If You Can't Control Access, You Can't Control the Cloud (Part 1)
Let's be honest, Linux file permissions don't get nearly as much hype as containers or CI/CD pipelines. But without them? Automation breaks. Access controls fail. Security nightmares begin. And that's the tea... As someone navigating this wild world of Cloud and DevOps, I've realized one truth: If you don't respect permissions, they will disrespect your entire system setup. Whether you're setting up EC2 instances, deploying containers, or managing shared cloud infrastructure, file permissions quietly, but powerfully hold everything together. So, let's shine some light on the unsung heroes of cloud infrastructure security and give them the flowers they truly deserve. Index What Are Linux Permissions? Basic Permissions: Read, Write, Execute! But Make It Practical Changing Ownership: Because Who Owns It, Owns the Power Modifying Permissions: Granular Control That Can Make or Break Your Deployment Numeric Shortcuts: Work Smarter, Not Harder! Summary: File Permissions Are Security's First Line of Defense 1. What Are Linux Permissions? Linux permissions control who can access what, and how they can interact with it. Simple, right? But in a cloud environment where multiple users, teams, services, and automation scripts interact with files and directories every second, this simple concept becomes mission critical. If you notice in all my articles I like to give various scenarios and real world use cases, now let's imagine this... You're managing a shared Linux server on AWS. Devs need read- access to config files. CI/CD scripts need execute access to deployment folders. If your permissions are too loose, one misstep can expose sensitive .env files or corrupt your deploy process. If they're too tight, automation fails and your Slack blows up with "why is the pipeline broken again?" messages. Now at the business or board level, let's say you're rolling out a financial dashboard for stakeholders. That dashboard pulls data from a backend running on Linux servers. If permissions aren't set right, unauthorized access to logs or data files could expose sensitive business data. That's not just an oops! that's a compliance issue waiting to go viral and potentially cost your company millions. Dangerous right! Now let's get into Basic Permissions... 2. Basic Permissions: Read, Write, Execute! But Make It Practical We often see drwxr-xr-- and just nod, like we totally get it (no judgment, we've all been there). But understanding this cryptic code is actually straightforward once you break it down: First character d: This is a directory, - could be for files or l for symbolic links or shortcuts). Next three characters rwx: Owner's permissions (read, write, execute) Next three characters r-x: Group's permissions (read, no write, execute) Last three characters r--: Others' permissions (read only, no write, no execute) Use ls -l or ls -ld to check permissions and you'll see the layout: user , group , and others . For best practices others has been changed to r-- (read only permission). Now, let's go back to our scenarios... Imagine you're automating backups. The backup script needs read and execute access to a directory. If it lacks execute x, the script fails even though it can read the files. Result? You think the backup succeeded, but nothing actually got saved. Two weeks later when you need those backups? Good luck explaining that one to your boss... Picture your product launch website files being updated by the marketing team. If they accidentally have write w access to production HTML files, one wrong edit and your brand goes live with "Welcome to Our Webite" yes, with the typo. And trust me, your customers will screenshot that faster than you can fix it. The nice ones will definately send to you for corrections, so let's hope all are nice... 3. Changing Ownership: Because Who Owns It, Owns the Power Ownership defines control. You can change the owner using chown, assign groups using chgrp, or do both: chown user:group directory. # Change owner chown oluwadamilola /cloud_folder # Change group chgrp dev_team /cloud_folder # Change both chown oluwadamilola:dev_team /cloud_folder Now let's put all this into practice... Interesting right, you are getting a hang of everything. So back to our practical scenarios... You are given an assignment to deploy microservices on a Kubernetes node. If files used by your containers are owned by root or another user, services may fail with permission errors. Ownership must match the container's running user. I've seen entire production environments grind to a halt because someone forgot this basic principle. Also you're the senior DevOps engineer and you're onboarding a new DevOps engineer. Transferring ownership of key automation scripts ensures continuity. If you forget? Your systems rely on a former employee's account talk about risk! Nothing says "amateur hour" like having to call a
