Centralizing AWS Root User Management: A Best Practice for Security and Compliance
In today's complex cloud environments, managing access and permissions across multiple AWS accounts can be overwhelming and often a neglected task. One of the most critical aspects of this management is handling root user access for member accounts within an AWS Organization. In attempts to meet compliance, AWS customers are constantly setting root user credentials, enabling MFA, and then... promptly forgetting the password or where they stored their MFA devices. To avoid these hassles, you can centralize root access for member accounts within IAM. This removes the root user credentials within your member accounts in your AWS Organization - eliminating the need to secure your root user and use SCPs to lock them down. In this blog post, we'll review how to set up centralized root user management for member accounts as well as key considerations to setting this up in your existing AWS Organization. Why Centralize Root User Management? Before diving into the setup process, let's take a look at why centralizing root user management is crucial: Enhanced Security: Centralizing control, mitigates the risk of unauthorized access to root user accounts by not having them exist. Simplified Administration: Manage all member account root users from a single point - saves time and reduces complexity. Simplified Policies: Centralization reduces the number of SCPs required in your AWS Organization. Improved Compliance: Audit and reporting are far easier for reporting for compliance requirements. Note: Centralizing root user management does not eliminate the requirement for a root user email address when creating an AWS account within your AWS Organization. Prerequisites Prior to configuring centralized root user management in your AWS Organization, we should first setup some best practices and remove some old ones: Create or identify a member account within your AWS Organization. This AWS account will be the centralized point to manage root user access within your AWS Organization. With platformr we create our customers the Identity account which operates in your AWS Organization as the focal point to manage organizational identity operations. We will delegate the AWS Identity and Access Management to the Identity account Remove any SCP that inhibits the root user in your AWS Organization. If you keep the SCP applied, it will cause failure in your attempts to remove root user credentials from your AWS Organization. A root user deny SCP is a common implementation in existing AWS Organizations, but no longer necessary. With platformr we have removed this within our Foundation deployment in order to support the modern centralized root user management. Enabling Centralized Root User Management For instructions on how to set up centralized root user management in your AWS Organization you can follow the documentation here: Enabling centralized root access. The instructions will guide you through actions taken within your management account of your AWS Organization. While AWS documentation does not directly walk you through enabling trusted access for AWS Identity and Access Management in AWS Organizations, it does give you additional links to show you how to do it. To complete the task, all you need to do is: Go into the AWS Organizations console in the management account click on the Services link in the left-side vertical navigation, and find the AWS Identity and Access Management link in the center of the page and click to start enabling: Once enabled, you can go to the IAM console and on the left-side vertical navigation you can click on Root access management to open the list of accounts. Initially the page will open up with listing the top-level OUs and you can view the list of accounts by clicking on the List link. With the accounts listed out you should see Root user credentials listed in green font as Not present. If you had an error you will see details listed in red. This could mean: You may have an SCP blocking the root user. You are logged in as the root user of the management account and it cannot view the details. Delegating Root User Management Next you should delegate the administration of root user management in your AWS Organization. In an AWS Organization, delegating the management of AWS services allows administrators to grant specific member accounts the authority to manage certain AWS services on behalf of the organization. This delegation helps distribute administrative responsibilities, improve security, and reduce reliance on the management (root) account. Important: Restricting access to the AWS management account is essential for maintaining security. Any AWS service that integrates with AWS Organizations should be delegated to a member account rather than being managed within the AWS management account. At this time the AWS web console does not have the ability to delegate AWS Identity and Access managemen
In today's complex cloud environments, managing access and permissions across multiple AWS accounts can be overwhelming and often a neglected task. One of the most critical aspects of this management is handling root user access for member accounts within an AWS Organization. In attempts to meet compliance, AWS customers are constantly setting root user credentials, enabling MFA, and then... promptly forgetting the password or where they stored their MFA devices.
To avoid these hassles, you can centralize root access for member accounts within IAM. This removes the root user credentials within your member accounts in your AWS Organization - eliminating the need to secure your root user and use SCPs to lock them down.
In this blog post, we'll review how to set up centralized root user management for member accounts as well as key considerations to setting this up in your existing AWS Organization.
