Phantom DNS Query to GCP VM Metadata Service in My AWS Workload
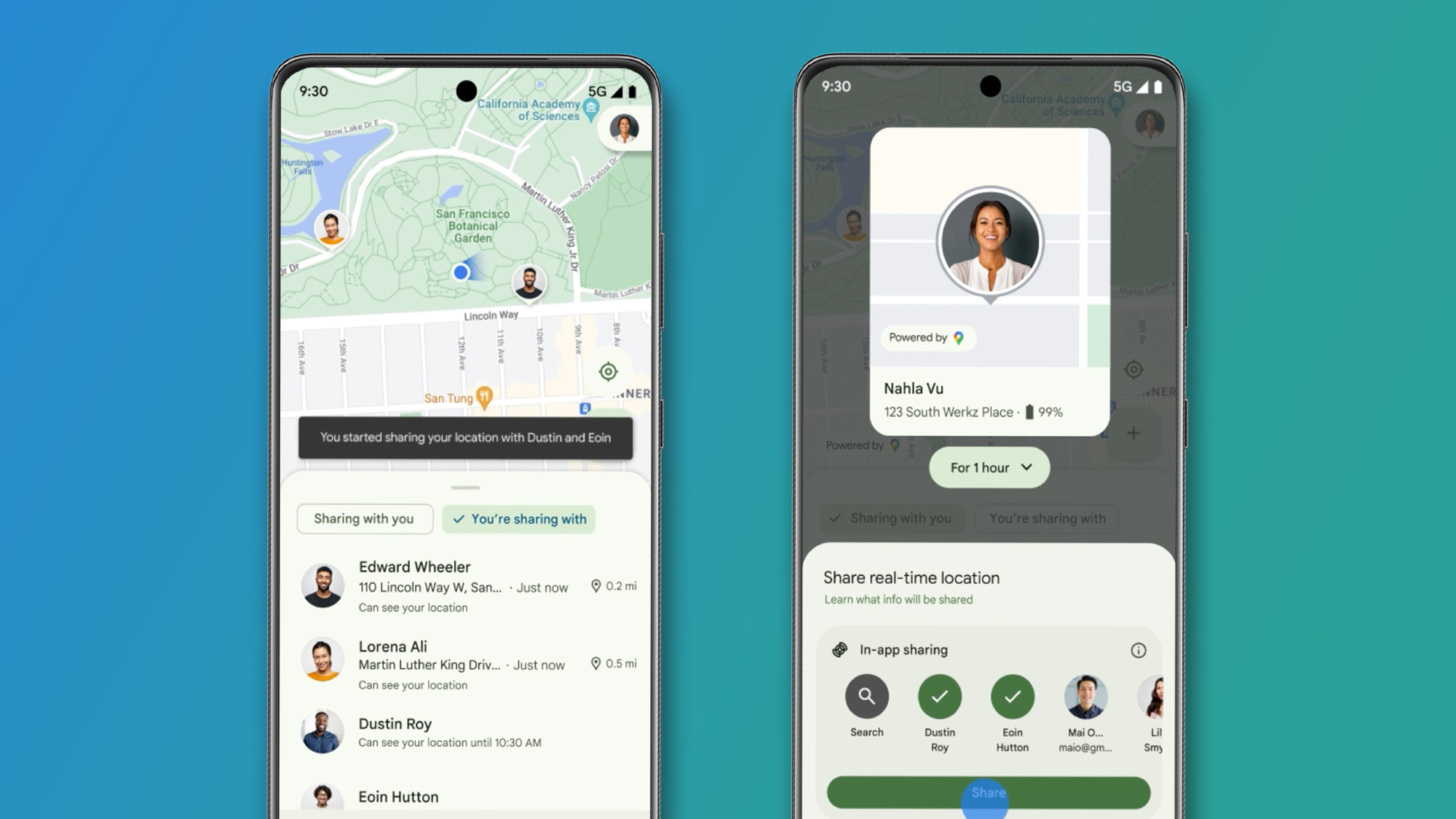
I Found Suspicious DNS Calls on AWS I was debugging flaky outbound calls from an AWS Fargate task. To gain better visibility into potential network issues, I followed the common best practice of enabling Route 53 Resolver query logging for DNS queries within my VPC on AWS. Shortly after the logs started populating, while examining them for clues related to the original outbound problems, I noticed something odd... I noticed repeated lookups for metadata.google.internal. — an endpoint meant exclusively for Google Cloud VMs, but hey, my workload was on AWS all the time! At first glance, it felt like a hacker reconnaissance probing my AWS Fargate tasks

I Found Suspicious DNS Calls on AWS
I was debugging flaky outbound calls from an AWS Fargate task. To gain better visibility into potential network issues, I followed the common best practice of enabling Route 53 Resolver query logging for DNS queries within my VPC on AWS. Shortly after the logs started populating, while examining them for clues related to the original outbound problems, I noticed something odd...
I noticed repeated lookups for metadata.google.internal. — an endpoint meant exclusively for Google Cloud VMs, but hey, my workload was on AWS all the time!
At first glance, it felt like a hacker reconnaissance probing my AWS Fargate tasks
































































































































































![[The AI Show Episode 143]: ChatGPT Revenue Surge, New AGI Timelines, Amazon’s AI Agent, Claude for Education, Model Context Protocol & LLMs Pass the Turing Test](https://www.marketingaiinstitute.com/hubfs/ep%20143%20cover.png)

























































































































![[DEALS] Koofr Cloud Storage: Lifetime Subscription (1TB) (80% off) & Other Deals Up To 98% Off – Offers End Soon!](https://www.javacodegeeks.com/wp-content/uploads/2012/12/jcg-logo.jpg)
























![Is this too much for a modular monolith system? [closed]](https://i.sstatic.net/pYL1nsfg.png)




















































































































_roibu_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)




 CISO’s Core Focus.webp?#)





































































































![M4 MacBook Air Drops to Just $849 - Act Fast! [Lowest Price Ever]](https://www.iclarified.com/images/news/97140/97140/97140-640.jpg)
![Apple Smart Glasses Not Close to Being Ready as Meta Targets 2025 [Gurman]](https://www.iclarified.com/images/news/97139/97139/97139-640.jpg)
![iPadOS 19 May Introduce Menu Bar, iOS 19 to Support External Displays [Rumor]](https://www.iclarified.com/images/news/97137/97137/97137-640.jpg)