Hybrid Solution For Secure Data Mining In Cloud Computing
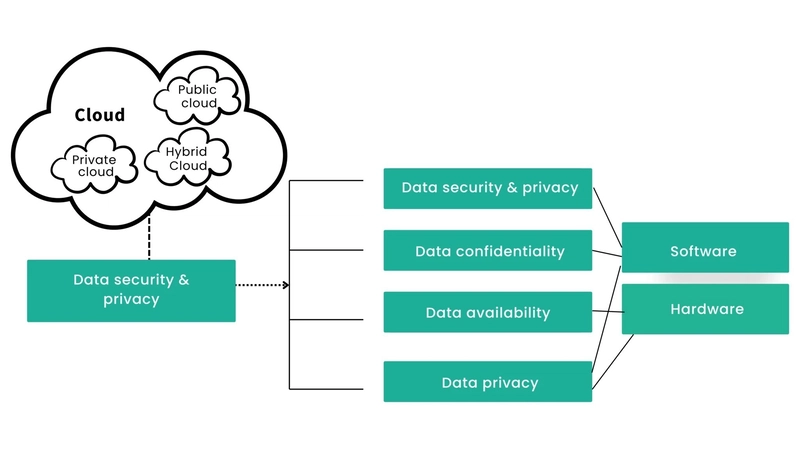
Data mining in cloud environments has become a cornerstone for organizations aiming to extract valuable insights from extensive datasets. While cloud computing offers unparalleled scalability and flexibility, it also introduces significant concerns regarding data privacy and security. To address these challenges, hybrid solutions have emerged, combining multiple techniques to ensure effective and privacy-preserving data mining operations. Understanding Privacy-Preserving Data Mining Privacy-Preserving Data Mining (PPDM) focuses on enabling data analysis without compromising the confidentiality of sensitive information. Traditional data mining methods often risk exposing personal data, leading to potential misuse. PPDM employs various strategies to mitigate these risks, ensuring that data remains protected throughout the mining process. Advanced Cloud Security Solutions In the realm of data mining in cloud environments, ensuring robust security measures is paramount. Companies like Glaxit offer advanced cloud security solutions designed to protect critical data and applications hosted in the cloud. Their services encompass comprehensive strategies to protect against internal and external threats, ensuring data confidentiality, integrity, and compliance with regulatory standards. Challenges in Cloud-Based Data Mining While data mining in cloud platforms offers numerous advantages, it also presents unique challenges: Data Confidentiality: Ensuring that sensitive information remains inaccessible to unauthorized parties is paramount. Data Integrity: Maintaining the accuracy and consistency of data during transmission and storage is crucial. Regulatory Compliance: Adhering to data protection regulations, such as GDPR, necessitates robust privacy measures. Hybrid Solutions for Privacy Preservation To tackle these challenges, hybrid approaches integrate multiple privacy-preserving techniques, enhancing the overall security of data mining in cloud environments. Notable hybrid methods include: K-Anonymity and Homomorphic Encryption: Combining k-anonymity, which generalizes data to prevent individual identification, with homomorphic encryption, allowing computations on encrypted data without decryption, enhances privacy. Research indicates that this integration improves privacy levels by 23% while maintaining data utility. Geometric Data Perturbation and K-Anonymization: This approach perturbs numerical data geometrically and anonymizes categorical data, balancing privacy with data utility. Studies have shown that this method achieves better classification accuracy compared to individual techniques. Real-World Applications and Examples Implementing hybrid privacy-preserving techniques in data mining in cloud environments has practical applications across various sectors: Healthcare: Hospitals can analyze patient data to identify treatment trends without exposing individual records, enhancing patient confidentiality. Finance: Financial institutions can detect fraudulent activities by analyzing transaction patterns while safeguarding customer information. Retail: Retailers can study purchasing behaviors to optimize inventory and marketing strategies without compromising consumer privacy. Implementing Hybrid Solutions: Steps and Considerations Adopting hybrid solutions for privacy-preserving data mining in cloud environments involves several critical steps: Data Assessment: Evaluate the sensitivity of the data to determine appropriate privacy measures. Technique Selection: Choose suitable hybrid methods based on data types and desired outcomes. Integration and Testing: Implement the selected techniques and rigorously test to ensure data utility and privacy are balanced. Compliance Verification: Ensure that the implemented solutions adhere to relevant data protection regulations. Continuous Monitoring: Regularly monitor and update the system to address emerging threats and maintain robust security. Conclusion As organizations increasingly rely on data mining in cloud platforms, prioritizing data privacy becomes essential. Hybrid solutions, which combine various privacy-preserving techniques, offer a robust approach to secure sensitive information while enabling effective data analysis. By implementing these strategies, businesses can harness the full potential of cloud-based data mining without compromising on privacy or security.

