. Fix: Implement tagging policies or track source commits with specific AI markers + governance checklists. 5. No Mapped Compliance Framework Teams follow "best practices" but can't prove alignment with IEC 62443, CRA, or FDA pre-submission standards. Fix: Build a mapping checklist showing each security control met in your pipeline tooling. What a Secure, Audit-Ready Pipeline Looks Like Below is a high-level view of a compliant CI/CD pipeline. From SBOM generation to secrets management and security gates - each layer aligns with audit requirements: Want to Fix Your Pipeline Before the Auditor Does? I've helped DevOps and Cybersecurity teams design fast audit-ready pipelines. You can: Download my Free CI/CD YAML Audit Checklist Book a 30-minute free consult (limited slots)
"Last month, I reviewed a FinTech's CI pipeline. Everything looked smooth… until the audit flagged 37 license violations on Open-Source Software (OSS), 2 hardcoded secrets, and no SBOM at all. Sound familiar?"
It's 2025, and DevOps is everywhere - but so are audit failures. You're exposed if your team is shipping code fast but hasn't prepared for SBOM governance, CI/CD security, and AI-generated code traceability. As someone helping teams across MedTech, FinTech, and Industrial Software, here's what I've seen inside real pipelines - and why they're failing.
The 5 Most Common Compliance Pitfalls in DevOps
1. No SBOM Strategy
Most teams still don't generate a proper Software Bill of Materials (SBOM), or worse, they rely on automated SCA tools but never review the output.
Fix: Adopt SBOM tools like BlackDuck, Syft, or CycloneDX, and automate export in your build.
2. Secrets in Repos or CI Variables
I've reviewed pipelines with unencrypted secrets exposed in env variables or YAML files - a ticking time bomb.
Fix: Use Azure Key Vault, GitHub Secrets, or HashiCorp Vault with strict access policies.
3. No Policy Gates or Security Gating
CI/CD runs green even when critical vulnerabilities exist. Why? No security gate policies.
Fix: Integrate gating with Coverity, BlackDuck, Trivy, or custom rules to break builds.
4. Lack of AI Code Tracking
With the rise of AI code tools, teams can't distinguish AI-generated vs. developer-written code. This creates audit headaches under the EU CRA.
Fix: Implement tagging policies or track source commits with specific AI markers + governance checklists.
5. No Mapped Compliance Framework
Teams follow "best practices" but can't prove alignment with IEC 62443, CRA, or FDA pre-submission standards.
Fix: Build a mapping checklist showing each security control met in your pipeline tooling.
What a Secure, Audit-Ready Pipeline Looks Like
Below is a high-level view of a compliant CI/CD pipeline. From SBOM generation to secrets management and security gates - each layer aligns with audit requirements:
Want to Fix Your Pipeline Before the Auditor Does?
I've helped DevOps and Cybersecurity teams design fast audit-ready pipelines.
You can:
Download my Free CI/CD YAML
Audit Checklist
Book a 30-minute free consult (limited slots)
































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)

























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




















































































































_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




 CISO’s Core Focus.webp?#)





































































































![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)