A Comprehensive Guide to AES Encryption in Python
Introduction In the world of cybersecurity, encryption is a fundamental technique used to secure sensitive information. One of the most widely used encryption methods is the Advanced Encryption Standard (AES), which provides a strong layer of security against data breaches and unauthorized access. This article will provide a deep dive into AES encryption, explaining its working principles, implementation in Python, and real-world use cases. Additionally, we will explore the Fernet module from the cryptography library to perform AES encryption effortlessly. Understanding AES Encryption AES (Advanced Encryption Standard) is a symmetric encryption algorithm, meaning the same key is used for both encryption and decryption. It operates on fixed-size blocks of data, typically 128-bit, and supports key lengths of 128, 192, or 256 bits, providing robust security. Key Features of AES Feature Description Symmetric Encryption Uses the same key for both encryption and decryption. Block Cipher Works on fixed-size blocks of data (128-bit blocks). Key Sizes Supports 128, 192, and 256-bit key lengths. High Security Resistant to most cryptographic attacks. Fast Performance Efficient on both hardware and software. AES is widely used in secure communications, encrypted storage, and VPN security. AES Encryption in Python Using the Cryptography Library Python provides several libraries for encryption, but one of the most user-friendly and secure options is the cryptography library. Installing the Library Before we start coding, install the library using the following command: pip install cryptography Step-by-Step Implementation of AES Encryption 1. Generate a Secret Key The key is a crucial component in AES encryption. Using the Fernet module from cryptography, we generate a strong encryption key. from cryptography.fernet import Fernet from cryptography.fernet import Fernet key = Fernet.generate_key() print("Generated Key:", key) 2. Encrypt a Message Once we have the key, we can encrypt any plaintext message. cipher = Fernet(key) message = "This is a secret message." encrypted_message = cipher.encrypt(message.encode()) print("Encrypted Message:", encrypted_message) 3. Decrypt the Message To retrieve the original message, use the same key to decrypt it. decrypted_message = cipher.decrypt(encrypted_message).decode() print("Decrypted Message:", decrypted_message) Example Output: Generated Key: b'your_generated_key_here' Encrypted Message: b'gAAAAABg...' Decrypted Message: This is a secret message. This example demonstrates how encryption turns readable text into an unreadable format while allowing decryption when the correct key is used. AES Encryption with Manual Key and IV Handling For those who want deeper control over AES encryption, we can manually specify the key and Initialization Vector (IV). `from Crypto.Cipher import AES import base64 import os key = os.urandom(16) iv = os.urandom(16) def encrypt_message(message, key, iv): cipher = AES.new(key, AES.MODE_CBC, iv) padded_message = message + (16 - len(message) % 16) * ' ' # Padding ciphertext = cipher.encrypt(padded_message.encode()) return base64.b64encode(iv + ciphertext).decode() def decrypt_message(ciphertext, key): raw_data = base64.b64decode(ciphertext) iv = raw_data[:16] cipher = AES.new(key, AES.MODE_CBC, iv) decrypted_text = cipher.decrypt(raw_data[16:]).decode().strip() return decrypted_text message = "This is a highly secure message." encrypted_msg = encrypt_message(message, key, iv) decrypted_msg = decrypt_message(encrypted_msg, key) print(f"Encrypted: {encrypted_msg}") print(f"Decrypted: {decrypted_msg}")` Key Components in Manual AES Implementation In manual AES implementation, two critical components are involved: the Key and the Initialization Vector (IV). The Key is a secret value used for both encrypting and decrypting data. It must be kept secure because anyone with access to the key can decrypt the encrypted data. The strength of AES encryption depends on the key's length, which can be 128, 192, or 256 bits. The Initialization Vector (IV) is an additional input to the encryption process that ensures the same plaintext encrypts to different ciphertexts each time, even when the same key is used. This randomness is crucial for preventing patterns in the encrypted data, which could otherwise be exploited by attackers. The IV does not need to be secret but should be unique for each encryption operation to maintain security. AES Use Cases AES encryption is widely adopted across various industries and applications due to its robustness and efficiency. Here are some of the most common real-world use cases: Securing API Communications: APIs often transmit sensitive data between clients and servers. AES encryption ensures that th
Introduction
In the world of cybersecurity, encryption is a fundamental technique used to secure sensitive information. One of the most widely used encryption methods is the Advanced Encryption Standard (AES), which provides a strong layer of security against data breaches and unauthorized access.
This article will provide a deep dive into AES encryption, explaining its working principles, implementation in Python, and real-world use cases. Additionally, we will explore the Fernet module from the cryptography library to perform AES encryption effortlessly.
Understanding AES Encryption
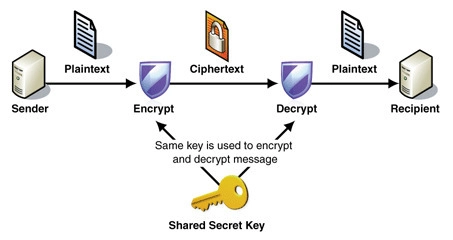
AES (Advanced Encryption Standard) is a symmetric encryption algorithm, meaning the same key is used for both encryption and decryption. It operates on fixed-size blocks of data, typically 128-bit, and supports key lengths of 128, 192, or 256 bits, providing robust security.