Data mining in cloud environments has become a cornerstone for organizations aiming to extract valuable insights from extensive datasets. While cloud computing offers unparalleled scalability and flexibility, it also introduces significant concerns regarding data privacy and security. To address these challenges, hybrid solutions have emerged, combining multiple techniques to ensure effective and privacy-preserving data mining operations.
Understanding Privacy-Preserving Data Mining
Privacy-Preserving Data Mining (PPDM) focuses on enabling data analysis without compromising the confidentiality of sensitive information. Traditional data mining methods often risk exposing personal data, leading to potential misuse. PPDM employs various strategies to mitigate these risks, ensuring that data remains protected throughout the mining process.
Advanced Cloud Security Solutions
In the realm of data mining in cloud environments, ensuring robust security measures is paramount. Companies like Glaxit offer advanced cloud security solutions designed to protect critical data and applications hosted in the cloud. Their services encompass comprehensive strategies to protect against internal and external threats, ensuring data confidentiality, integrity, and compliance with regulatory standards.
Challenges in Cloud-Based Data Mining
While data mining in cloud platforms offers numerous advantages, it also presents unique challenges:
Data Confidentiality: Ensuring that sensitive information remains inaccessible to unauthorized parties is paramount.
Data Integrity: Maintaining the accuracy and consistency of data during transmission and storage is crucial.
Regulatory Compliance: Adhering to data protection regulations, such as GDPR, necessitates robust privacy measures.
Hybrid Solutions for Privacy Preservation
To tackle these challenges, hybrid approaches integrate multiple privacy-preserving techniques, enhancing the overall security of data mining in cloud environments. Notable hybrid methods include:
K-Anonymity and Homomorphic Encryption: Combining k-anonymity, which generalizes data to prevent individual identification, with homomorphic encryption, allowing computations on encrypted data without decryption, enhances privacy. Research indicates that this integration improves privacy levels by 23% while maintaining data utility.
Geometric Data Perturbation and K-Anonymization: This approach perturbs numerical data geometrically and anonymizes categorical data, balancing privacy with data utility. Studies have shown that this method achieves better classification accuracy compared to individual techniques.
Real-World Applications and Examples
Implementing hybrid privacy-preserving techniques in data mining in cloud environments has practical applications across various sectors:
Healthcare: Hospitals can analyze patient data to identify treatment trends without exposing individual records, enhancing patient confidentiality.
Finance: Financial institutions can detect fraudulent activities by analyzing transaction patterns while safeguarding customer information.
Retail: Retailers can study purchasing behaviors to optimize inventory and marketing strategies without compromising consumer privacy.
Implementing Hybrid Solutions: Steps and Considerations
Adopting hybrid solutions for privacy-preserving data mining in cloud environments involves several critical steps:
Data Assessment: Evaluate the sensitivity of the data to determine appropriate privacy measures.
Technique Selection: Choose suitable hybrid methods based on data types and desired outcomes.
Integration and Testing: Implement the selected techniques and rigorously test to ensure data utility and privacy are balanced.
Compliance Verification: Ensure that the implemented solutions adhere to relevant data protection regulations.
Continuous Monitoring: Regularly monitor and update the system to address emerging threats and maintain robust security.
As organizations increasingly rely on data mining in cloud platforms, prioritizing data privacy becomes essential. Hybrid solutions, which combine various privacy-preserving techniques, offer a robust approach to secure sensitive information while enabling effective data analysis. By implementing these strategies, businesses can harness the full potential of cloud-based data mining without compromising on privacy or security.











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)





























































































.webp?#)























































































![Here’s the first live demo of Android XR on Google’s prototype smart glasses [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/google-android-xr-ted-glasses-demo-3.png?resize=1200%2C628&quality=82&strip=all&ssl=1)














![New Beats USB-C Charging Cables Now Available on Amazon [Video]](https://www.iclarified.com/images/news/97060/97060/97060-640.jpg)

![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)