Bicep vs. Terraform
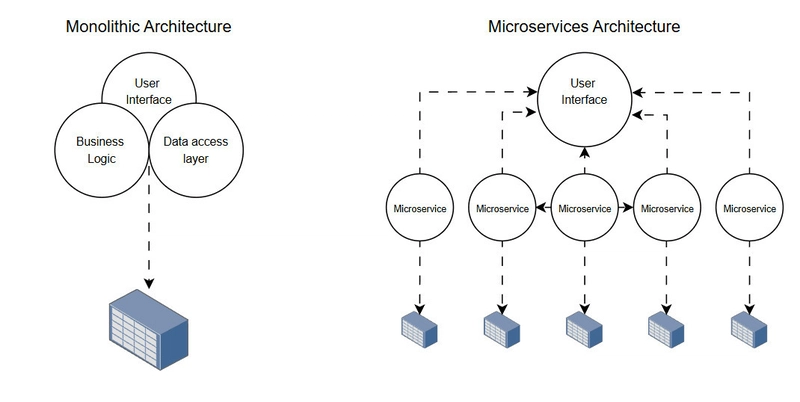
In July 2014, HashiCorp released Terraform, the leading infrastructure-as-code (IaC) solution. Terraform’s extensive provider ecosystem spans major cloud platforms, and developers can create custom providers to manage any API-driven service. In March 2021, Microsoft released Bicep, a domain-specific language designed for deploying Azure resources. This marked a significant shift for Azure users for two key reasons: It simplified the complex JSON syntax of ARM templates, and it provided native integration with Azure’s tooling and security features. Despite the existence of long-established IaC tools such as Puppet, Chef, and Ansible, Terraform and Bicep have gained strong support from the community. The main difference between them is that Terraform is cloud-agnostic and supports multiple providers, whereas Bicep is designed specifically for deploying resources in Microsoft Azure. In this post, we will examine both solutions and help you determine which best suits your use case. What is Bicep? Bicep is Microsoft's dedicated IaC language for Azure resource deployment. It provides a declarative way to define Azure infrastructure with built-in dependency management and resource visualization. Bicep files use the .bicep extension and provide type safety through automatic resource property validation and IntelliSense support in popular IDEs, helping catch configuration errors before deployment. In practice, a Bicep configuration looks like this: resource storageAccount 'Microsoft.Storage/storageAccounts@2021-06-01' = { name: 'mystorageaccount' location: 'eastus' sku: { name: 'Standard_LRS' } kind: 'StorageV2' properties: { supportsHttpsTrafficOnly: true minimumTlsVersion: 'TLS1_2' } } In the above example, we're creating an Azure storage account with a standard performance tier and locally redundant storage (LRS). The configuration specifies basic security settings, including HTTPS-only traffic and minimum TLS version 1.2. Each Bicep resource begins with the keyword resource followed by the resource type and API version, making it clear what's being deployed. It is important to note that Bicep files are modular by design, allowing you to break down complex infrastructure into reusable components. Key features of Bicep Built-in modularity: Bicep's module system allows you to create reusable components that can be shared across projects. These modules can accept parameters and return outputs, making them flexible building blocks for complex infrastructure. Stateless operations: State files are used for resource tracking and building a model of your infrastructure's current state. Unlike other IaC tools, Bicep doesn't require state file management. Azure Resource Manager tracks all resource states directly in Azure, simplifying deployment workflows and reducing operational complexity. Native Azure integration: Bicep integrates with Azure RBAC, Key Vault, and other Azure services. This native integration means you can leverage Azure's security features and access controls without additional configuration. IDE support: Because Microsoft developed both Bicep and Visual Studio Code, the integration between them is exceptional. VS Code provides rich IntelliSense support, real-time validation, and syntax highlighting for Bicep files. This tight integration significantly improves the developer experience and helps catch errors early in the development process. Why use Bicep over ARM Templates? ARM templates (Azure Resource Manager templates) are a JSON-based configuration format used to interact with the ARM. These templates provide a consistent structure for defining Azure resources and can be pinned to specific API versions, ensuring deployment stability across update cycles. JSON works well for small configurations, but as your infrastructure grows, you can quickly find yourself lost in nested brackets and what can only be described as indentation hell. Debugging becomes tedious, and making changes requires careful attention to maintain valid JSON syntax. Bicep solves this by providing a developer-friendly DSL (domain-specific language). Here is a side-by-side comparison of the storageAccount resource snippet from earlier: What is Terraform? Terraform is an IaC, that HashiCorp developed. Terraform uses HashiCorp Configuration Language(HCL), a domain-specific language designed to describe infrastructure in a concise, readable format. In practice, a Terraform configuration looks like this: resource "azurerm_storage_account" "example" { name = "mystorageaccount" resource_group_name = "example-resources" location = "eastus" account_tier = "Standard" account_replication_type = "LRS" enable_https_traffic_only = true min_tls_version = "TLS1_2" } Similar to the Bicep configuration, this Terraform code creates an Azure storage account. Th