Let's be honest, Linux file permissions don't get nearly as much hype as containers or CI/CD pipelines. But without them? Automation breaks. Access controls fail. Security nightmares begin.
And that's the tea...
As someone navigating this wild world of Cloud and DevOps, I've realized one truth: If you don't respect permissions, they will disrespect your entire system setup. Whether you're setting up EC2 instances, deploying containers, or managing shared cloud infrastructure, file permissions quietly, but powerfully hold everything together.
So, let's shine some light on the unsung heroes of cloud infrastructure security and give them the flowers they truly deserve.
Index
What Are Linux Permissions?
Basic Permissions: Read, Write, Execute! But Make It Practical
Changing Ownership: Because Who Owns It, Owns the Power
Modifying Permissions: Granular Control That Can Make or Break Your Deployment
Numeric Shortcuts: Work Smarter, Not Harder!
Summary: File Permissions Are Security's First Line of Defense
1. What Are Linux Permissions?
Linux permissions control who can access what, and how they can interact with it. Simple, right? But in a cloud environment where multiple users, teams, services, and automation scripts interact with files and directories every second, this simple concept becomes mission critical.
If you notice in all my articles I like to give various scenarios and real world use cases, now let's imagine this...
You're managing a shared Linux server on AWS. Devs need read- access to config files. CI/CD scripts need execute access to deployment folders. If your permissions are too loose, one misstep can expose sensitive .env files or corrupt your deploy process. If they're too tight, automation fails and your Slack blows up with "why is the pipeline broken again?" messages.
Now at the business or board level, let's say you're rolling out a financial dashboard for stakeholders. That dashboard pulls data from a backend running on Linux servers. If permissions aren't set right, unauthorized access to logs or data files could expose sensitive business data. That's not just an oops! that's a compliance issue waiting to go viral and potentially cost your company millions. Dangerous right! Now let's get into Basic Permissions...
2. Basic Permissions: Read, Write, Execute! But Make It Practical
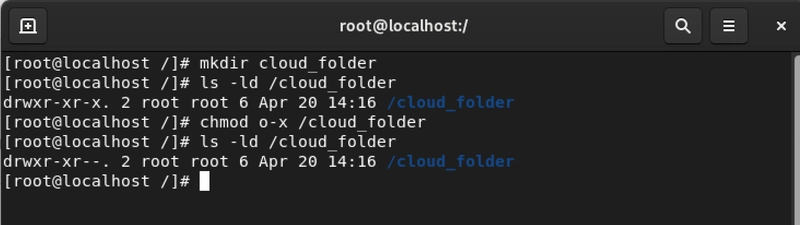
We often see drwxr-xr-- and just nod, like we totally get it (no judgment, we've all been there). But understanding this cryptic code is actually straightforward once you break it down:
- First character
d: This is a directory,-could be for files orlfor symbolic links or shortcuts). - Next three characters
rwx: Owner's permissions (read, write, execute) - Next three characters
r-x: Group's permissions (read, no write, execute) - Last three characters
r--: Others' permissions (read only, no write, no execute)
Use ls -l or ls -ld to check permissions and you'll see the layout: user , group , and others .
For best practices others has been changed to r-- (read only permission).
Now, let's go back to our scenarios...
Imagine you're automating backups. The backup script needs read and execute access to a directory. If it lacks execute x, the script fails even though it can read the files. Result? You think the backup succeeded, but nothing actually got saved. Two weeks later when you need those backups? Good luck explaining that one to your boss...
Picture your product launch website files being updated by the marketing team. If they accidentally have write w access to production HTML files, one wrong edit and your brand goes live with "Welcome to Our Webite" yes, with the typo. And trust me, your customers will screenshot that faster than you can fix it. The nice ones will definately send to you for corrections, so let's hope all are nice...
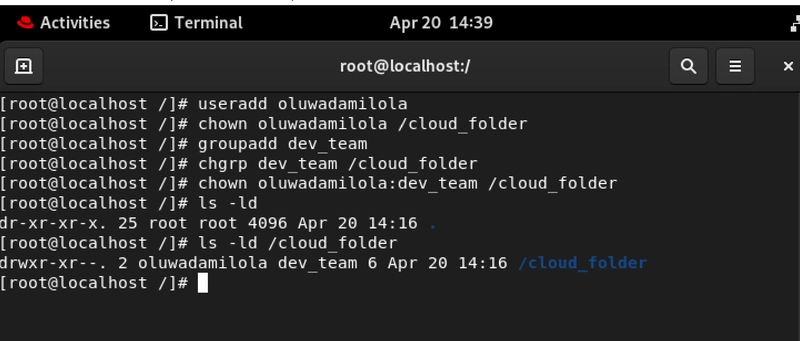
3. Changing Ownership: Because Who Owns It, Owns the Power
Ownership defines control. You can change the owner using chown, assign groups using chgrp, or do both: chown user:group directory.
