Controlled Access in Event-Driven Architectures: Exploring Solution Approaches (Part 2 of 3)
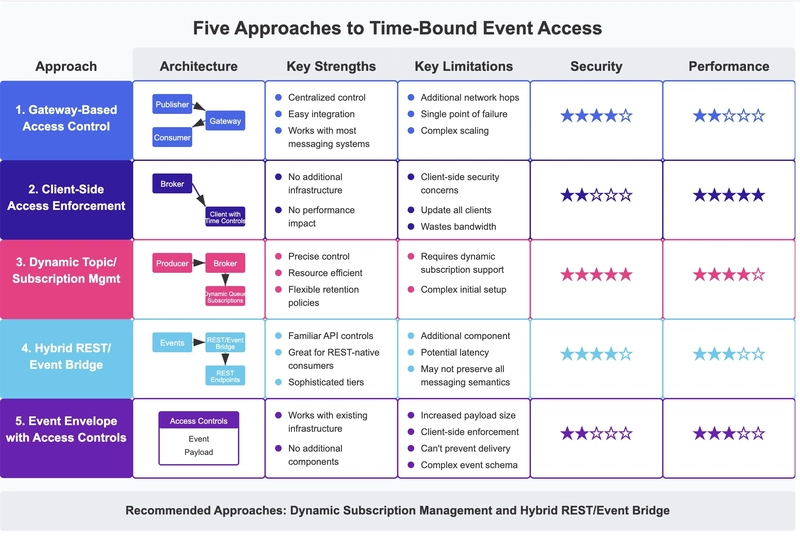
TL;DR This article presents five architectural approaches to implementing controlled, time-bound access in event-driven architectures. We analyze gateway-based solutions, client-side enforcement, dynamic subscription management, hybrid REST/event bridges, and event envelope modifications, highlighting their strengths and implementation challenges. Table of Contents Core Requirements Approach 1: Gateway-Based Access Control Approach 2: Client-Side Access Enforcement Approach 3: Dynamic Topic/Subscription Management Approach 4: Hybrid REST/Event Bridge Approach 5: Event Envelope with Embedded Access Controls Implementation Considerations The Practical Middle Ground Five approaches to implementing time-bound access in event-driven systems In our previous article, we identified a critical gap in event-driven architectures: the lack of controlled, time-bound access mechanisms that are standard in API-based systems. Today, we'll examine various approaches to bridging this gap, exploring their strengths and limitations. Core Requirements Before diving into solutions, let's establish what we're looking for in an ideal approach: Temporal Control: The ability to define precise start and end times for event streaming Non-disruptive Integration: Minimal changes to existing producers and consumers Flexible Retention: Options for storing events for delayed consumption Operational Simplicity: Manageable deployment and administration overhead Performance Neutrality: Minimal impact on throughput and latency Let's explore five different architectural patterns that address these requirements in different ways. Approach 1: Gateway-Based Access Control Description: Implementing a gateway layer between event producers and consumers that enforces access policies. Gateway-based access control architecture How It Works: Events flow through a gateway service that validates consumer authorizations Gateway maintains subscription state and enforces time-bound access Gateway can filter or block events based on subscription status Strengths: Centralizes access control in a single component Can be added to existing systems with minimal changes Works with most messaging systems and brokers Weaknesses: Introduces additional network hops and potential latency Creates a potential single point of failure May struggle with high-volume event flows Can be complex to scale horizontally Approach 2: Client-Side Access Enforcement Description: Building time-bound access controls into consumer libraries. How It Works: Consumer libraries include token-based authentication Tokens carry expiration timestamps and access scopes Libraries self-enforce access limitations Strengths: No additional infrastructure components Works with existing messaging infrastructure No performance impact on message delivery Weaknesses: Relies on client-side enforcement (security concerns) Requires updating all consumer libraries Limited serverside visibility into access status Continues to receive events even after expiration (wasting bandwidth) Approach 3: Dynamic Topic/Subscription Management Description: Controlling event access by dynamically managing subscription bindings at the messaging layer. How It Works: Create consumer-specific queues or subscription endpoints Add/remove topic subscriptions based on access windows Retain queue configurations while modifying topic bindings Strengths: Works at the messaging infrastructure level Precise control over event flow Efficient use of network and processing resources Can implement retention policies for delayed consumption Weaknesses: Requires messaging infrastructure that supports dynamic subscription changes More complex implementation for initial setup May require administrative privileges on messaging infrastructure Operational complexity in managing many dynamic subscriptions Potential latency during subscription change propagation Approach 4: Hybrid REST/Event Bridge Description: Using REST endpoints as delivery mechanisms for event streams, with controlled access at the REST layer. How It Works: Events are received and queued by a bridge component Bridge exposes REST endpoints for event consumption Standard API access controls (keys, tokens, time windows) applied at REST layer Events delivered via REST calls or webhooks Strengths: Leverages familiar API access control patterns Works well for REST-native consumers Can implement sophisticated access tiers and time windows Simplified integration for API-centric organizations Weaknesses: Additional component to deploy and manage Potential latency increase compared to direct messaging May not preserve all messaging semantics Scalability depends on implementation quality Approach 5: Event Envelope with
TL;DR
This article presents five architectural approaches to implementing controlled, time-bound access in event-driven architectures. We analyze gateway-based solutions, client-side enforcement, dynamic subscription management, hybrid REST/event bridges, and event envelope modifications, highlighting their strengths and implementation challenges.
