Cloud Security Automation: Essential for Modern Environments
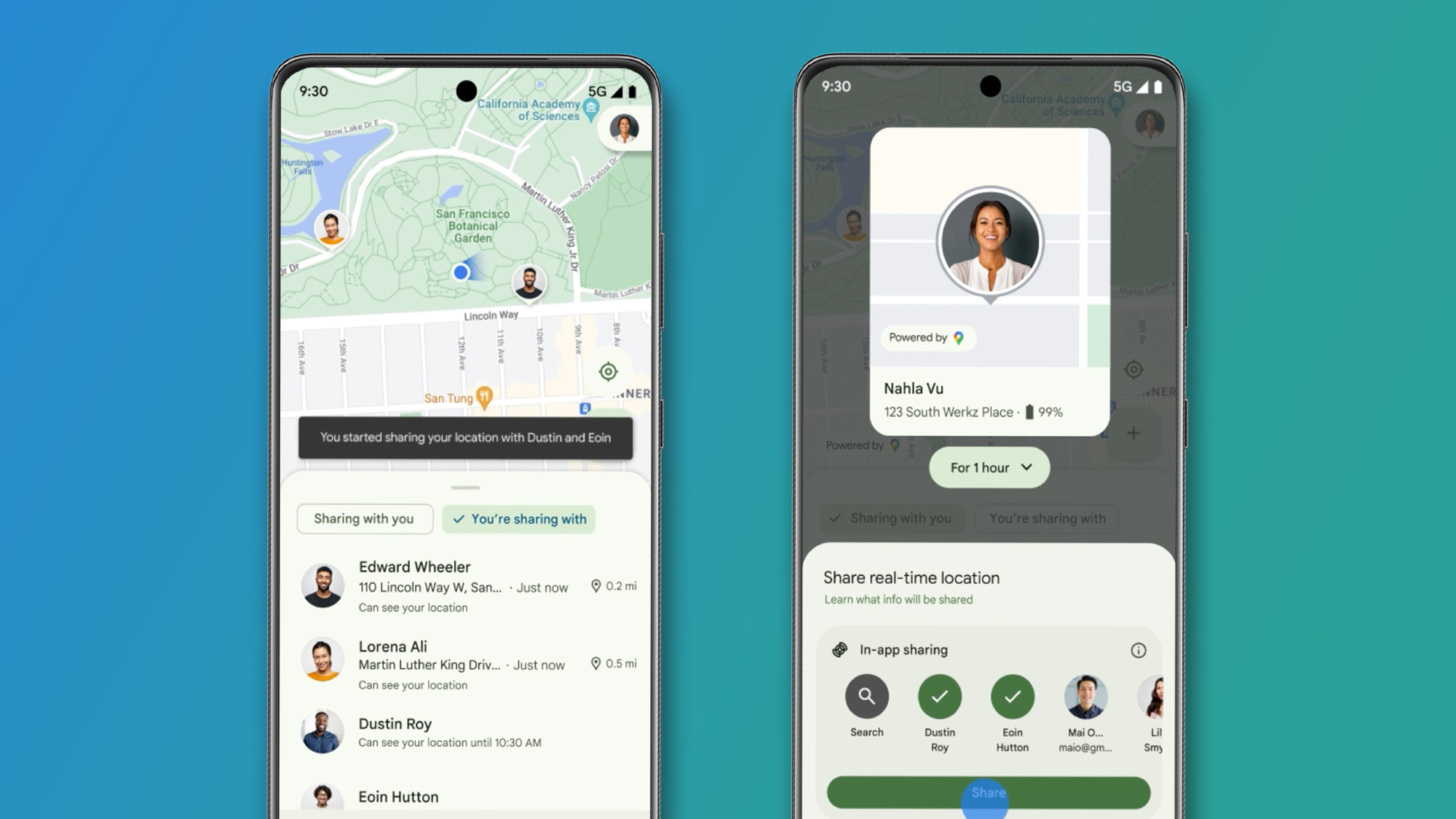
As organizations rapidly adopt cloud technologies, cloud security automation has become essential for protecting digital assets. Security teams face mounting challenges in managing dynamic cloud environments, where resources constantly change and access permissions require ongoing updates. Traditional manual approaches can no longer keep pace with the volume of security alerts and the complexity of cloud infrastructure. Modern security platforms now offer streamlined solutions that enable teams to automate critical security tasks without extensive technical expertise. Key Benefits of Security Automation Security teams gain multiple strategic advantages when implementing automated cloud security processes. Modern automation tools transform how organizations protect their cloud infrastructure while maximizing team efficiency and response capabilities. Elimination of Manual Tasks Security professionals spend countless hours performing repetitive tasks like reviewing logs, updating access controls, and responding to basic alerts. Automation eliminates these time-consuming activities, allowing teams to focus on complex security challenges that require human expertise. By handling routine operations automatically, security staff can dedicate their skills to threat hunting, incident investigation, and strategic security improvements. Reduced Risk of Human Error Manual security processes are inherently prone to mistakes. Even experienced professionals can mistype commands, overlook critical alerts, or forget steps in complex procedures. Automated systems execute tasks with perfect consistency, following predefined workflows without deviation. This systematic approach ensures security controls are applied uniformly across cloud environments, significantly decreasing the likelihood of configuration errors or missed security incidents. Enhanced Incident Response Speed Cloud environments generate security alerts at a massive scale, far beyond what human teams can process manually. Automation platforms can analyze and respond to threats in seconds, compared to the minutes or hours required for manual investigation. This rapid response capability is crucial for containing potential security breaches before they can cause significant damage. Automated systems can immediately implement defensive measures, such as isolating compromised resources or revoking suspicious access credentials, without waiting for human intervention. Scalable Security Operations As cloud infrastructures grow, security operations must scale accordingly. Automation allows security teams to maintain effective protection even as their cloud footprint expands. Automated workflows can monitor and protect thousands of cloud resources simultaneously, adjusting security controls and responding to threats across the entire environment. This scalability ensures consistent security coverage without requiring proportional increases in security staff. Challenges in Cloud Security Management While automation offers significant advantages, security teams must navigate several unique obstacles when protecting cloud environments. Understanding these challenges is crucial for implementing effective security automation strategies. Dynamic Resource Management Cloud environments are inherently fluid, with resources constantly being created and destroyed. Virtual machines, containers, and serverless functions may exist for only minutes or hours, making traditional security monitoring approaches ineffective. Security teams must implement automated systems that can track and protect these ephemeral resources throughout their brief lifecycles. This requires continuous discovery mechanisms and real-time security policy enforcement that adapts to rapid infrastructure changes. Identity and Access Management Complexity Managing access permissions in cloud environments presents ongoing challenges. Organizations must constantly adjust IAM policies as applications evolve, teams change, and new services are deployed. Without automation, security teams struggle to maintain proper access controls and risk creating security gaps through misconfigured permissions. Automated IAM management systems must continuously monitor and adjust access rights while ensuring compliance with security policies and regulatory requirements. Alert Volume and Analysis Cloud platforms generate massive amounts of security alerts, far exceeding the processing capacity of human analysts. Security teams face the daunting task of filtering through thousands of notifications to identify genuine threats. Traditional manual alert triage becomes impossible at cloud scale, leading to alert fatigue and potentially missed security incidents. Automated systems must intelligently analyze and prioritize alerts, correlating information from multiple sources to identify significant security events. I