# Change owner
chown oluwadamilola /cloud_folder
# Change group
chgrp dev_team /cloud_folder
# Change both
chown oluwadamilola:dev_team /cloud_folder
Now let's put all this into practice...
Interesting right, you are getting a hang of everything. So back to our practical scenarios...
You are given an assignment to deploy microservices on a Kubernetes node. If files used by your containers are owned by root or another user, services may fail with permission errors. Ownership must match the container's running user. I've seen entire production environments grind to a halt because someone forgot this basic principle.
Also you're the senior DevOps engineer and you're onboarding a new DevOps engineer. Transferring ownership of key automation scripts ensures continuity. If you forget? Your systems rely on a former employee's account talk about risk! Nothing says "amateur hour" like having to call a former employee because they're still the owner of critical system files.
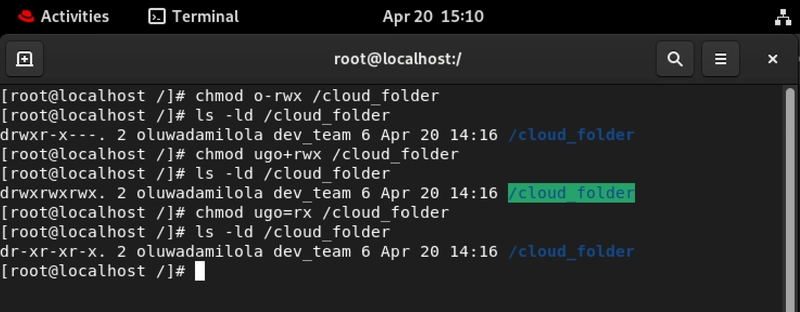
4. Modifying Permissions: Granular Control That Can Make or Break Your Deployment
Using chmod, you can adjust permissions with precision. Want to remove write access from others? Easy. Want to give full access to your CI/CD pipeline? Done.
# Remove all permissions from others
chmod o-rwx
# Add full permissions to user, group, and others
chmod ugo+rwx
# Set exact permissions (read + execute only)
chmod ugo=rx `
View this in it's holy grail...
Here's a use case:
Your automation pipeline pushes logs to a shared folder. You set chmod o-rwx to prevent other users from peeking at sensitive logs. Clean. Controlled. Secure. No more "who accessed the customer data logs?" creating more incidents to investigate.
Also in your company, your business partners need read-only access to performance reports. You set chmod g=r on the reports folder, assign them to the group, and boom!, read-only access, no accidental edits, no disasters. When the CEO asks why last quarter's numbers changed in the report, you won't be the one sweating bullets.
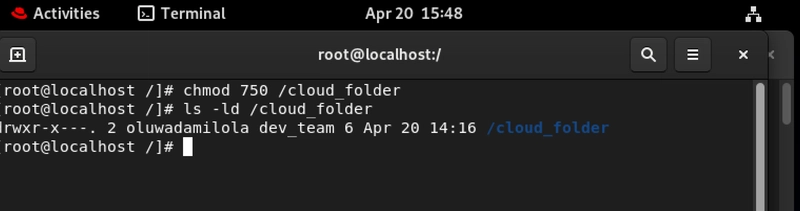
5. Numeric Shortcuts: Work Smarter, Not Harder!
For the efficiency minded (and who in cloud ops isn't?), permissions can be expressed as numbers:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
Add them up for each group (owner, group, others) to get a three-digit number:
chmod 750 /cloud_folder
This translates to:
- Owner (7): read (4) + write (2) + execute (1) = 7 (Full control)
- Group (5): read (4) + execute (1) = 5 (Can read and execute)
- Others (0): No permissions (Complete lockout)
So think about what happens if we set chmod 000?
When scripting your infrastructure with Terraform or using config management like Ansible, numeric notation is clean and precise. Instead of verbose strings, your IaC code simply uses mode: "0644" for configuration files. This consistency prevents deployment chaos and makes auditing way simpler.
If you find your self in a situation where you're setting up a multi-tenant environment where different business units share infrastructure. Using numeric permissions in your automation ensures each tenant's data remains properly isolated critical for both compliance and preventing internal politics.
6. Summary: File Permissions Are Security's First Line of Defense
Cloud pros love tools. We rave about Terraform, geek out over Docker, and throw around terms like observability and scalability. But behind the buzzwords is a quiet foundation and Linux file permissions are part of that.
They protect your scripts. They power your automation. They ensure the right people and only the right people can do the right things.
So the next time you're tempted to skip chmod or use 777 as a quick fix (we've all been there), remember: if you can't control access, you can't control the cloud. And sloppy permissions today mean security incidents tomorrow.
Your cloud infrastructure is only as secure as its weakest permission setting. Make them count...
Drop a comment if you've ever had a permissions disaster story. Trust me, we've all got at least one, and I'm here for the tea!
Connect with me on LinkedIn
#30DaysLinuxChallenge #CloudWhistler #RedHat #CloudJourney #DevOps #Linux #OpenSource #CloudSecurity #Womenthatbuild #RedHatEnterpriseLinux #Accesscontrol #EnterpriseIT #Ansible #OpenShift #SysAdmin #Automation #CloudEngineer










































