The Invisible Sudo Intruder: When Your AWS EC2 User Data Fails (and How to Fix It)
We've all been there: staring at a cloud instance that stubbornly refuses to configure itself as expected. You've meticulously crafted your user data script, double-checked your parameters, checked the iam roles for permissions and yet... nothing. The culprit? Often, it's a simple, yet easily overlooked detail: the absence of sudo. The Case of the Missing SSM Parameter Recently, I encountered a frustrating issue while automating the CloudWatch agent installation and configuration on an EC2 instance. def _create_launch_config(self, cloudwatch_config_parameter): user_data = ec2.UserData.for_linux() user_data.add_commands("pwd") user_data.add_commands( "#!/bin/bash -ex", # CloudWatch agent configuration "/opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl " "-a fetch-config -m ec2 " f"-c ssm:${cloudwatch_config_parameter} -s", ) A user data script is a script that runs automatically when an EC2 instance is launched. It's typically used for initial setup tasks, such as installing software, configuring settings, or pulling application code. How It Works: You provide the script when launching the EC2 instance (via the AWS console, CLI, or API). The script executes only once at the first boot (unless configured otherwise). It runs as the root user, usually under /var/lib/cloud/instance/scripts/. How About My Script? My user data script was designed to fetch the CloudWatch agent configuration from an SSM parameter. However, despite the script running without apparent errors, the CloudWatch agent wasn't picking up the configuration inside the EC2. After many hours of debugging, the solution turned out to be remarkably simple: adding sudo to the command that retrieved the SSM parameter. "sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl " "-a fetch-config -m ec2 " f"-c ssm:${cloudwatch_config_parameter} -s", Why sudo Matters in User Data User data scripts are executed when an EC2 instance is launched. While they sometimes run with root privileges, this isn't always guaranteed. Moreover, even if the initial script execution has elevated privileges, subsequent commands might still require explicit sudo to perform specific actions. In the case of SSM and CloudWatch, the amazon-cloudwatch-agent-ctl command needs to access system resources and interact with AWS services, which typically require root privileges. Without sudo, the command might fail silently or produce cryptic error messages that don't directly point to the permission issue. Common Scenarios Where You Need sudo in User Data: Installing software: apt-get install, yum install, etc. Modifying system configurations: Editing configuration files, creating directories, etc. Starting/stopping services: systemctl start, service restart, etc. Accessing AWS services: Using AWS CLI commands or AWS SDKs that require elevated privileges. Debugging Tips: Check system logs: Examine the EC2 instance's system logs (/var/log/syslog or /var/log/messages) for error messages. These logs often contain valuable clues about permission issues or other errors encountered during user data execution. Check application logs: If you are troubleshooting a specific application, check its logs. CloudWatch agent logs are located at /opt/aws/amazon-cloudwatch-agent/logs/amazon-cloudwatch-agent.log SSH into the created EC2 instance: This is crucial for interactive debugging. Run the commands from your user data script manually, one by one, to isolate the issue. This allows you to see the output of each command and identify any errors. Try running the command with and without sudo. Locate and inspect the CloudWatch configuration files: After the CloudWatch agent attempts to fetch its configuration, check the configuration files to see if they were created or updated correctly. The default location is usually /opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.d/file.json or /opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.json. Examine the contents of these files to ensure that the SSM parameter was retrieved successfully and that the configuration is valid. if the file does not exist, that is a huge clue that the agent was unable to pull the config. Test commands interactively: SSH into the instance and run the commands manually to see if they work with sudo. This will help you isolate permission problems. By adding these specific steps, you'll provide readers with more actionable advice for troubleshooting user data issues. Lessons Learned: Permissions are crucial: Always consider the required permissions for each command in your user data script. Explicit is better than implicit: Even if you think a command might have the necessary permissions, explicitly use sudo to avoid unexpected behavior. Debugging requires patience and methodical tes
We've all been there: staring at a cloud instance that stubbornly refuses to configure itself as expected. You've meticulously crafted your user data script, double-checked your parameters, checked the iam roles for permissions and yet... nothing. The culprit? Often, it's a simple, yet easily overlooked detail: the absence of sudo.
The Case of the Missing SSM Parameter