Table of Contents
- Core Requirements
- Approach 1: Gateway-Based Access Control
- Approach 2: Client-Side Access Enforcement
- Approach 3: Dynamic Topic/Subscription Management
- Approach 4: Hybrid REST/Event Bridge
- Approach 5: Event Envelope with Embedded Access Controls
- Implementation Considerations
- The Practical Middle Ground

Five approaches to implementing time-bound access in event-driven systems
In our previous article, we identified a critical gap in event-driven architectures: the lack of controlled, time-bound access mechanisms that are standard in API-based systems. Today, we'll examine various approaches to bridging this gap, exploring their strengths and limitations.
Core Requirements
Before diving into solutions, let's establish what we're looking for in an ideal approach:
- Temporal Control: The ability to define precise start and end times for event streaming
- Non-disruptive Integration: Minimal changes to existing producers and consumers
- Flexible Retention: Options for storing events for delayed consumption
- Operational Simplicity: Manageable deployment and administration overhead
- Performance Neutrality: Minimal impact on throughput and latency
Let's explore five different architectural patterns that address these requirements in different ways.
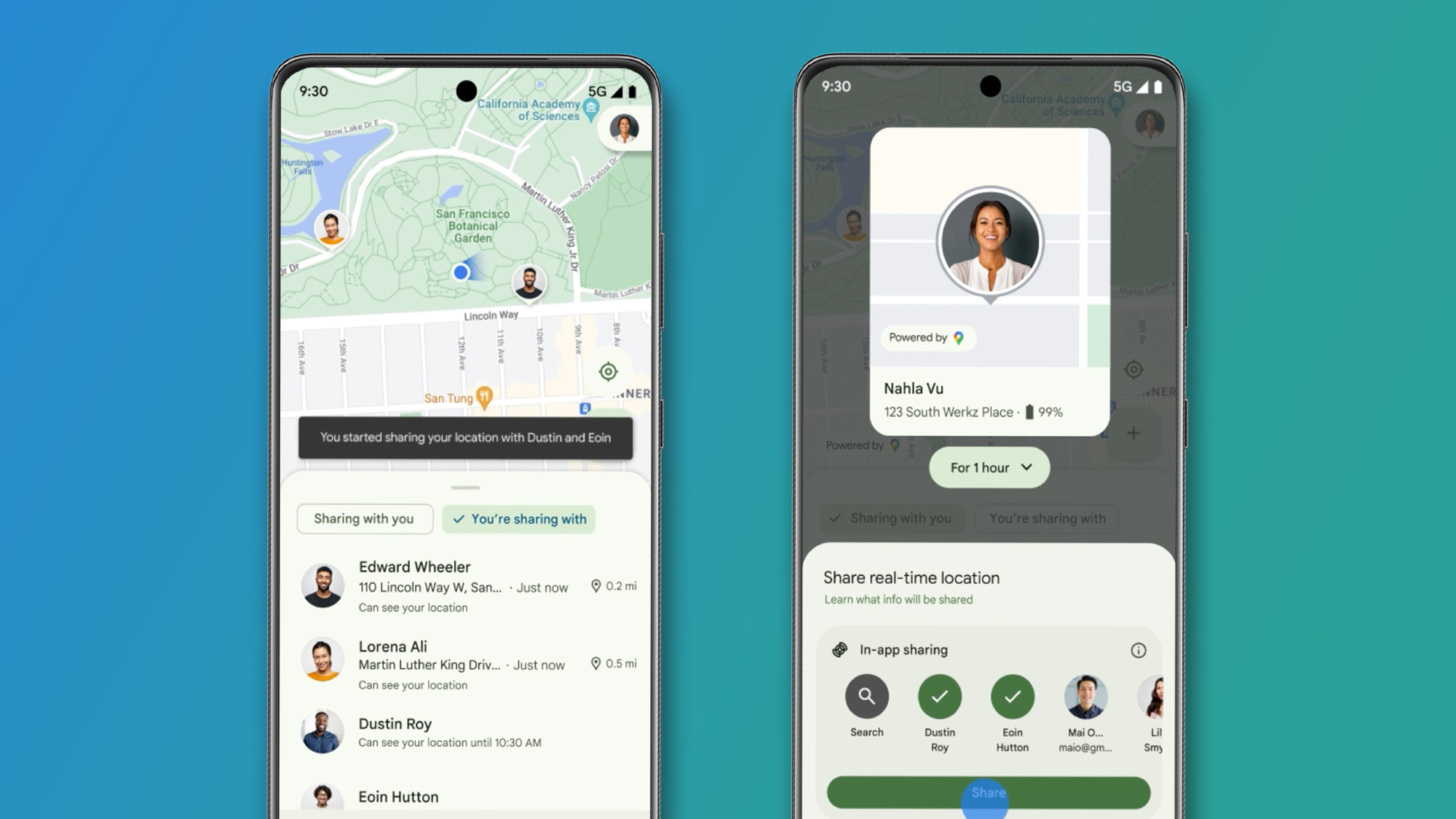
Approach 1: Gateway-Based Access Control
Description: Implementing a gateway layer between event producers and consumers that enforces access policies.
Gateway-based access control architecture
How It Works:
- Events flow through a gateway service that validates consumer authorizations
- Gateway maintains subscription state and enforces time-bound access
- Gateway can filter or block events based on subscription status
Strengths:
- Centralizes access control in a single component
- Can be added to existing systems with minimal changes
- Works with most messaging systems and brokers
Weaknesses:
- Introduces additional network hops and potential latency
- Creates a potential single point of failure
- May struggle with high-volume event flows
- Can be complex to scale horizontally
Approach 2: Client-Side Access Enforcement
Description: Building time-bound access controls into consumer libraries.
How It Works:
- Consumer libraries include token-based authentication
