Russian APT Hackers Using Device Code Phishing Technique to Bypass MFA
A sophisticated cyber campaign orchestrated by the Russian state-backed group Storm-2372 has emerged, exploiting device code phishing tactics to circumvent Multi-Factor Authentication (MFA) security measures. This targeted approach represents a significant escalation in threat actors’ capabilities to defeat advanced security systems through social engineering, allowing attackers to gain unauthorized access to high-value targets without triggering […] The post Russian APT Hackers Using Device Code Phishing Technique to Bypass MFA appeared first on Cyber Security News.

A sophisticated cyber campaign orchestrated by the Russian state-backed group Storm-2372 has emerged, exploiting device code phishing tactics to circumvent Multi-Factor Authentication (MFA) security measures.
This targeted approach represents a significant escalation in threat actors’ capabilities to defeat advanced security systems through social engineering, allowing attackers to gain unauthorized access to high-value targets without triggering traditional security alerts.
The attack campaign primarily targets organizations with valuable data and strategic influence across multiple sectors including government agencies, technology companies, financial institutions, defense contractors, healthcare providers, and media organizations.
Digital evidence of these attacks has been discovered across several nations including the United States, Ukraine, the United Kingdom, Germany, Canada, and Australia, indicating the global scope of this operation.
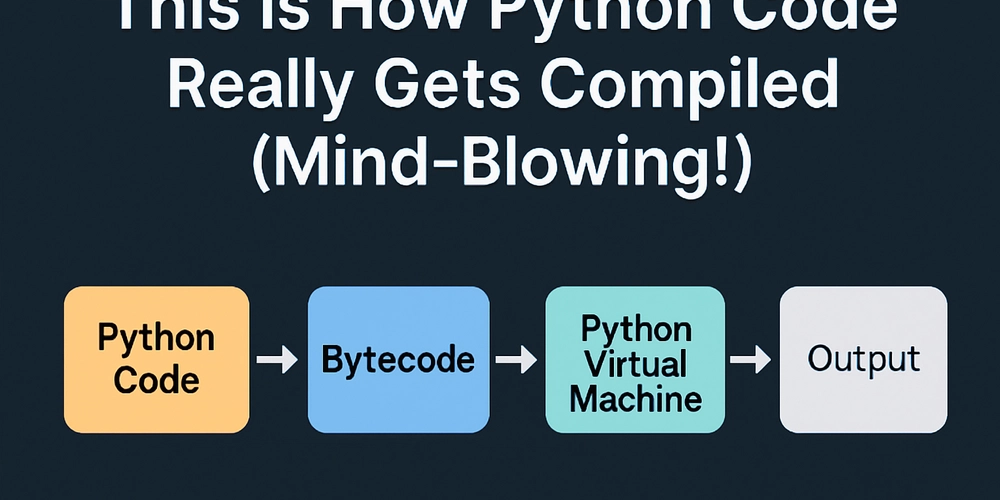
The device code phishing technique weaponizes a legitimate authentication method originally designed to simplify login processes for devices with limited input capabilities.
In these attacks, victims receive seemingly authentic phishing messages that direct them to genuine authentication portals, creating a false sense of security while the attackers operate behind the scenes.
SOCRadar researchers noted that this attack methodology is particularly dangerous because it exploits trusted authentication workflows rather than attempting to create convincing duplicates of login pages.
By leveraging actual OAuth device authorization flows, the attackers can bypass traditional phishing detection systems that look for counterfeit login pages.
The attack sequence begins when cybercriminals send phishing communications via email or SMS containing urgent authentication requests.
.webp)
These messages guide targets to actual login pages such as Microsoft’s device code portal, where victims are instructed to enter an attacker-generated code.
Upon code entry, the attacker gains persistent access to the victim’s corporate account without triggering standard MFA challenges.
Technical Examination of the Device Code Phishing Mechanism
The device code phishing attack exploits the OAuth 2.0 device authorization grant flow, which was designed to help users authenticate on devices with limited input capabilities.
When implemented legitimately, this flow allows users to authenticate on a separate device and then use a code to authorize access on the original device.
However, Storm-2372 inverts this process by controlling the authorization endpoint.
In a typical attack scenario, the threat actor initiates an OAuth authorization request to a legitimate service like Microsoft.
The service generates a device code and user code along with a verification URL. Instead of using this for legitimate purposes, the attacker forwards the user code to the victim through a phishing message.
When the victim visits the authentic verification URL and enters the provided code, they inadvertently authorize the attacker’s session.
What makes this attack particularly effective is that it doesn’t require the attacker to create fake login pages or steal credentials directly.
The victim interacts with genuine authentication portals throughout the process, making traditional phishing detection ineffective.
Furthermore, once the attacker obtains the authentication token, they can refresh it indefinitely in many configurations, maintaining persistent access even after password changes.
To defend against these sophisticated attacks, cybersecurity professionals should implement conditional access policies that restrict authentication based on device compliance and geographic location, regularly audit OAuth token requests, deploy phishing-resistant MFA solutions using FIDO2 security keys rather than SMS-based verification, and conduct comprehensive security awareness training focusing specifically on these emerging threats.
Equip your team with real-time threat analysis With ANY.RUN’s interactive cloud sandbox -> Try 14-day Free Trial
The post Russian APT Hackers Using Device Code Phishing Technique to Bypass MFA appeared first on Cyber Security News.











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)




























































































.webp?#)


























































































![Here’s the first live demo of Android XR on Google’s prototype smart glasses [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/google-android-xr-ted-glasses-demo-3.png?resize=1200%2C628&quality=82&strip=all&ssl=1)














![New Beats USB-C Charging Cables Now Available on Amazon [Video]](https://www.iclarified.com/images/news/97060/97060/97060-640.jpg)

![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)