Beware of this sneaky Google phishing scam
Attackers are sending phishing emails that appear to be from “no-reply@google.com,” presented as an urgent subpoena alert about “law enforcement” seeking information from the target’s Google Account. Bleeping Computer reports that the scam utilizes Google’s “Sites” web-building app to create realistic-looking phishing websites and emails that aim to intimidate victims into giving up their credentials. […]


Attackers are sending phishing emails that appear to be from “no-reply@google.com,” presented as an urgent subpoena alert about “law enforcement” seeking information from the target’s Google Account. Bleeping Computer reports that the scam utilizes Google’s “Sites” web-building app to create realistic-looking phishing websites and emails that aim to intimidate victims into giving up their credentials.
As explained by EasyDMARC, an email authentication company, the emails manage to bypass the DomainKeys Identified Mail (DKIM) authentication that would normally flag fake emails, because they came from Google’s own tool. The scammers simply entered the full text of the email as the name of their fake app, which autofills that text into an email sent by Google to their own chosen address.
When forwarded from the scammer to a user’s Gmail inbox, it remains signed and valid since DKIM only checks the message and headers. PayPal users were similarly targeted using the DKIM relay attack last month. Finally, it links to a real-looking support portal on sites.google.com instead of accounts.google.com, hoping the recipient won’t catch on.
Etherem Name Service developer Nick Johnson received the same Google phishing scam and reported the attackers’ misuse of Google OAuth applications as a security bug to Google. The company initially brushed it off as “working as intended,” but then backtracked and is now working on a fix.











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)































































































































![From fast food worker to cybersecurity engineer with Tae'lur Alexis [Podcast #169]](https://cdn.hashnode.com/res/hashnode/image/upload/v1745242807605/8a6cf71c-144f-4c91-9532-62d7c92c0f65.png?#)
























![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)























































































































_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)

_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)





















































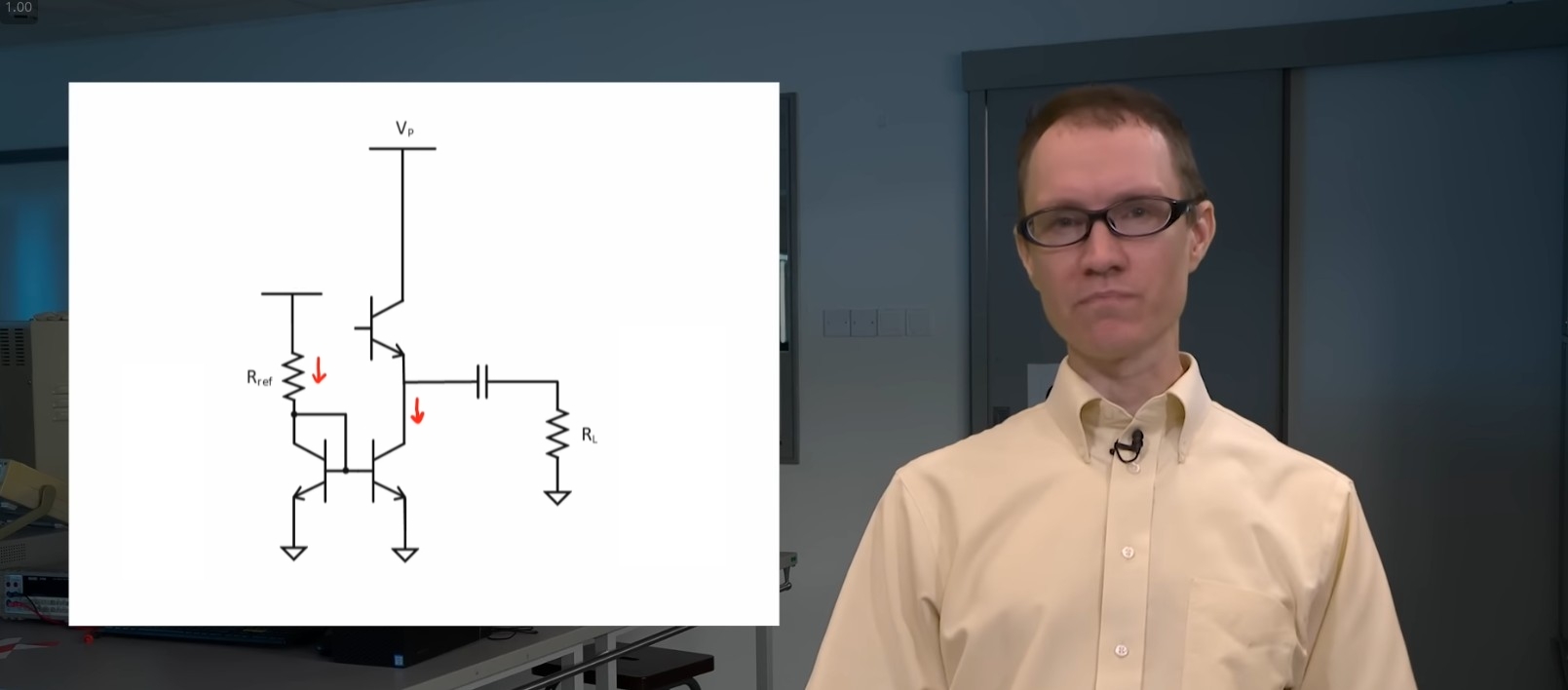






































![Apple highlights Apple Intelligence ‘Clean Up’ feature in new ad [Video]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2025/04/apple-intelligence-clean-up.jpeg?resize=1200%2C628&quality=82&strip=all&ssl=1)

![CMF Phone 2 Pro has a dual-tone design and improved camera in latest teasers [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/cmf-phone-2-pro-camera-tease.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

![Lenovo shows off its next 8.8-inch Legion Tab with vague AI promises [Gallery]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/lenovo-legion-tab-y700-2025-1.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)












![Samsung Targets Late 2026 Launch for Advanced Texas Chip Fab Following Delays [Report]](https://www.iclarified.com/images/news/97073/97073/97073-640.jpg)

![Apple Shares Official Trailer for 'Long Way Home' Starring Ewan McGregor and Charley Boorman [Video]](https://www.iclarified.com/images/news/97069/97069/97069-640.jpg)
![Apple Watch Series 10 Back On Sale for $299! [Lowest Price Ever]](https://www.iclarified.com/images/news/96657/96657/96657-640.jpg)



























![Mobile Legends: Bang Bang [MLBB] Free Redeem Codes April 2025](https://www.talkandroid.com/wp-content/uploads/2024/07/Screenshot_20240704-093036_Mobile-Legends-Bang-Bang.jpg)