Key Features of AES
| Feature | Description |
|---|---|
| Symmetric Encryption | Uses the same key for both encryption and decryption. |
| Block Cipher | Works on fixed-size blocks of data (128-bit blocks). |
| Key Sizes | Supports 128, 192, and 256-bit key lengths. |
| High Security | Resistant to most cryptographic attacks. |
| Fast Performance | Efficient on both hardware and software. |
AES is widely used in secure communications, encrypted storage, and VPN security.
AES Encryption in Python Using the Cryptography Library
Python provides several libraries for encryption, but one of the most user-friendly and secure options is the cryptography library.
Installing the Library
Before we start coding, install the library using the following command:
pip install cryptography
Step-by-Step Implementation of AES Encryption
1. Generate a Secret Key
The key is a crucial component in AES encryption. Using the Fernet module from cryptography, we generate a strong encryption key.
from cryptography.fernet import Fernet
from cryptography.fernet import Fernet
key = Fernet.generate_key()
print("Generated Key:", key)
2. Encrypt a Message
Once we have the key, we can encrypt any plaintext message.
cipher = Fernet(key)
message = "This is a secret message."
encrypted_message = cipher.encrypt(message.encode())
print("Encrypted Message:", encrypted_message)
3. Decrypt the Message
To retrieve the original message, use the same key to decrypt it.
decrypted_message = cipher.decrypt(encrypted_message).decode()
print("Decrypted Message:", decrypted_message)
Example Output:
Generated Key: b'your_generated_key_here'
Encrypted Message: b'gAAAAABg...'
Decrypted Message: This is a secret message.
This example demonstrates how encryption turns readable text into an unreadable format while allowing decryption when the correct key is used.
AES Encryption with Manual Key and IV Handling
For those who want deeper control over AES encryption, we can manually specify the key and Initialization Vector (IV).
`from Crypto.Cipher import AES
import base64
import os
key = os.urandom(16)
iv = os.urandom(16)
def encrypt_message(message, key, iv):
cipher = AES.new(key, AES.MODE_CBC, iv)
padded_message = message + (16 - len(message) % 16) * ' ' # Padding
ciphertext = cipher.encrypt(padded_message.encode())
return base64.b64encode(iv + ciphertext).decode()
def decrypt_message(ciphertext, key):
raw_data = base64.b64decode(ciphertext)
iv = raw_data[:16]
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_text = cipher.decrypt(raw_data[16:]).decode().strip()
return decrypted_text
message = "This is a highly secure message."
encrypted_msg = encrypt_message(message, key, iv)
decrypted_msg = decrypt_message(encrypted_msg, key)
print(f"Encrypted: {encrypted_msg}")
print(f"Decrypted: {decrypted_msg}")`
Key Components in Manual AES Implementation
In manual AES implementation, two critical components are involved: the Key and the Initialization Vector (IV).
- The Key is a secret value used for both encrypting and decrypting data. It must be kept secure because anyone with access to the key can decrypt the encrypted data. The strength of AES encryption depends on the key's length, which can be 128, 192, or 256 bits.
- The Initialization Vector (IV) is an additional input to the encryption process that ensures the same plaintext encrypts to different ciphertexts each time, even when the same key is used. This randomness is crucial for preventing patterns in the encrypted data, which could otherwise be exploited by attackers. The IV does not need to be secret but should be unique for each encryption operation to maintain security.
AES Use Cases
AES encryption is widely adopted across various industries and applications due to its robustness and efficiency. Here are some of the most common real-world use cases:
Securing API Communications: APIs often transmit sensitive data between clients and servers. AES encryption ensures that this data remains confidential and secure, even if intercepted during transmission.
Encrypting Sensitive Data in Databases: Databases store critical information such as user credentials, financial records, and personal details. AES encryption protects this data at rest, making it unreadable to unauthorized users or attackers who gain access to the database.
Protecting Files and Storage Systems: AES is used to encrypt files, folders, and entire storage systems, ensuring that sensitive data remains secure even if the storage medium is compromised.
Ensuring Secure VPN Connections: Virtual Private Networks (VPNs) rely on AES encryption to create secure tunnels for data transmission over the internet. This ensures that all communication between the user and the VPN server remains private and protected from eavesdropping.
These use cases highlight the versatility and importance of AES encryption in modern cybersecurity practices.
Conclusion
AES encryption is a powerful tool for securing sensitive information. Whether using the cryptography library for easy implementation or manually handling encryption details, understanding AES is essential for any cybersecurity enthusiast or developer.
Would you like a deeper dive into real-world applications, such as securing API communications with AES? Let me know in the comments!











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)




























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)

































_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)





































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)