- Tokens carry expiration timestamps and access scopes
- Libraries self-enforce access limitations
Strengths:
- No additional infrastructure components
- Works with existing messaging infrastructure
- No performance impact on message delivery
Weaknesses:
- Relies on client-side enforcement (security concerns)
- Requires updating all consumer libraries
- Limited serverside visibility into access status
- Continues to receive events even after expiration (wasting bandwidth)
Approach 3: Dynamic Topic/Subscription Management
Description: Controlling event access by dynamically managing subscription bindings at the messaging layer.
How It Works:
- Create consumer-specific queues or subscription endpoints
- Add/remove topic subscriptions based on access windows
- Retain queue configurations while modifying topic bindings
Strengths:
- Works at the messaging infrastructure level
- Precise control over event flow
- Efficient use of network and processing resources
- Can implement retention policies for delayed consumption
Weaknesses:
- Requires messaging infrastructure that supports dynamic subscription changes
- More complex implementation for initial setup
- May require administrative privileges on messaging infrastructure
- Operational complexity in managing many dynamic subscriptions
- Potential latency during subscription change propagation
Approach 4: Hybrid REST/Event Bridge
Description: Using REST endpoints as delivery mechanisms for event streams, with controlled access at the REST layer.
How It Works:
- Events are received and queued by a bridge component
- Bridge exposes REST endpoints for event consumption
- Standard API access controls (keys, tokens, time windows) applied at REST layer
- Events delivered via REST calls or webhooks
Strengths:
- Leverages familiar API access control patterns
- Works well for REST-native consumers
- Can implement sophisticated access tiers and time windows
- Simplified integration for API-centric organizations
Weaknesses:
- Additional component to deploy and manage
- Potential latency increase compared to direct messaging
- May not preserve all messaging semantics
- Scalability depends on implementation quality
Approach 5: Event Envelope with Embedded Access Controls
Description: Embedding access control metadata in event payloads themselves.