As organizations rapidly adopt cloud technologies, cloud security automation has become essential for protecting digital assets. Security teams face mounting challenges in managing dynamic cloud environments, where resources constantly change and access permissions require ongoing updates. Traditional manual approaches can no longer keep pace with the volume of security alerts and the complexity of cloud infrastructure. Modern security platforms now offer streamlined solutions that enable teams to automate critical security tasks without extensive technical expertise.
Key Benefits of Security Automation
Security teams gain multiple strategic advantages when implementing automated cloud security processes. Modern automation tools transform how organizations protect their cloud infrastructure while maximizing team efficiency and response capabilities.
Elimination of Manual Tasks
Security professionals spend countless hours performing repetitive tasks like reviewing logs, updating access controls, and responding to basic alerts. Automation eliminates these time-consuming activities, allowing teams to focus on complex security challenges that require human expertise. By handling routine operations automatically, security staff can dedicate their skills to threat hunting, incident investigation, and strategic security improvements.
Reduced Risk of Human Error
Manual security processes are inherently prone to mistakes. Even experienced professionals can mistype commands, overlook critical alerts, or forget steps in complex procedures. Automated systems execute tasks with perfect consistency, following predefined workflows without deviation. This systematic approach ensures security controls are applied uniformly across cloud environments, significantly decreasing the likelihood of configuration errors or missed security incidents.
Enhanced Incident Response Speed
Cloud environments generate security alerts at a massive scale, far beyond what human teams can process manually. Automation platforms can analyze and respond to threats in seconds, compared to the minutes or hours required for manual investigation. This rapid response capability is crucial for containing potential security breaches before they can cause significant damage. Automated systems can immediately implement defensive measures, such as isolating compromised resources or revoking suspicious access credentials, without waiting for human intervention.
Scalable Security Operations
As cloud infrastructures grow, security operations must scale accordingly. Automation allows security teams to maintain effective protection even as their cloud footprint expands. Automated workflows can monitor and protect thousands of cloud resources simultaneously, adjusting security controls and responding to threats across the entire environment. This scalability ensures consistent security coverage without requiring proportional increases in security staff.
Challenges in Cloud Security Management
While automation offers significant advantages, security teams must navigate several unique obstacles when protecting cloud environments. Understanding these challenges is crucial for implementing effective security automation strategies.
Dynamic Resource Management
Cloud environments are inherently fluid, with resources constantly being created and destroyed. Virtual machines, containers, and serverless functions may exist for only minutes or hours, making traditional security monitoring approaches ineffective. Security teams must implement automated systems that can track and protect these ephemeral resources throughout their brief lifecycles. This requires continuous discovery mechanisms and real-time security policy enforcement that adapts to rapid infrastructure changes.
Identity and Access Management Complexity
Managing access permissions in cloud environments presents ongoing challenges. Organizations must constantly adjust IAM policies as applications evolve, teams change, and new services are deployed. Without automation, security teams struggle to maintain proper access controls and risk creating security gaps through misconfigured permissions. Automated IAM management systems must continuously monitor and adjust access rights while ensuring compliance with security policies and regulatory requirements.
Alert Volume and Analysis
Cloud platforms generate massive amounts of security alerts, far exceeding the processing capacity of human analysts. Security teams face the daunting task of filtering through thousands of notifications to identify genuine threats. Traditional manual alert triage becomes impossible at cloud scale, leading to alert fatigue and potentially missed security incidents. Automated systems must intelligently analyze and prioritize alerts, correlating information from multiple sources to identify significant security events.
Integration Requirements
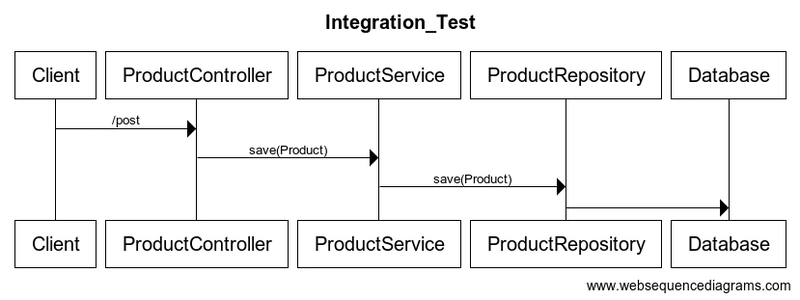