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)
































































































































![From fast food worker to cybersecurity engineer with Tae'lur Alexis [Podcast #169]](https://cdn.hashnode.com/res/hashnode/image/upload/v1745242807605/8a6cf71c-144f-4c91-9532-62d7c92c0f65.png?#)
























![BPMN-procesmodellering [closed]](https://i.sstatic.net/l7l8q49F.png)






















































































.jpg?#)

































_Tanapong_Sungkaew_via_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale#)


























































































![PSA: Reddit confirms ongoing outage [U: Fixed]](https://i0.wp.com/9to5mac.com/wp-content/uploads/sites/6/2023/06/reddit-down.jpg?resize=1200%2C628&quality=82&strip=all&ssl=1)

















![Apple Releases iOS 18.5 Beta 3 and iPadOS 18.5 Beta 3 [Download]](https://www.iclarified.com/images/news/97076/97076/97076-640.jpg)
![Apple Seeds visionOS 2.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97077/97077/97077-640.jpg)
![Apple Seeds tvOS 18.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97078/97078/97078-640.jpg)
![Apple Seeds watchOS 11.5 Beta 3 to Developers [Download]](https://www.iclarified.com/images/news/97079/97079/97079-640.jpg)

























![Mobile Legends: Bang Bang [MLBB] Free Redeem Codes April 2025](https://www.talkandroid.com/wp-content/uploads/2024/07/Screenshot_20240704-093036_Mobile-Legends-Bang-Bang.jpg)