How It Works:
- Add access control metadata to event envelopes
- Consumers validate their access rights against embedded metadata
- Infrastructure or consumers filter events based on access rights
Strengths:
- Works with existing messaging infrastructure
- No additional components needed
- Access control travels with the data
Weaknesses:
- Increases event payload size
- Relies on consumer-side enforcement
- Can't prevent delivery of events, only usage
- More complex event schema
Implementation Considerations
When evaluating these approaches, organizations should consider several factors:
- Scale: How many consumers and events will the system handle?
- Latency Requirements: How time-sensitive are the events?
- Security Posture: How critical is it to prevent unauthorized access?
- Existing Infrastructure: What messaging systems are already in place?
- Operational Capacity: Who will manage the solution day-to-day?
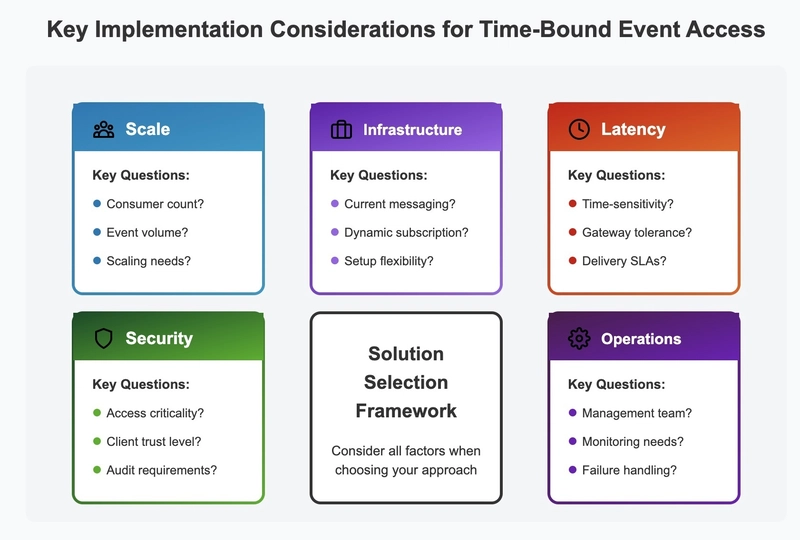
Decision framework for selecting an approach
The Practical Middle Ground
In practice, Approach 3 (Dynamic Topic/Subscription Management) and Approach 4 (Hybrid REST/Event Bridge) often provide the best balance of security, performance, and implementation feasibility.
The dynamic subscription approach works well for pure event-driven architectures, while the hybrid bridge approach offers an excellent transition path for organizations with significant API investment.
These middle-ground solutions typically provide:
- Stronger security than client-side enforcement
- Better performance than gateway-based approaches
- More flexible implementation options
- Easier operational management
Looking Forward
In our next article, we'll explore a specific implementation of the hybrid REST/Event bridge approach using modern event broker technology, detailing how it can be implemented to provide time-bound event access with minimal overhead.
We'll examine a proof-of-concept solution built using Solace EDA Platform that brings API-like subscription models to event-driven architectures, complete with a management interface for creating and controlling event access windows.
By the end of this series, you'll have a comprehensive understanding of not just the theoretical approaches to time-bound event access, but a concrete implementation path that you can adapt to your organization's needs.
Which of these approaches seems most suitable for your current architecture? Have you implemented something similar? Share your thoughts in the comments


































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)





























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)






















![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)



















































































































_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)













































































































![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)