Better Reverse Engineering with Frida and Ghidra
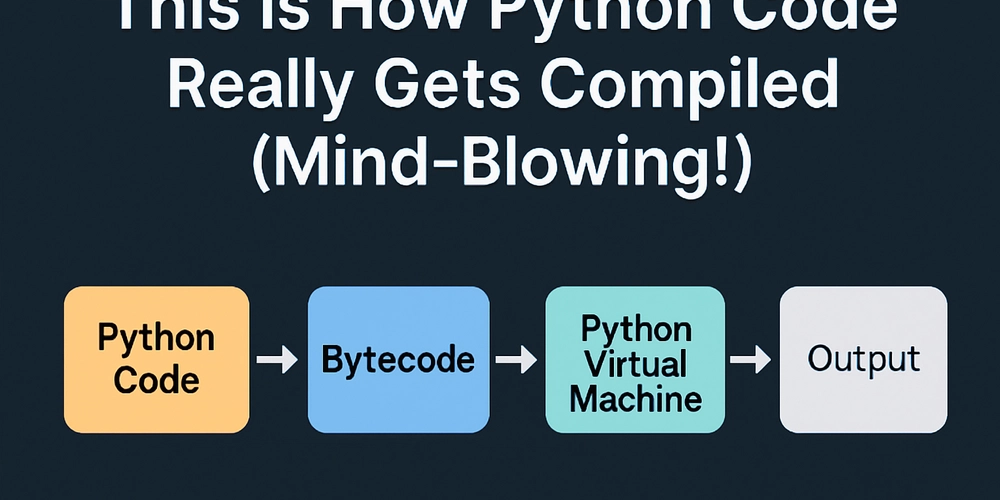
Frida and Ghidra: A Powerful Reverse Engineering Team Reverse engineering can feel like trying to understand a machine without its instruction manual. Tools like Ghidra are great for taking the machine apart and looking at all the pieces. But sometimes, you need to see the machine running to really get how it works. That's where Frida comes in handy. Ghidra is a free and open-source tool that lets you see the code and structure of computer programs. It helps you understand the blueprint of the software. Frida, on the other hand, is like a special toolkit that lets you poke around inside a program while it's actually running on a computer, phone, or other device. You can inject little bits of code (using a language called JavaScript) to watch what's happening and even change things as they go. So, why is using Frida together with Ghidra so helpful for reverse engineering? They work together to give you a full picture: Ghidra shows you what the program could do. Frida shows you what it actually does when it's running. You can see the real data being used, which helps confirm what you see in Ghidra. Some programs try to hide their inner workings. Ghidra can have trouble with these. But Frida can often bypass these tricks by looking at the program after it has already revealed its true form in the computer's memory. Ghidra can draw maps of how the program flows. Frida can show you the exact path the program takes when you perform a specific action. This makes it easier to understand complicated logic and how different parts of the program connect. Frida lets you really focus your investigation: You can "hook" functions. This means you can jump in whenever a specific part of the program (a function) is used. You can see what information goes into the function and what comes out. You can even change the information or make the function do something different. This is super useful for seeing how different parts of a program communicate and for finding potential weaknesses. You can look at and change the program's memory. Frida lets you peek at the raw data the program is using and even modify it. This can help you understand how information is stored, find hidden secrets, or test if the program is vulnerable to attacks (in a safe, controlled way, of course!). You can trace what the program is doing. Frida can keep a detailed log of the program's actions – what functions it calls, what system commands it uses, and other important events. This gives you a timeline of the program's activity, making it easier to figure out exactly what's happening. Using Frida makes Ghidra even more powerful: The real-world information you get from Frida makes your analysis in Ghidra more accurate. You can add notes to the code in Ghidra based on what you observe with Frida. If you have an idea about how something works in Ghidra, you can use Frida to test that idea in the running program. This back-and-forth process speeds up your reverse engineering work and makes it more reliable. Sometimes, parts of a program only run in very specific situations that are hard to figure out just by looking at the code in Ghidra. Frida can help you trigger these situations and see what happens, revealing hidden or less obvious features. Imagine this example: You're using Ghidra to look at a mobile app and you find a strange piece of code that seems to handle private user information. With Frida, you could: See exactly when and how this piece of code is used. Record the actual private information it's working with. Look at the information in the app's memory while this code is running. Try giving it different kinds of information to see if there are any security issues. This live view, combined with Ghidra's ability to show you the code itself, gives you a much clearer picture of what's going on. How to get started: Both Frida and Ghidra have good documentation and helpful communities online. To start using them together: Install Ghidra: You can download the latest version from the official Ghidra website: https://ghidra-sre.org/. Follow the installation instructions provided on the site. Install Frida: Frida is typically installed using pip, the package installer for Python. Open your terminal or command prompt and run: pip install frida-tools. You can find more information about Frida installation on their documentation page: https://frida.re/docs/installation/. Learn a little bit of JavaScript: Frida uses JavaScript for its scripting capabilities. There are many online resources for learning JavaScript, such as the Mozilla Developer Network (MDN) JavaScript guide: https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide. Read Frida's documentation: The official Frida documentation provides a comprehensive guide to its features and API: https://frida.re/docs/home/. Pay particular attention to the sections on "Core Concepts" and the "API Reference." Start by practicing on simple programs: Try