In July 2014, HashiCorp released Terraform, the leading infrastructure-as-code (IaC) solution. Terraform’s extensive provider ecosystem spans major cloud platforms, and developers can create custom providers to manage any API-driven service.
In March 2021, Microsoft released Bicep, a domain-specific language designed for deploying Azure resources. This marked a significant shift for Azure users for two key reasons: It simplified the complex JSON syntax of ARM templates, and it provided native integration with Azure’s tooling and security features.
Despite the existence of long-established IaC tools such as Puppet, Chef, and Ansible, Terraform and Bicep have gained strong support from the community.
The main difference between them is that Terraform is cloud-agnostic and supports multiple providers, whereas Bicep is designed specifically for deploying resources in Microsoft Azure.
In this post, we will examine both solutions and help you determine which best suits your use case.
What is Bicep?
Bicep is Microsoft's dedicated IaC language for Azure resource deployment. It provides a declarative way to define Azure infrastructure with built-in dependency management and resource visualization.
Bicep files use the .bicep extension and provide type safety through automatic resource property validation and IntelliSense support in popular IDEs, helping catch configuration errors before deployment.
In practice, a Bicep configuration looks like this:
resource storageAccount 'Microsoft.Storage/storageAccounts@2021-06-01' = {
name: 'mystorageaccount'
location: 'eastus'
sku: {
name: 'Standard_LRS'
}
kind: 'StorageV2'
properties: {
supportsHttpsTrafficOnly: true
minimumTlsVersion: 'TLS1_2'
}
}
In the above example, we're creating an Azure storage account with a standard performance tier and locally redundant storage (LRS). The configuration specifies basic security settings, including HTTPS-only traffic and minimum TLS version 1.2. Each Bicep resource begins with the keyword resource followed by the resource type and API version, making it clear what's being deployed.
It is important to note that Bicep files are modular by design, allowing you to break down complex infrastructure into reusable components.
Key features of Bicep
- Built-in modularity: Bicep's module system allows you to create reusable components that can be shared across projects. These modules can accept parameters and return outputs, making them flexible building blocks for complex infrastructure.
- Stateless operations: State files are used for resource tracking and building a model of your infrastructure's current state. Unlike other IaC tools, Bicep doesn't require state file management. Azure Resource Manager tracks all resource states directly in Azure, simplifying deployment workflows and reducing operational complexity.
- Native Azure integration: Bicep integrates with Azure RBAC, Key Vault, and other Azure services. This native integration means you can leverage Azure's security features and access controls without additional configuration.
- IDE support: Because Microsoft developed both Bicep and Visual Studio Code, the integration between them is exceptional. VS Code provides rich IntelliSense support, real-time validation, and syntax highlighting for Bicep files. This tight integration significantly improves the developer experience and helps catch errors early in the development process.
Why use Bicep over ARM Templates?
ARM templates (Azure Resource Manager templates) are a JSON-based configuration format used to interact with the ARM. These templates provide a consistent structure for defining Azure resources and can be pinned to specific API versions, ensuring deployment stability across update cycles.
JSON works well for small configurations, but as your infrastructure grows, you can quickly find yourself lost in nested brackets and what can only be described as indentation hell. Debugging becomes tedious, and making changes requires careful attention to maintain valid JSON syntax.
Bicep solves this by providing a developer-friendly DSL (domain-specific language). Here is a side-by-side comparison of the storageAccount resource snippet from earlier:
What is Terraform?
Terraform is an IaC, that HashiCorp developed. Terraform uses HashiCorp Configuration Language(HCL), a domain-specific language designed to describe infrastructure in a concise, readable format.
