The Biggest Failure of Next.js? CVE-2025-29927 Is a Game Over Moment
What started as an ordinary day in the Next.js community quickly turned into chaos. A devastating vulnerability—CVE-2025-29927—was discovered, allowing requests to bypass authentication middleware entirely. But here’s the kicker: Vercel and Netlify were untouched. Did they know something the rest of us didn’t? The Silence Before the Storm When the report dropped on February 27th, the response was dead silent. No urgent fix. No statement. And Lee Robinson? Nowhere to be found. The Next.js community was in the dark—completely unaware of the security nightmare lurking beneath their self-hosted deployments. Is this just an oversight, or is there more to the story? By March 14th, Next.js maintainers finally began triaging the issue. But was it too late? The vulnerability—one that could let attackers completely sidestep middleware-based authentication—had been sitting there for who knows how long. Developers relying on next start and output: 'standalone' for their self-hosted applications were left wide open. A Questionable Exclusion Perhaps the most eyebrow-raising detail of this entire saga? The platforms that weren’t affected. Vercel? Unscathed. Netlify? Completely fine. Both of these platforms were miraculously untouched by the vulnerability. For those deploying self-hosted solutions, however, it was a different story. It didn’t take long for speculation to spread: Had Vercel been aware of this weakness all along? Was it something about their infrastructure that allowed them to avoid it, or was there an internal fix they never disclosed to the broader Next.js community? The Vulnerability: A Simple Header, A Devastating Impact The flaw itself stemmed from an internal header: x-middleware-subrequest. Designed to prevent infinite request loops, it became the Achilles' heel of Next.js authentication. Attackers could forge this header, bypass middleware checks, and walk straight through authentication barriers as if they owned the place. If your security checks relied on middleware, they were effectively useless. Patching the Wound Once the Next.js team finally moved, patches came quickly: March 14: Next.js 15.x and 14.x received patches. March 17-23: Backports rolled out for versions 12 through 15. March 18: The CVE was officially issued by GitHub. March 21: The security advisory went public. The fix was in—but trust? That was another matter entirely. What Now? The Fallout and Lessons Learned Next.js has prided itself on stability, but CVE-2025-29927 raises an uncomfortable truth: self-hosted deployments are not getting the same level of proactive security as Vercel’s managed infrastructure. Whether this was an oversight or something more deliberate, the community is left wondering—what else is lurking under the surface? As the dust settles, one thing is clear: middleware can no longer be blindly trusted. And for those running self-hosted Next.js applications, the only question that remains is—what’s next?
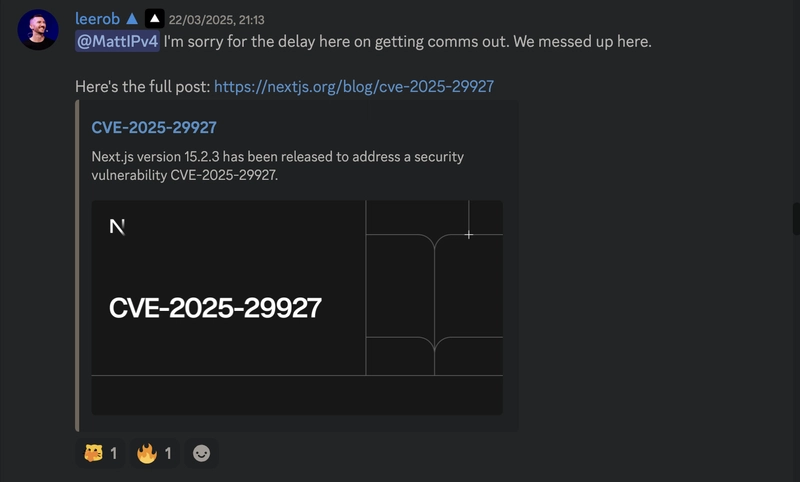
What started as an ordinary day in the Next.js community quickly turned into chaos. A devastating vulnerability—CVE-2025-29927—was discovered, allowing requests to bypass authentication middleware entirely.
But here’s the kicker: Vercel and Netlify were untouched. Did they know something the rest of us didn’t?
The Silence Before the Storm
When the report dropped on February 27th, the response was dead silent. No urgent fix. No statement. And Lee Robinson? Nowhere to be found.
The Next.js community was in the dark—completely unaware of the security nightmare lurking beneath their self-hosted deployments.
Is this just an oversight, or is there more to the story?
By March 14th, Next.js maintainers finally began triaging the issue. But was it too late? The vulnerability—one that could let attackers completely sidestep middleware-based authentication—had been sitting there for who knows how long. Developers relying on next start and output: 'standalone' for their self-hosted applications were left wide open.
A Questionable Exclusion
Perhaps the most eyebrow-raising detail of this entire saga? The platforms that weren’t affected.
- Vercel? Unscathed.
- Netlify? Completely fine.
Both of these platforms were miraculously untouched by the vulnerability. For those deploying self-hosted solutions, however, it was a different story. It didn’t take long for speculation to spread: Had Vercel been aware of this weakness all along? Was it something about their infrastructure that allowed them to avoid it, or was there an internal fix they never disclosed to the broader Next.js community?
The Vulnerability: A Simple Header, A Devastating Impact
The flaw itself stemmed from an internal header: x-middleware-subrequest. Designed to prevent infinite request loops, it became the Achilles' heel of Next.js authentication. Attackers could forge this header, bypass middleware checks, and walk straight through authentication barriers as if they owned the place. If your security checks relied on middleware, they were effectively useless.
Patching the Wound
Once the Next.js team finally moved, patches came quickly:
- March 14: Next.js 15.x and 14.x received patches.
- March 17-23: Backports rolled out for versions 12 through 15.
- March 18: The CVE was officially issued by GitHub.
- March 21: The security advisory went public.
The fix was in—but trust? That was another matter entirely.
What Now? The Fallout and Lessons Learned
Next.js has prided itself on stability, but CVE-2025-29927 raises an uncomfortable truth: self-hosted deployments are not getting the same level of proactive security as Vercel’s managed infrastructure. Whether this was an oversight or something more deliberate, the community is left wondering—what else is lurking under the surface?
As the dust settles, one thing is clear: middleware can no longer be blindly trusted. And for those running self-hosted Next.js applications, the only question that remains is—what’s next?












































































































































































![[The AI Show Episode 142]: ChatGPT’s New Image Generator, Studio Ghibli Craze and Backlash, Gemini 2.5, OpenAI Academy, 4o Updates, Vibe Marketing & xAI Acquires X](https://www.marketingaiinstitute.com/hubfs/ep%20142%20cover.png)

























































































































![[DEALS] The Premium Learn to Code Certification Bundle (97% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)


![From drop-out to software architect with Jason Lengstorf [Podcast #167]](https://cdn.hashnode.com/res/hashnode/image/upload/v1743796461357/f3d19cd7-e6f5-4d7c-8bfc-eb974bc8da68.png?#)








































































































.png?#)

































_Christophe_Coat_Alamy.jpg?#)
 (1).webp?#)





































































































![Apple Considers Delaying Smart Home Hub Until 2026 [Gurman]](https://www.iclarified.com/images/news/96946/96946/96946-640.jpg)
![iPhone 17 Pro Won't Feature Two-Toned Back [Gurman]](https://www.iclarified.com/images/news/96944/96944/96944-640.jpg)
![Tariffs Threaten Apple's $999 iPhone Price Point in the U.S. [Gurman]](https://www.iclarified.com/images/news/96943/96943/96943-640.jpg)




































































































