Frida and Ghidra: A Powerful Reverse Engineering Team
Reverse engineering can feel like trying to understand a machine without its instruction manual. Tools like Ghidra are great for taking the machine apart and looking at all the pieces. But sometimes, you need to see the machine running to really get how it works. That's where Frida comes in handy.
Ghidra is a free and open-source tool that lets you see the code and structure of computer programs. It helps you understand the blueprint of the software. Frida, on the other hand, is like a special toolkit that lets you poke around inside a program while it's actually running on a computer, phone, or other device. You can inject little bits of code (using a language called JavaScript) to watch what's happening and even change things as they go.
So, why is using Frida together with Ghidra so helpful for reverse engineering?
They work together to give you a full picture:
- Ghidra shows you what the program could do. Frida shows you what it actually does when it's running. You can see the real data being used, which helps confirm what you see in Ghidra.
- Some programs try to hide their inner workings. Ghidra can have trouble with these. But Frida can often bypass these tricks by looking at the program after it has already revealed its true form in the computer's memory.
- Ghidra can draw maps of how the program flows. Frida can show you the exact path the program takes when you perform a specific action. This makes it easier to understand complicated logic and how different parts of the program connect.
Frida lets you really focus your investigation:
- You can "hook" functions. This means you can jump in whenever a specific part of the program (a function) is used. You can see what information goes into the function and what comes out. You can even change the information or make the function do something different. This is super useful for seeing how different parts of a program communicate and for finding potential weaknesses.
- You can look at and change the program's memory. Frida lets you peek at the raw data the program is using and even modify it. This can help you understand how information is stored, find hidden secrets, or test if the program is vulnerable to attacks (in a safe, controlled way, of course!).
- You can trace what the program is doing. Frida can keep a detailed log of the program's actions – what functions it calls, what system commands it uses, and other important events. This gives you a timeline of the program's activity, making it easier to figure out exactly what's happening.
Using Frida makes Ghidra even more powerful:
- The real-world information you get from Frida makes your analysis in Ghidra more accurate. You can add notes to the code in Ghidra based on what you observe with Frida.
- If you have an idea about how something works in Ghidra, you can use Frida to test that idea in the running program. This back-and-forth process speeds up your reverse engineering work and makes it more reliable.
- Sometimes, parts of a program only run in very specific situations that are hard to figure out just by looking at the code in Ghidra. Frida can help you trigger these situations and see what happens, revealing hidden or less obvious features.
Imagine this example:
You're using Ghidra to look at a mobile app and you find a strange piece of code that seems to handle private user information. With Frida, you could:
- See exactly when and how this piece of code is used.
- Record the actual private information it's working with.
- Look at the information in the app's memory while this code is running.
- Try giving it different kinds of information to see if there are any security issues.
This live view, combined with Ghidra's ability to show you the code itself, gives you a much clearer picture of what's going on.
How to get started:
Both Frida and Ghidra have good documentation and helpful communities online. To start using them together:
- Install Ghidra: You can download the latest version from the official Ghidra website: https://ghidra-sre.org/. Follow the installation instructions provided on the site.
- Install Frida: Frida is typically installed using pip, the package installer for Python. Open your terminal or command prompt and run:
pip install frida-tools. You can find more information about Frida installation on their documentation page: https://frida.re/docs/installation/. - Learn a little bit of JavaScript: Frida uses JavaScript for its scripting capabilities. There are many online resources for learning JavaScript, such as the Mozilla Developer Network (MDN) JavaScript guide: https://developer.mozilla.org/en-US/docs/Web/JavaScript/Guide.
- Read Frida's documentation: The official Frida documentation provides a comprehensive guide to its features and API: https://frida.re/docs/home/. Pay particular attention to the sections on "Core Concepts" and the "API Reference."
- Start by practicing on simple programs: Try using Frida to look at basic applications on your computer to get a feel for how to hook functions and observe their behavior. There are often tutorials and examples available online that can guide you through your first Frida scripts.
In conclusion:
Ghidra is a fantastic tool for taking software apart and seeing its structure. Frida adds the crucial ability to see that software in action. When you combine these two tools, you get a really powerful way to understand how any program works, find hidden features, and uncover potential security problems. They make the often-difficult job of reverse engineering much more effective and insightful. So, give Frida and Ghidra a try and see what you can discover!











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)




























































































.webp?#)


























































































![Here’s the first live demo of Android XR on Google’s prototype smart glasses [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/google-android-xr-ted-glasses-demo-3.png?resize=1200%2C628&quality=82&strip=all&ssl=1)














![New Beats USB-C Charging Cables Now Available on Amazon [Video]](https://www.iclarified.com/images/news/97060/97060/97060-640.jpg)

![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)