In practice, a Terraform configuration looks like this:
resource "azurerm_storage_account" "example" {
name = "mystorageaccount"
resource_group_name = "example-resources"
location = "eastus"
account_tier = "Standard"
account_replication_type = "LRS"
enable_https_traffic_only = true
min_tls_version = "TLS1_2"
}
Similar to the Bicep configuration, this Terraform code creates an Azure storage account. The key difference in syntax is Terraform's use of quotation marks around property names and the explicit resource provider prefix azurerm_storage_account. The configuration sets up the same standard tier storage with LRS replication and basic security settings.
Key features of Terraform
- Plugin ecosystem: Terraform has a rich plugin ecosystem it calls providers. These modular components enable interaction with various cloud platforms and services. Each provider, including the Azure provider, acts as a translation layer between Terraform's configuration and the respective platform's API, such as the ARM.
- State management: State management is at the core of Terraform's operation. Terraform maintains a state file tracking all resources it manages, including their configurations and dependencies. This state allows Terraform to determine what needs to be created, updated, or deleted when configurations change.
- Workspaces: Terraform's workspace feature allows you to create isolated environments for the same code. This is useful for creating separate environments that need different variables, such as pre-prod and production environments.
- Remote backend support: Terraform can store its state files in remote backends like Azure Storage, AWS S3, or HashiCorp's Terraform Cloud. This enables team collaboration and state locking to prevent concurrent modifications and secure storage of sensitive infrastructure data.
Bicep and Terraform similarities
Terraform and Bicep share a few similarities in their approach to IaC, making them both powerful tools for modern cloud deployment.
1. Developer-friendly DSL
Both tools provide a developer-friendly domain-specific language. At a glance, Terraform's HCL and Bicep's syntax share similarities in their declarative nature and resource definition structure - although Bicep opts for a more concise syntax by eliminating quotation marks around property names.
2. Open source community
Both Bicep and Terraform have strong open-source communities. Bicep is available under the MIT License, while Terraform recently moved to the BUSL (Business Source License).
This license change in August 2023 sparked debate in the IaC community, leading to the creation of OpenTofu - a community-driven, fully open-source fork of Terraform maintained by the Linux Foundation.
3. Strong Azure integration
Bicep and Terraform offer robust Azure support. Terraform has Azure as a first-party provider and is maintained as one of the core Terraform plugins.










































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
















































































































![[DEALS] The All-in-One Microsoft Office Pro 2019 for Windows: Lifetime License + Windows 11 Pro Bundle (89% off) & Other Deals Up To 98% Off](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)





































![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)






















































































































_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)
































































































![What features do you get with Gemini Advanced? [April 2025]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2024/02/gemini-advanced-cover.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)













![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)
![EU Postpones Apple App Store Fines Amid Tariff Negotiations [Report]](https://www.iclarified.com/images/news/97068/97068/97068-640.jpg)
![Apple Slips to Fifth in China's Smartphone Market with 9% Decline [Report]](https://www.iclarified.com/images/news/97065/97065/97065-640.jpg)