Why Centralize Root User Management?
Before diving into the setup process, let's take a look at why centralizing root user management is crucial:
- Enhanced Security: Centralizing control, mitigates the risk of unauthorized access to root user accounts by not having them exist.
- Simplified Administration: Manage all member account root users from a single point - saves time and reduces complexity.
- Simplified Policies: Centralization reduces the number of SCPs required in your AWS Organization.
- Improved Compliance: Audit and reporting are far easier for reporting for compliance requirements.
Note: Centralizing root user management does not eliminate the requirement for a root user email address when creating an AWS account within your AWS Organization.
Prerequisites
Prior to configuring centralized root user management in your AWS Organization, we should first setup some best practices and remove some old ones:
Create or identify a member account within your AWS Organization. This AWS account will be the centralized point to manage root user access within your AWS Organization. With platformr we create our customers the
Identityaccount which operates in your AWS Organization as the focal point to manage organizational identity operations. We will delegate the AWS Identity and Access Management to theIdentityaccountRemove any SCP that inhibits the root user in your AWS Organization. If you keep the SCP applied, it will cause failure in your attempts to remove root user credentials from your AWS Organization. A
root user denySCP is a common implementation in existing AWS Organizations, but no longer necessary. With platformr we have removed this within our Foundation deployment in order to support the modern centralized root user management.
Enabling Centralized Root User Management
For instructions on how to set up centralized root user management in your AWS Organization you can follow the documentation here: Enabling centralized root access. The instructions will guide you through actions taken within your management account of your AWS Organization.
While AWS documentation does not directly walk you through enabling trusted access for AWS Identity and Access Management in AWS Organizations, it does give you additional links to show you how to do it. To complete the task, all you need to do is:
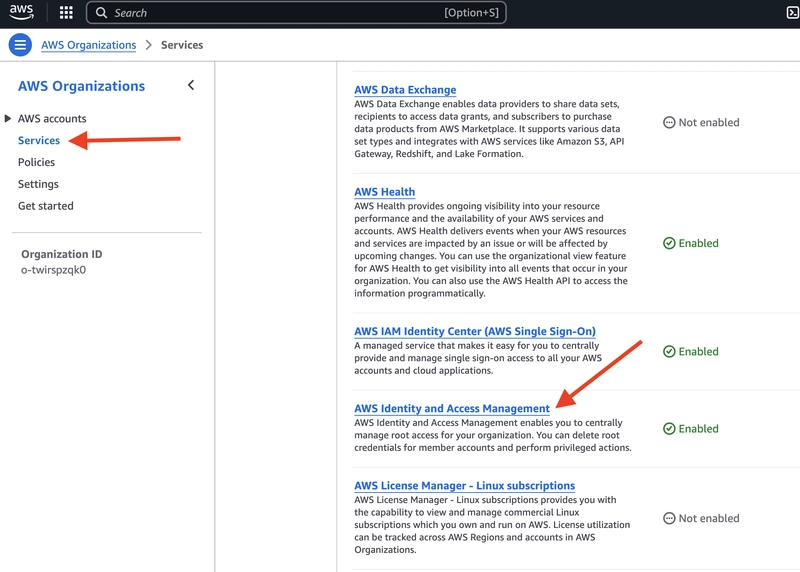
- Go into the AWS Organizations console in the management account
- click on the
Serviceslink in the left-side vertical navigation, and - find the
AWS Identity and Access Managementlink in the center of the page and click to start enabling:
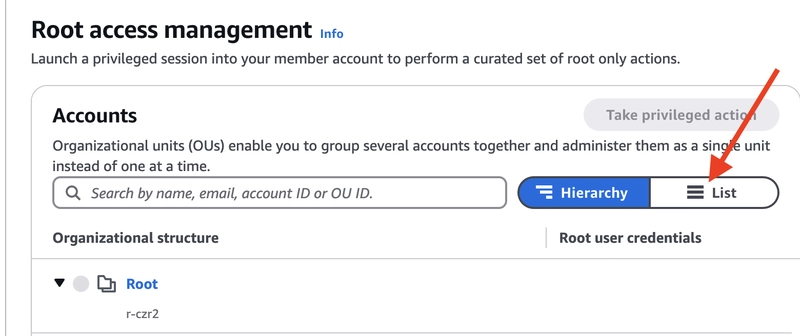
Once enabled, you can go to the IAM console and on the left-side vertical navigation you can click on Root access management to open the list of accounts.
Initially the page will open up with listing the top-level OUs and you can view the list of accounts by clicking on the List link.
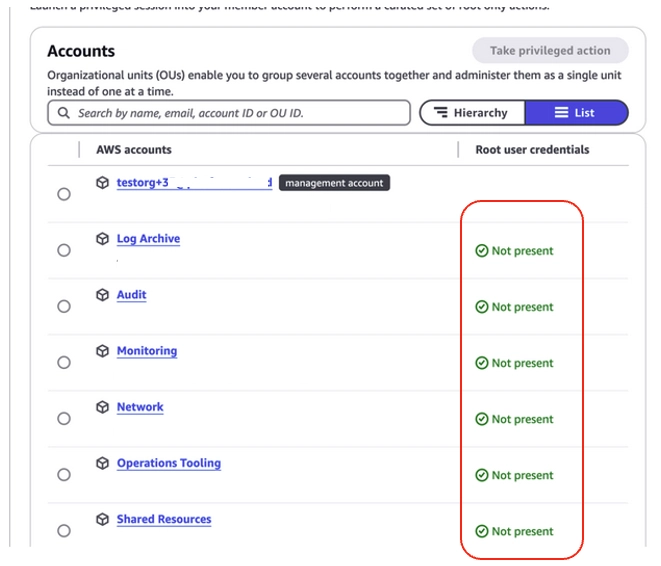
With the accounts listed out you should see Root user credentials listed in green font as Not present.
If you had an error you will see details listed in red. This could mean:
- You may have an SCP blocking the root user.
- You are logged in as the root user of the management account and it cannot view the details.
Delegating Root User Management
Next you should delegate the administration of root user management in your AWS Organization. In an AWS Organization, delegating the management of AWS services allows administrators to grant specific member accounts the authority to manage certain AWS services on behalf of the organization. This delegation helps distribute administrative responsibilities, improve security, and reduce reliance on the management (root) account.
Important: Restricting access to the AWS management account is essential for maintaining security. Any AWS service that integrates with AWS Organizations should be delegated to a member account rather than being managed within the AWS management account.
At this time the AWS web console does not have the ability to delegate AWS Identity and Access management. Instead you will need to use AWS CLI or SDK. The following is an example CLI command for registering the delegated admin account. You will need to update the --account-id with the member account in your AWS Organization.
aws organizations register-delegated-administrator
--service-principal iam.amazonaws.com
--account-id 111111111111
To align with best practices, similar service management functions should be isolated within a dedicated account. In this case, it is recommended to create an Identity account specifically for this purpose. Within platformr, we automate the creation of the Identity account and the delegation of IAM root user management, along with IAM Access Analyzer, IAM Identity Center, and other identity-related services.
Once you have registered in the delegated admin for AWS Identity and Access Management, you can log into the delegated admin AWS account and use it instead of accessing the management account. Just as you saw in the management account the Root access management in IAM web console will be available in your delegated admin account.










































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)
























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)









































































































.png?#)

































_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)

































































































![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)