Modern cloud environments utilize diverse services and tools, each generating its own security data and requiring specific management approaches. Security teams must integrate multiple security tools, monitoring systems, and response mechanisms into a cohesive security framework. This integration challenge requires automated platforms that can seamlessly connect different security components while maintaining consistent policy enforcement across the entire cloud infrastructure.
Modern Security Automation Platforms
Security orchestration and automation platforms have evolved to address the complex demands of cloud security. These solutions provide comprehensive tools that transform how organizations implement and manage security automation.
Simplified Workflow Creation
Modern automation platforms offer intuitive interfaces that enable security teams to build sophisticated workflows without extensive programming knowledge. Through visual editors and pre-built components, security professionals can design complex automation processes using drag-and-drop functionality. This accessibility allows teams to rapidly develop and deploy security automations that previously required significant development resources.
Ready-to-Use Integrations
Leading platforms provide extensive libraries of pre-configured integrations with common security tools and cloud services. These built-in connections eliminate the need for custom integration development, significantly reducing implementation time. Security teams can quickly connect their existing security infrastructure to automated workflows, ensuring seamless operation across different tools and platforms.
Maintenance and Updates
Platform providers handle the underlying infrastructure maintenance, including updates, patches, and integration maintenance. This managed approach frees security teams from the burden of maintaining separate automation systems or custom scripts. As security tools and cloud services evolve, the platform providers ensure continued compatibility and functionality, reducing the operational overhead for security teams.
Scalable Architecture
Modern automation platforms are designed to scale with organizational needs. Their cloud-native architecture allows for seamless expansion as security requirements grow, without requiring significant infrastructure changes. These platforms can handle increasing workflow complexity and higher automation volumes while maintaining performance and reliability.
Security and Compliance Features
Enterprise-grade automation platforms include built-in security controls and compliance capabilities. They offer features like role-based access control, audit logging, and encryption to protect automation workflows and sensitive data. These security measures ensure that automation itself doesn't introduce new vulnerabilities while helping organizations maintain regulatory compliance.
Conclusion
The rapid evolution of cloud environments demands sophisticated security automation solutions. Organizations must embrace automated approaches to effectively protect their cloud infrastructure while managing increasing security workloads. Modern automation platforms provide the essential tools and capabilities needed to address these challenges effectively.
Security teams benefit from reduced manual effort, improved accuracy, and faster incident response through automation. These advantages become particularly crucial as cloud environments grow more complex and threats become more sophisticated. By implementing automation platforms, organizations can maintain robust security practices without overwhelming their security staff.
The latest generation of security automation platforms offers unprecedented accessibility and functionality. Their user-friendly interfaces and pre-built integrations enable security teams to implement advanced automation without extensive technical expertise. This democratization of security automation helps organizations of all sizes enhance their security posture and operational efficiency.
As cloud adoption continues to accelerate, security automation will become increasingly vital for maintaining effective security programs. Organizations that leverage these tools position themselves to better protect their digital assets while optimizing their security operations. The future of cloud security clearly lies in intelligent automation that can adapt and scale with evolving security needs.































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)

























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




























































































-The-Elder-Scrolls-IV-Oblivion-Remastered---Official-Reveal-00-18-14.png?width=1920&height=1920&fit=bounds&quality=70&format=jpg&auto=webp#)























_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




 CISO’s Core Focus.webp?#)










































































































![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)

![Apple Drops New Immersive Adventure Episode for Vision Pro: 'Hill Climb' [Video]](https://www.iclarified.com/images/news/97133/97133/97133-640.jpg)