A Lightweight Authentication and Key Negotiation Protocol for IIoT using ECC
Industrial Internet of Things (IIoT) is reshaping the manufacturing and automation sectors by connecting smart devices across factories, plants, and supply chains. But as connectivity grows, so do security risks — especially when devices are resource-constrained and operate in potentially hostile environments. In this post, I’ll share a lightweight three-factor mutual authentication protocol using Elliptic Curve Cryptography (ECC) that I developed as part of my cryptography project. This scheme ensures secure communication between users and gateways in an IIoT environment. ECC ECC offers strong security with smaller key sizes, making it ideal for IIoT devices that have limited processing power and storage. It supports faster computations and lower energy consumption compared to traditional cryptographic methods like RSA. Authentication & Login Phase When the user wants to log in, the smart card is used to verify the three factors again (ID, password, biometric). Only if all three match, the gateway authenticates the user and starts a secure session.
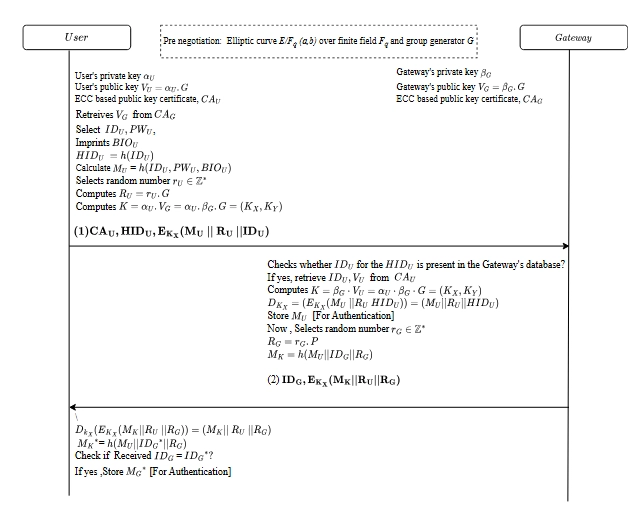
Industrial Internet of Things (IIoT) is reshaping the manufacturing and automation sectors by connecting smart devices across factories, plants, and supply chains. But as connectivity grows, so do security risks — especially when devices are resource-constrained and operate in potentially hostile environments.
In this post, I’ll share a lightweight three-factor mutual authentication protocol using Elliptic Curve Cryptography (ECC) that I developed as part of my cryptography project. This scheme ensures secure communication between users and gateways in an IIoT environment.
ECC
ECC offers strong security with smaller key sizes, making it ideal for IIoT devices that have limited processing power and storage. It supports faster computations and lower energy consumption compared to traditional cryptographic methods like RSA.
Authentication & Login Phase
When the user wants to log in, the smart card is used to verify the three factors again (ID, password, biometric). Only if all three match, the gateway authenticates the user and starts a secure session.











































































































































































![[The AI Show Episode 144]: ChatGPT’s New Memory, Shopify CEO’s Leaked “AI First” Memo, Google Cloud Next Releases, o3 and o4-mini Coming Soon & Llama 4’s Rocky Launch](https://www.marketingaiinstitute.com/hubfs/ep%20144%20cover.png)

















































































































































































![Rogue Company Elite tier list of best characters [April 2025]](https://media.pocketgamer.com/artwork/na-33136-1657102075/rogue-company-ios-android-tier-cover.jpg?#)





























































































.webp?#)























































































![Here’s the first live demo of Android XR on Google’s prototype smart glasses [Video]](https://i0.wp.com/9to5google.com/wp-content/uploads/sites/4/2025/04/google-android-xr-ted-glasses-demo-3.png?resize=1200%2C628&quality=82&strip=all&ssl=1)














![New Beats USB-C Charging Cables Now Available on Amazon [Video]](https://www.iclarified.com/images/news/97060/97060/97060-640.jpg)

![Apple M4 13-inch iPad Pro On Sale for $200 Off [Deal]](https://www.iclarified.com/images/news/97056/97056/97056-640.jpg)