Recently, I encountered a frustrating issue while automating the CloudWatch agent installation and configuration on an EC2 instance.
def _create_launch_config(self, cloudwatch_config_parameter):
user_data = ec2.UserData.for_linux()
user_data.add_commands("pwd")
user_data.add_commands(
"#!/bin/bash -ex",
# CloudWatch agent configuration
"/opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl "
"-a fetch-config -m ec2 "
f"-c ssm:${cloudwatch_config_parameter} -s",
)
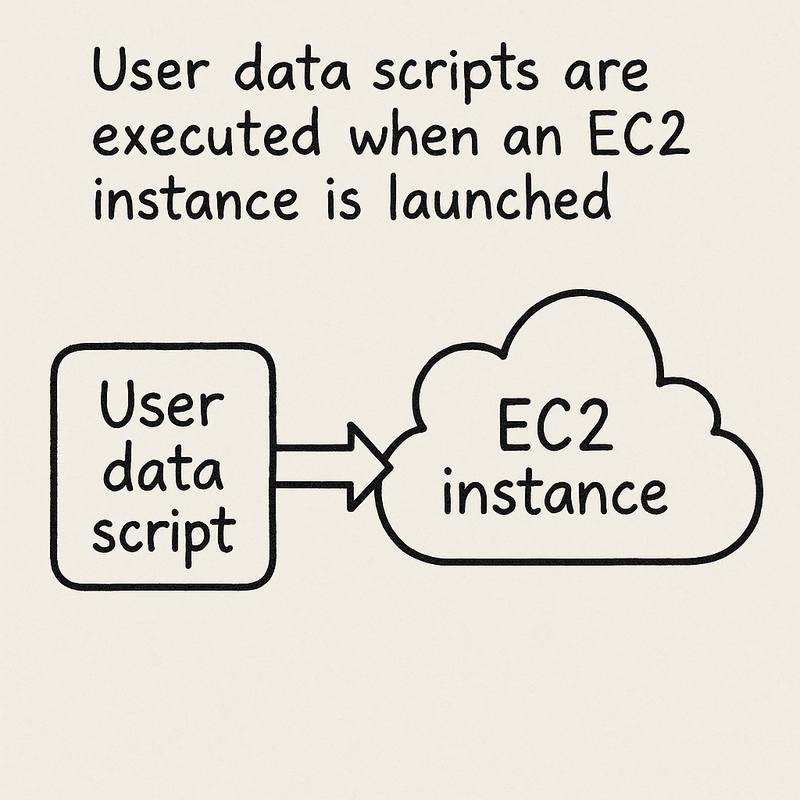
A user data script is a script that runs automatically when an EC2 instance is launched. It's typically used for initial setup tasks, such as installing software, configuring settings, or pulling application code.
How It Works:
- You provide the script when launching the EC2 instance (via the AWS console, CLI, or API).
- The script executes only once at the first boot (unless configured otherwise).
- It runs as the root user, usually under /var/lib/cloud/instance/scripts/.
How About My Script?
My user data script was designed to fetch the CloudWatch agent configuration from an SSM parameter. However, despite the script running without apparent errors, the CloudWatch agent wasn't picking up the configuration inside the EC2.
After many hours of debugging, the solution turned out to be remarkably simple: adding sudo to the command that retrieved the SSM parameter.
"sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl "
"-a fetch-config -m ec2 "
f"-c ssm:${cloudwatch_config_parameter} -s",
Why sudo Matters in User Data
User data scripts are executed when an EC2 instance is launched.
While they sometimes run with root privileges, this isn't always guaranteed. Moreover, even if the initial script execution has elevated privileges, subsequent commands might still require explicit sudo to perform specific actions.
In the case of SSM and CloudWatch, the amazon-cloudwatch-agent-ctl command needs to access system resources and interact with AWS services, which typically require root privileges. Without sudo, the command might fail silently or produce cryptic error messages that don't directly point to the permission issue.
Common Scenarios Where You Need sudo in User Data:
Installing software:
apt-get install,yum install, etc.Modifying system configurations: Editing configuration files, creating directories, etc.
Starting/stopping services:
systemctl start,service restart, etc.Accessing AWS services: Using AWS CLI commands or AWS SDKs that require elevated privileges.
Debugging Tips:
Check system logs: Examine the EC2 instance's system logs (/var/log/syslog or /var/log/messages) for error messages. These logs often contain valuable clues about permission issues or other errors encountered during user data execution.
Check application logs: If you are troubleshooting a specific application, check its logs. CloudWatch agent logs are located at /opt/aws/amazon-cloudwatch-agent/logs/amazon-cloudwatch-agent.log
-
SSH into the created EC2 instance:
- This is crucial for interactive debugging.
- Run the commands from your user data script manually, one by one, to isolate the issue.
- This allows you to see the output of each command and identify any errors.
- Try running the command with and without sudo.
-
Locate and inspect the CloudWatch configuration files:
- After the CloudWatch agent attempts to fetch its configuration, check the configuration files to see if they were created or updated correctly.
- The default location is usually
/opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.d/file.jsonor/opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.json. - Examine the contents of these files to ensure that the SSM parameter was retrieved successfully and that the configuration is valid.
- if the file does not exist, that is a huge clue that the agent was unable to pull the config.
Test commands interactively: SSH into the instance and run the commands manually to see if they work with sudo. This will help you isolate permission problems.
By adding these specific steps, you'll provide readers with more actionable advice for troubleshooting user data issues.
Lessons Learned:
Permissions are crucial: Always consider the required permissions for each command in your user data script.
Explicit is better than implicit: Even if you think a command might have the necessary permissions, explicitly use sudo to avoid unexpected behavior.Debugging requires patience and methodical testing: Don't get discouraged, systematically troubleshoot, and utilize the debugging tips mentioned above.
Don't let the silent
sudosaboteur derail your cloud automation efforts. By understanding the importance of permissions and employing effective debugging techniques, you can ensure that your user data scripts run smoothly and reliably.











































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)


























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)

































_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)





































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)




































































































































