Building a Scalable Micro Frontend Architecture for Enterprise Applications
Monolithic frontends are great… until they’re not. As your app grows and your teams grow faster, tightly coupled single-page applications (SPAs) become bottlenecks — blocking release cycles, bloating your CI/CD pipeline, and making every change feel like defusing a bomb. We faced this challenge and made a shift: moving from a centralized SPA to a micro frontend architecture that allowed independent development, secure integration, and long-term scalability. Here’s how we approached it. The Problem With multiple teams contributing to a shared frontend, we started seeing real issues: • Regression risk on every merge • Feature teams stepping on each other’s toes • Difficult onboarding and slower innovation • Security logic duplicated across modules We needed a way to decouple our frontend — but without breaking user experience or introducing performance penalties. The Architecture: Host + Feature Modules We built around a host shell that dynamically loads standalone feature modules. Each feature app (micro frontend) is independently built and deployed. Host responsibilities: • Routing & layout • Shared UI components • Secure session management • Loading feature modules via custom elements or dynamic imports Feature module responsibilities: • Own business logic & UI • Operate independently (separate repo, pipeline, ownership) • Integrate with host APIs and event systems This separation allowed true autonomy without giving up consistency. Security & Session Design Session handling across isolated modules is tricky. Our approach included: • Central session validation handled by the host • Controlled sharing of session metadata with feature modules • Use of lightweight client identifiers to improve trust and traceability • Feature modules validating session presence before sending requests This kept our architecture stateless on the client while preserving secure flows across boundaries. Deployment Setup Each feature app had: • Its own Git repo • Its own CI/CD pipeline • Static hosting (S3, Nginx, etc.) The host maintained a manifest (think plugin registry) and loaded modules based on role, route, or config. Result: One team’s delay or rollback didn’t affect the rest of the platform. What Worked Well • Faster releases with isolated risk • Feature teams could work independently and scale horizontally • Secure, stateless sessions that didn’t rely on sticky behavior • Unified experience for users even across separately deployed modules Lessons Learned • Define contracts early (event APIs, auth flows) • Fail gracefully when a module doesn’t load • Avoid unnecessary sharing — lean into isolation Wrapping Up Micro frontends aren’t a silver bullet — but they’re a great way to scale large frontends while keeping teams and features loosely coupled. If you’re thinking of going modular, start small. A shared shell + 1-2 feature apps is a good place to experiment. I would love to hear how others are handling session security or deployment in distributed frontends. Let’s connect!
Monolithic frontends are great… until they’re not. As your app grows and your teams grow faster, tightly coupled single-page applications (SPAs) become bottlenecks — blocking release cycles, bloating your CI/CD pipeline, and making every change feel like defusing a bomb.
We faced this challenge and made a shift: moving from a centralized SPA to a micro frontend architecture that allowed independent development, secure integration, and long-term scalability. Here’s how we approached it.
The Problem
With multiple teams contributing to a shared frontend, we started seeing real issues:
• Regression risk on every merge
• Feature teams stepping on each other’s toes
• Difficult onboarding and slower innovation
• Security logic duplicated across modules
We needed a way to decouple our frontend — but without breaking user experience or introducing performance penalties.
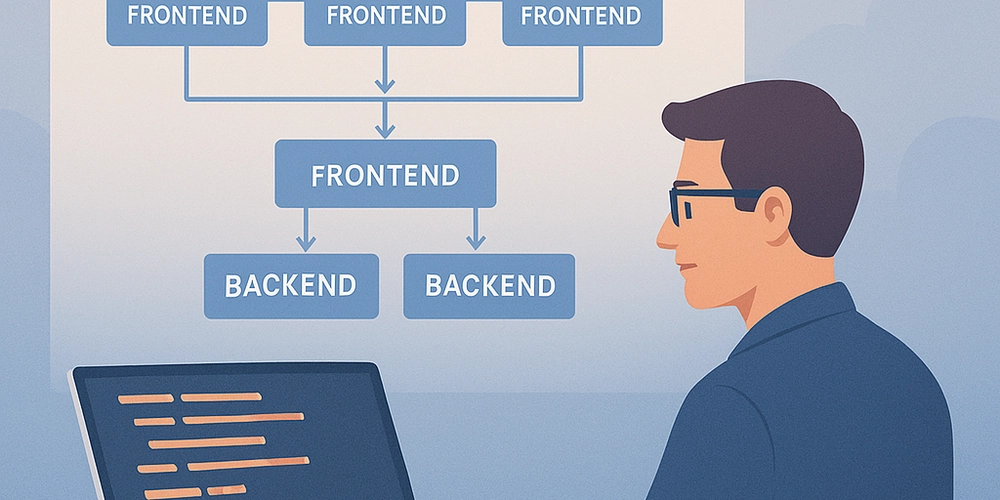
The Architecture: Host + Feature Modules
We built around a host shell that dynamically loads standalone feature modules. Each feature app (micro frontend) is independently built and deployed.
Host responsibilities:
• Routing & layout
• Shared UI components
• Secure session management
• Loading feature modules via custom elements or dynamic imports
Feature module responsibilities:
• Own business logic & UI
• Operate independently (separate repo, pipeline, ownership)
• Integrate with host APIs and event systems
This separation allowed true autonomy without giving up consistency.
Security & Session Design
Session handling across isolated modules is tricky. Our approach included:
• Central session validation handled by the host
• Controlled sharing of session metadata with feature modules
• Use of lightweight client identifiers to improve trust and traceability
• Feature modules validating session presence before sending requests
This kept our architecture stateless on the client while preserving secure flows across boundaries.
Deployment Setup
Each feature app had:
• Its own Git repo
• Its own CI/CD pipeline
• Static hosting (S3, Nginx, etc.)
The host maintained a manifest (think plugin registry) and loaded modules based on role, route, or config.
Result: One team’s delay or rollback didn’t affect the rest of the platform.
What Worked Well
• Faster releases with isolated risk
• Feature teams could work independently and scale horizontally
• Secure, stateless sessions that didn’t rely on sticky behavior
• Unified experience for users even across separately deployed modules
Lessons Learned
• Define contracts early (event APIs, auth flows)
• Fail gracefully when a module doesn’t load
• Avoid unnecessary sharing — lean into isolation
Wrapping Up
Micro frontends aren’t a silver bullet — but they’re a great way to scale large frontends while keeping teams and features loosely coupled.
If you’re thinking of going modular, start small. A shared shell + 1-2 feature apps is a good place to experiment.
I would love to hear how others are handling session security or deployment in distributed frontends. Let’s connect!










































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
















































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





































![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)